In Linux, you can hide a directory and file by adding a dot (.) prefix in the filename, for example the .htaccess. This file is not visible to others but can be accessed publicly sometimes. Some objects or content in the web server are used to facilitate the data processing. But often times, there are configuration errors especially in the permissions set which leads to potential vulnerability such as Directory traversal, Sensitive data exposure, Cross-Site Request Forgery (CSRF) attacks, XSS LFI/RFI attack, Unvalidated redirects and forwards, and many more.
We will learn the following topics in detail:
- Brute Force Attacks
- Wordlists File in Kali Linux
- Find Hidden Objects on a Website
Brute Force Attacks
Brute force is a type of cyber-attack method that relies on a wordlist. Brute force is specifically applied in many areas of cyber-attacks such as fuzzing, cracking, and credential login. A Wordlist is a plain text file which contains a collection of words such as usernames, passwords, objects, and directories.
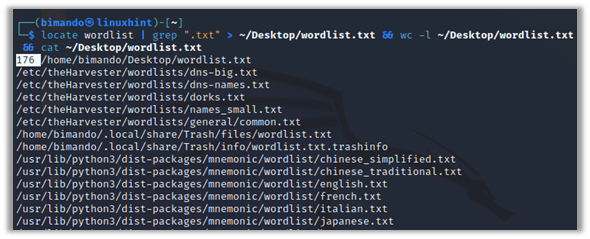
You can find the wordlists freely on the internet. The most popular wordlist that is used by penetration testers is SecLists. You can download the files at GitHub at https://github.com/danielmiessler/SecLists. Kali Linux also comes with a bunch of prebuilt wordlists. You can find the wordlists file in your Kali Linux using this command:
My Kali Linux machine has 176 plain text wordlist files as shown in the following figure:
DIRB – Directory Buster in Kali Linux
Dirb is a preinstalled Kali Linux tool which is used to enumerate the web server directories and objects. Dirb searches for content by fuzzing the URL on the target website based on a wordlist that is prepared beforehand or, in other words, using the Brute Force technique. Dirb analyzes and displays the response code which is provided by the target website. The response code 200 means that the object exists.
DIRB – Commands and Usage
Let’s first take a look at the available Dirb commands and the usage in the following examples.
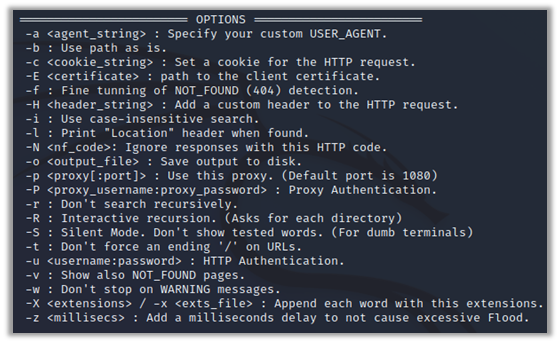
Now, analyze the most interesting options in the following:
Define a Custom USER_AGENT
Some web server uses firewall technology to filter the request to the server. One of the most frustrating things as a penetration tester is when we perform crawling or brute force. The firewall catches our request as a bot, then it blocks the requests. There are several features of Dirb to evade the firewall detection. The first point to evade the firewall is to define a legitimate user agent instead of a Dirb default user agent. You can find a list of user agents on the internet. For example, you can find it at https://developers.whatismybrowser.com/useragents/explore/.
To define a user agent when using Dirb in the Kali Linux terminal, use the following argument:
Add a Delay to the Request
Dirb does the request simultaneously, one request after another. Using this default request speed sometimes causes the request flooding to the server. Some firewalls may block our request immediately when they catch the flood request. To avoid that, we could define a delay in milliseconds format. A thousand milliseconds mean one second.
Using a Non-Recursive Request
The main purpose to use this option is basically the same as adding a delay to the request. Yes, it is to bypass the firewall detection. Use the -r switch to enable this option.
Don’t Stop on a Warning Message
Activating this option tells Dirb to keep sending the request whatever it takes until the last word in a wordlist. Use the -w switch to enable this option.
Logging
Saving the output result to a file is important; we don’t remember everything, right?
How to Use Dirb in Kali Linux
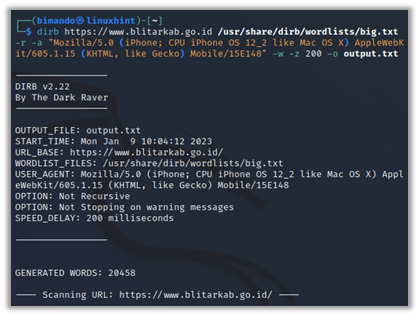
From the information about the command and the usage in the previous examples, the following is my favorite command for using Dirb:
Note that the milliseconds number in delaying the request may vary. You need to do a trial test before that.
Based on the previous command pattern, the actual command should be like this:
| URL TARGET | https://www.blitarkab.go.id |
| WORDLIST FILE | /usr/share/dirb/wordlists/big.txt |
| USER_AGENT | Mozilla/5.0 (iPhone; CPU iPhone OS 12_2 like Mac OS X |
| TIME DELAY | 200 milliseconds |
| OUTPUT FILENAME | output.txt |
From the previous Dirb scans, we get some interesting results such as:
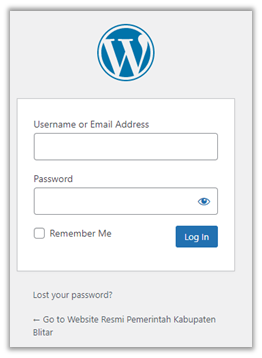
The WordPress administrator login page at https://www.blitarkab.go.id/admin which is redirected to https://www.blitarkab.go.id/wp-login.php.
The cPanel login page at https://www.blitarkab.go.id/cpanel which is redirected to the actual cPanel web service page at https://www.blitarkab.go.id:2083/.
The WHM Login page at https://www.blitarkab.go.id:2087/.
And a webmail login page at https://www.blitarkab.go.id:2096/.
Now, we could brute force those credential pages in the next stage.
Conclusion
We covered how to find the hidden objects and directories using Dirb in Kali Linux. We also found two credential login pages for WordPress CMS and cPanel. Those pages are not meant to be accessed publicly.