We will learn the following topics in detail:
- Identify the technology behind a website
- Identify whether a website is using certain a Content Management System
- Google Hacking or Google Dorking
- Find information about the vulnerability and exploit in a web application
WhatWeb
GitHub: https://github.com/urbanadventurer/WhatWeb
Figure 1. Whatweb official banner
WhatWeb is an awesome scanner to fingerprint web application technologies including Content Management Systems (CMS), JavaScript libraries, web servers, embedded devices, version numbers, email addresses, account IDs, web framework modules, and more. WhatWeb is written in the Ruby language. WhatWeb has 1822 plugins (the number keeps growing). It is open-source and is already installed in Kali Linux. If you do not have Kali Linux, you can download the WhatWeb at GitHub.
WhatWeb is my other favorite tool when performing web application information gathering in Kali Linux. It is simple but displays so much valuable information.
Let’s take a look at the WhatWeb command in the following Kali Linux terminal:
Figure 2. Whatweb in Kali Linux terminal
WhatWeb Target Selection
WhatWeb supports various target selections method such as fixed single or multiple URLs:
A single hostname or IP address:
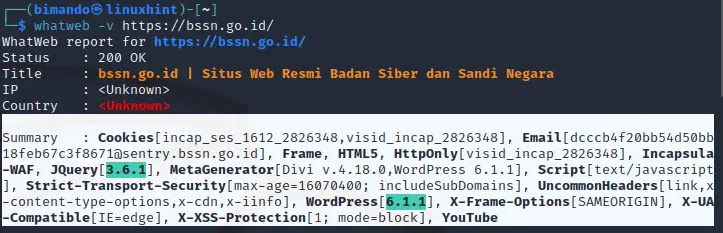
Figure 3. Whatweb report on bssn.go.id
Multiple IP addresses in a range with CIDR format:
Whatweb 175.106.20.1-255
For a file which contains an IP address range in CIDR format, you need to add a -i / –input-file=[FILE] argument:
WhatWeb Aggression Level
WhatWeb, by default, runs in stealthy mode. It is the fastest because it only requires one HTTP request of a website. For penetration testing purposes, the user could set the aggression level of the scan to a more aggressive mode or intensive by adding the -a 4 (-a means using heavy aggression mode, -a 1 is using a stealthy mode which is the default mode) parameter.
WhatWeb Change User Agent
Whatweb, by default, defines its user-agent with “WhatWeb/0.0.5”.
You can explore more user-agents lists on this website:
https://developers.whatismybrowser.com/useragents/explore/
WhatWeb Proxy
You can also hide your identity using a proxy. There is a lot of free proxy servers on the internet. To use an open proxy, add the following argument:
By default, the proxy port is 8080. If you are using a private proxy that needs authentication, you can add the –proxy-user [username:password] argument:
WhatWeb List Plugins
If you are wondering what are those 1.824 plugins that WhatWeb use, you can see it using –list-plugins or -l switch.
Figure 4. Whatweb plugins list
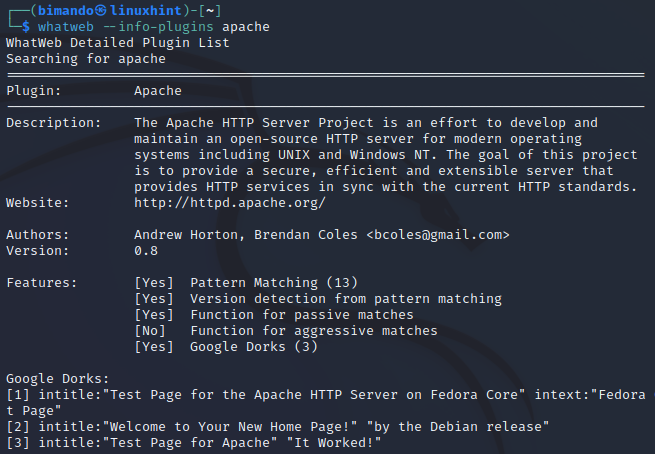
To see the detailed information of certain plugins, run the following command:
Figure 5. Whatweb plugins detailed information
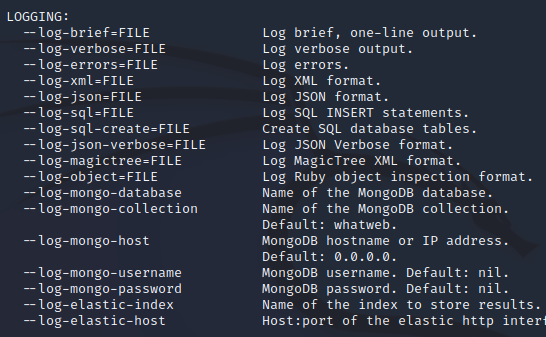
WhatWeb Logging
WhatWeb provides different methods and file format to save the output. They are: verbose output, errors log, XML format, JSON format, SQL INSERT statements, JSON verbose format, and MongoDB output.
Figure 6. Whatweb logging
CMSeeK
GitHub: https://github.com/Tuhinshubhra/CMSeeK
Figure 7. CMSeeK official banner
CMSeeK is a content management system (CMS) detection tool that is built in Python. It has a module to scan 170 different CMS such as WordPress, Joomla, Drupal, and many more. What makes CMSeeK more interesting is that it could detect the CMS version, user enumeration, plugin enumeration, theme enumeration, user detection, find available vulnerabilities based on CMS version, and many more.
Installing CMSeeK in Kali Linux
CMSeeK is not pre-installed by default in Kali Linux. First, you must install it in your Kali Linux using the apt install command or you can also download it at GitHub using the recently provided link.
Figure 8. Installing CMSeeK
CMSeeK offers two methods of using it – they are guided or using arguments. Once you successfully install the CMSeeK, let’s take a look at following CMSeek command usage:
CMSeek Target Specifying
Scan a single URL:
cmseek --url [URL]
Scan multiple URL which are stored in a file that contains a list of URL target which is formatted with separated comma:
cmseek --list [LIST]
CMSeek User-Agent
You can also modify the user agent in CMSeeK. There are three different options available: random user agent, a Googlebot user agent, or a custom user agent.
cmseek --googlebot
cmseek --user-agent USER_AGENT
CMSeeK doesn’t provide a logging option. But don’t worry, we could achieve that with a redirection operator (‘>>’).
CMSeeK in Action
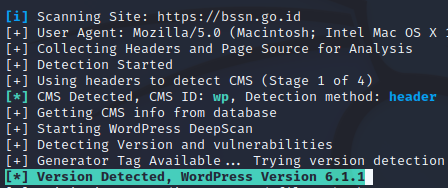
Let’s run the CMSeeK and see the result. Here, we scan the https://bssn.go.id CMS using CMSeeK in Kali Linux terminal using the following command:
Figure 9. CMSeek scans bssn.go.id
From the previous command, we could identify the arguments used:
| -v | Turn on verbose mode. |
| -r | Use a random USER_AGENT. |
| >> [OUTPUT] | Redirect the output to a file. |
Note that using the redirection operator, you will not see anything on the terminal. Instead, it is redirected to the file that you specified. Let’s check the file using the cat command:
From the previous CMSeeK command, we get the following information such as:
CMS NAME & VERSION
Figure 10. CMSeeK identify CMS name & version
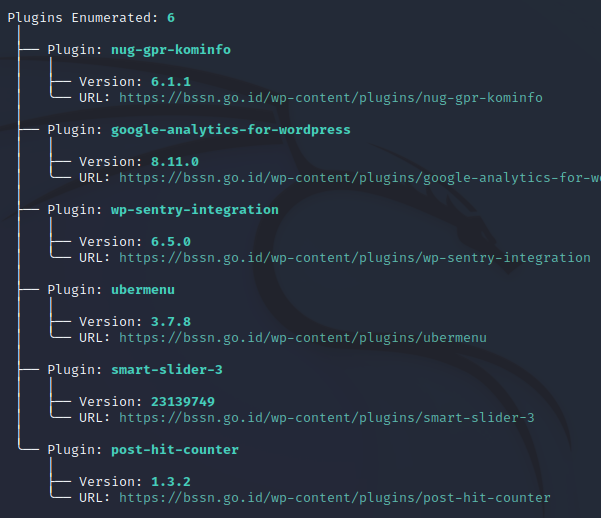
CMS PLUGINS
Figure 11. CMSeeK identify WP plugins
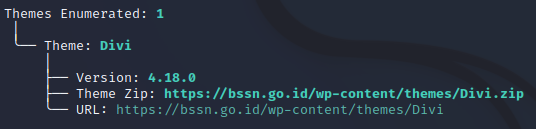
CMS THEME
Figure 12. CMSeeK identify WP theme
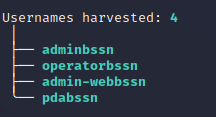
USERS
Figure 13. CMSeeK enumerate WP users
Conclusion
CMSeek is a very powerful tool to do an information gathering, especially on CMS. Once you successfully identified the CMS, you can do the vulnerability scanning and assessment using another tool. For the purpose of scanning a certain CMS, Kali Linux has several CMS vulnerability scanner tools such as:
- WPScan for WordPress. Download at GitHub at https://github.com/wpscanteam/wpscan (Pre-installed in Kali Linux)
- Droopescan for Drupal. Download at GitHub at https://github.com/SamJoan/droopescan
- Drupwn for Drupal. Download at GitHub at https://github.com/immunIT/drupwn
- Joomscan for Joomla. Download at GitHub at https://github.com/OWASP/joomscan