We will learn the following topics in detail:
- Installing & Configuring DVWA in Kali Linux
- Apache 2 web server setup
- PHP configuration
- MySQL database setup
DVWA at a Glance
Damn Vulnerable Web Application (DVWA) is a web application that is built for a penetration tester to test and practice their offensive hacking skills in a controlled environment.
Install DVWA on Kali Linux
Installing DVWA on Kali is actually easy, actually, there are several methods available. First, the user has to download the project from the DVWA GitHub page and run a few configuration settings such as database, web server, and PHP. Second, the user could also get a prebuilt DVWA package when they are installing Metasploitable. Third, the Kali Linux repository also provides the package for DVWA, using the apt-install command. The last method is the easiest and effortless way to install DVWA on Kali Linux.
In this tutorial, we will learn how to build or install DVWA on Kali Linux manually. With the aim of learning how to make a website and know what technology is which is often used to build a website.
Pre-requisite
Before installing DVWA into our Kali Linux, make sure we have an updated repo list and installed all of the required packages with the following command:
sudo apt install -y apache2 mariadb-server mariadb-client php php-mysqli php-gd libapache2-mod-php
1. Download the DVWA GitHub Project
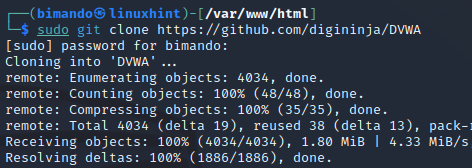
First, we need to download or clone the DVWA GitHub project on our Kali Linux located in/var/www/html directory. Simply use the git clone command to do that but make sure to change the current directory into /var/www/html using the cd command.
sudo git clone https://github.com/digininja/DVWA
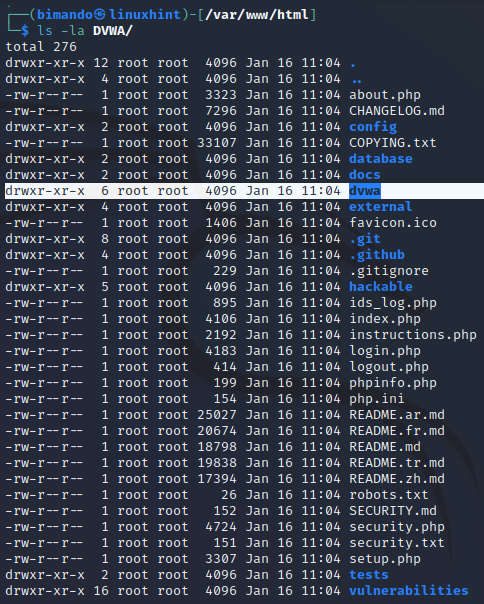
Once you downloaded the project, let us take a look at what files are in it.
Then, set permission to read, write, and execute permissions to the DVWA directory.
This permission allows DVWA to store the PHPids logs and to store the uploaded file located in DVWA/hackable/uploads directory.
2. DVWA Configuration File
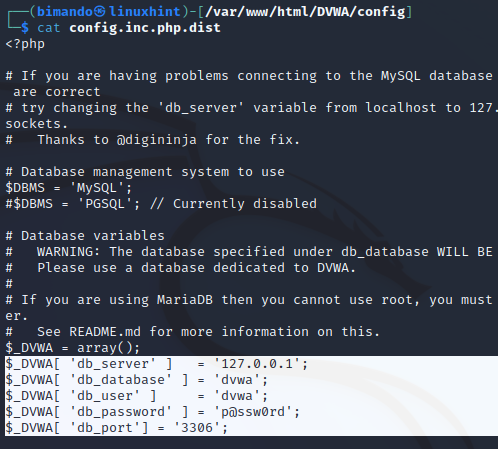
The default example of the configuration setting of DVWA is located under the /config directory. The filename is config.inc.php.dist. You could find the configuration such as DBMS, database credentials, default DVWA security settings, and many more. Let us take a look at the file below.
This file is an example file, the DVWA will not use it. Otherwise, we will copy this file and rename it (by removing the .dist at the end) to config.inc.php.
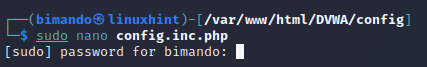
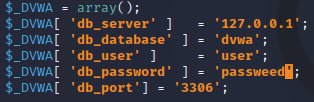
Now, open the copied file (config.inc.php) using any text editor and change the database default setting of username and password.
As an example, we will change the user to ‘user’ and the password to ‘passweed’.
Please take note of the value above. We need the value of db_server, db_database, db_user, and db_password for the next configuration below.
3. Configuring the Database
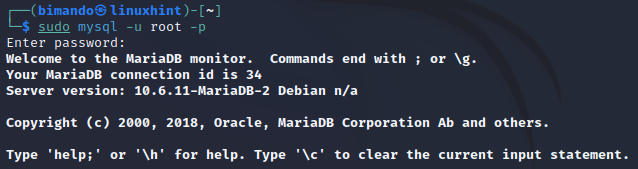
First, we need to fire up the MySQL service by using the following command:
Then, log in to MySQL using the root user, you will be asked for the root password:
Let us recap the database info value on the DVWA configuration setting (in step 2) that we are going to use in the table below.
| db_server | 127.0.0.1 |
| db_database | dvwa |
| db_user | user |
| db_password | passweed |
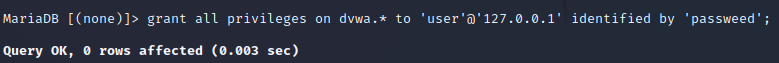
From the information above, create a database user with the name ‘user’ and the password ‘passweed’ on our localhost server at ‘127.0.0.1’ using the following command:
If configured correctly, the happy output will be “Query OK”.
The last step is to grant the user privilege all over the ‘dvwa’ database. Run the command below. You need to supply the username, password, and server information again.
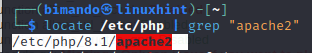
4. Configure the Apache2 Web Server
The apache2 installation file on your Kali Linux is stored in the /etc/php directory followed by the version of your PHP. In this tutorial, we are using the latest PHP version 8.1.
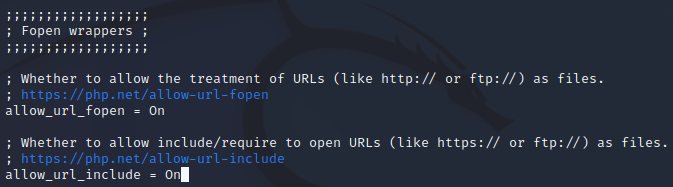
Now, we will make changes to a PHP function allow_url_include to be enabled. The configuration is stored in /apache2/php.ini file. Open the file using your favorite text editor. Here, I am using the nano text editor.
Scroll down to the Fopen wrappers section and ensure these two functions are enabled by setting the value to On, they are allow_url_fopen and allow_url_include.
Then, save the changes by pressing Ctrl + O and Enter. Exit the nano editor by pressing Ctrl + X. By allowing this function, DVWA allows us to do the XSS remote file inclusion (RFI) attack.
5. Launch DVWA on the Browser
Once everything is configured, restart the apache2 service and the MySQL service by running the following command:
sudo service mysql restart
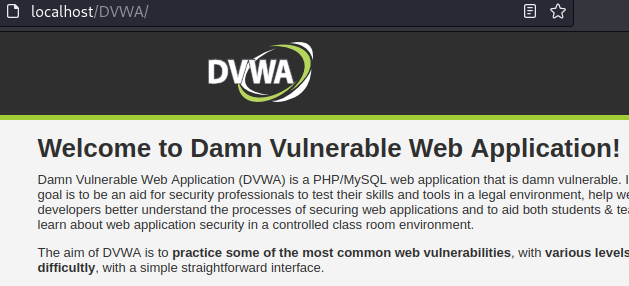
Then, open a browser, and visit http://localhost/DVWA/ or http://127.0.0.1/DVWA/. You will see a DVWA welcome page as shown below.
The last configuration is needed, still. We have created database user credentials before but we did not create the database. To create one, go to the DVWA page and on the left panel click ‘Setup / Reset DB’.
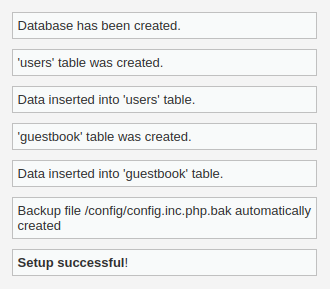
You will see the ‘Database Setup’ page. Now, scroll all the way down to the bottom and find a button named ‘Create / Reset Database’.
Click that button.
The setup is done. Your DVWA is ready to be exploited. You can explore every available vulnerability page at DVWA such as Brute Force, Command Injection, CSRF attack, File Inclusion, File Upload, SQL injection, XSS attack, and many more as shown in the figure below.
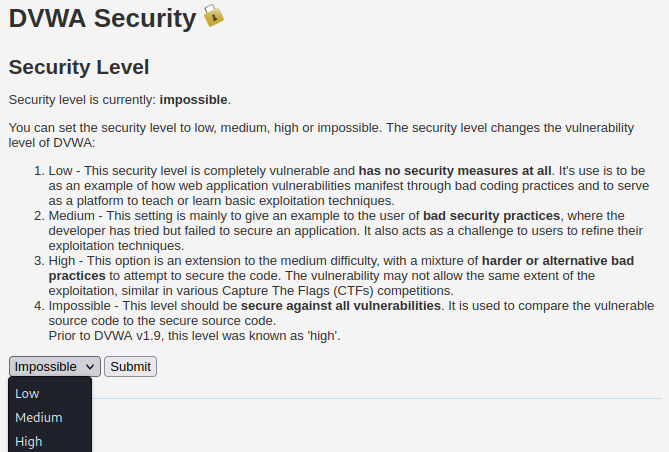
Ensure to select the suitable security level before running the test. By default, the security level was set to impossible, which is another term for a secure page. Please start from the lowest level to master the fundamental concept.
Conclusion
Hacking is also a practical skill that requires experience and quantity in performing a penetration test. DVWA is useful for training or teaching others how to attack the vulnerabilities of a web application with no risk or with a controlled environment.