Network Ports
There are two different network ports: TCP and UDP. TCP is commonly known as a connection-based protocol, and it requires a formal connection, which is a three-way handshake. UDP is commonly referred to as a connection-less protocol because it does not require a formal connection and does not consider the traffic flow, and this type is currently fading out.
Scans
[adthrive-in-post-video-player video-id=”5wvbWLRV” upload-date=”2020-09-10T06:29:45.000Z” name=”Ping Sweep in Kali Linux 2020″ description=”Ping Sweep in Kali Linux 2020″ player-type=”collapse” override-embed=”true”]
There are several different scanning options for using the NMAP tool.
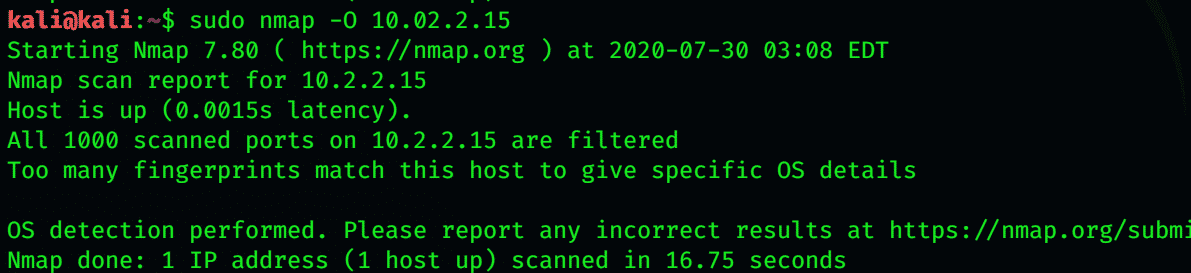
-O detects the operating system. Detection is based upon signatures because each operating system responds differently to packets.
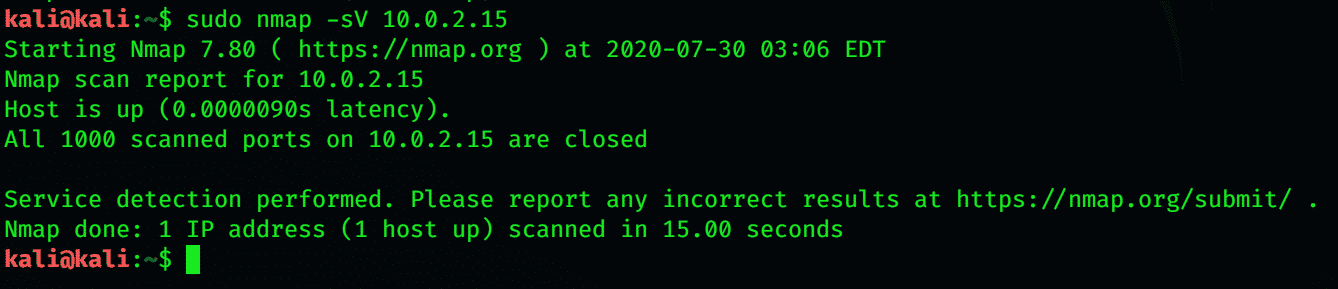
-V is version detection. This will detect the version of the program and whether the program is running. An alternative to this would be telnet, the IP address, and the port.
-s P is a ping sweep. Nmap gives you the option of using different styles of ping sweep; the default is ICMP, but you can also use TCP syn and TCP act.
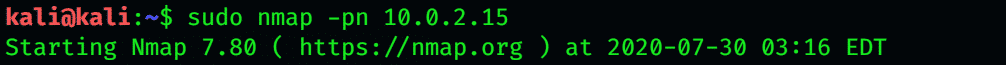
-P n skips host discovery.
-s a uses an ACK scan.
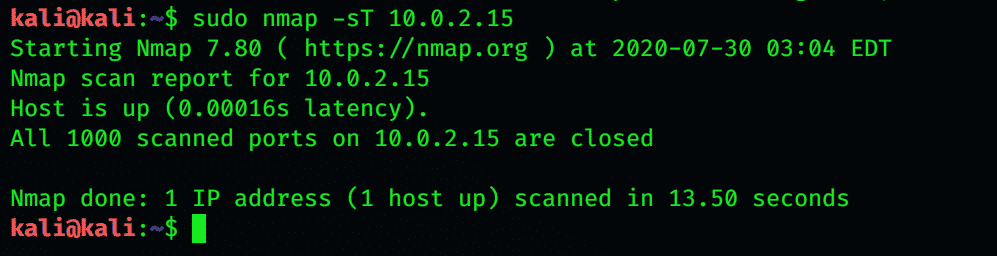
-s T is a TCP connect scan, which is a noisy, full TCP connect scan that uses a three-way handshake for syn, synack, and AK. This is a very noisy and lengthy scan, but it is very reliable.
-s s is a stealthy sense counting that uses a partial TCP three-way handshake and is also very quick.
Scans that are effective with Linux- and UNIX-based operating systems but not as effective with Windows include the following:
-s F is a fin scan, also commonly referred to as info in the inverse scan. This bypasses stateful firewalls that have a list of IP addresses that can access the server.
-s X is an Xmas scan.
-s N is a null scan; it sends no parameters.
-s U is a UDP scan.
-s L verifies your subnet.
-s P-PP sends an ICMP timestamp request. It evades ICMP-blocking firewalls.
If you wish to update an NMAP package, enter the following command:
The addition of Kali Linux repositories in the /etc/apt/sources.the list file is important. If you forgot to add them, add the repositories given below in the sources. List files.
Usage of Nmap
In your Linux, Windows, or Mac terminal, type Nmap to perform your scan, including the option and the target specifications. You can pass hostnames, IP addresses networks, etc. Nmap 10.0.2.15 [Target or any I.P Address]. A scan medium map is a great place where you can test your scanning.
TCP Connect Port Scan
The establishment of a TCP connection to a thousand common ports is done using this command.
Use -sU Option to Scan UDP Service
It is not only useful to get information about the other’s computer. It is of paramount importance as it gives you information regarding what server information others can see. Nmap -sV allows you to get ideal information regarding programs running on a machine.
Remote OS Detection
-O detects the operating system. It detects is based upon signatures because each operating system responds differently to packets. This is achieved by using information that Nmap gets through the TCP SYN.
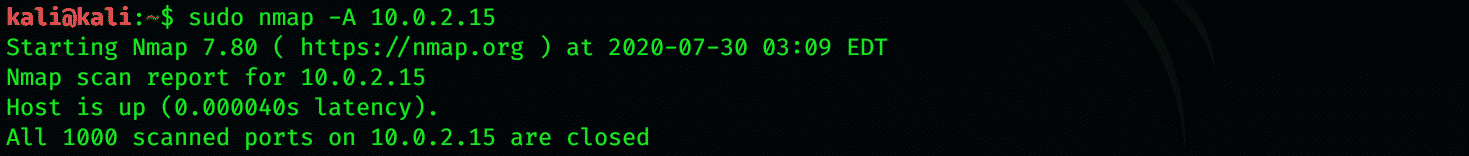
OS Detection, Version Detection, Script Scanning, and Traceroute
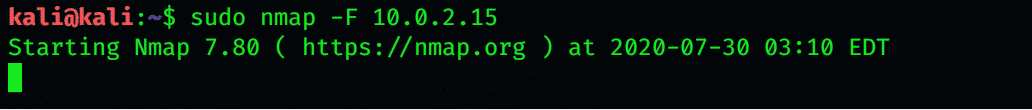
Nmap scans thousands of used ports on the machine you are targeting. This process takes a lot of time. If you wish to scan only the most common scans to reduce time consumption, use the -F flag. By using this flag, Nmap only scans the 100 most common ports.
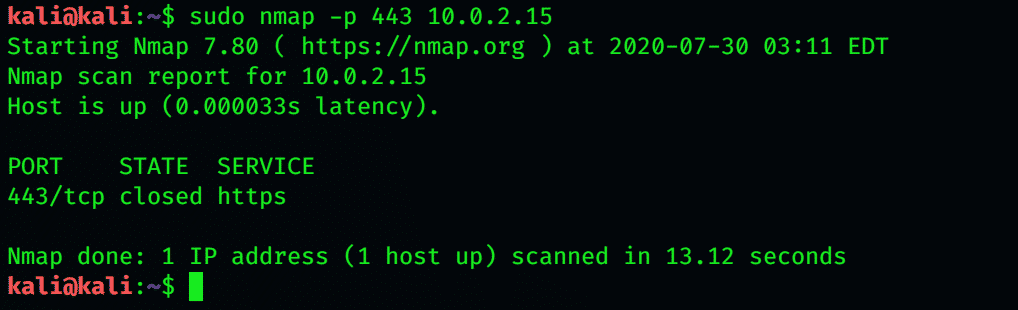
To scan the selected ports using Nmap, use -p. Now, Nmap will only scan the specified ports.
Scan Multiple Ports
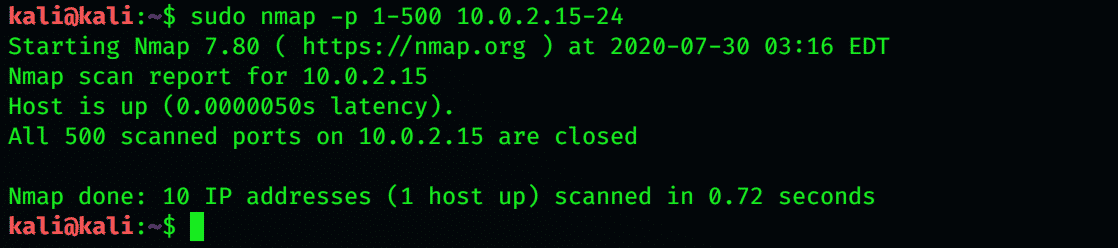
Port Range Scan
Fast Port Scan (100 ports) for Multiple IP Addresses
Port Scan within IP Address Range
Disable Host Discovery Port Scan Only
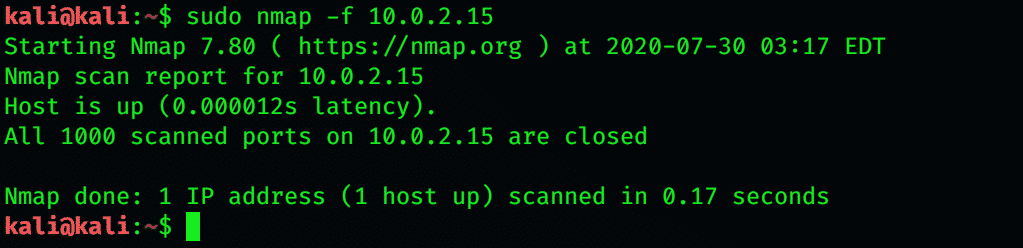
Requested scan (including ping scans) uses tiny fragmented IP packets. Harder for packet filters
s P is a ping sweep. Nmap gives you the option of using different tyles of ping sweep; the default is ICMP, but you can also use TCP syn and TCP act.
Conclusion
With the latest technology and tools, you can easily map the hidden information of any network. Nmap is a popular hacking tool used in Kali Linux for mapping and gathering information. This article gives a brief description of the use of Nmap. Hopefully, it will help you while using Kali Linux.