[adthrive-in-post-video-player video-id=”hHPNWlFt” upload-date=”2020-07-07T13:36:50.000Z” name=”Top Sniffing and Spoofing Tools Kali Linux 2020.1″ description=”Top Sniffing and Spoofing Tools Kali Linux 2020.1″ player-type=”collapse” override-embed=”true”]
dnschef
The dnschef tool is a DNS proxy for analyzing malware and penetration testing. A highly configurable DNS proxy, dnschef is used for analyzing network traffic. This DNS proxy can fake requests and use these requests to be sent to a local machine, instead of a real server. This tool can be used across platforms and has the capability to create fake requests and responses based on domain lists. The dnschef tool also supports various DNS record types.
In circumstances where forcing an application to user another proxy server is not possible, a DNS proxy should be used instead. If a mobile application ignores HTTP proxy settings, then dnschef will be able to trick applications by forging the requests and responses to a chosen target.
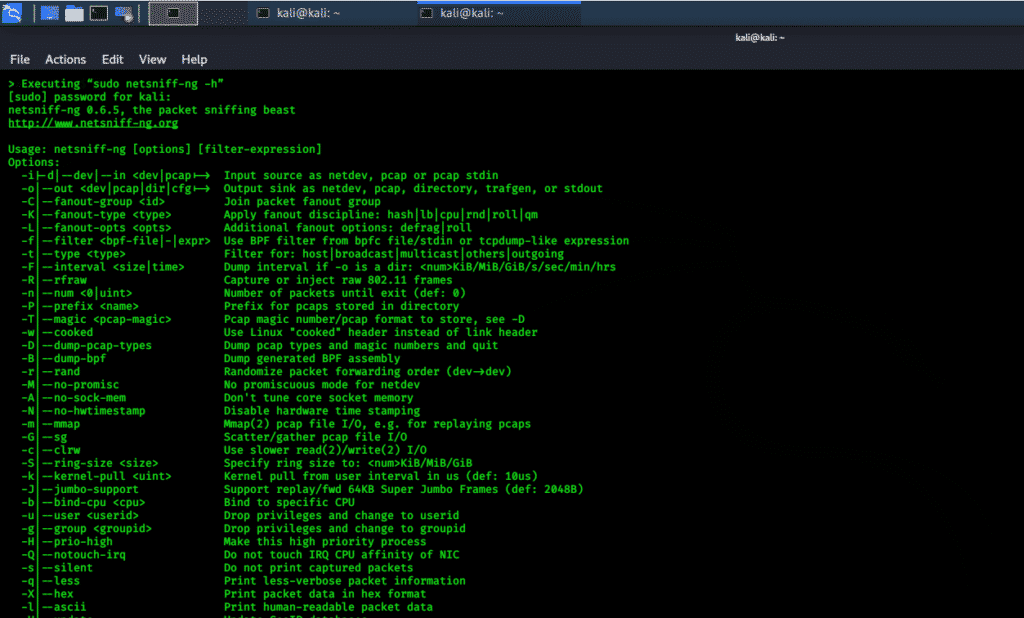
netsniff-ng
The netsniff-ng tool is a fast, efficient, and freely available tool that can analyze packets in a network, capture and replay pcap files, and redirect traffic among different interfaces. These operations are all performed with zero-copy packet mechanisms. The transmission and reception functions do not require a kernel to copy packets to user space from kernel space and vice versa. This tool contains multiple sub-tools inside of it, such as trafgen, mausezahn, bpfc, ifpps, flowtop, curvetun, and astraceroute. Netsniff-ng supports multithreading, which is why this tool works so quickly.
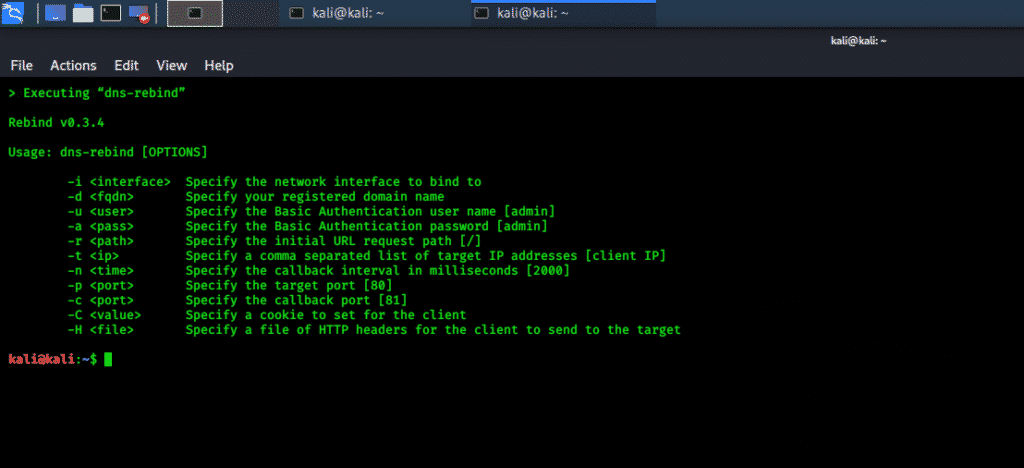
rebind
The rebind tool is a network spoofing tool that performs a “multiple record DNS rebinding attack.” Rebind can be used to target home routers, as well as non RFC1918 public IP addresses. With the rebind tool, an external hacker can gain access to the internal web interface of the targeted router. The tool works on routers with a weak-end-system model in their IP-Stack and with web services that are bound to the router’s WAN interface. This tool does not require root privileges and only requires a user to be inside the target network.
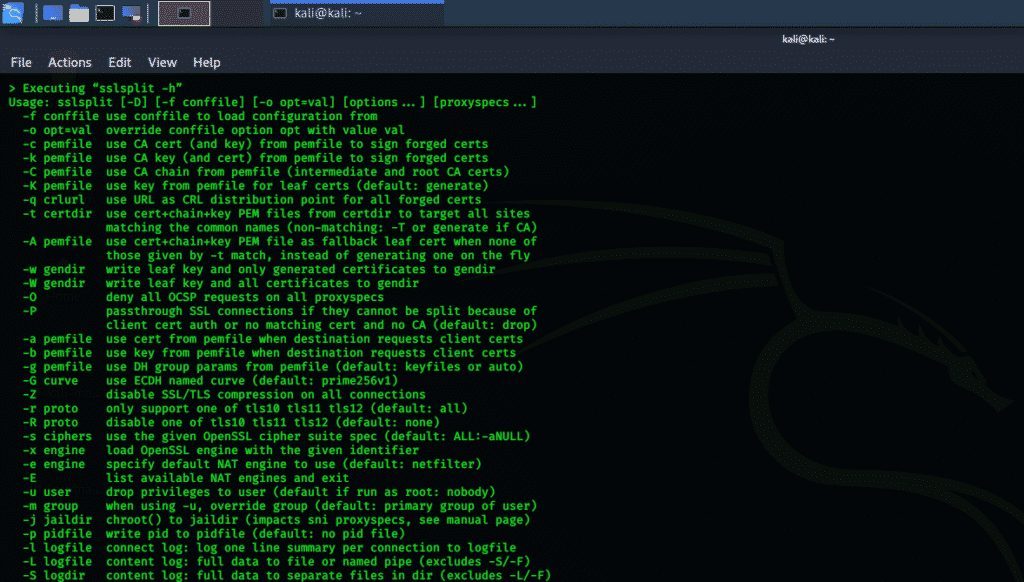
sslsplit
The sslsplit tool is a Kali Linux tool that acts against SSL/TLS encrypted network connections by using “man in the middle” (MIMT) attacks. All connections are intercepted through a network address translation engine. SSLsplit receives these connections and proceeds to terminate the SSL/TLS encrypted connections. Then, sslsplit originates a new connection to the source address and logs all the data transmissions.
SSLsplit supports a variety of connections, from TCP, SSL, HTTP, and HTTPS, to IPv4 and IPv6. SSLsplit generates forged certificates based on the original server certificate and can decrypt RSA, DSA and ECDSA keys, as well as remove public key pinning.
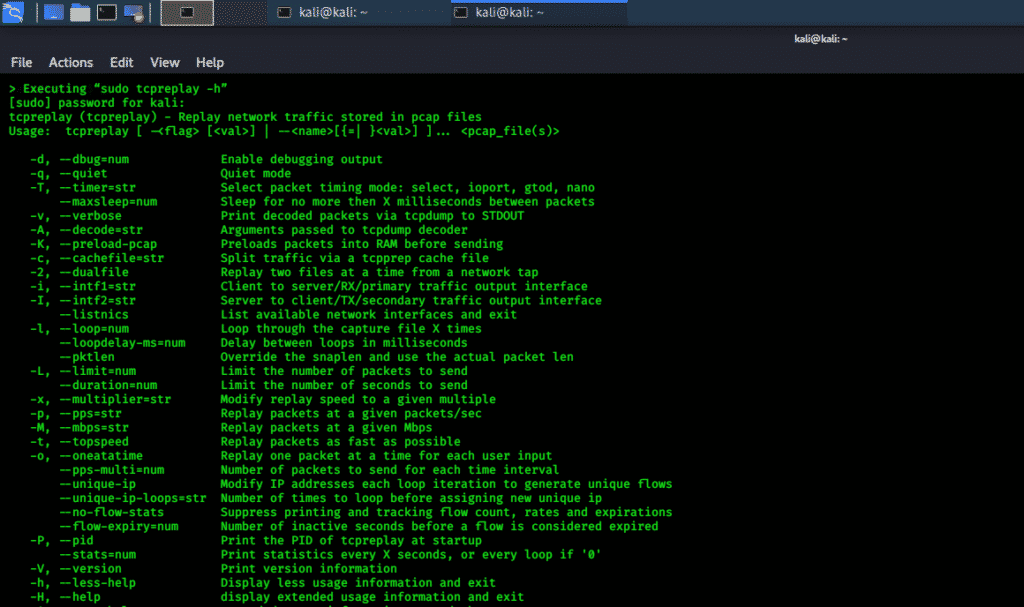
tcpreplay
The tcpreplay tool is used to replay network packets stored in pcap files. This tool resends all the traffic generated in the network, stored in pcap, at its recorded speed; or, with the capability of quick operation of system.
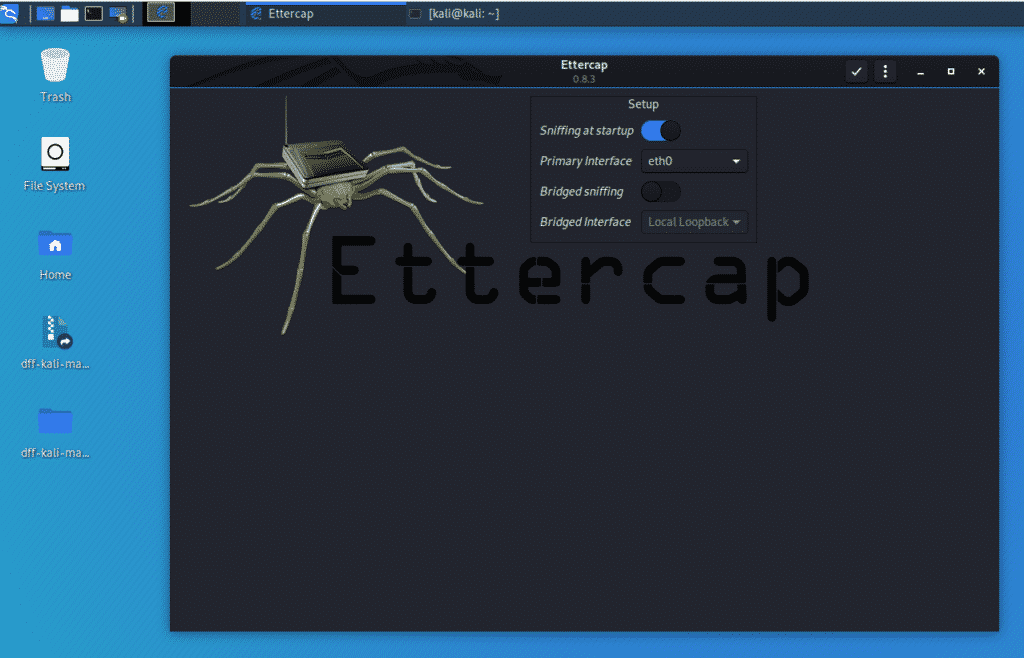
ettercap
The Ettercap tool is a comprehensive toolkit for “man in the middle” attacks. This tool supports sniffing of live connections, in addition to filtering content on-the-fly. Ettercap can dissect various protocols actively and passively. This tool also includes many different options for network analysis, as well as host analysis. This tool has a GUI interface and the options are easy to use, even to a new user.
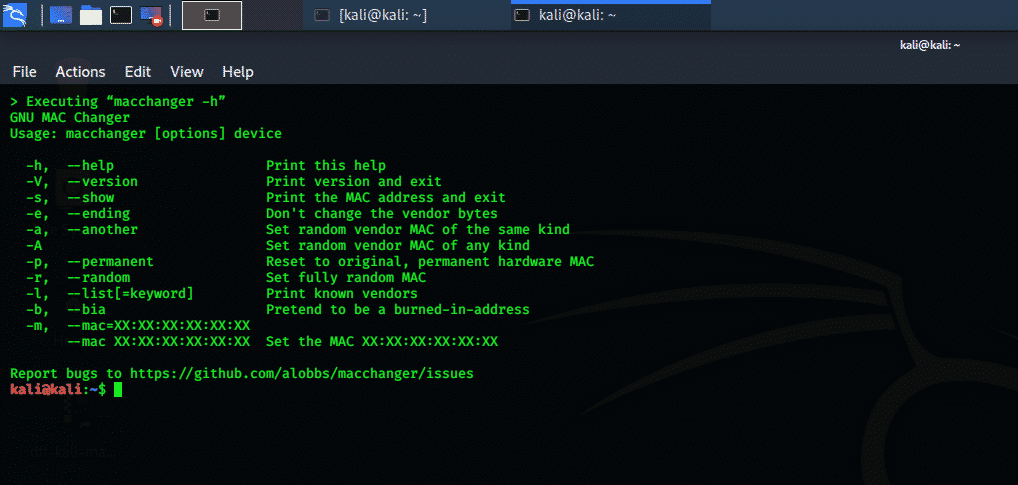
macchanger
The macchanger tool is a favorite tool for pentesting in Kali Linux. Changing the MAC address is very important while pentesting a wireless network. The macchanger tool changes the attacker’s current MAC address temporarily. If the victim network has MAC filtering enabled, which filters unapproved MAC addresses, then macchanger is the best defensive option.
Figure 8 MAC addressing changing tool
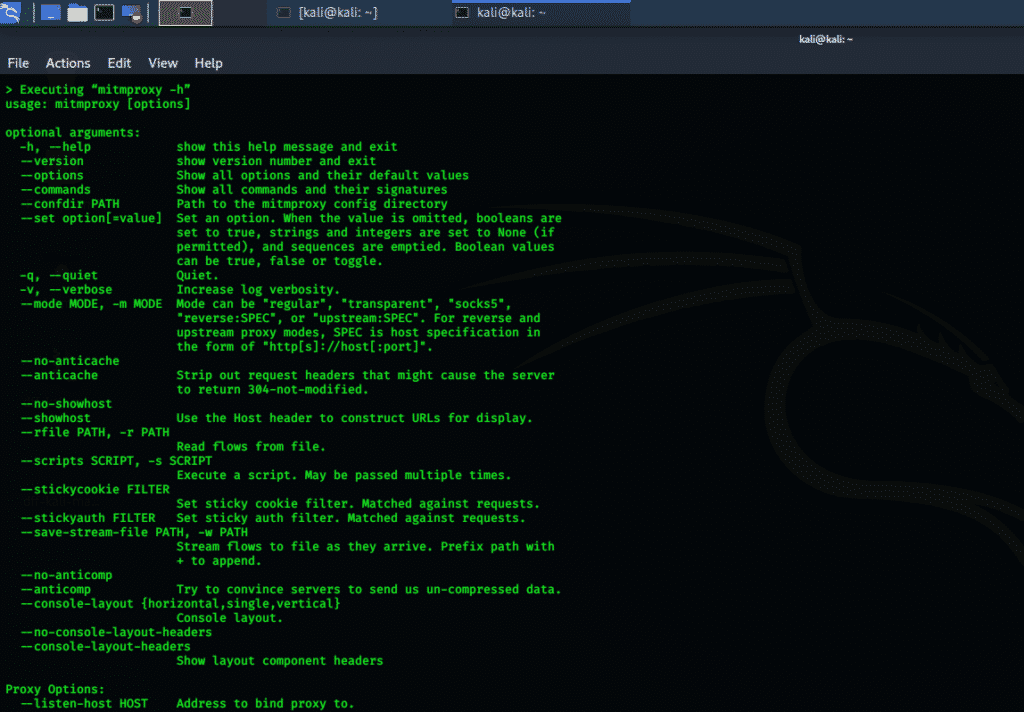
mitmproxy
This “man-in-the-middle” proxy tool is an SSL HTTP proxy. Mitmproxy has terminal console interface and has the ability to capture and inspect live traffic flow. This tool intercepts and can change HTTP traffic at the same time. Mitmproxy stores HTTP conversations for offline analysis and can replay HTTP clients and servers. This tool can also make changes to HTTP traffic data using Python scripts.
responder
The responder tool is a sniffing and spoofing tool that answers requests by the server. As the name implies, this tool only responds to a Filer server service call request. This improves the stealth of the target network and ensures the legitimacy of the NetBIOS Name Service (NBT-NS) typical behavior.
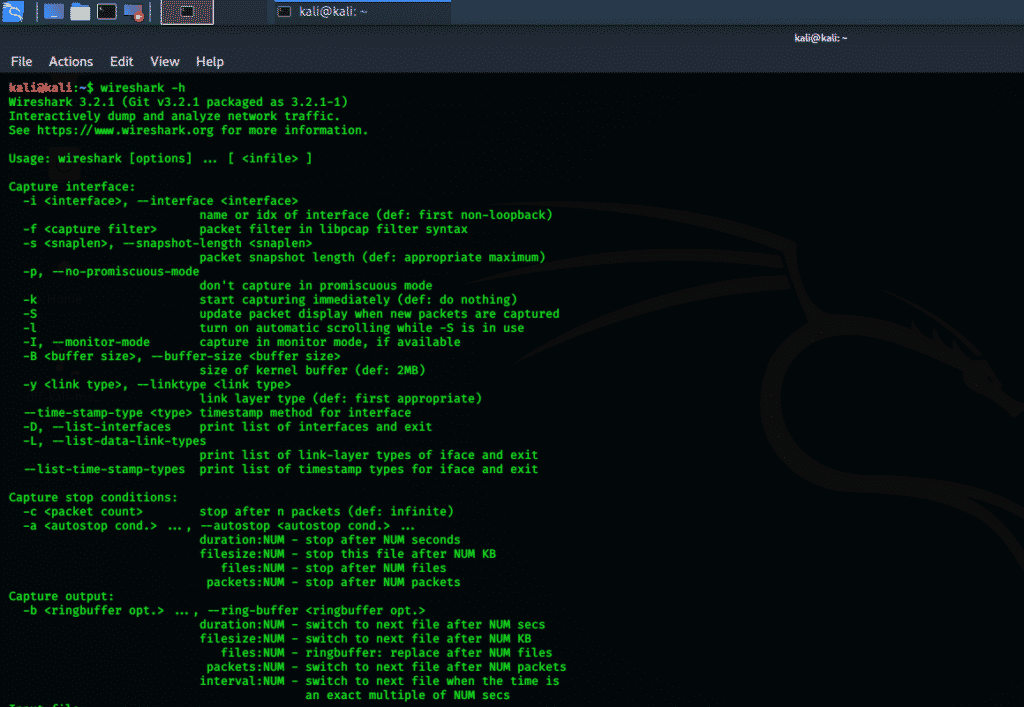
Wireshark
Wireshark is one of the best network protocols analyzing freely available packages. Webshark was previously known as Ethereal and is widely used in commercial industries, as well as educational institutes. This tool has a “live capturing” ability for packet investigation. The output data is stored in XML, CSV, PostScript, and plain text documents. Wireshark is the best tool for network analysis and packet investigation. This tool has both console interface and graphical user interface (GUI), and the options on the GUI version are very easy to use.
Wireshark inspects thousands of protocols, and new ones are being added with every update. Live capturing of protocols and then analyzing is offline; Three-way handshake; Analyzing VoIP protocols. Data is read from many platforms i.e., Wi-Fi, Ethernet, HDLC, ATM, USB, Bluetooth, Frame Relay, Token Ring and many others. It can read and write a wide variety of different captured file formats.
Conclusion
This article covered the top 10 sniffing and spoofing tools in Kali Linux and described their special abilities. All these tools are open-source and freely available on Git, as well as the Kali tool repository. Among these tools, Ettercap, sslsplit, macchange and Wireshark are the best tools for pentesting.