Brief introduction to Traceroute and Traceroute with Nmap
When we interact with other devices within a network, such as the Internet, the information or packets are sent through a number of network devices such as routers until reaching the destination. If we connect two computers directly with a UTP cable the packets are sent directly from a computer to another, this does not happen normally when routers, hubs and similar devices route packets through the network. Let’s take the internet as an example, if I access a website the traffic first will pass through my local router or device, then it will probably pass through my ISP routing devices, probably neutral routers or devices related to my and destination local devices.
The transference of the packets between routing devices is called “hop”, so if I ping a website the first hop will be my local router and next hops will be each router through which the packets pass until reaching the web server.
Tracerouting as its name says consists in gathering information on the intermediating routers through which the traffic pass from a point to another. Most OS (operating systems) already bring this functionality through the command “traceroute”. Nmap also brings additional tools included in the Nmap NSE (Nmap Scripting Engine) suite for tracerouting which will be described below.
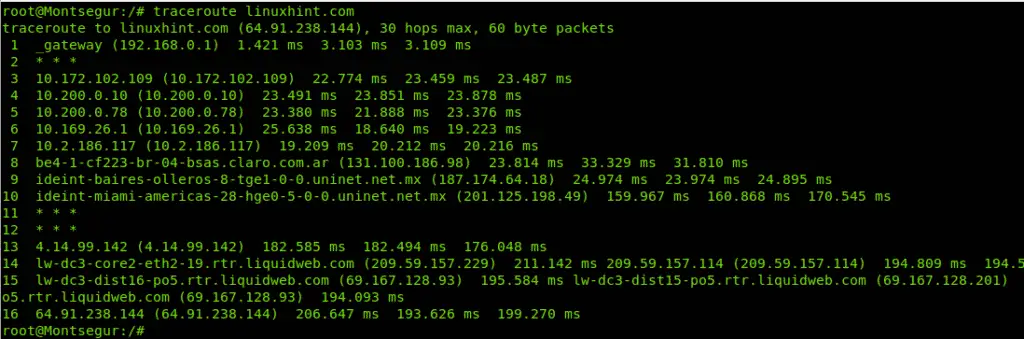
Example of regular traceroute with Linux (no Nmap).The following example shows how traceroute is carried out through Linux Hint without aid of Nmap.
Traceroute examples with Nmap
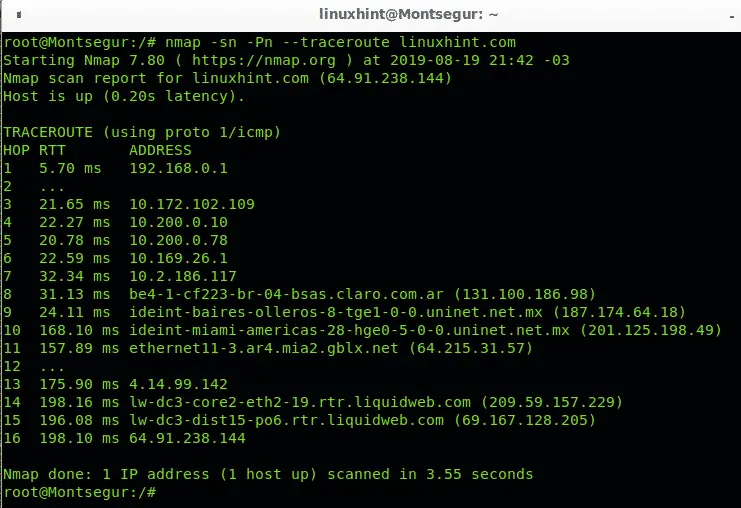
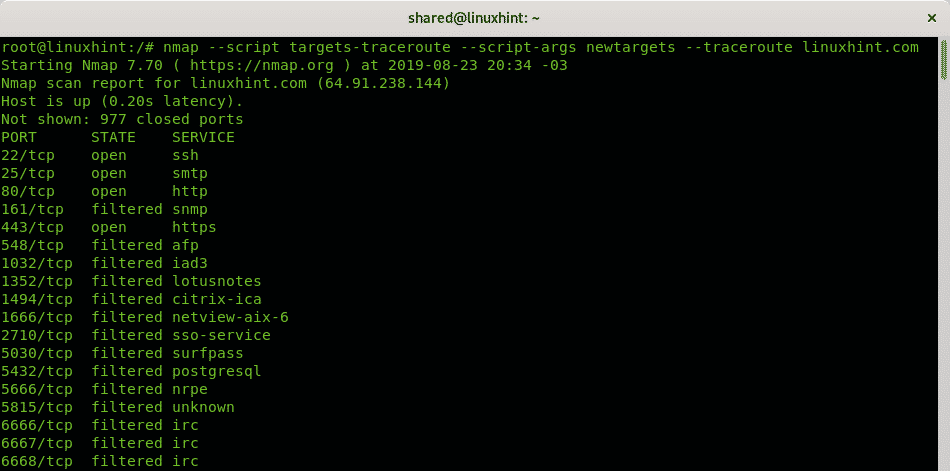
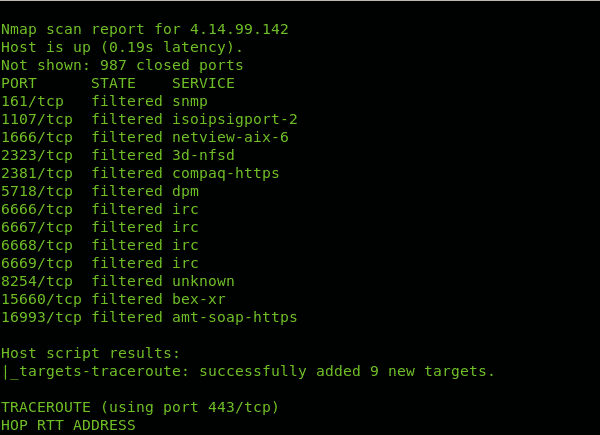
In the following example we are tracing the route from my device to LinuxHint.com, the option -sn instructs Nmap to omit the default port scan, since we aren’t interested to scan LinuxHint.com ports but only the route, the option or flag -Pn instructs Nmap to avoid the host discovery since we know the host is alive. The option –traceroute is used to trace all hops or intermediating routers.
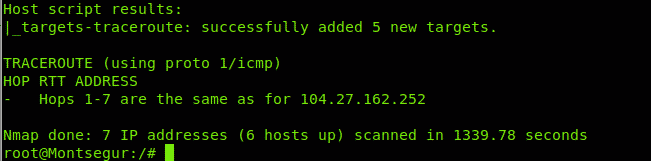
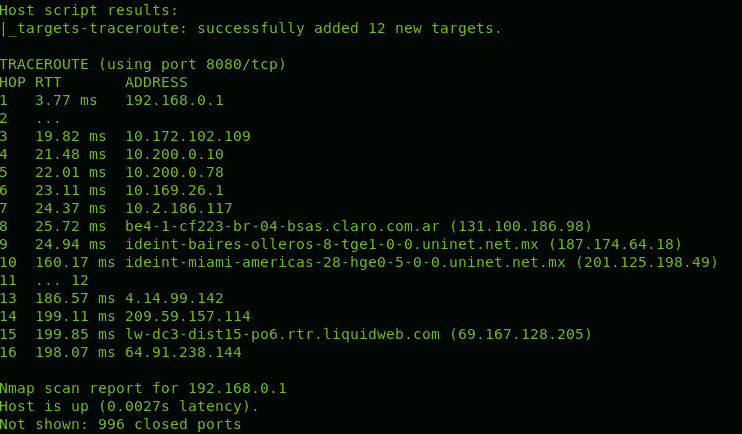
As you can see in the results above, there are 16 devices (hops) between my computer and LinuxHint.com server, it is specified in the column HOP. The column RTT (Round Trip Time or latency) shows the speed in milliseconds for each hop including return from that HOP, this is especially useful to diagnose connection issues. The column ADDRESS shows the address of each routing device or hop.
In this case you see the first hop is my router with address 192.168.0.1, then it goes to 7 routers, the eight router is located in Buenos Aires, Argentina, and belongs to the telecommunication company Claro which sends the traffic to the next hop located in Mexico, then it goes to Miami, to a gblx.net router to end at liquidweb hosting service. 16 hops in total. Of course, as farer the router the RTT increases.
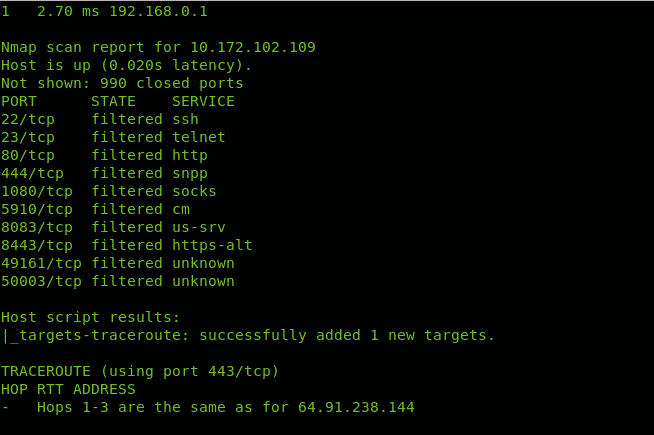
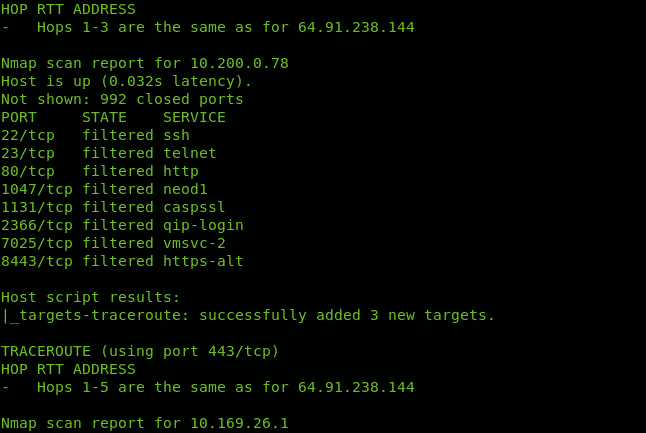
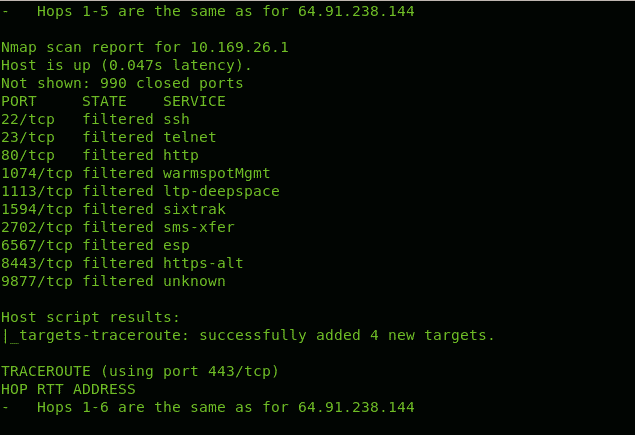
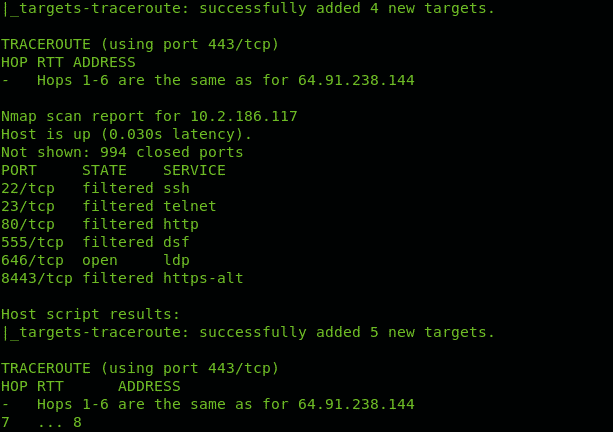
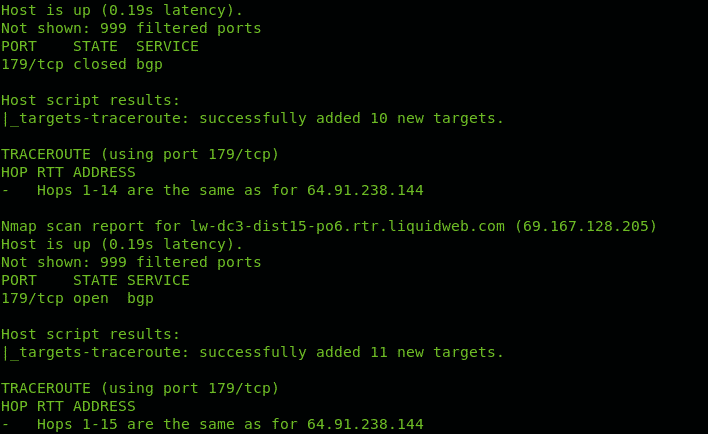
Inserting traceroute hops into the Nmap scan with NSE
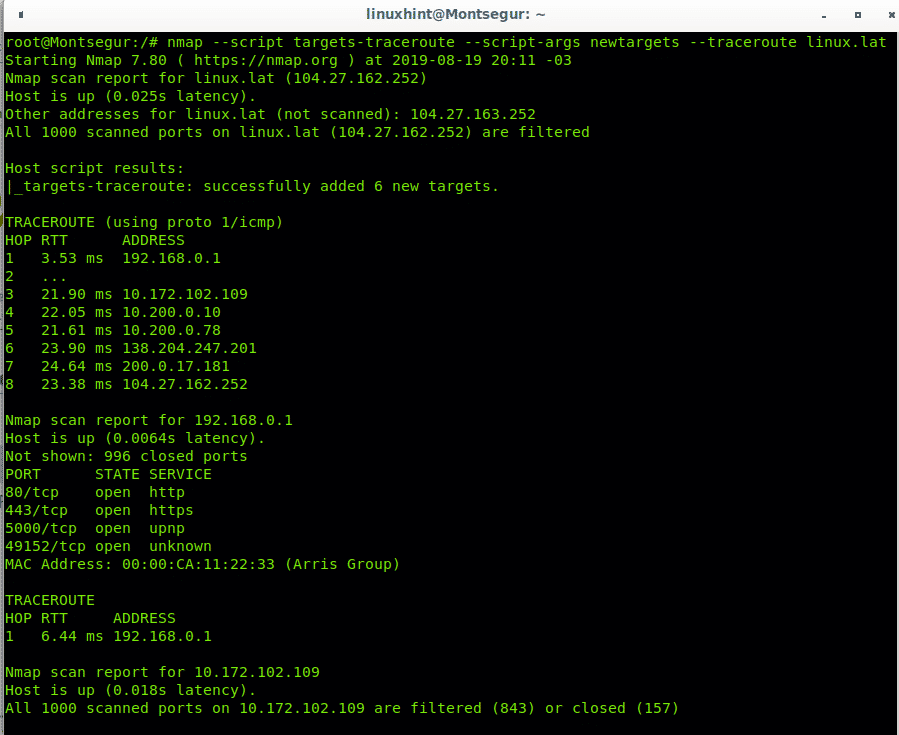
Nmap Scripting Engine includes scripts to manage tracerouting adding great functionalities. In this case we only use Nmap NSE to port scan all hops intermediating to reach linux.lat.
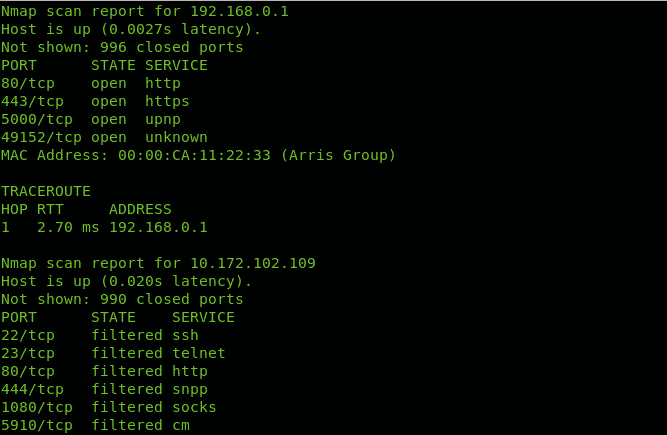
You can see in contrast to the first example Nmap checked for ports state.
Let’s try to traceroute all hops until reaching the site LinuxHint.com
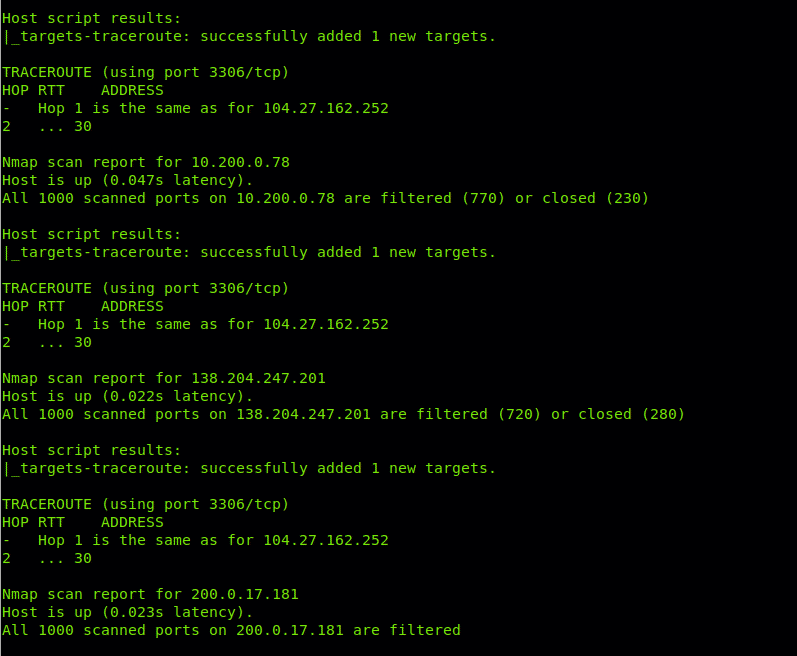
Note: some screenshots were omitted since was too much useless examples for descriptive purpose.
As you can see Nmap throws information on ports for discovered hops.
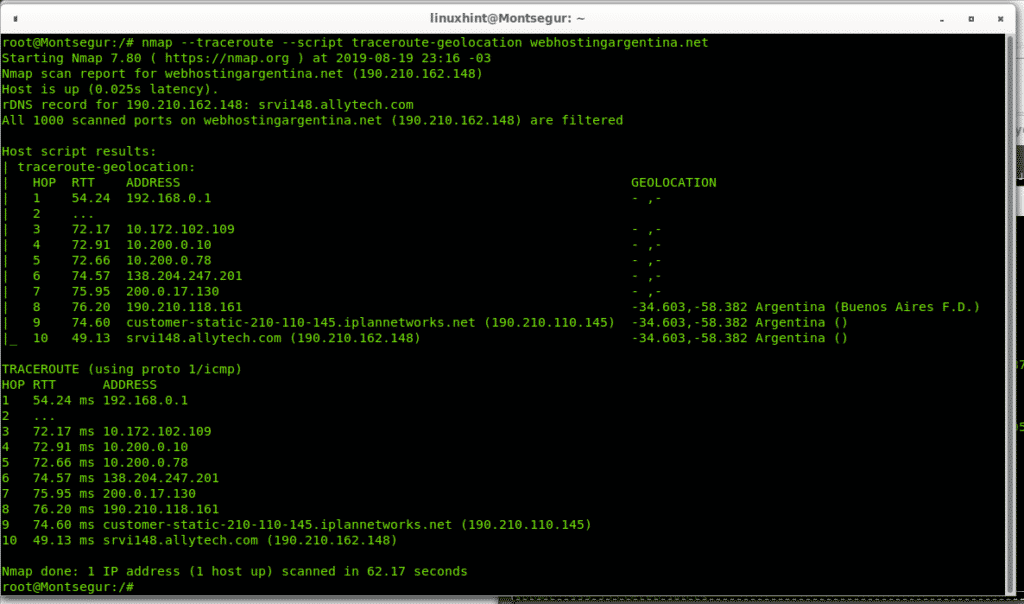
Geolocation of each hop in a traceroute using NSE (Incompatible with Google Earth/Maps)
The following NSE script allows us to geographically locate each hop through which the traffic goes (only country). This script used to allow to save results in a KML file which we could import to Google Earth and Google maps but the format is unreadable for new versions of Google Earth and Google maps since the format is obsolete (3 different alternatives for geolocation from the Nmap Scripting Engine suite are mentioned below).
As you see some of the hops countries are listed as Argentinians.
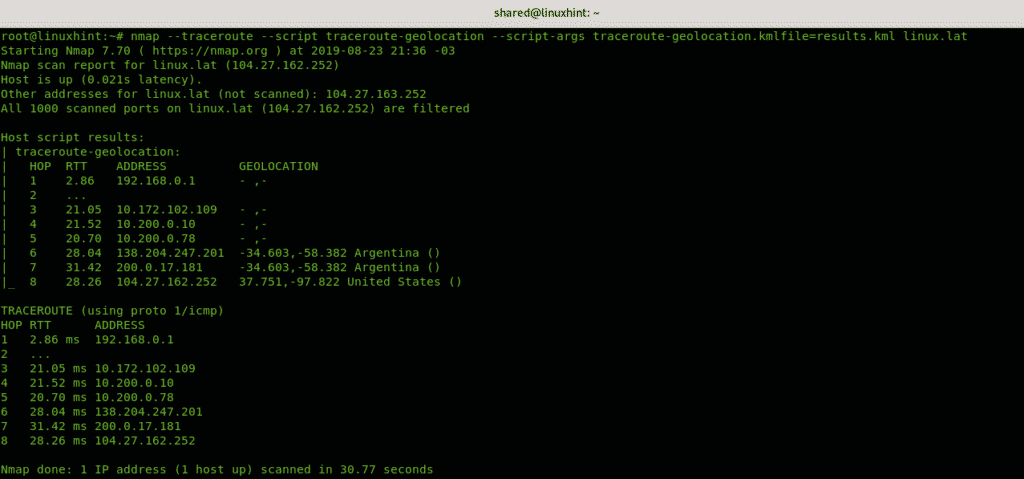
traceroute-geolocation linux.lat
As you can see some hops are identified as Argentinians and one American but not all hops were geolocated, this functionality is to geolocate hops, if you want to geolocate devices you have additional scripts like the ip-geolocation-geoplugin, ip-geolocation-maxmind and ip-geolocation-ipinfodb, you can manually geolocate each hop you discovered while tracerouting both with Nmap or the regular Linux
Conclusion on Nmap traceroute
Nmap traceroute is a great tool to diagnose connectivity problems such as delays or lack of access, if a specific hop is blocking you, through Nmap traceroute you can even discover your target hosting service or identify additional targets according to your goals. It is important to highlight when tracerouting results may vary depending on available and closer hops, also there is not really an advantage for Nmap traceroute over regular Linux traceroute command if you don’t need additional functions to traceroute, despite this Nmap continues being one of the best tools for offensive and defensive security when attacking or diagnosing security measures even if its tracerouting functions aren’t considerably advantageous as you can confirm reading additional articles on the Related Articles section.
I hope you found this tutorial useful as introduction to Nmap traceroute, keep following LinuxHint for more tips and updates on Linux and networking.