- How to check for open ports on Linux remotely with Nmap
- How to check for open ports on Linux locally
- Removing services on Debian 10 Buster
- How to close open ports on Linux using UFW
- How to close open ports on Linux using iptables
- Related articles
How to check for open ports on Linux locally
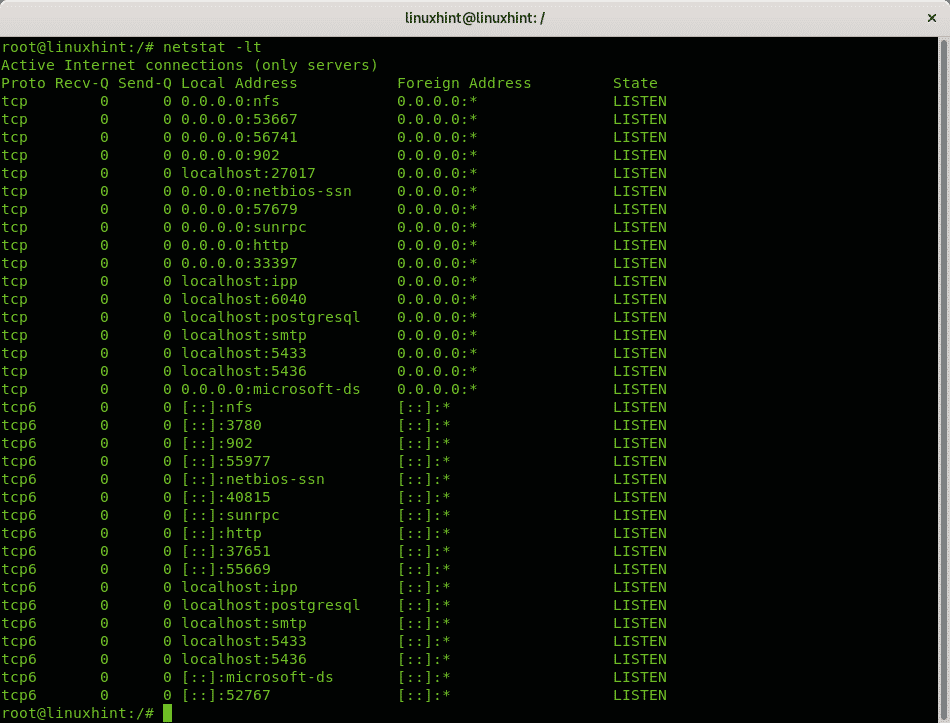
The command netstat is present on all computer OS (Operating Systems) to monitor network connections. The following command uses netstat to show all listening ports using the TCP protocol:
Where:
netstat: calls the program.
-l: lists listening ports.
-t: specifies TCP protocol.
The output is human friendly, well ordered in columns showing the protocol, received and sent packets, local and remote IP addresses and the port state.
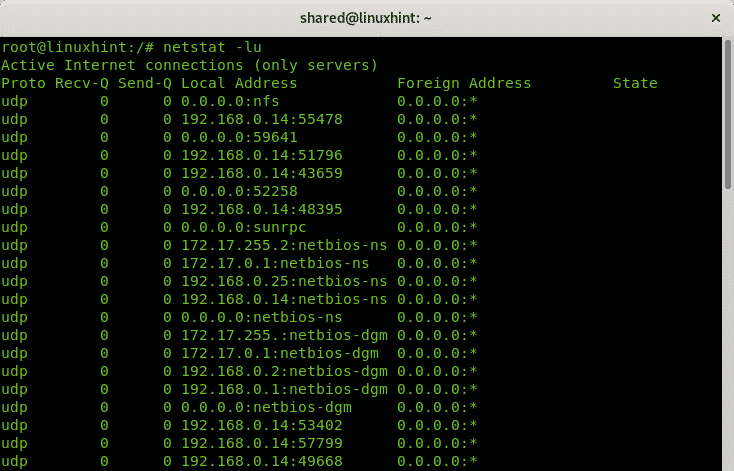
If you change the TCP protocol for UDP the result, at least on Linux, will display only open ports without specifying the state because contrary to the TCP protocol, the UDP protocol is stateless.
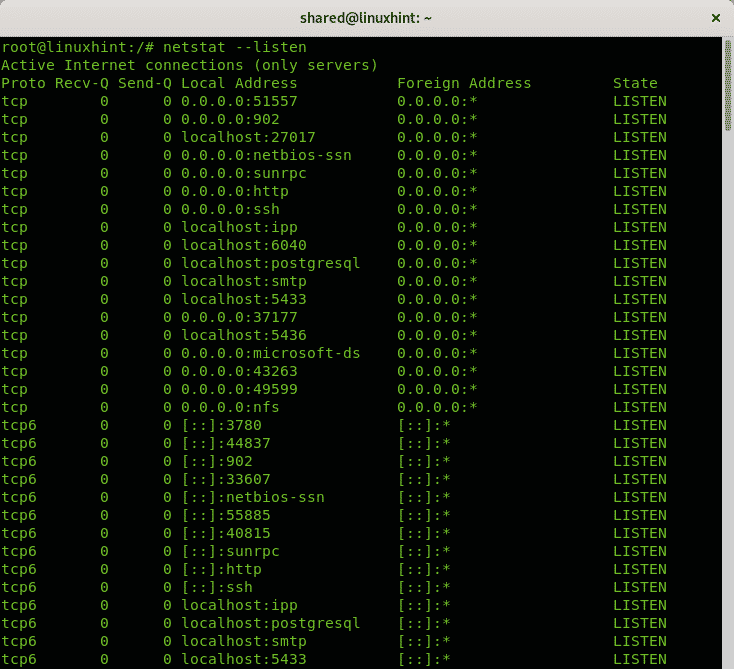
You can avoid specifying protocols and use only the option -l or –listen to get information on all ports listening independently of the protocol:
The option above will display information for TCP, UDP and Unix socket protocols.
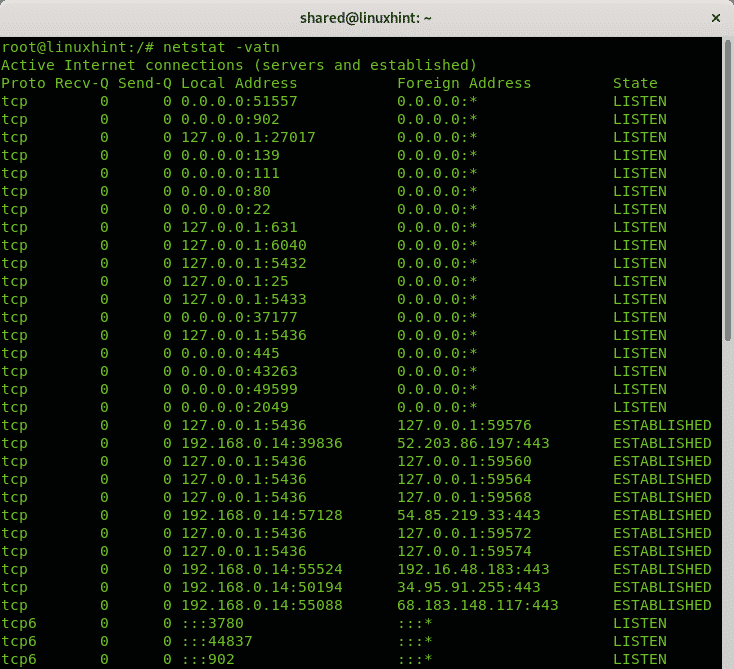
All examples above show how to print information on listening ports without established connections. The following command shows how to display listening ports and established connections:
Where:
netstat: calls the program
-v: verbosity
-a: shows active connections.
-t: shows tcp connections
-n: shows ports in numerical value
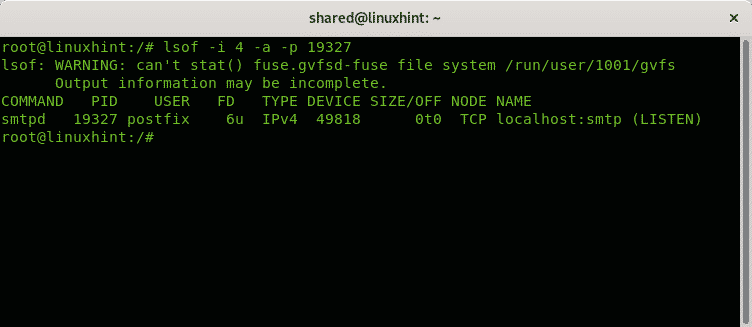
Let’s say you identified a suspicious process in your system and you want to check associated ports to it. You can use the command lsof used to list open files associated to processes.
In the next example I will check the process 19327:
Where:
lsof: calls the program
-i: lists files interacting with internet, the option 4 instructs to print only IPv4, the option 6 is available for IPv6.
-a: instructs the output to be ANDed.
-p: specifies the PID number of the process you want to check.
As you see the process is associated with the listening smtp port.
How to check for open ports on linux remotely
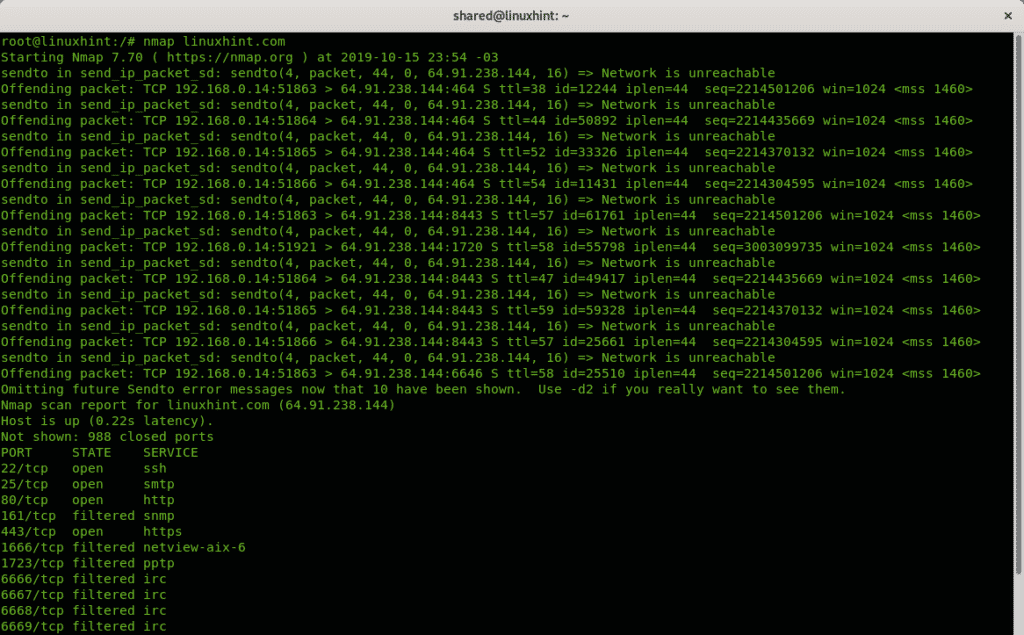
If you want to detect ports on a remote system the most widely used tool is Nmap (Network Mapper). The following example shows a single port scan against Linuxhint.com:
The output is ordered in 3 columns showing the port, the port state and the service listening behind the port.
PORT STATE SERVICE
22/tcp open ssh
25/tcp open smtp
80/tcp open http
161/tcp filtered snmp
443/tcp open https
1666/tcp filtered netview-aix-6
1723/tcp filtered pptp
6666/tcp filtered irc
6667/tcp filtered irc
6668/tcp filtered irc
6669/tcp filtered irc
9100/tcp filtered jetdirect
By default nmap scans the most common 1000 ports only. If you want nmap to scan all ports run:
At the Related Articles section of this tutorial you can find additional tutorials on Nmap to scan ports and targets with many additional options.
Removing services on Debian 10 buster
Additionally to firewall rules to keep your ports blocked removing unnecessary services is recommended. Under Debian 10 Buster this can be achieved with apt.
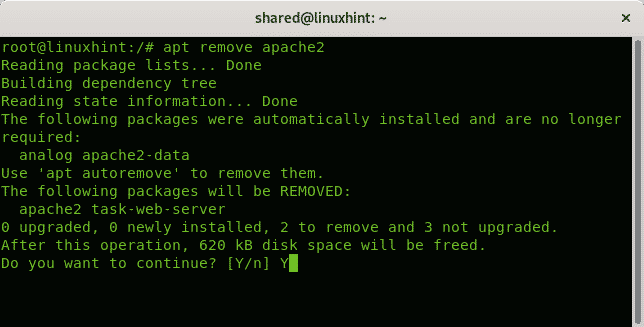
The following example shows how to remove the Apache 2 service using apt:
If requested press Y to end the removal.
How to close open ports on Linux using UFW
If you find open ports you don’t need to be open the easiest solution is to close it using UFW (Uncomplicated Firewall)
There are two ways to block a port, by using the option deny and with the option reject, the difference is the reject instruction will inform the second side the connection was rejected.
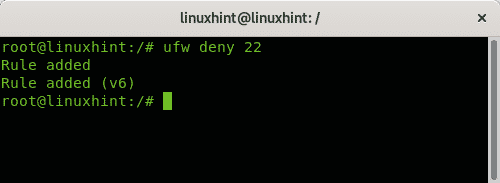
To block the port 22 using the rule deny just run:
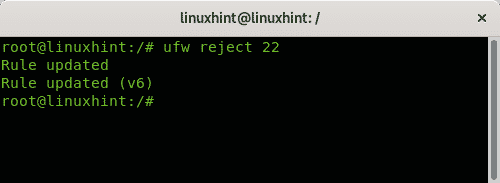
To block the port 22 using the rule reject just run:
On the Related Articles section at the end of this tutorial you can find a good tutorial on Uncomplicated Firewall.
How to close open ports on Linux using iptables
While UFW is the easiest way to manage ports, it is a frontend for Iptables.
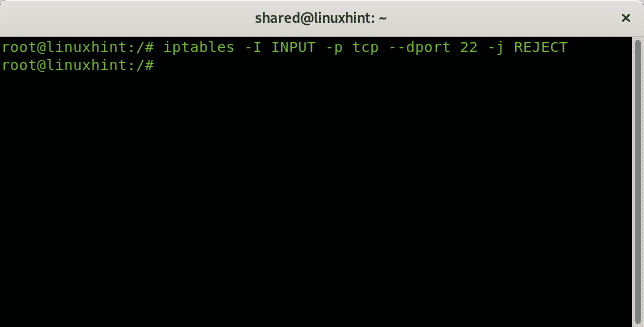
The following example shows how to reject connections to the port 22 using iptables:
The rule above instructs to reject all tcp incoming (INPUT) connections to destination port (dport) 22. Being rejected the source will be informed the connection was rejected.
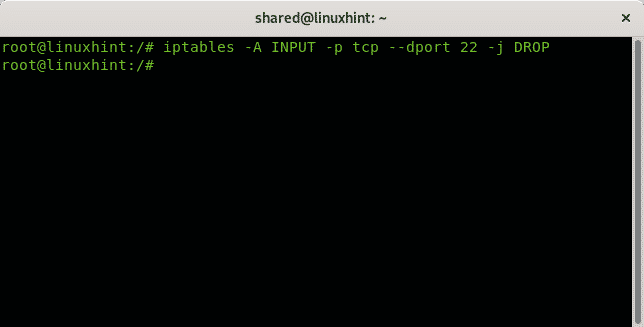
The following rule just drops all packets without informing the source the connection was rejected:
I hope you found this brief tutorial useful. Keep following LinuxHint for additional updates and tips on Linux and Networking.