Wireless Testing and Tools
[adthrive-in-post-video-player video-id=”6gE0DwqC” upload-date=”2020-09-10T05:54:19.000Z” name=”Kali Linux Network Reconnaissance” description=”Kali Linux Network Reconnaissance” player-type=”collapse” override-embed=”true”]
Wireless testing examines and analyses devices that can connect with other networks. These devices perform various tasks and functions and are tested to ensure their compliance and regulation. There are various tools used for this purpose; for example, Aircrack-ng, Wifite, Wireshark, Wash, etc. Another term used for testing the potential in a device or network is known as Network Reconnaissance. There are various tools used for the activation of Network Reconnaissance in wireless testing.
This article will discuss Network Reconnaissance and the tools used for its activation.
Network Reconnaissance for Beginners
How can you target something you cannot see? For this purpose, there is a footprinting tool known as Nmap. If you are annoyed by your neighbors continuously using your WiFi, you can use this tool to scan your entire home network. Nmap can show you every device that is connected and gives all information about the target device. It is also used to scan servers or routers. You can download Nmap from any website, such as nmap.org. It is available for popular operating systems, such as Linux and Windows. Nmap is pre-installed for Kali Linux, you just have to launch it and run the program. All you have to do is open Nmap and enter your route password, and there you go.
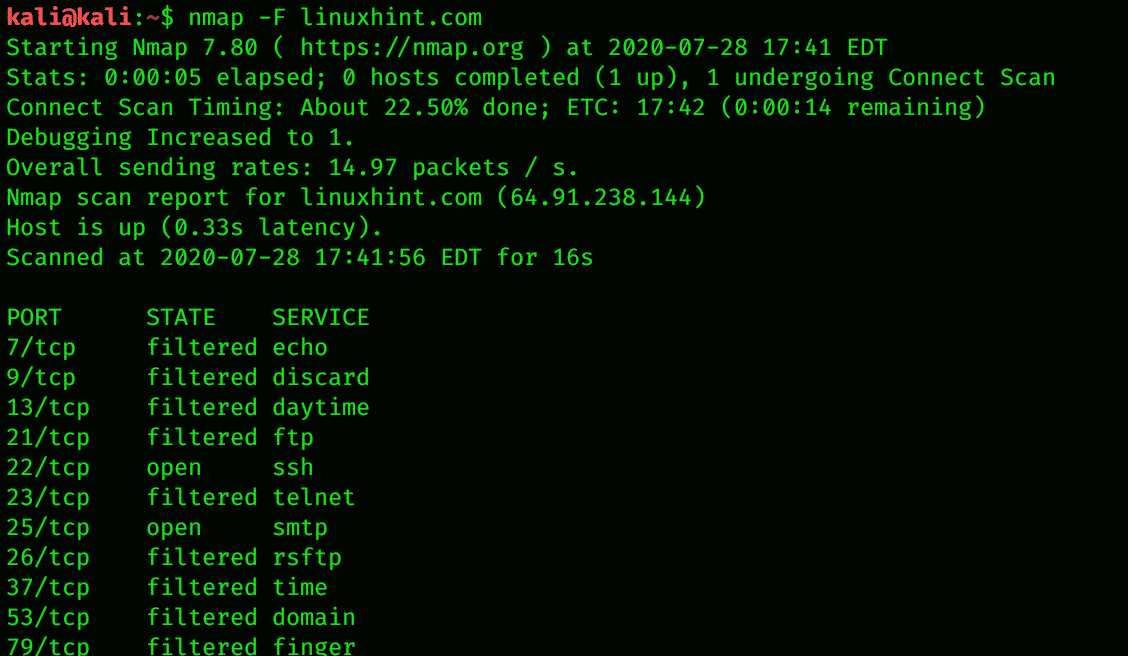
Nmap for Local Networks
Nmap is a great Network Reconnaissance tool used for scanning the data connected to any device. You can scan all the up servers and systems and check the weaknesses of the network and OS. You can check for live systems, open ports, perform banner grabbing, prepare proxies, view the IP address and the OS version, and other details about the connected device with Nmap. To receive this information, enter the following command:
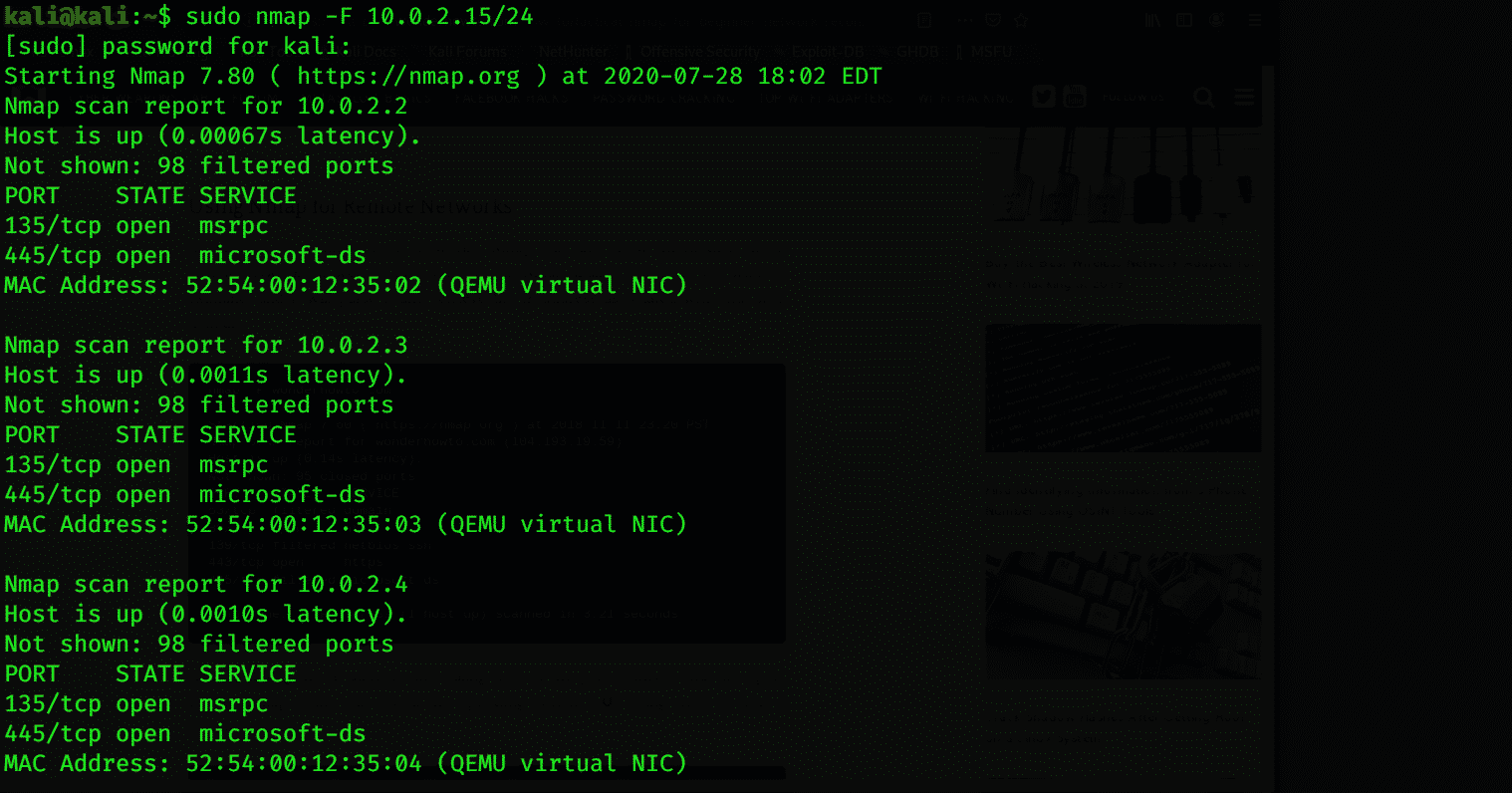
Nmap for Remote Networks
Nmap sends TCP and UDP packets to the remote host and analyzes nearly every part of the response. Nmap also performs tests, such as TCP. In a nutshell, Nmap is used for the determination of network inventory, as well as how vulnerable the host is. Nmap also provides remote OS detection. OS detection is finding what operating system is running on the target machine using TCP/IP stack fingerprinting. The following command code can help you for this purpose:
Configure Nmap to Scan a Single Target
To monitor someone’s every move, scanning their device is the best option. By running Nmap, you can get detailed information about the IP address, OS version, and all the websites connected to the device on your network. Nmap Scanning is useful even you are scanning for a single target. This can be done by scanning your local server by running Nmap. The following command code can be used to scan a single target:
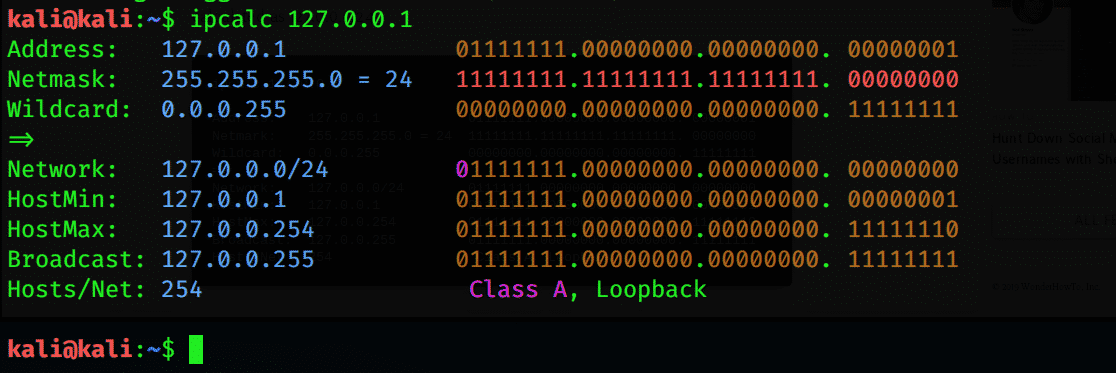
Calculate the subnet and Scan a Range to Discover Devices
Nmap can discover all the devices, IP addresses, and MAC addresses connected to a server. You can find a subnet range of all the devices by using a simple tool known as IPcalc. The subnet range is the range of the IP addresses that are available or connected to a network. To list all devices in the subnet range, enter the following command:
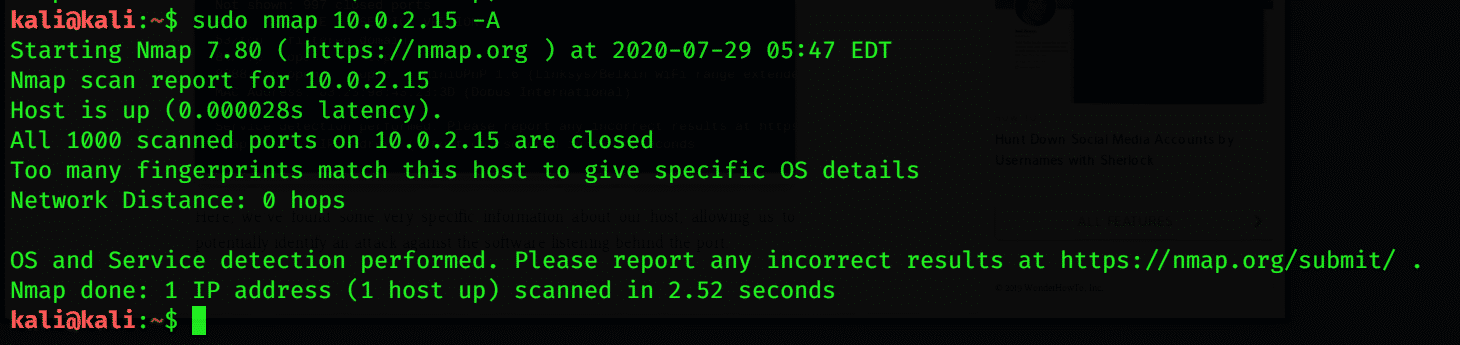
Create a Target List of Active Hosts
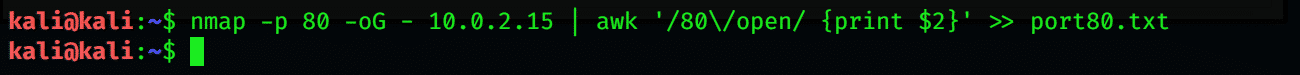
After determining all the IP addresses in the given range, you can get more information by using the –A attribute with the command. You can also obtain a file containing lists of your active host by following the Nmap terminal command below:
' >> port80.txt
Identify the Operating System on Discovered Devices
A useful thing to know about a device is its OS. By using Nmap, you can identify and detect the operating system the device is using. Use the following terminal emulator command to do so:
Using Nmap, you can also obtain information about the applications and their versions via the following command:
Advanced Scans and Workarounds
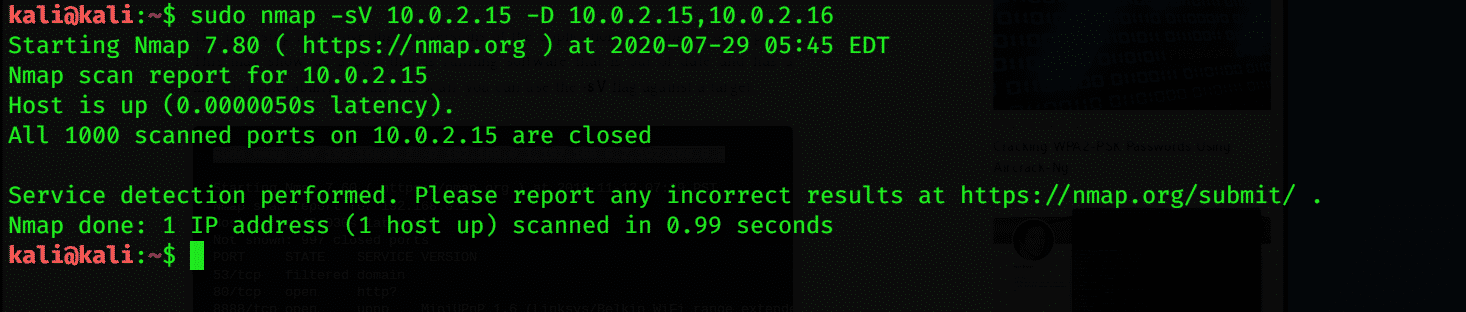
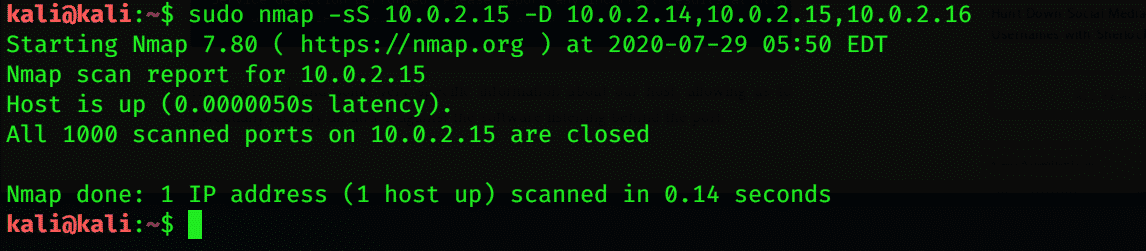
Nmap may stop working due to router issues. In this case, you may experience difficulties in scanning the data. You can solve this issue by adding –Pn, which can drop and beep facing by the router. If you do not want to be detected by other people for scanning, then you can add –D.
Conclusion
If you want to explore the devices that are connected to the network, then Nmap is your best option for this task. Nmap is a de facto scanning tool that scans for live hosts, OS, and open ports. It is an open tool available for all platforms. The main purpose of Nmap is that of network penetration tester; in other words, Network Reconnaissance. I hope that the concepts discussed in this article are enough for you to get the basic idea of Network Reconnaissance and tools used to perform this task in Kali Linux.