There are a lot of information-gathering tools in Kali Linux. In this tutorial, we will learn specifically about web application information gathering such as Whois, Whatweb, NSLookup, and CMSeek. Those tools are open-source and already pre-installed in Kali Linux. If you do not have Kali Linux, you could download or check those tools projects at GitHub. Links will be provided in each tool section below.
Information gathering can be broken into two methods: active information gathering, and passive information gathering. Active information gathering is when the hacker is making a contact with the target. For example, using a crafted payload to assess how a certain web application would respond. While passive information gathering, the hacker uses a third-party program to do the work, for example using the OSINT technique to gather a lot of information available on the internet. From that simple definition, you would immediately know what information gathering tools we are going to use below are being categorized.
We will learn the following topics in detail:
- Kind of information collected during the information gathering phase
- Ownership detail information of a domain name
- Identify the name server IP address
Before a penetration tester conducts information gathering, they first define the target. Different target categories use different techniques and proper tools. For example, if your target is a wireless network, any techniques used in gathering information about web applications may not be applied.
Information Gathering Objective
- Domain Name Server (DNS) records
- Detect whether the website is behind a firewall
- Network hosts, opened ports, and services
- The Operating System
- Secure socket layer protocol
- Enumerate users, email addresses, and or email server
Web Application Information Gathering Tools in Kali Linux
Kali Linux is a powerful Linux Distribution that provides open-source tools for various tasks related to information gathering.
WHOIS
GitHub: https://github.com/rfc1036/whois
WHOIS is a TCP-based transaction-oriented query and response protocol that is widely used to provide information about the ownership of the domain name such as registration date or domain creation date and expiration date, name servers, and registrant contact information (address, phone, and mail). Some of the domain registrar providers or companies might offer a service to hide registrant information.
Whois is pre-installed in Kali Linux, it also can be found on the internet. I often use Whois in Kali Linux and Whois online to see if there are any differences in information between them. In this tutorial, we will cover whois in Kali Linux, for sure.
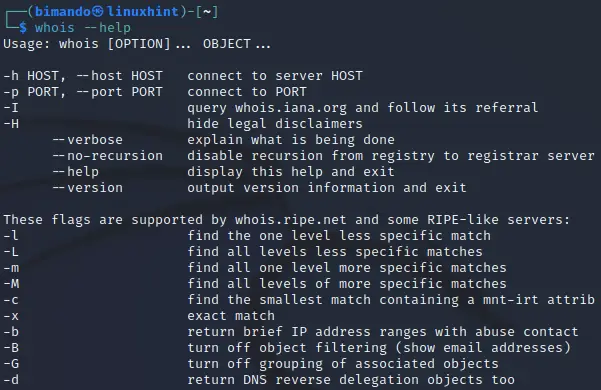
Let us take a look at Whois command usage in the Kali Linux terminal below:
Figure . Whois command usage in Kali Linux
To run Whois in Kali Linux, type the following command pattern:
You can add ‘–verbose’ to the end of the command to display more detailed information. Remember to type [domain-name] without the protocol type, neither HTTP nor HTTPS. For example,
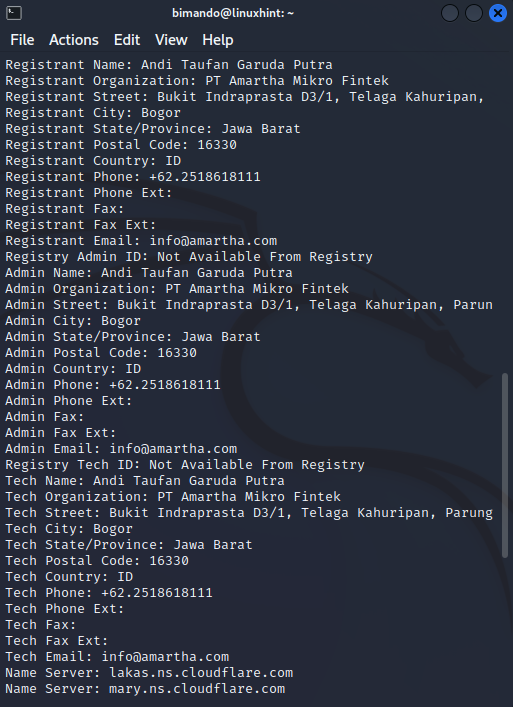
The example below is the domain information output using whois that is publicly open, we are going to run it on amartha.com.
Figure . Whois registrant info
As shown above, we could gain so much detailed information about domain name ownership of amartha.com such as the creation date, registrant name, address, phone number, and email address.
To save the information from the terminal output or text file you can add an output redirection operator (‘>>’) followed by the file name and type. Using this operator at the end of every command means that any output which is meant to be displayed on the terminal will also be saved to a text file.
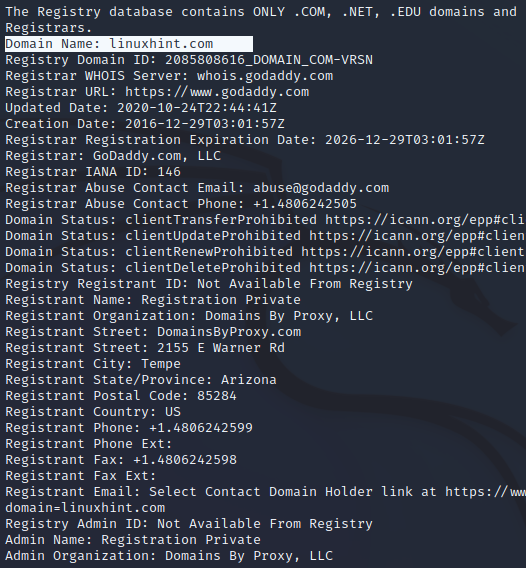
Now, take a look at how the domain name registrant is using a private service to display their Whois information. For this example, let us check linuxhint.com.
Figure . Whois registrant info
From the output above, Whois tells us that the linuxhint.com registrant name is protected or hidden using a private service.
NSLookup
NSlookup short for Name Server Lookup is a network administration tool to query internet domain name system details such as IP address record, MX record (mailing server), Name Servers, SOA record (start of authority), and TXT record. NSLookup is a standard program for every operating system. NSLookup also comes with an online version. There are so many websites that provide an NSLookup program.
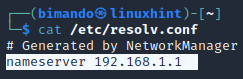
NSlookup can be run in two modes: interactive mode and non-interactive mode. To enter Interactive mode, you only need to run NSlookup with no arguments given (then your computer’s default name server is displayed). The default name server in your Kali Linux is stored in /etc/resolved.conf as shown below.
Figure . Kali Linux DNS records file
The name server of my Kali Linux machine is my local router IP address, which is the actual domain name server is my ISP name server itself.
NSlookup Interactive Mode
NSlookup interactive mode is activated when you run NSlookup without any argument supplied.
Figure . NSLookup interactive mode
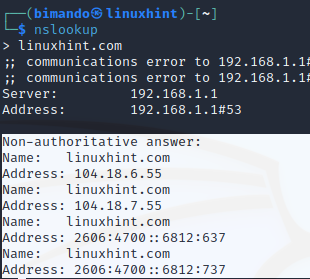
Find the IP address of the domain name, just input the hostname or domain name.
Figure . NSLookup
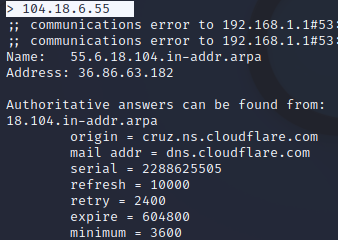
Reverse DNS lookup by typing the IP address as an argument to nslookup. Let us input the IP address of linuxhint.com above.
Figure . NSLookup reverse DNS
From the information above, It is clear that linuxhint.com is behind a firewall service, Cloudflare.
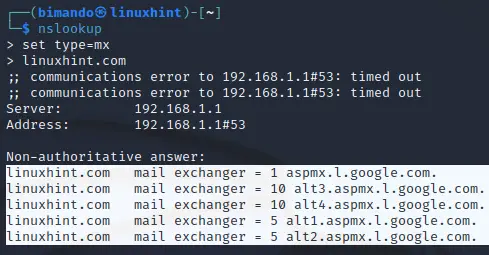
Enumerate the MX records (the mail servers that are responsible for managing incoming email messages on behalf of a recipient’s domain), by adding the following argument before inputting the domain name.
Figure . NSLookup MX records
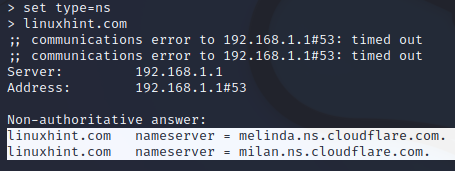
Enumerate the NS records, by adding the following argument before inputting the domain name.
Figure . NSLookup Name Servers records
To exit NSlookup interactive mode just simply type ‘exit’.
NSlookup Non-interactive Mode
The non-interactive mode is activated when you specify the query for what record you are looking for. For example:
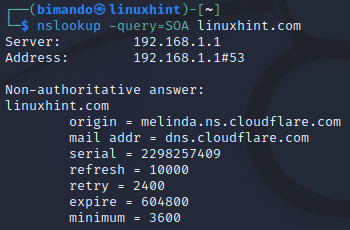
Enumerate the SOA record (start of authority) this record stores authoritative information about a domain or zone such as the email address of the administrator, the recent domain being updated, and the time between refreshes the server should wait.
Figure . NSLookup non-interactive mode
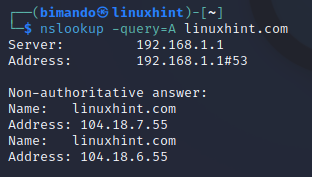
Enumerate the A record which is a DNS record that points a domain or subdomain to an IP address of the hosting server.
Figure . NSLookup A records
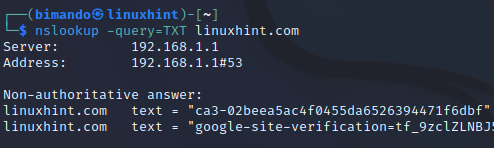
Enumerate the TXT Record. It is a DNS record type that is used to store information in the form of text on your hosting domain.
Figure . NSLookup TXT records
CONCLUSION
Whois and NSLookup are powerful information gathering tools in Kali Linux. It gives you so much detailed information about your target domain name. You should not skip this process because of several reasons. One, you are lucky if you could get open-public registrant information. Second, if you found that the target is behind a firewall, you need to evade or bypass that firewall. You would not set a firewall as your target, right?