This tutorial focuses on ping sweep using Nmap.
Ping sweep is a method to discover devices within a network as long as they are turned on and connected. Of course, you can discover all hosts within a network using different techniques. But one of the ping sweep advantages is contrary to other methods, this one is not aggressive and can skip regular scan stages, making it harder to be detected.
Ping sweep can be done using different tools, like Nmap (Network Mapper), the most flexible and widely used network and security scanner, the main tool for both system administrators and hackers.
All instructions explained in this ping sweep tutorial include screenshots, making it easy for any user to follow them.
Getting Started with Nmap Ping Sweep
In case you don’t have Nmap installed yet, on Debian and its Linux distributions you can install it by running the command shown below.
Once Nmap is installed, we can proceed with the ping sweep techniques.
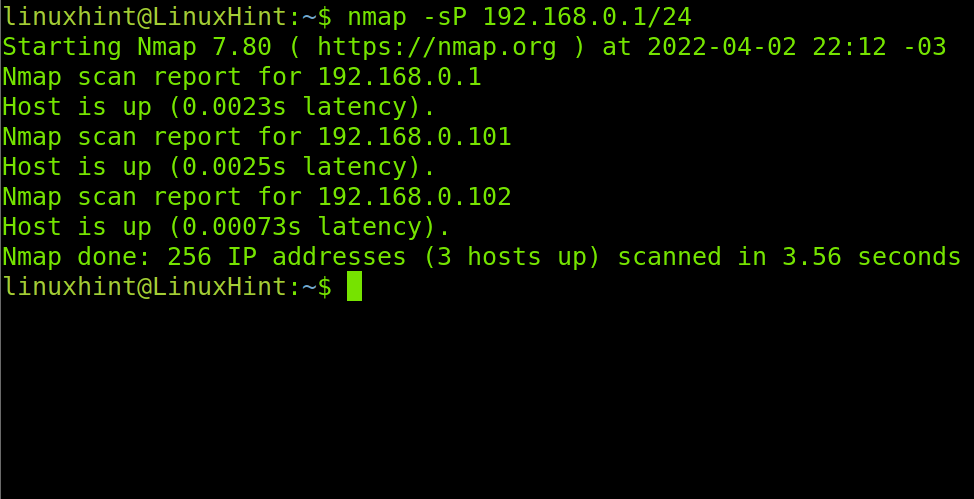
There are two main Nmap flags we can use for ping sweep. These flags basically tell Nmap not to run a port scan after the host discovery process finds a device.
The flags are -sP and -sn, where -sn is the replacement of the old -sP flag.
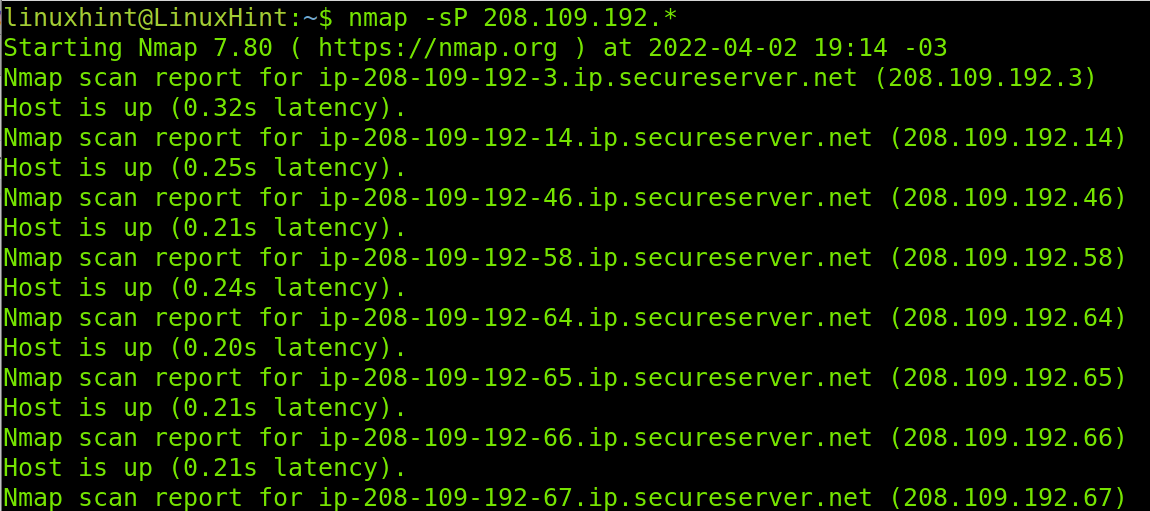
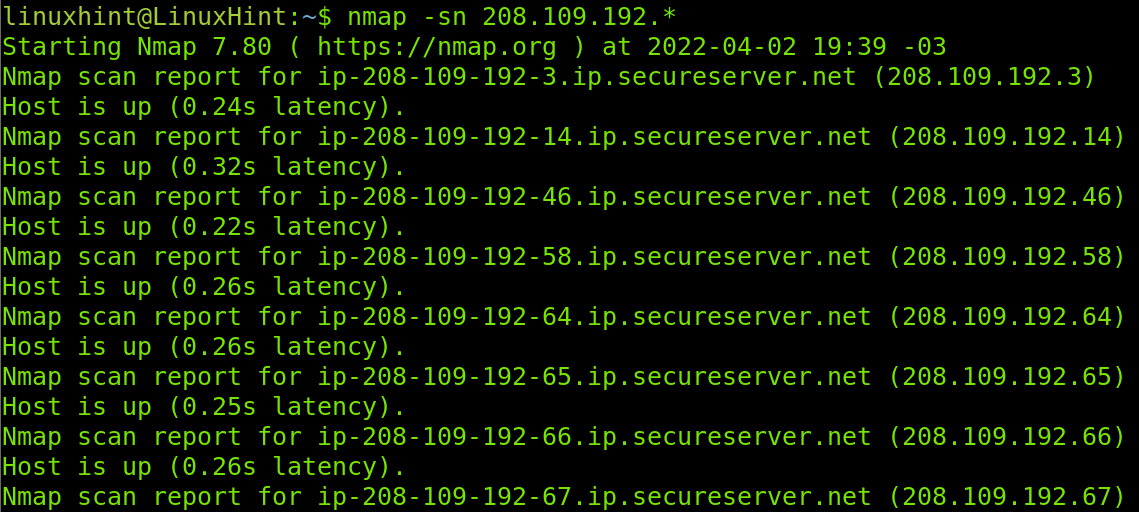
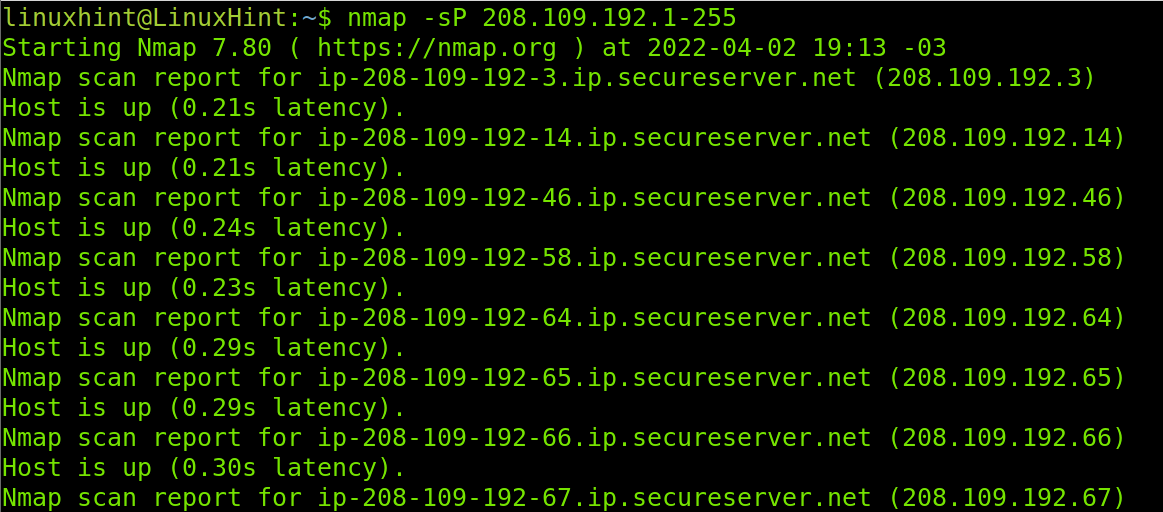
The example below shows how to discover all hosts within the last segment or octet of the network with the first three segments/octets 208.109.192.X. Where X is the segment with all hosts we want to discover. In this case, I instructed Nmap to find all hosts by defining an IP range from 1 to 255 (1-255).
Another way to check all hosts within an octet is by implementing the wildcard (*), it is exactly the same as defining a range from 1 to 255.
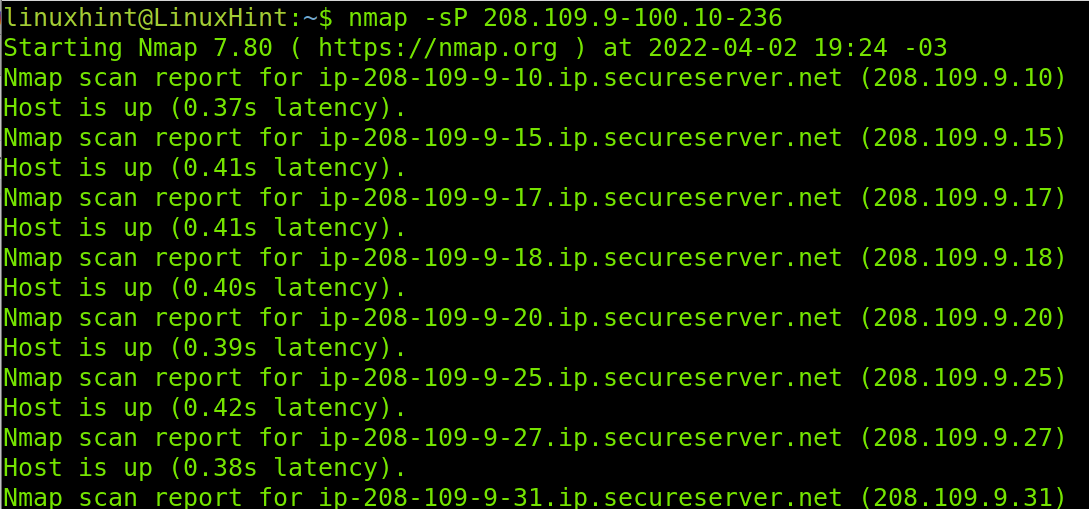
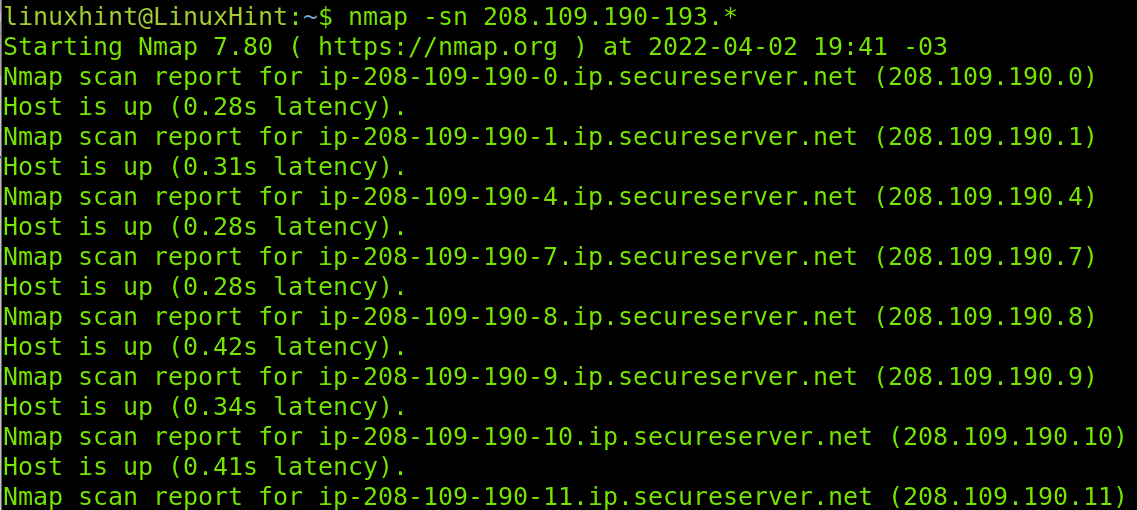
You can look for available hosts in more to one segment. In the example below, Nmap will check for alive hosts in the third and fourth segments, the third segment will return available hosts between 9 and 100, while the fourth segment will be analyzed for alive hosts between 10 and 236.
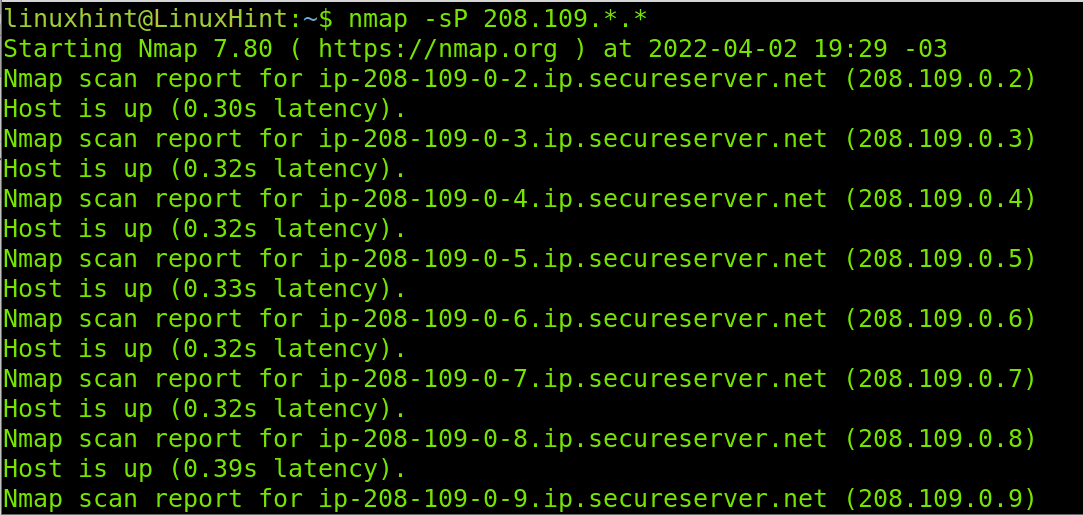
If you are looking for all alive hosts within more than a segment, you can use the wildcard in multiple segments as shown below, of course this will take longer.
You also can use subnets to discover hosts using Nmap ping sweep as shown in the following image.
As said previously, Nmap notified the -sP flag explained above is being replaced by the -sn flag.
As you can see in the example below, the result is exactly the same.
With both flags, you can combine wildcard and IP ranges as shown below.
Like with the -sP flag, with -sn you can also discover hosts by specifying the subnet as shown below.
The -sn flag usage is the same as with -sP.
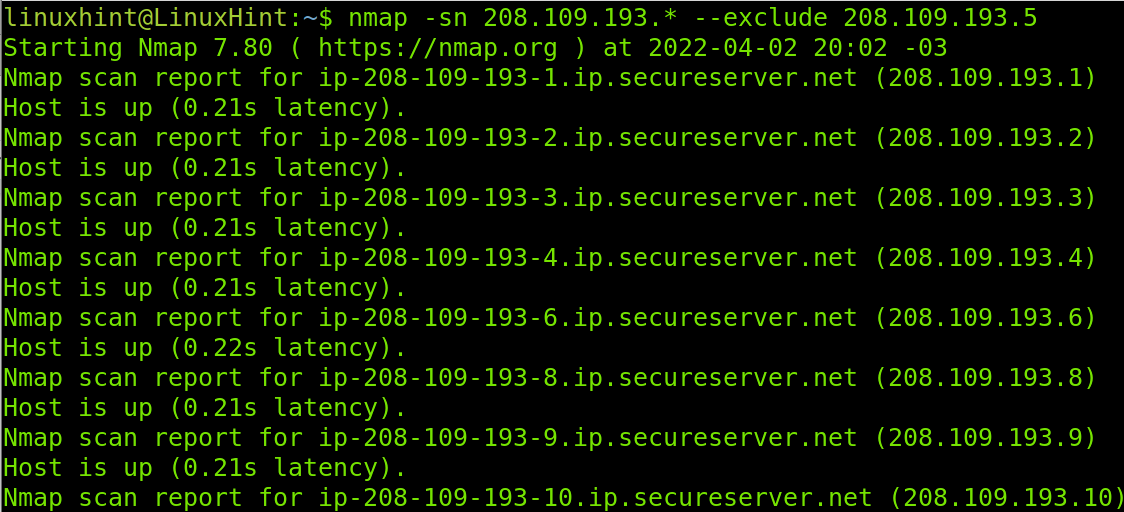
There are additional options you can implement. For example, you can scan a whole range or part of it while excluding a specific IP or a specific range. To do it, you need to add the –exclude option.
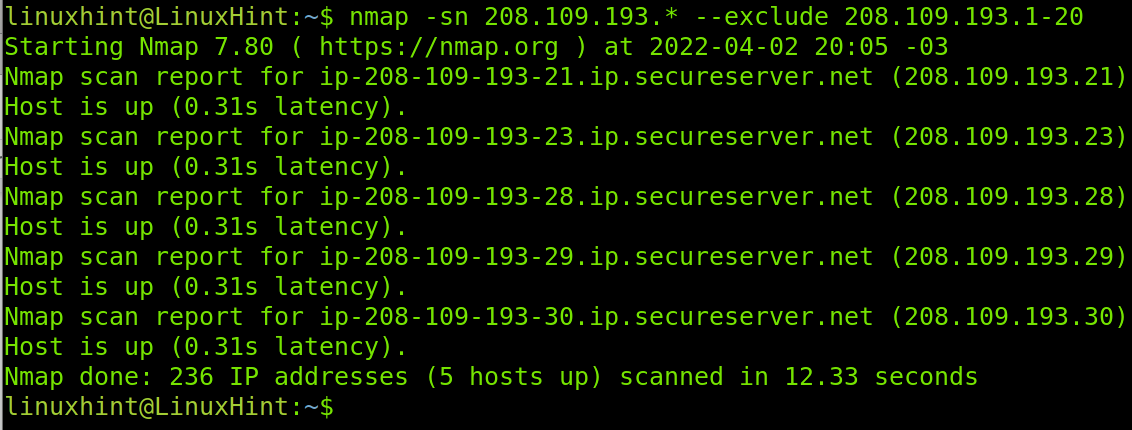
As you can see in the example below, all IP addresses within the last segment will be checked as specified by the wildcard, but the –exclude option instructs to skip the IP 208.109.193.5.
The example below excludes the IPs range from 208.109.193.1 to 208.109.193.20. These IP addresses will be skipped.
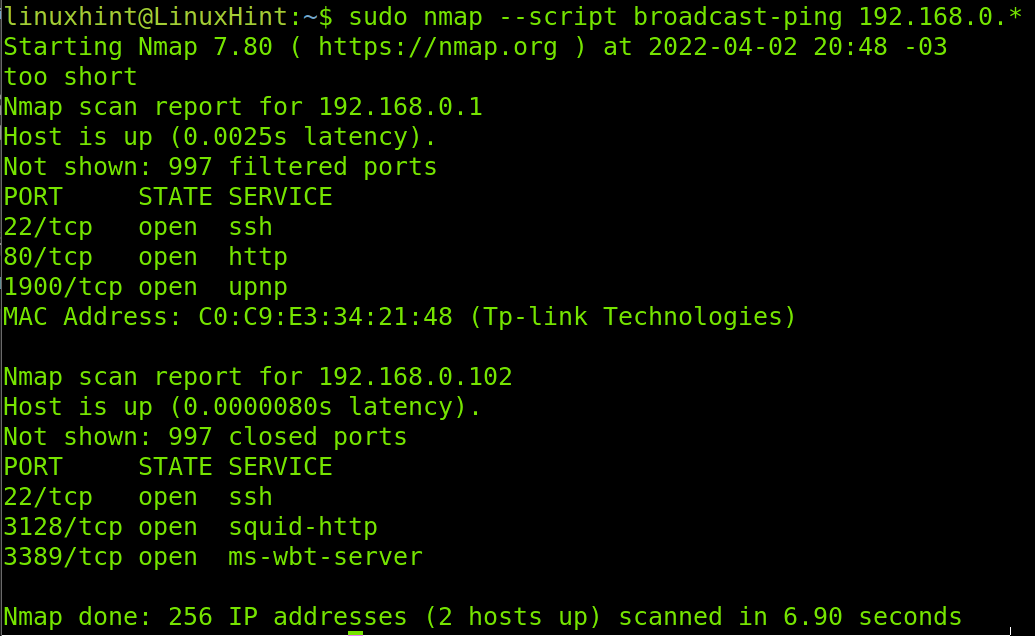
Additionally, to the flags explained above, the NSE (Nmap Scripting Engine) offers a script for host discovery broadcast-ping. The Nmap Scripting Engine (NSE) is a set of scripts to automate scanning tasks. Users can write their own NSE scripts.
This script requires root privileges because it sends RAW packets. Another disadvantage is that not all devices are configured to reply to RAW packets. The output will return additional information on discovered hosts including the MAC address.
The proper syntax to run the broadcast-ping script to detect hosts within a network is shown below.
You also can define different segments for hosts to be discovered.
If you are interested in learning more about this script, visit https://nmap.org/nsedoc/scripts/broadcast-ping.html.
Ping Sweep with fping
The market offers other tools capable of executing ping sweep for host discovery, one of them is fping.
To install fping on Debian based Linux distributions, run the following command.
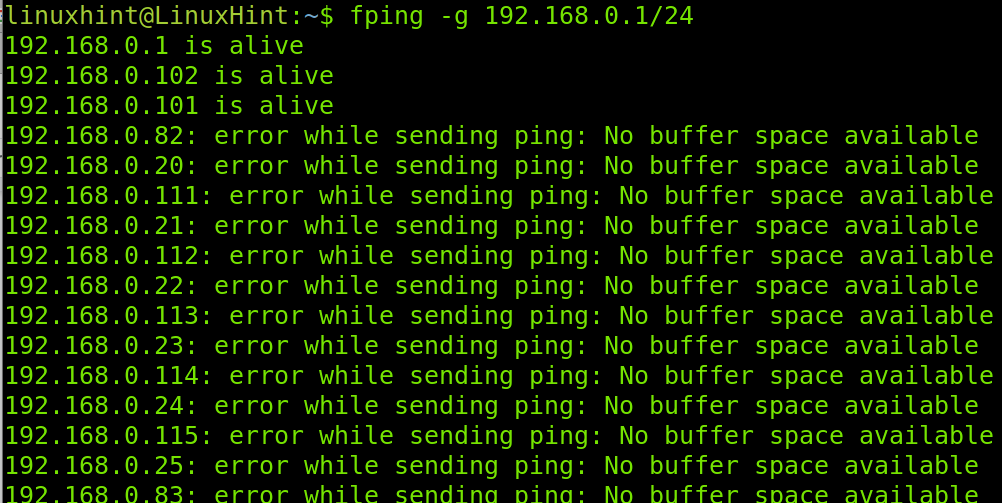
After fping is installed, use the –g flag to discover hosts. This tool is more limited than Nmap, it does not support wildcard nor IP ranges.
That’s all about ping sweep techniques using Nmap, including the fping bonus.
Conclusion
As you can see, executing ping sweep with Nmap is pretty easy and can be done by any user level. Nmap is a formidable tool for this and other purposes, and offers a variety of methods to get a result. Personally, I think Nmap is the most complete tool to audit and diagnose networks. The fping sample is also formidable to show the superiority of Nmap over its alternatives. Nmap can discover live hosts with more accuracy than alternatives specifically designed for this purpose. NSE also allows you to write your own scripts to discover hosts, automating the combination of different flags and scripts, a feature which is not included in many network scanners. Additionally, to the programs shown in this tutorial, the market offers other alternatives like hping.
Thank you for reading this Nmap tutorial to execute ping sweep. I hope it was useful for you. Keep following Linux Hint for more professional tips and tutorials.