How to Use Proxychains for Anonymous Web Browsing in Kali Linux
Most people mistakenly think that using a VPN service only while browsing the internet is very safe to hide their privacy and data. Until they found out about Proxychains. Proxychains basically utilize the connections from multiple proxy servers and could be using various protocols such as HTTP, SOCK4 & SOCK5. ProxyChains acts as an intermediary between the source IP and the endpoint IP. Thus, Proxychain is able to create a secure connection and makes it almost impossible for a tracker to know what you are looking for. Let’s start the tutorial by updating your Kali Linux machine.
1. Updating Kali Linux
The first and always recommended step is to keep your system up-to-date for security and optimal performance. Now, open a terminal in Kali Linux and type the following command to update the package lists and upgrade the installed packages:
2. Locating Proxychains in Kali Linux
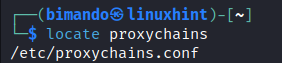
Proxychains is pre-built into the Kali Linux machine. But if you wonder where the Proxychains configuration file is, it is actually saved under the /etc/ file system. To locate or find the Proxychains configuration file in Kali Linux, you can use the following command:
3. Configuring Proxychains in Kali Linux
Before we run Proxychains, you need to set up the configuration file properly. The configuration file is stored at /etc/proxychains.conf. Now, open it using a text editor like Nano, Gedit, or Leafpad:
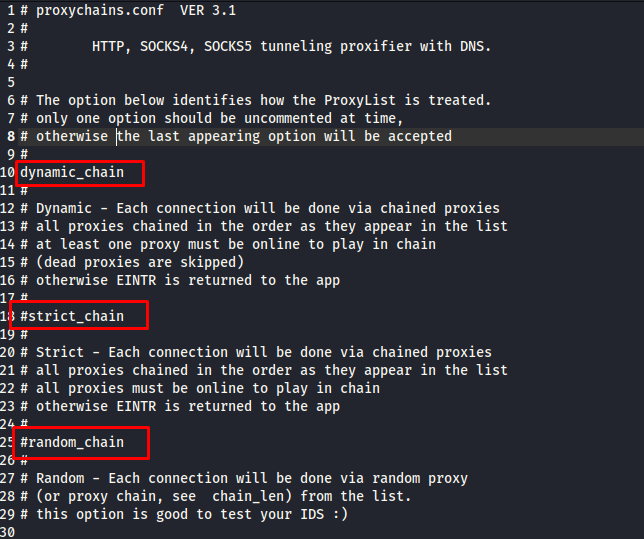
If it is your first time configuring Proxychains, you need to know the several options on how Proxychains should behave with your proxy server. They are dynamic chains, strict chains, random chains, or round-robin chains. You would find each of those method definitions in the configuration file as shown in the following image:
You can only choose one method of chaining. For convenience and flexibility offer, it is recommended to use the dynamic chains by uncommenting the options (deleting the “#” on line 10 on the previous image).
4. Adding Proxies
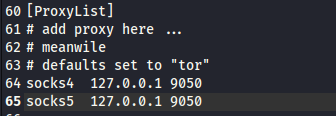
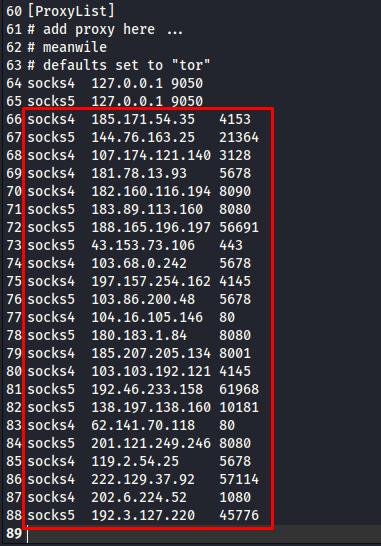
Now, still on the configuration file, scroll all the way down to the bottom of the file. You will find the ProxyList section. There, you should input the valid proxies. You can add free or premium proxies to the configuration file. An example entry for a SOCKS5 proxy looks like this:
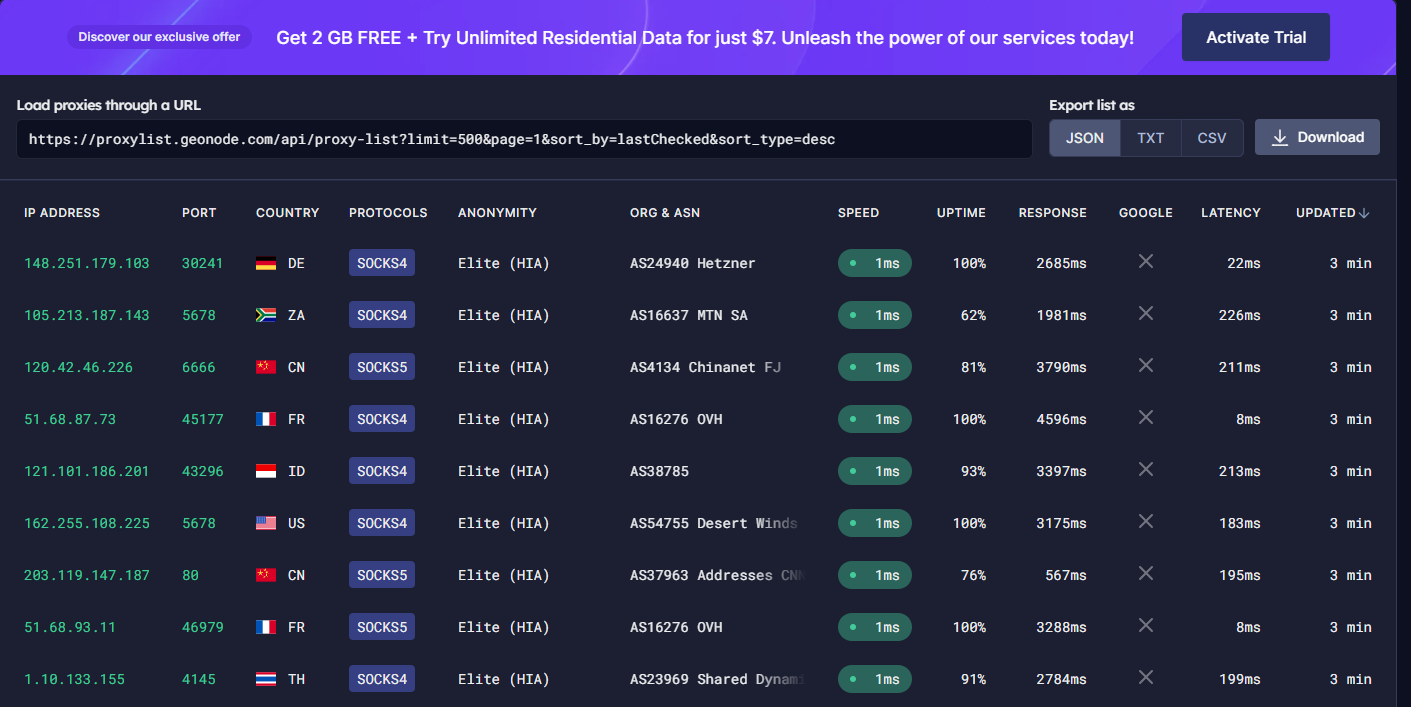
Next is we need to search for some proxy servers. Actually, there are a lot of websites that provide free proxy servers such as Geonode.com. Go ahead to that website and select as many proxies as you want.
But please reduce your expectation if you are using a free service. Sometimes, those proxies are overworked or even dead. Use the premium service instead if you take this privacy matter seriously.
Don’t worry, we have done several trials on the proxy server provider which offers high-speed connectivity, super anonymous, and yet the most important thing is that it needs less budget. If you have a high value of your internet data and privacy, you should try LunaProxy. It has a high-quality dynamic residential proxy IP network that helps you to bypass the country restrictions and website blocking which provides 200 million real residential IP proxies around the world, supports SOCKS5 and HTTP proxy protocols, and is super anonymous. LunaProxy also often shares a lot of discount coupons on its page. The price starts from $0.7 cent per GigaByte; it won’t affect your wallet though.
Go ahead and get your Luna Proxy here.
Once you get the proxy server, input the proxy list in the Proxychains configuration file with the format as shown in the following image:
Save and close the file. Now, it’s done!
5. Browsing Anonymously Using Proxychains
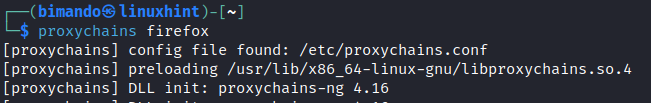
Once you added the proxies, save the configuration file and exit the text editor. To use Proxychains for anonymous browsing, simply prefix the desired application’s command with Proxychains. For example, to browse the web using Firefox, use the following command:
A new Firefox tab will be opened, and you could start browsing anonymously.
6. Verifying Anonymity While Using Proxychains
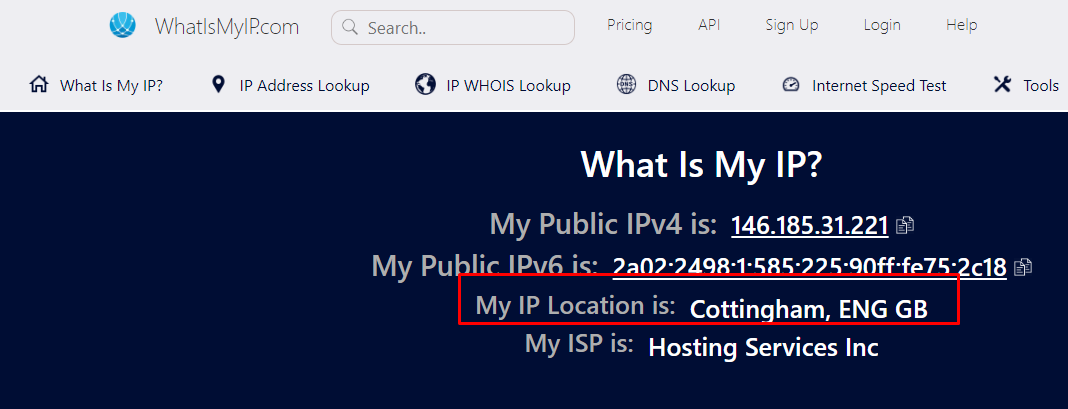
Before we browse wildly on the internet, we need to verify our anonymity. You can check it by visiting a website that displays your public IP address and check if it matches the one that is provided by your chosen proxy. If successful, you achieve the anonymous web browsing in Kali Linux using Proxychains. You can check your IP address using a free web service such as https://www.whatismyip.com/.
My current internet provider is originally located in Indonesia, but it was detected that my IP-based location is in England.
Advantages of Using Proxychains
Using Proxychains for anonymous web browsing in Kali Linux offers a plethora of advantages:
- Enhanced Privacy: Proxychains conceals your real IP address, making it challenging for websites and malicious actors to track your online activities.
- Location Spoofing: By routing your internet traffic through proxies, you can appear to be browsing from a different geographical location, granting access to region-locked content.
- Increased Security: Proxychains adds an additional layer of security, safeguarding your data and personal information from potential threats.
- Bypassing Filters and Firewalls: In regions with internet restrictions, Proxychains can help bypass the filters and firewalls, granting access to a more open internet.
Professional Tips for Effective Use of Proxychains
- Choose Reliable Proxies: Opt for reputable and secure proxies to ensure a reliable and safe anonymous browsing. Sometimes, the free proxy is sick. Please use the premium or the paid version of proxy servers.
- Regularly Update the Proxies: Proxies may become slow or unreliable over time. Regularly update your list of proxies for a smooth browsing experience.
- Avoid Logging In. To maintain anonymity, refrain from logging into personal accounts while using Proxychains.
- Combine with VPN: For even stronger protection, consider using Proxychains in conjunction with a trusted VPN service.
- Test the Anonymity Regularly: Periodically verify your anonymity to ensure that Proxychains is functioning correctly.
Frequently Asked Questions (FAQs)
Can I use Proxychains with any application in Kali Linux?
Yes, Proxychains can be used with any application virtually that relies on internet connectivity. However, it’s essential to configure each application to use Proxychains explicitly.
Is Proxychains legal to use?
Easy answer. Yes, Proxychains is a legal tool. The legality of its use, however, is determined by your country of residence and the actions that you take while using it. When using Proxychains, always abide by the laws and regulations of your nation.
How many proxies should I use?
The number of proxies you should use depends on your specific needs and preferences. Using multiple proxies can enhance anonymity but may affect the browsing speed. Strike a balance based on your requirements. Also, please consider the quality of your proxy server connection, latency, and speed.
Can Proxychains completely hide my identity?
While Proxychains offers a higher level of anonymity, it may not completely hide your identity from determined adversaries. Employ additional security measures like VPNs for comprehensive protection.
Are free proxies safe to use?
Free proxies can be risky as their security and reliability are often questionable. It’s advisable to use the trusted and verified premium proxies for a safer browsing experience. Mostly, free proxies are dead proxies.
Can I use Proxychains on Windows or macOS?
Unfortunately, Proxychains is primarily designed for Linux-based systems like Kali Linux. While there are alternative methods for Windows and macOS, Proxychains’ native support is limited to Linux.
Conclusion
Embracing the power of Proxychains for anonymous web browsing in Kali Linux empowers you with enhanced privacy and security while exploring the online realm. By following the outlined steps and implementing the expert tips, you can confidently traverse the internet while safeguarding your identity and data from prying eyes. Remember to use Proxychains responsibly and respect the laws and regulations that govern the online activities in your region.