This blog will demonstrate:
- How to Install Hashcat in Kali Linux?
- How to Use Hashcat in Kali Linux?
- Bonus Tip: How to Use Kali’s Wordlists for Password Cracking
- Conclusion
How to Install Hashcat in Kali Linux?
Hashcat is an ethical hacking tool that is used by cybersecurity professionals for password cracking. It uses brute force and many other hashing algorithms to crack hashes or convert hashes to passwords. For this purpose, it uses different types of attacking modes. Hashcat is preinstalled in Kali Linux. In case, if it is not installed on Kali, install it by following the below steps.
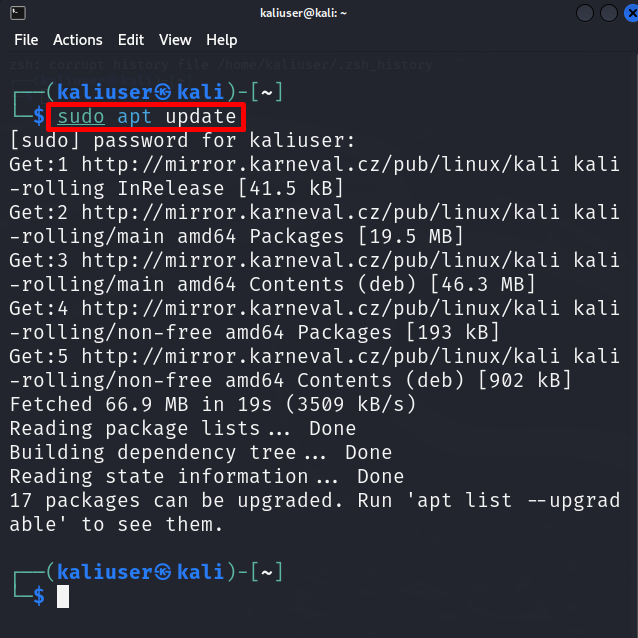
Step 1: Update Kali
First, update the Kali to the latest rolling release using the “apt update” command:
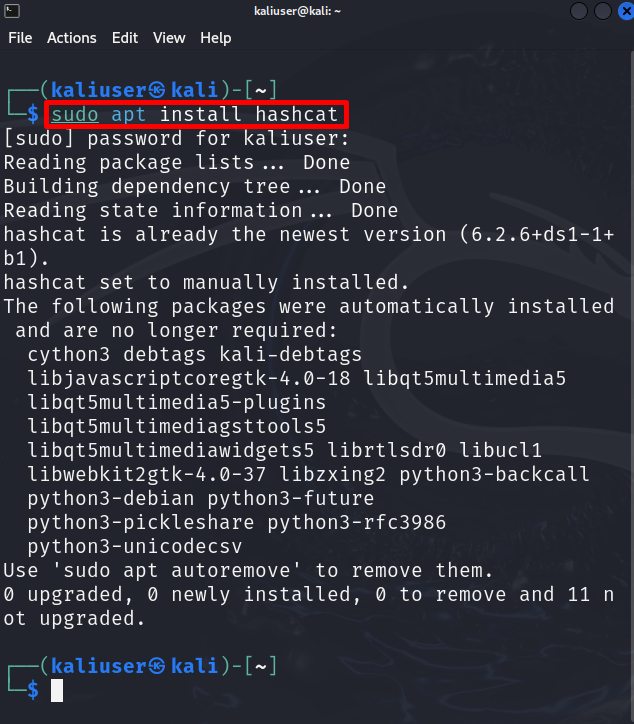
Step 2: Install Hashcat
Now, install the hashcat package in Kali using the “apt install hashcat” command:
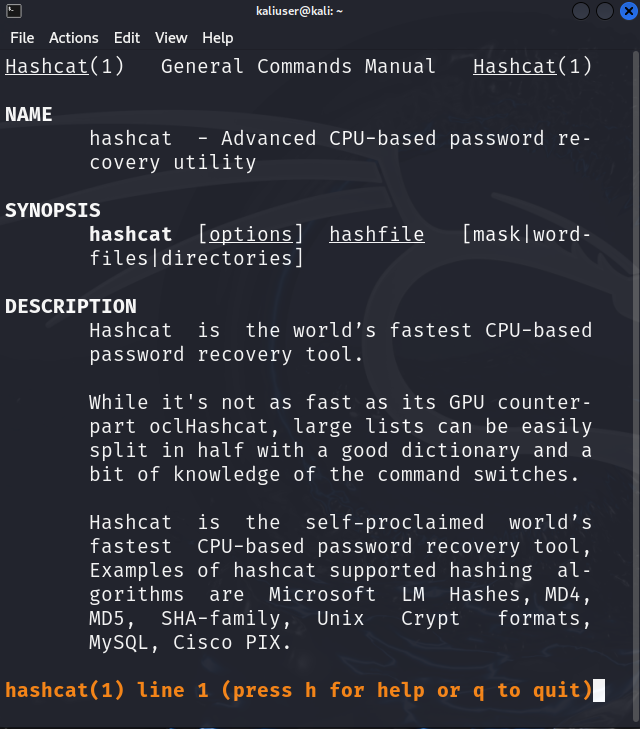
Step 3: Check the Hashcat Manual
To check the hashing algorithm code or to choose hashcat’s attack modes, check its manual using the below command:
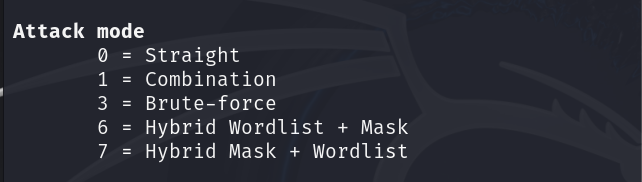
Attacking Mode
Here, you can see different attacking modes are available in the hashcat tool. A short description of these modes is as follows:
- Straight: Try to crack the password from a provided word list.
- Combination: Try to crack passwords by combining words from multiple wordlists.
- Brute-force: It applies the brute force technique and tries each character from the provided charset.
- Hybrid Wordlist + Mask: It combines wordlist and mask
- Hybrid Mask + Wordlist: It also combines mask and wordlist.
- Association Attack: It uses combinations of hints that are associated with a particular user password or field such as username, any personal information or file name:
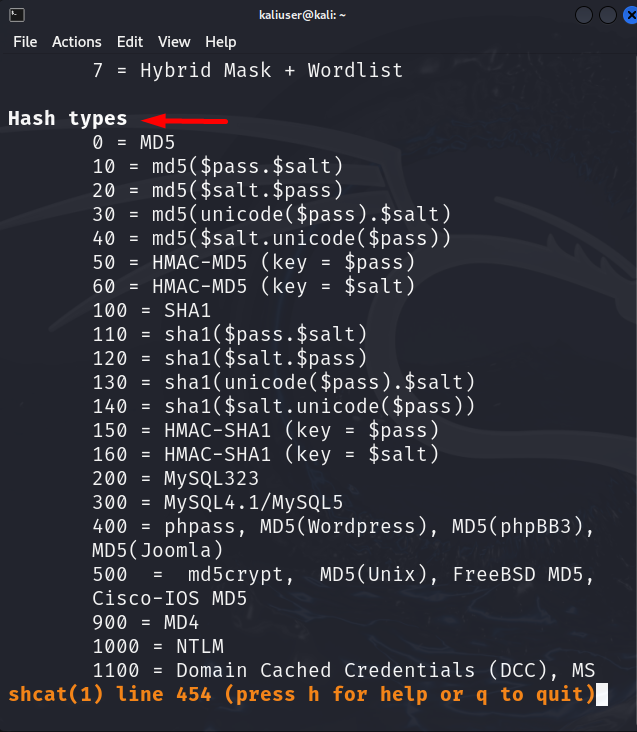
Hash Types
The types of hashes that are required to be cracked are stated in Hash types. The code of the hash type is used to crack the hashed password:
How to Use Hashcat in Kali Linux?
Hashcat uses CPU and GPU crackers in Kali Linux that efficiently crack the password from provided hashes. If you are using Kali Linux on a virtual machine, you are unable to fully use GPU crackers. However, hashcat works fine with CPU mode as well. To use hashcat either on the Kali system or the Kali virtual machine, the user must have at least 4 to 8 GB of RAM.
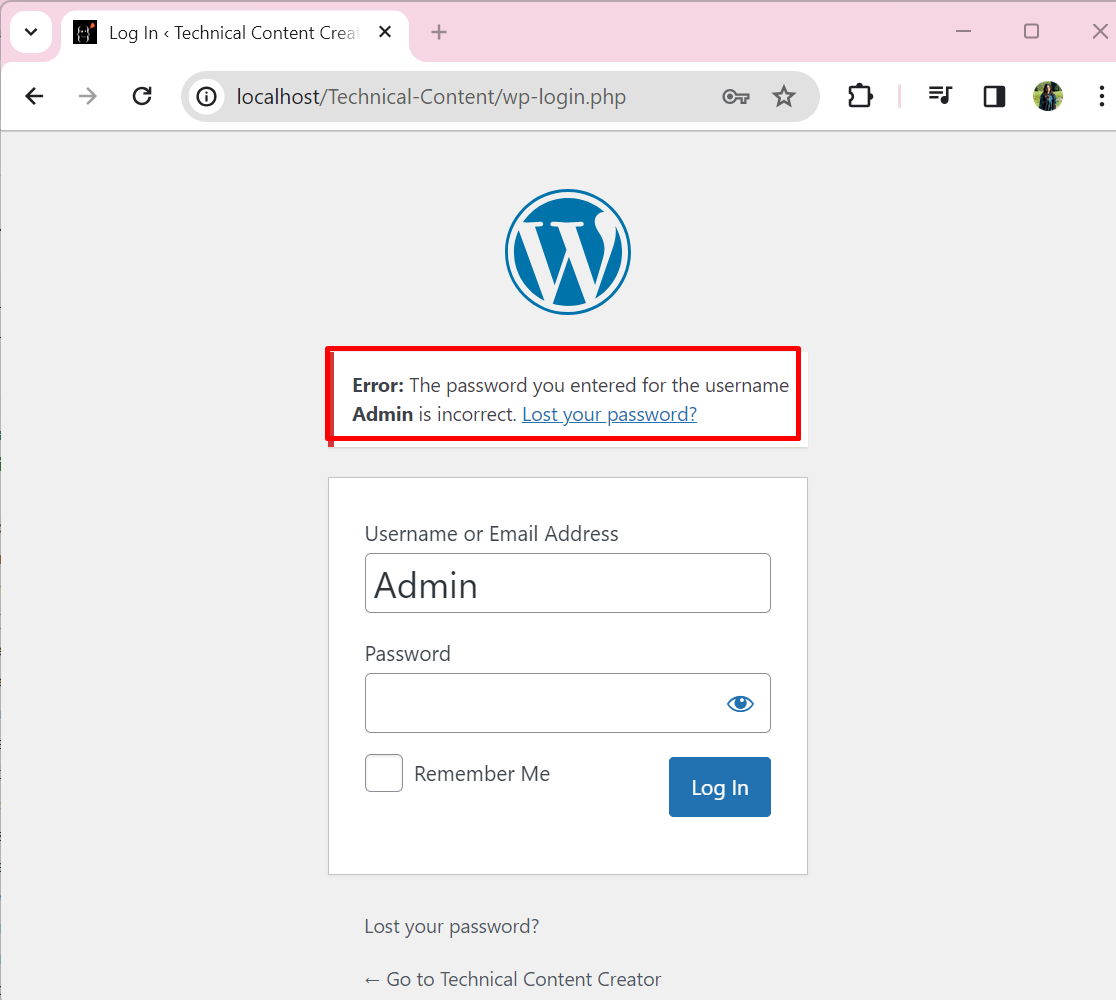
Let’s try to understand the use of Hashcat for password hacking by taking an example of a WordPress Website. Let’s suppose the user forgets the admin account password and is now unable to access the website dashboard as shown below:
Now, we will use the hashcat tool to recover the WordPress website admin’s forgotten password. For proper demonstration, follow the below procedure.
Step 1: Get Hashed Password
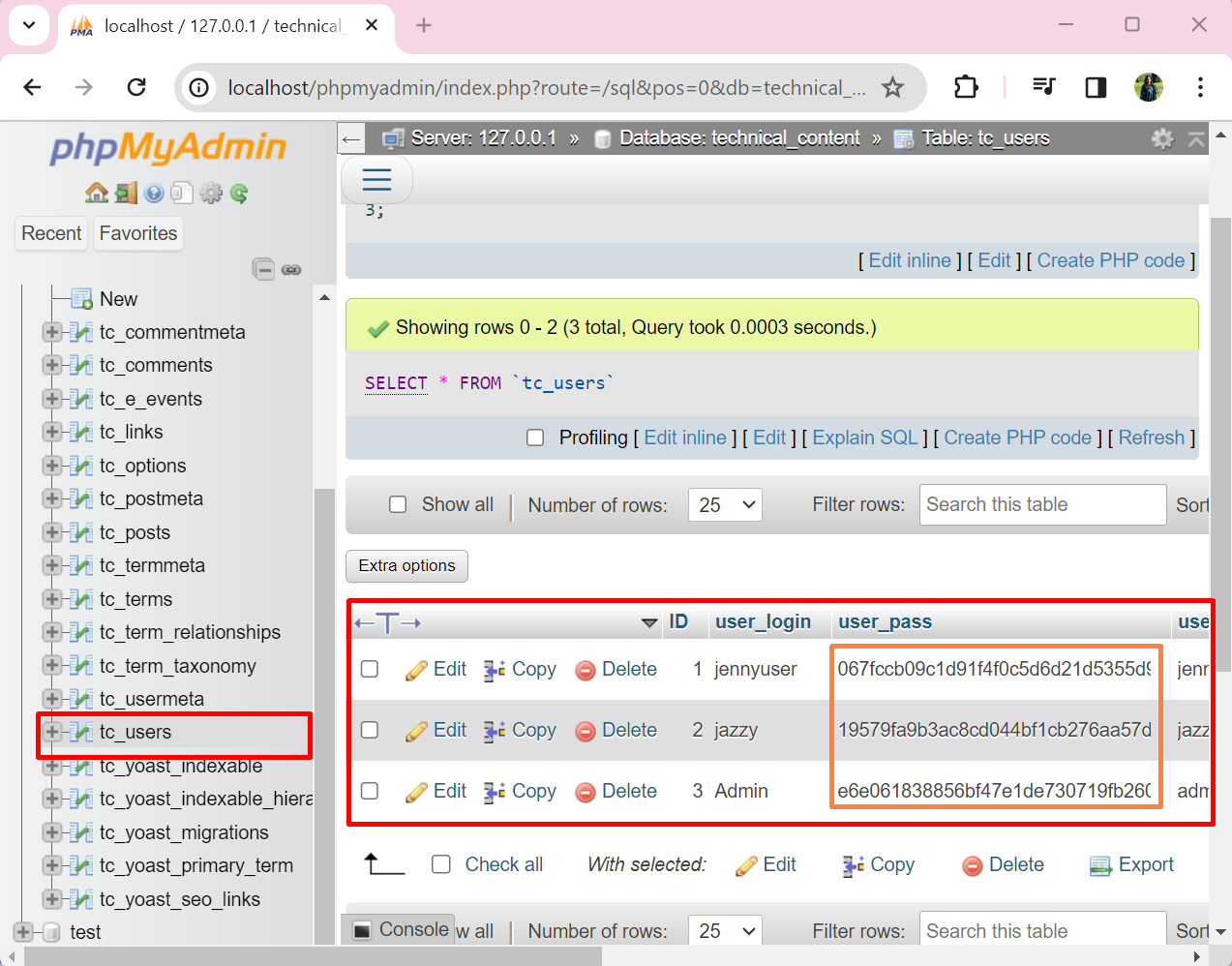
Admin users definitely have access to the WordPress database. Let’s get the encrypted hashed passwords of website users from the database:
Step 2: Save the Hashed Password in the Text File
Next, save the password hashes into a text file. Here, we are creating the “hashpass.txt” file in the “Desktop” directory by using the nano editor:
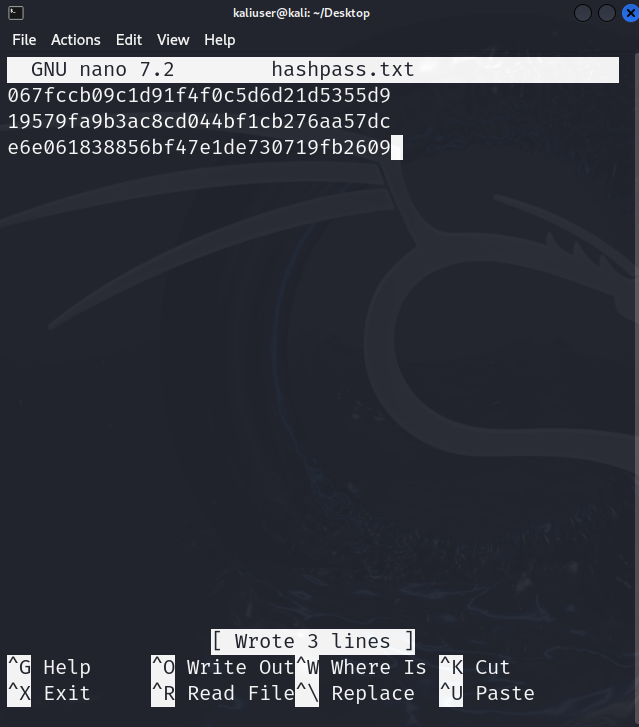
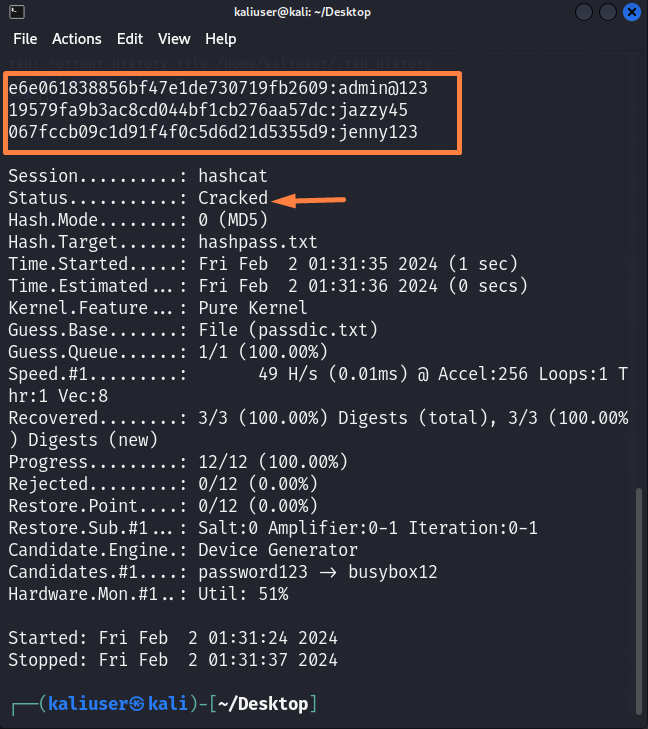
Save the password that is converted into hashes in the “hashpass.txt” file. For demonstration, we have saved three passwords that were already converted into hashed through the “MD5” hashing algorithm:
To save the file, press “CTRL+S” and to shut down the editor, use “CTRL+X”.
Step 3: Provide WordList Dictionary
Next, provide the wordlist dictionary from where the hashcat will try to match the hashes of words with the provided password hashes in the “hashpass.txt” file. For the demonstration, we will create our own wordlist that will contain 12 different passwords:
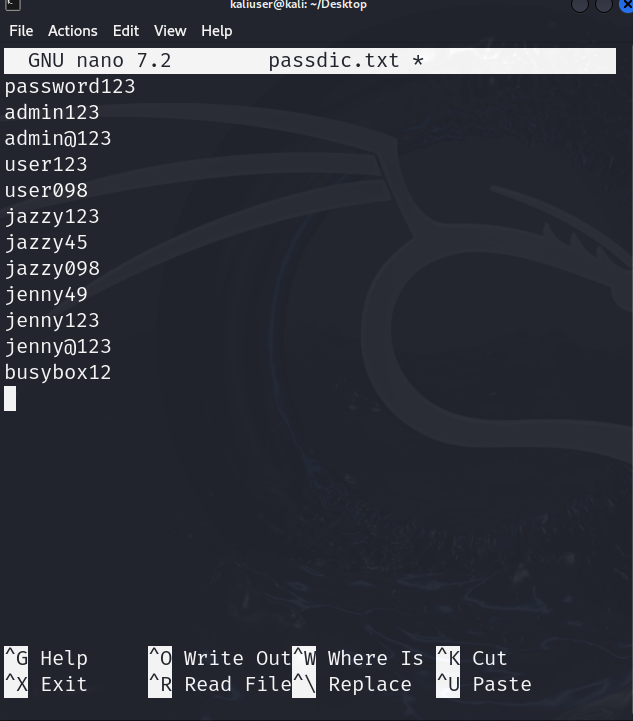
Here, we have saved different combinations of passwords in our “passdic.txt” wordlist. The user can also use Kali’s provided wordlist which is explained in below section:
Step 4: Crack the Password
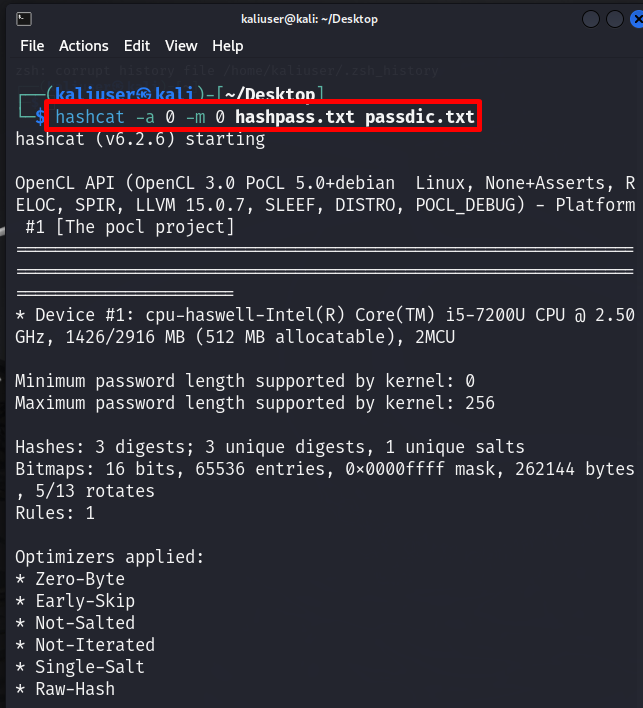
Now, crack the password using the “hashcat -a <attack mode> -m <hash-type> <path-to-hashpass.txt> <path-to-wordlist>” command:
Here, “-a 0” means we have used “Straight attack mode” and “-m 0” means we are converting MD5 hashes into passwords. So, we will apply the “MD5” hashing algorithm to match the hashes of “hashpass.txt” to the provided wordlist (passdic.txt):
Here, you can see we have effectively cracked the website password from the provided password hashes:
Step 5: Verification
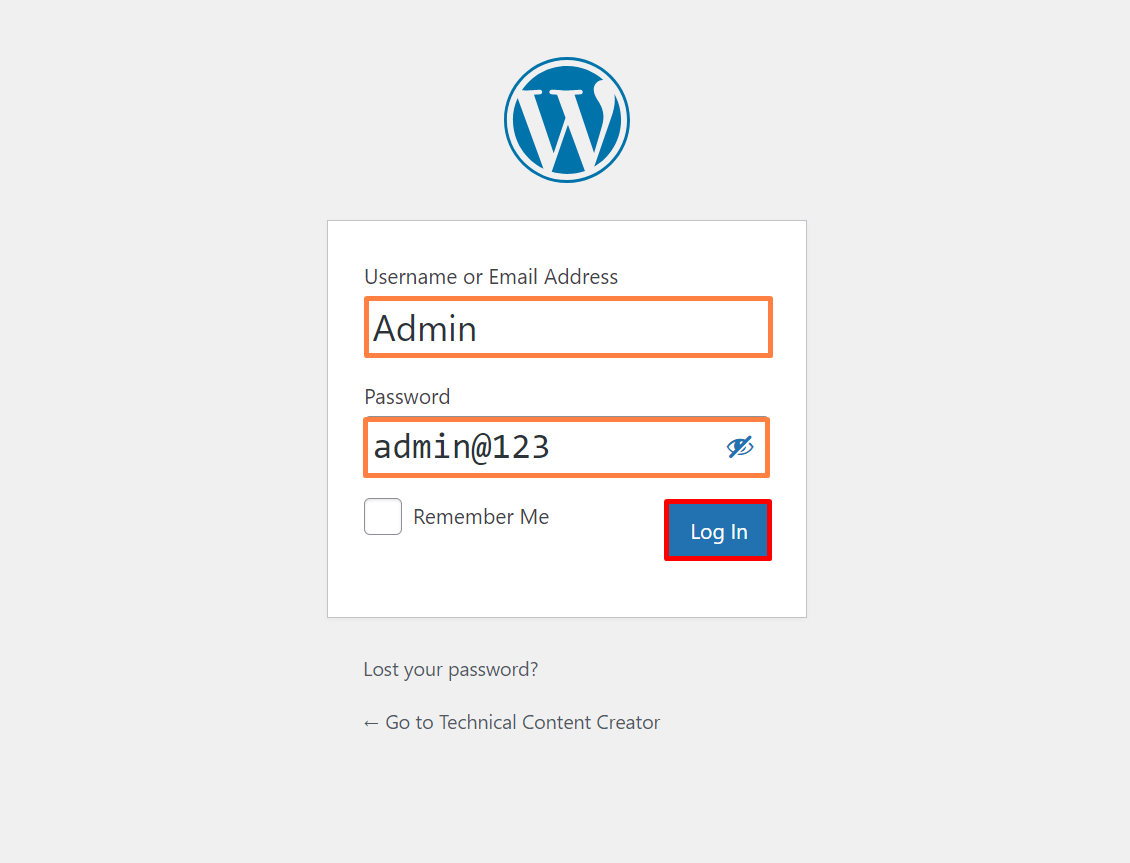
For verification, let’s try the admin password “admin@123” to access the WordPress website:
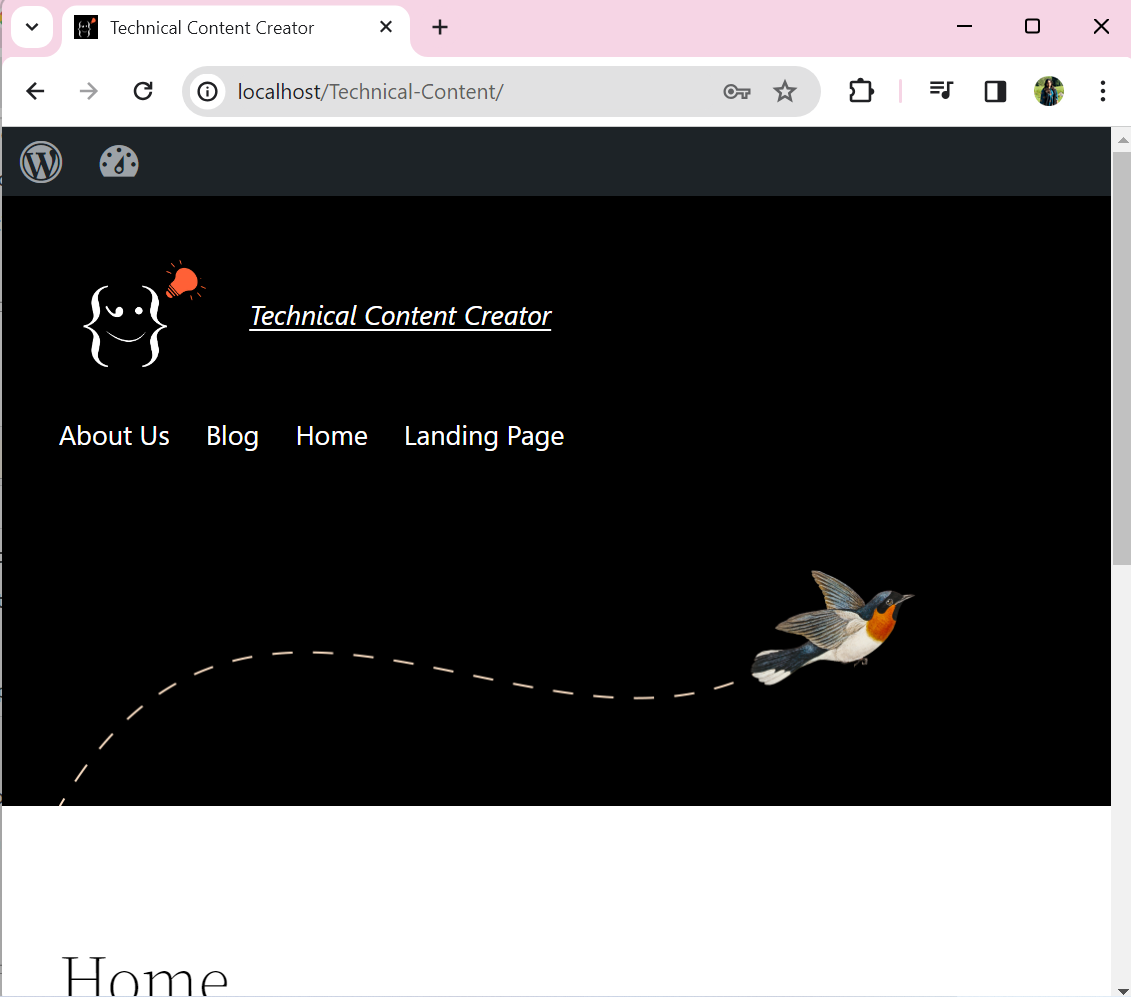
Here, you can see we have successfully recovered the forgotten password using Kali’s hashcat tool:
Bonus Tip: How to Use Kali’s Wordlists for Password Cracking
Kali Linux also provides a pre-installed Wordlist that will be used to crack different types of passwords. This wordlist contains millions of words and password combinations. To use Kali’s “rockyou.txt” wordlist for password cracking, follow the below steps.
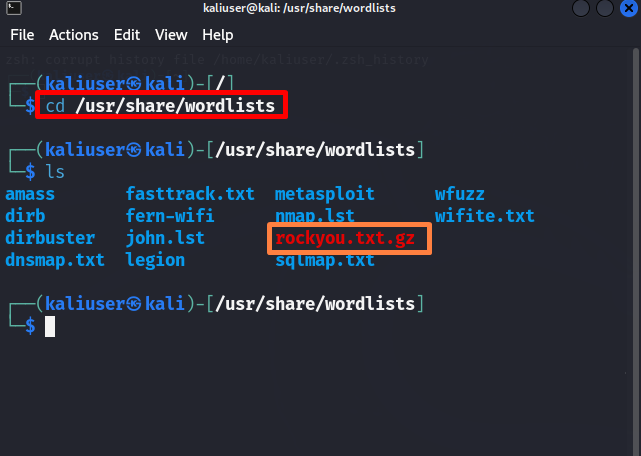
Step 1: Open “wordlists” Directory
To open the “wordlists” directory, utilize the given command:
Next, run the “ls” to view all files and directories of Kali’s “wordlists” directory. Here, different types of passwords or word lists are available. To track the normal or straight passwords such as user account passwords, you can use the “rockyou.txt” file:
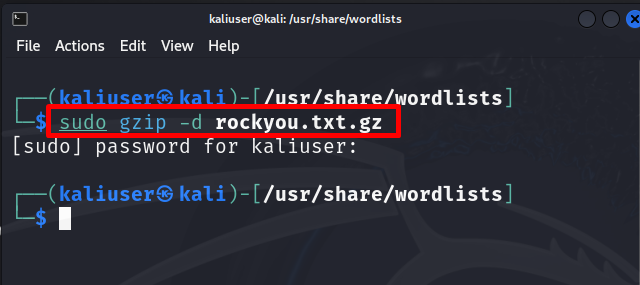
Step 2: Unzip the “rockyou.txt.gz” File
To use the “rockyou.txt” file in the hashcat tool, first, unzip the file using the “gzip -d rockyou.txt.gz” command. This action may require “sudo” user rights:
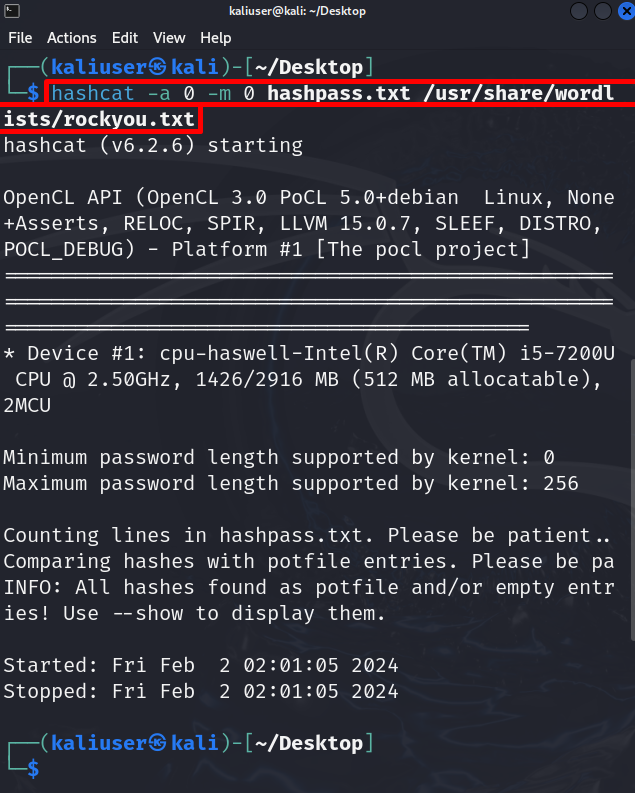
Step 3: Crack the Password
Now, use the hashcat command to crack the password.
Here, you can see this time we have used the “rockyou.txt” file instead of a personal wordlist:
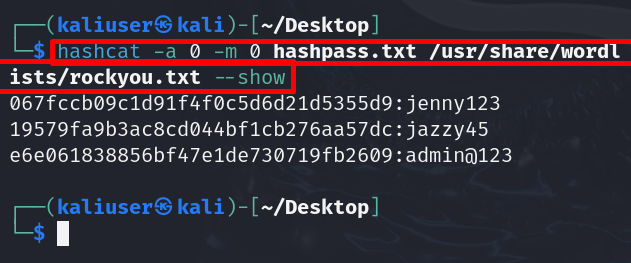
In the above output, you can see the hashes are found but cannot be viewed. To view the hashes, simply add the “–show” option in the hashcat command:
We have elaborated on how to use hashcat in Kali Linux.
Conclusion
To use the hashcat tool in Kali Linux, first save the passwords that were converted in the hashes in the “.txt” text file. After that, match the password hashes with a wordlist text file such as Kali’s wordlist file “rockyou.txt” file. For this purpose, simply use the “hashcat -a <attack mode> -m <hash-type> <path-to-hashpass.txt> <path-to-wordlist>” command. This post has demonstrated the use of hashcat on Kali Linux.