WordPress is the number one popular Content Management System (CMS) in the world. If you wonder what CMS is. I would like to make this simple analogy. In building a website, initially, we could achieve that using hard code with HTML, JavaScript, and CSS. It is like running a Kali Linux program in the terminal or command-line interface. It is inconvenient if you have zero knowledge about that programming language.
CMS platforms such as WordPress, make it easy for us. It is like running a GUI version Kali Linux program. You only need to click on things like that. WordPress allows the web admin with no technical skill or web programming language knowledge to focus on building content. It also has an enormous number of themes and plugins. But sometimes, there are vulnerabilities found in WordPress itself, the themes, and the plugins.
We will learn the following topics in detail:
- Get the API token of WPScan
- Identify the WordPress version of the target
- Enumerate a WordPress Theme
- Enumerate WordPress Plugins
- Enumerate a WordPress User
- Scan the WordPress, theme, and plugins vulnerabilities
PREPARATION
WPScan is free and already pre-installed in Kali Linux. But if you do not have WPScan on your machine, you could install it either using apt install or downloading it at GitHub at https://github.com/wpscanteam/wpscan. Even though WPScan is an open-source tool in Kali Linux. But there is a difference between WPScan and other free tools. To be able to use the WPScan vulnerability scanner requires a little extra work, we need a WPScan API token. It is free, you only need to create an account at https://wpscan.com.
- Register an account at https://wpscan.com by clicking the Get started button on the top corner.
Figure . WPScan.com sign up
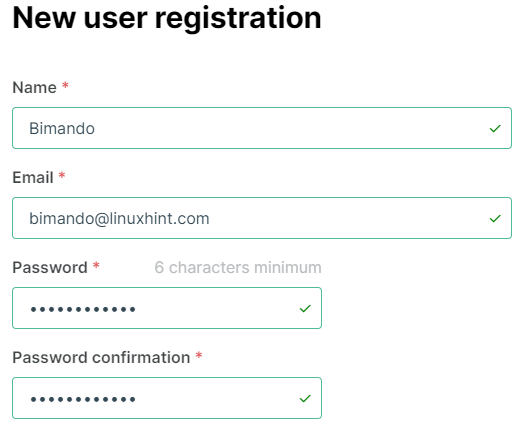
Then, fill in any required information on the new user registration form as shown below.
Figure . WPScan.com user registration form
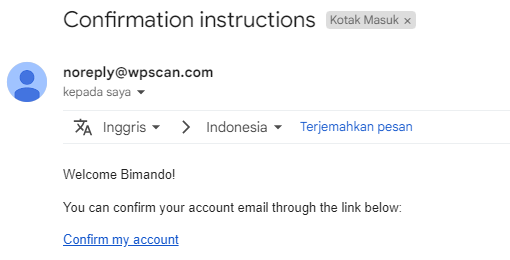
- Once you submit your registration information, you need to confirm your email account. Open up your mailbox and click on the confirmation link sent by wpscan.com.
Figure . WPScan email confirmation
- Once your email confirmation is successful, then click on your Profile menu.
Figure . WPScan.com Profile menu
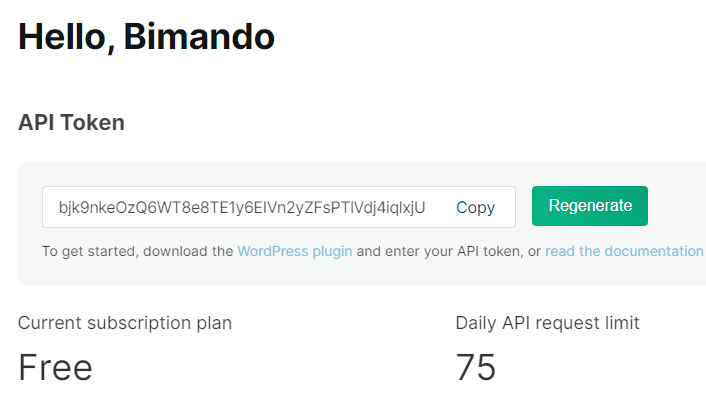
You will see your API token as shown figure below. Copy that token and save it to a file. We will use it later on the terminal.
Figure . WPScan.com API token value
Before we jump into the WPScan tutorial in Kali Linux, I would like to introduce what information you could get on wpscan.com. The developer is taking this tool more seriously, not just building a free tool. Their work is very interesting.
WPScan Service Status
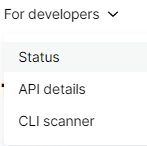
On the WPScan dropdown menu bar entitled For Developer, there is a page linked to monitoring the Status of the WPScan system operational.
Figure . WPScan.com For Developers menu
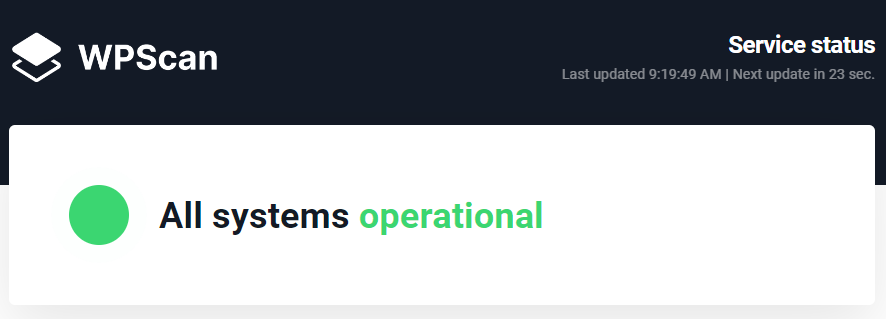
This report is important when we conduct a penetration test and we may be facing some errors. In case when you found an error while running WPScan on Kali Linux, you first ensure whether the system is online by visiting https://status.wpscan.com/.
Figure . WPScan.com service status
When everything is running well, you will see a status like the figure above.
WPScan – WordPress CMS Vulnerability
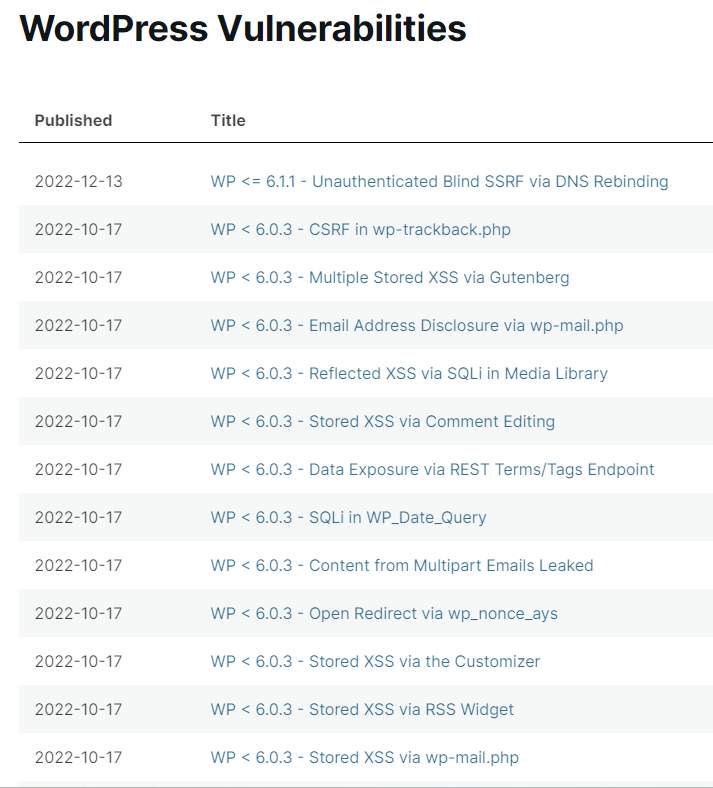
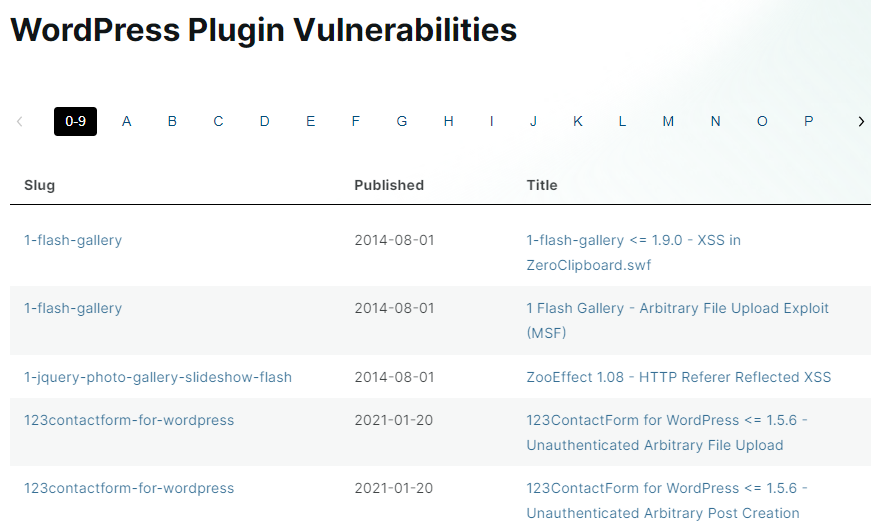
WPScan also publishes information about WordPress Vulnerabilities found for every version.
Figure . WordPress vulnerabilities
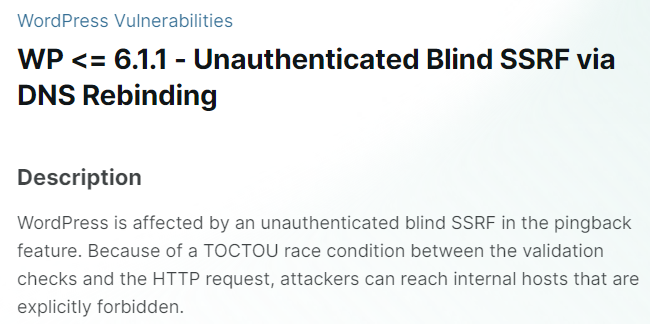
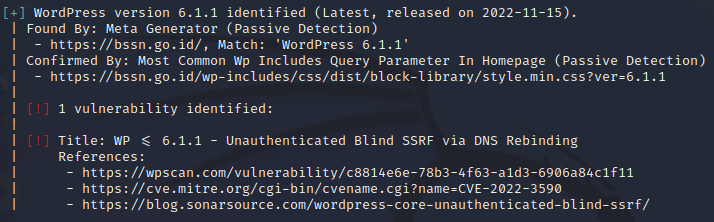
You can read the detailed information for every vulnerability in the list. For example, the following figure shows that WordPress version 6.1.1 or below has a vulnerability on unauthenticated blind SSRF via DSN rebinding.
Figure . WordPress 6.1.1 vulnerability information
WPScan – WordPress Theme & Plugin Vulnerability
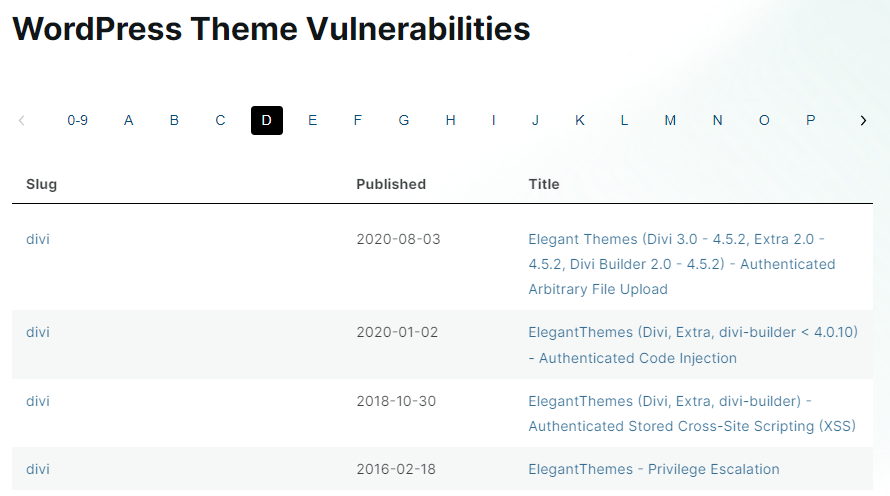
WPScan also publishes the theme and plugin vulnerability information.
Figure . WordPress theme vulnerabilities
Figure .WordPress plugin vulnerabilities
WPScan Tutorial on Kali Linux
I assume you have already installed WPScan and the API token. First, let us see the available command and the usage of WPScan. Run the following command to display the full information.
Figure . WPScan on Kali Linux terminal
WPScan provides firewall evasion using a user agent randomization for each scan using the following argument.
I also often add the “–force” flag so that WPScan will continue to scan if the index raises a 403 error code or a forbidden error.
To enable the vulnerability scanner feature, we should define our API token by using the following argument:
WPScan supports logging in three different formats: JSON, CLI, and CLI with no color. You could save the output of your WPScan result by defining the output filename followed by the format using the following command:
-f or --format [FORMAT]
From the WPScan command that we learned above, we will try to scan some WordPress targets and enumerate the users, vulnerability plugins, and vulnerability theme. To do the enumeration we should use the following argument:
The available options for our objective are:
| u | Enumerate users |
| vp | Enumerate vulnerable plugins |
| vt | Enumerate vulnerable themes |
Now, let us set the target to https://bssn.go.id and scan the vulnerability with WPScan. To run a WPScan with the default options settings, you can simply run the following command:
First, WPScan will identify the WordPress version and the vulnerability found and the rest of it depends on the enumerated options we are using.
Figure . WordPress 6.1.1 vulnerability
As shown in the figure above, our target has a WordPress version 6.1.1 which is vulnerable to Unauthenticated Blind SSRF via DNS rebinding. The detailed information is shown earlier in figure 9 above.
WPScan Enumerate Users
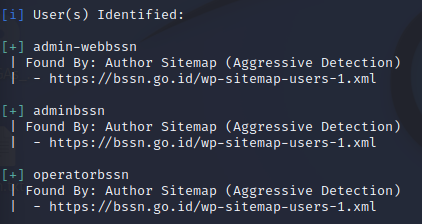
Figure . WordPress users enumeration
The target bssn.go.id has three users: admin-webbssn, adminbssn, and operatorbssn.
WPScan Enumerate Plugins Vulnerabilities
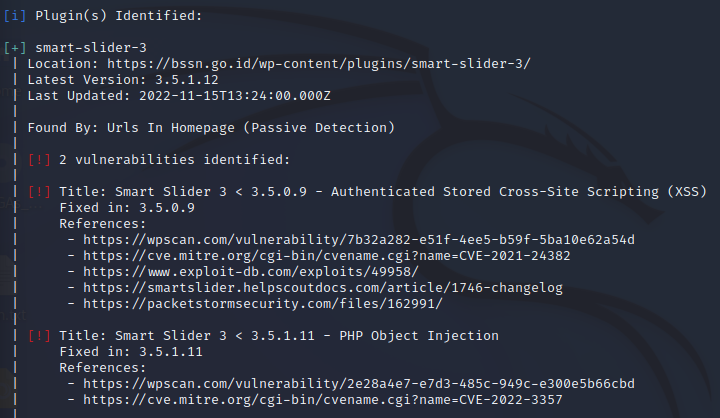
Figure . WordPress plugin vulnerability enumeration
The target has two plugins vulnerability as shown in the figure above. One of them, the PHP object Injection sounds interesting.
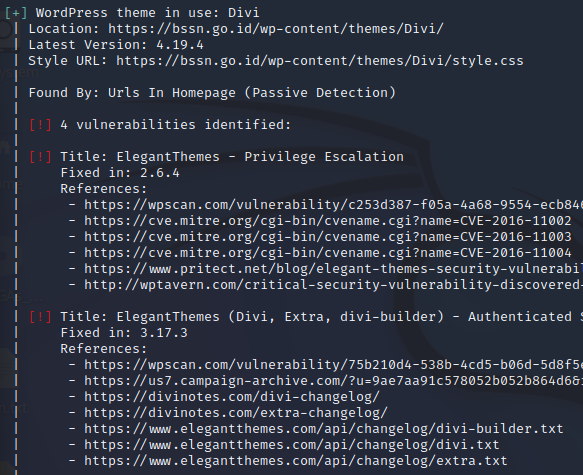
WPScan Enumerate Themes Vulnerabilities
Figure . WordPress theme vulnerability enumeration
Our target now has four theme vulnerabilities and one of them has a critical vulnerability, which is Privilege Escalation.
CONCLUSION
We learned how to do vulnerability scanning on a WordPress website. Note that the vulnerability we have found in this tutorial has not been validated. In the web application information gathering stage, we collect all information and the possible vulnerabilities. Then, from that reconnaissance, we need to do a vulnerability assessment to verify whether the target could be hacked.
For your information, our target above, a BSSN is an Indonesian government agency that is under and responsible to the President. BSSN has the task of carrying out government duties in the field of cyber security and ciphers to assist the President in administering government functions. Just imagine, how can a state agency in the field of cyber security have such vulnerabilities.