Scanning the Network Anonymously with Nmap and Proxychains
As an ethical hacker and penetration tester, network scanning is an essential practice for identifying the vulnerabilities and ensuring the safety of your target system and infrastructure. However, conducting network scans without proper precautions can expose your identity and make you vulnerable to malicious actors.
But don’t worry! We have a solution that will empower you to carry out the anonymous network scanning like a professional penetration tester. Proxychains and Nmap are dynamic duos that will not only keep your identity hidden but also provide comprehensive insights into your network’s security.
What Is Proxychains?
Before we dive into the exciting world of network scanning with Nmap, let’s first understand what Proxychains is. Proxychains, to put it simply, is a powerful tool that enables you to run the apps through many proxy servers. Your original IP address is hidden as a result, adding another level of anonymity.
It is quite challenging for anyone to determine the origin of your activity when you use Proxychains to route your network traffic through a number of proxy servers. When you want to perform network scans without giving your identity to prospective dangers, this is extremely helpful.
Getting Started: Installing Proxychains
Proxychains is only compatible with Unix-based operating systems, including Linux and macOS, so it can’t be installed in Windows. However, you can use the Windows Subsystem for Linux (WSL) and follow the Linux installation process. Follow the following instructions to set up Proxychains:
For Linux Users
Proxychains is already pre-installed in some Linux distros, especially in the cyber security field such as Kali Linux. But, if you have not installed Proxychains yet, open a terminal and use the following command to install it. But you need to keep your Linux system up-to-date first:
Then, install Proxychains using the following command:
For MacOS Users
In MacOS, you could install Proxychains using the Homebrew package manager. Open your terminal and enter the following command:
Configuring Proxychains
You need some configuration before using Proxychains properly. Proxychains provides a configuration file that is stored in /etc/proxychains.conf. To verify the path, you can find the file location using the following command:
The result is shown in the following image:
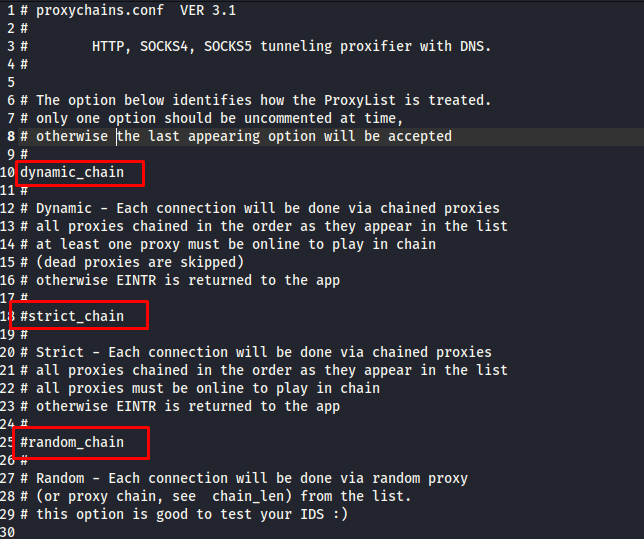
Now, open that file using your favorite text editor. It could be Nano, Gedit, Vim, or Mousepad. We just use the Mousepad for simple editing. Once you open it, you might find the configuration as shown in the following:
There are three main methods of using Proxychains: Dynamic Chaining, Strict Chaining, and Random Chaining. For convenient usage, we recommend you to use the Dynamic chain as it offers more flexibility. Just uncomment the Dynamic chain option to enable it (delete the “#”). Now, scroll down all the way to the bottom of the file.
Input the Proxy Server into the List
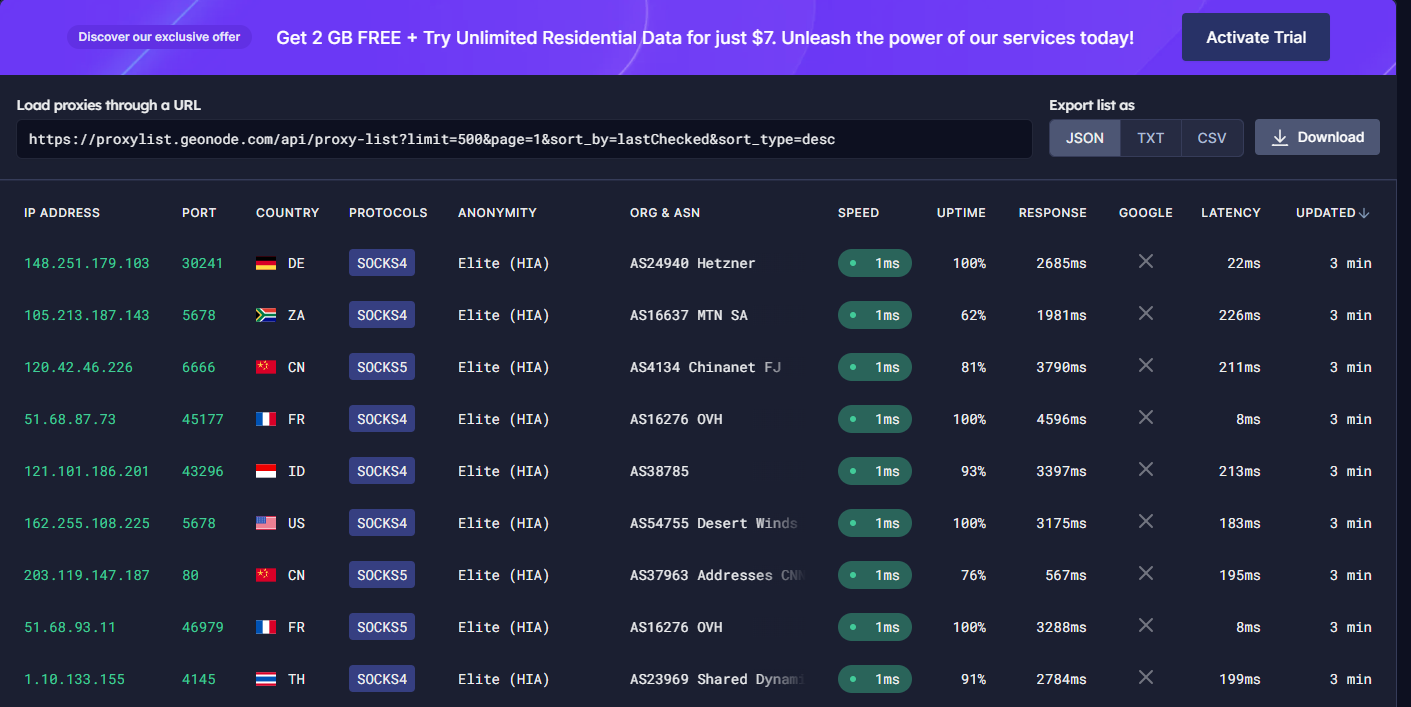
At this point, make sure that you already have at least one proxy server. The detail consists of IP address, protocol, and port number. Proxychains supports various protocol types including HTTP, SOCKS4, and SOCKS5. There are a lot of free proxy servers available on the internet; you can Google it. But, it has also a lot of limitations. In most cases of our experiments, most of the free proxies just don’t work, either because of being overworked or dying. Based on our experience, it is highly recommended that you should use a premium or a paid version of the proxy server. There are a lot of websites that provide free proxy servers such as Geonode.com. Go ahead to that website and select as many proxies as you want.
But please reduce your expectation if you are using a free service. Sometimes, those proxies are overworked or even dead. Use the premium service instead if you take this privacy matter seriously.
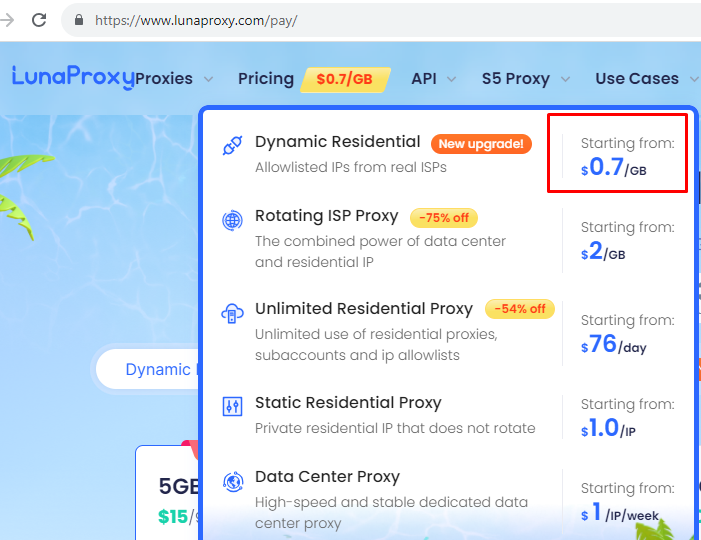
Don’t worry, we have done several trials on the proxy server provider which offers high-speed connectivity, is super anonymous, and yet the most important thing is that it needs less budget. If you have a high value of your internet data and privacy, you should try LunaProxy. It has a high-quality dynamic residential proxy IP network that helps you to bypass the country restrictions and website blocking which provides 200 million real residential IP proxies around the world, supports SOCKS5 and HTTP proxy protocols, and is super anonymous. LunaProxy also often shares a lot of discount coupons on its page. The price starts from $0.7 cent per GigaByte; it won’t affect your wallet though.
Go ahead and get your Luna Proxy here.
Input your proxy details in the configuration file. Just add it to the last line of the file under the “Proxy List” section. Here’s a snippet of the configuration file:
# type host port [user pass]
# (values separated by 'tab' or 'blank')
#
# Examples:
# socks5 192.168.67.78 1080 lamer secret
# http 192.168.89.3 8080 justu hidden
# socks4 192.168.1.49 1080
# http 192.168.39.93 8080
# Add your chosen proxies here, like:
# socks5 127.0.0.1 9050
socks5 192.168.39.93 9050
Anonymized Network Scanning with Nmap and Proxychains
Now that you have Proxychains all setup and ready, it’s time to unleash the power of Nmap for network scanning. Nmap, short for Network Mapper, is a versatile and comprehensive network scanning tool that is used by cybersecurity professionals and enthusiasts alike.
Nmap allows you to discover the hosts and services on a computer network, thus creating a map of the network’s structure. When combined with Proxychains, Nmap becomes an unstoppable force for anonymized network scanning. With Proxychains, you can route your Nmap scan through multiple proxies for enhanced anonymity. Simply add more proxy servers to the configuration file, and Nmap will follow the chain accordingly. Basically, you can run every option on NMAP using Proxychains. Here’s the example on how to use Nmap with Proxychains:
Basic Nmap Scanning
The simplest way to run an Nmap scan through Proxychains is by adding the “proxychains” command before the Nmap command. For example:
Using Nmap Scripts
Nmap comes with a vast array of scripts that enhance its capabilities. To use the Nmap scripts with Proxychains, follow this syntax:
Scanning Specific Ports
If you want to scan specific ports on a target, use the -p option followed by the port numbers. Proxychains ensures that your Nmap scan remains anonymous while probing the specified ports.
Advantages of Anonymized Network Scanning
You might wonder why bother with anonymized network scanning in the first place. Well, there are several compelling reasons to use Proxychains with Nmap for your network security assessments:
1. Enhanced Security and Anonymity
By routing your Nmap scans through multiple proxy servers, you shield your identity and location. This makes it difficult for potential attackers to trace your activities back to you, providing an added layer of security for your scanning endeavors.
2. Protecting Personal Information
When conducting network scans on behalf of your organization or clients, you handle the sensitive data and information. Anonymized scanning ensures that this data remains confidential and minimizes the risk of data breaches.
3. Bypassing Geo-Restrictions
Some network scans may involve probing the hosts in different geographical locations. Anonymized scanning allows you to bypass the geo-restrictions and access the targets that might be otherwise blocked.
4. Evading Detection
In certain scenarios, like penetration testing engagements, remaining undetected is crucial. Anonymized network scanning enables you to fly under the radar and gather the vital information without raising suspicion.
Conclusion
Congratulations! You now learned the art of using Proxychains with Nmap for anonymized network scanning. By harnessing the power of these tools, you can safeguard your identity, protect sensitive information, and carry on with your network scanning endeavors fearlessly! Regular network scanning, with the added advantage of the anonymity provided by Proxychains and Nmap, is a proactive step towards ensuring the safety and security of your digital assets.
The combination of Proxychains and Nmap is a game-changer in the realm of network scanning. With the ability to remain anonymous while uncovering potential threats, you possess a potent arsenal for safeguarding the digital assets.
Always remember to stay ethical and responsible. Anonymized network scanning should only be conducted on systems and networks that you have explicit permission to explore. Ethical hacking and cybersecurity are about protecting and defending, not causing harm.
Happy scanning, my friend! The world of cybersecurity is at your fingertips, and you have the tools to make a real difference. So, go ahead, dive into the depths of Proxychains and Nmap, and let your journey to excellence begin!