Docker Usage
Working as a pentester, you would not limit your usage to the pre-installed tools within Kali Linux. You would have to use a lot of different tools from different repositories. Installing these tools in your Kali Linux root repository is time consuming when you have many tools to install. Docker is a run-time container for all tools and creates isolated containers for you to install your tools.
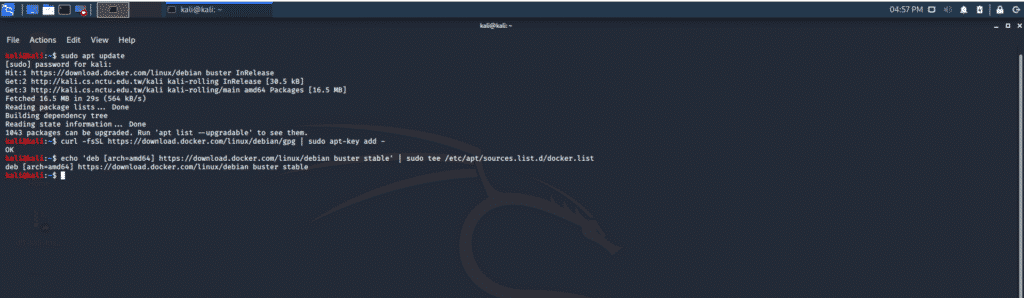
Step 1: Configure APT Keys
Always perform APT updating:
Step 2: Get PGP Key for official Docker
Step 3: Configure APT to Download, Install, and Update Docker
sudo tee /etc/apt/sources.list.d/docker.list
If everything is set up properly, then you will see a terminal window that appears as follows:
Step 4: Install Docker
The installation process I am following is given in Docker official documentation but as it has some minor bugs, I have added some commands to ensure proper installation. For this purpose, the following set of commands should be executed:
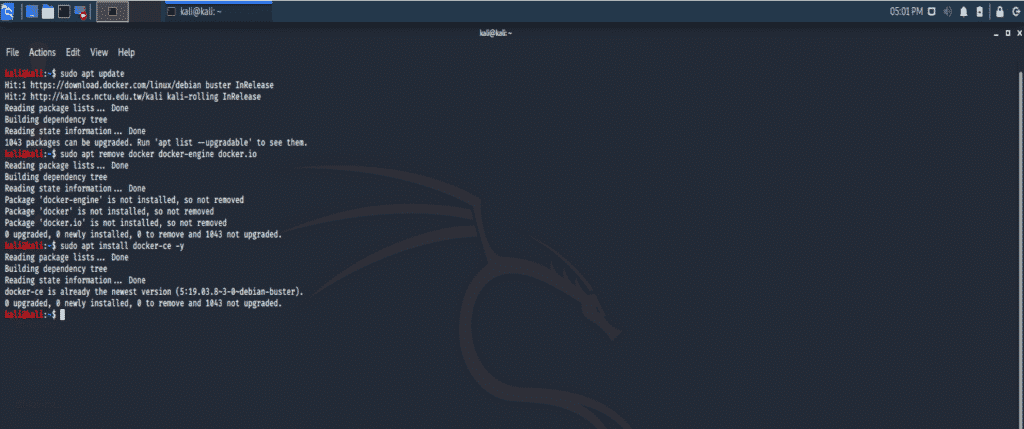
Step 5: Update the APT Again
Step 6: Terminate Outdated Versions Previously Installed
Step 7: Install Docker on Kali System
In the above command, “-y” stands for the “yes” condition. When installing a tool in the terminal, the user will be asked for permission to install the tool.
If the above steps have been performed correctly, than you will be able to see the following output on your terminal window:
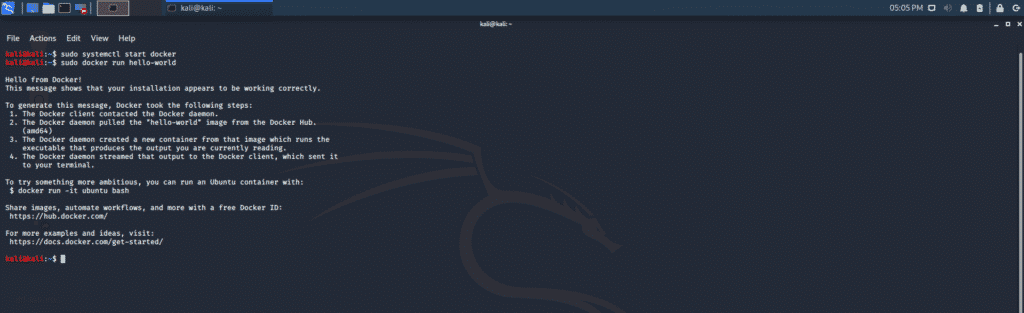
Step 8: Start the Docker Container
(Optional) Step 9: Set up Docker to Start Automatically on Reboot
This is an optional feature command; it will start Docker every time your OS boots. If you do not perform pentesting a lot, then you do not need to enable this feature.
Step 10: Verify Installation
The following command is taken from Docker official documentation. This command verifies if Docker is working.
The warning you see on the terminal window is normal, and Docker is working successfully. You should be able to see the following text on your terminal window:
Conclusion
Docker is a useful tool for penetration testing, and it is becoming more popular day by day. It can be helpful to work inside an isolated container, particularly while working with pentesting.