If you want to check these sshd logs on your Raspberry Pi system, you should follow this article that provides ways to check for the logs on Raspberry Pi. So, without delay, let’s move straight toward the main process.
How to Check the sshd Logs on Raspberry Pi
There are generally two methods to check the sshd logs on Linux and you can apply those methods in your Raspberry Pi OS to check the login attempts.
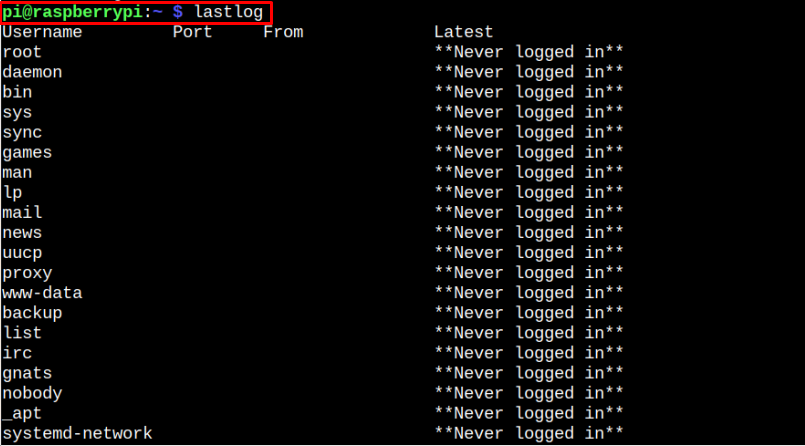
Method 1: Check sshd Logs through lastlog Command
The lastlog command provides you with the logs sessions on your Raspberry Pi system and you can execute this command to check the sshd log easily on your Raspberry Pi terminal.
The output provided may be different in your case since we have only logged in from the pi user.
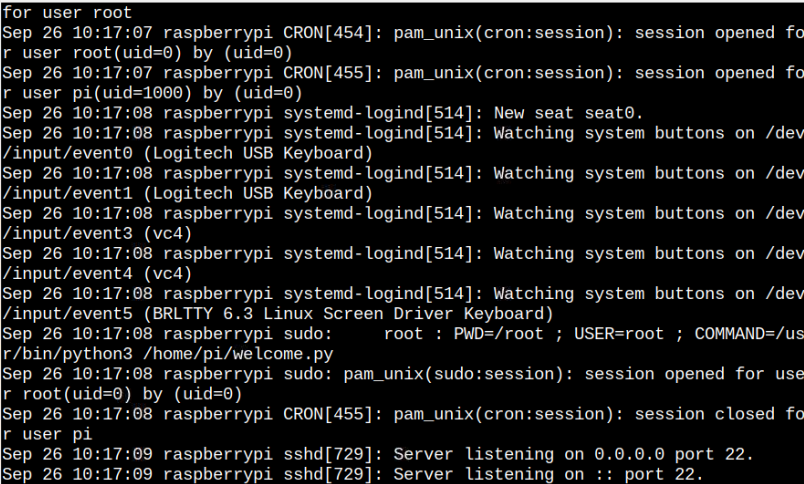
Method 2: Check the Logs through auth.log File
The auth.log file on your system also includes the sshd logs information as it provides detailed information about the login attempt performed on your Raspberry Pi system. You can run this file on the Raspberry Pi system through the “cat” command to see the sshd logs on the terminal.
In case you have difficulty running the above command for permission denied error, you can run the same command with the root user using “sudo”.
Conclusion
Exploring the login attempts on the Raspberry Pi system is beneficial for your device security because you can keep a check on the unauthorized login attempts made to your system. The above two methods are crucial to help you check the sshd logs on your Raspberry Pi system. You can use the “lastlog” command or retrieve the sshd logs information from the auth.log file. Both methods are useful to check for authorized and unauthorized login attempts on your Raspberry Pi system.