In this guide, we will discuss various ways to secure your Apache Tomcat server. The methods discussed in this guide are best suited for production as you may or may not require them during development.
1 – Suppress Server Info
A simple way to increase the security of the Apache Tomcat server is to remove the server banner from the HTTP response. If exposed, the flag could leak the version of Tomcat you are using, making it easier to gather information about the server and known exploits.
In recent versions of Tomcat (Tomcat 8 and above), the server banner is disabled by default. However, if you are using an older version of Tomcat, you may need to do this manually.
Edit the server.xml file under the conf directory of the Tomcat install directory.
Locate the Connector Port entry and remove the Server block.
Before:
connectionTimeout="20000"
server="<value>"
redirectPort="8443" />
After:
connectionTimeout="20000"
redirectPort="8443" />
Save the file and restart the Apache Tomcat service.
2 – Enable SSL/TLS
SSL allows you to serve data between the server and the client over HTTPS protocol. To use SSL in Tomcat, thereby enhancing security, edit the server.xml file and SSLEnabled directive in Connector port as:
connectionTimeout="20000"
SSLEnabled="true" scheme="https" keystoreFile="conf/key.jks" keystorePass="password" clientAuth="false" sslProtocol="TLS"
redirectPort="8443" />
The above entry assumes you have a Keystore with an SSL certificate.
3 – Don’t Run Tomcat as Root
Never run Tomcat as a privileged user. This allows you to protect the system in case of a compromised Tomcat service.
Create a user to run the Tomcat service.
Finally, change the ownership to the tomcat user created.
4 – Use the Security Manager
It is good to run the Apache Tomcat server using the security manager. This prevents untrusted applets from running in the browser.
Below is an example output:
Using CATALINA_BASE: /home/debian/apache-tomcat-10.0.10
Using CATALINA_HOME: /home/debian/apache-tomcat-10.0.10
Using CATALINA_TMPDIR: /home/debian/apache-tomcat-10.0.10/temp
Using JRE_HOME: /usr
Using CLASSPATH: /home/debian/apache-tomcat-10.0.10/bin/bootstrap.jar:/home/debian/apache-tomcat-10.0.10/bin/tomcat-juli.jar
Using CATALINA_OPTS:
Using Security Manager
Tomcat started.
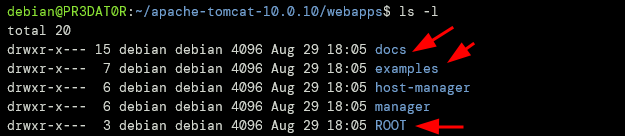
5 – Remove Unwanted Applications
Apache Tomcat comes with exploitable default sample applications. The best measure against this is to remove them from your webapps directory.
You can remove applications such as:
- ROOT – The Tomcat default page
- Docs – Tomcat documentation
- Examples – Servlets for testing
6 – Modify Tomcat’s Shutdown Procedure
Another way to secure Tomcat is to change the shutdown procedure. Doing this can help prevent malicious users from shutting down Tomcat’s services.
Tomcat can be shut down by using port 8005 on telnet and sending the shutdown command:
Connected to localhost.
Escape character is '^]'.
shutdown
Connection closed by foreign host.
To fix this, edit the server.xml file and remove the following block.
If you want to keep the shutdown command alive, change the default port and command. For example:
7 – Add Secure & HttpOnly Flags
Attackers can also manipulate installed applications’ cookies and sessions. To resolve this, edit the web.xml file and add the following entries in the session-config block.
<http-only>true</http-only>
<secure>true</secure>
</cookie-config>
Conclusion
This article outlined some necessary configurations you can make to Apache Tomcat to help increase and enhance security. Please note that the methods discussed are only a few of the many measures you can take to secure Tomcat.