Penetration testing may involve interaction with different networks and routers that can also compromise Kali’s security.
This post will demonstrate:
How to Secure Kali Linux?
To secure the Kali Linux system, the user needs to follow some essential steps such as keeping the Kali Linux up to date, changing the default root password as it can be easily used by any unauthorized user, managing incoming and outgoing traffic by a firewall, browsing over the internet anonymously and many more.
To completely secure the Kali Linux, follow the below-listed steps.
Step 1:Update Kali Linux
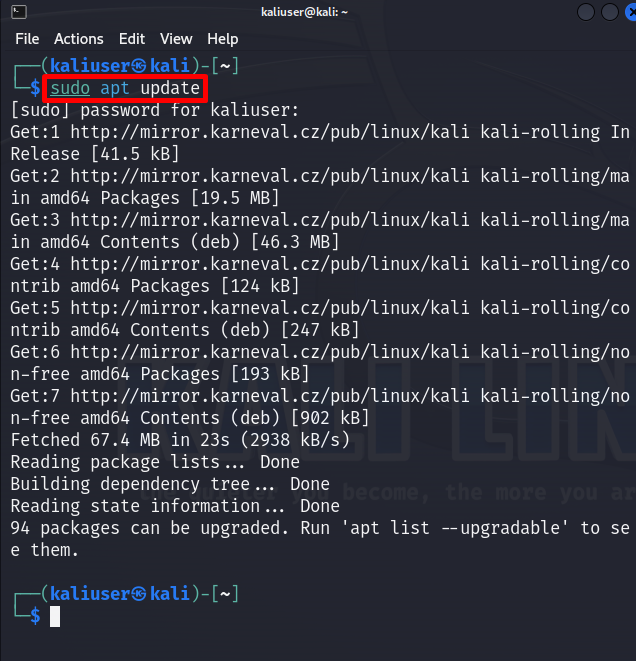
To secure the Kali Linux system, users need to keep the Kali image and repository up to date. For this purpose, launch Kali’s terminal using the “CTRL+ALT+T” key. Then, execute the “apt update” command:
This will update the Kali Linux with new rolling releases:
The above output shows that “94” packages are required to be upgraded. Upgrading the package with new features can also help to prevent Kali from security attacks.
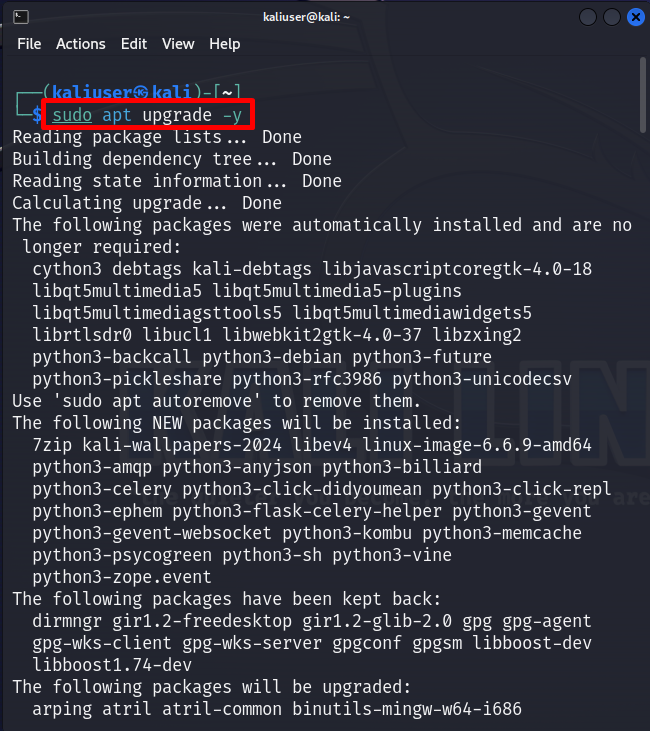
To upgrade the packages in Kali, run the “apt upgrade” command with “sudo” rights:
The “-y” option allows the operation to use the required disk space:
Step 2: Secure Your Identity
To secure the Kali system, users need to hide their identity by changing the hostname. Sometimes, users need to browse over the internet, this step will allow attackers to access your system through your identity. To secure your identity, we will recommend you download and use the “Tor browser”. This enables us to browse information or websites anonymously. To install the Tor browser, navigate to our associated article.
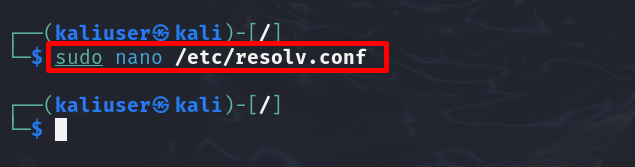
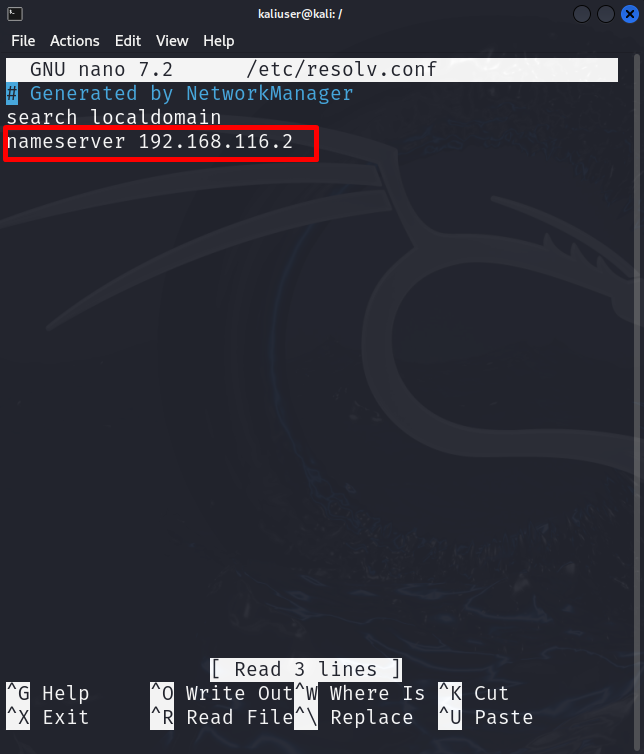
However, the user can also hide the identity by changing the hostname to “8.8.8.8”. For this purpose, first, open the “resolv.conf” file in any text editor as done below:
Next, replace the “nameserver” value with “8.8.8.8”. This will hide your real identity over the internet:
To save the changes in the nano editor, use “CTRL+S” and to exit the editor use “CTRL+X”.
Step 3: Unprivileged User Account
Directly using a root account on Kali is not a recommended option for security reasons. To secure your root account, the user needs to create an unprivileged account that is used as the root account but stands always lower than the root. We are already using an unprivileged account. So, to demonstrate the process, we need to log in to the root account.
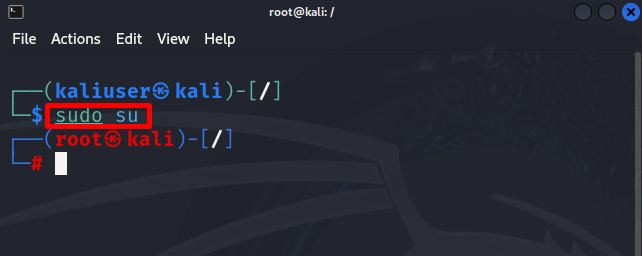
To log in to the root user terminal, utilize the “sudo su” command:
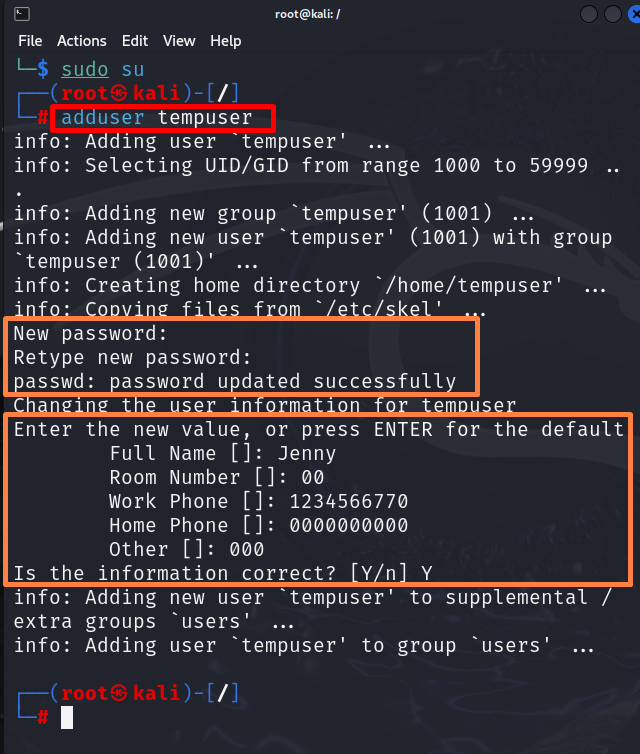
Then, add the new user in Kali Linux using the “adduser <user-name>” command:
This operation will encourage you to set new passwords for a new user and extra information such as Full Name, Room Number, Work Phone, and many more. We have added dummy information for illustration:
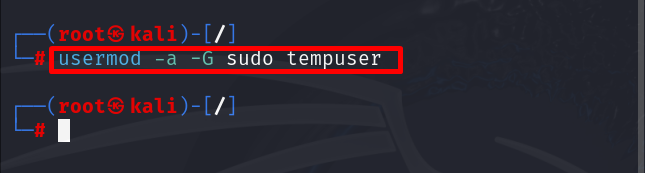
After creating the new user, add the user to the sudo user group to assign administrative privileges:
This all add the “tempuser” to sudo user group.
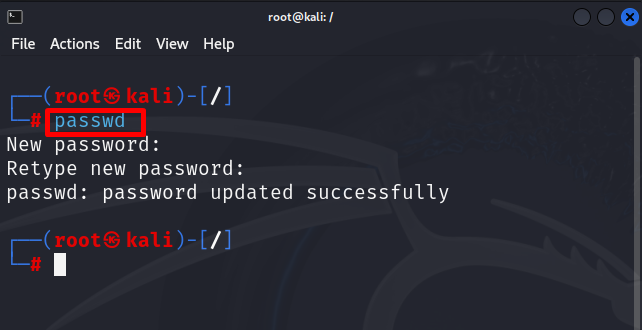
Step 4: Change Root Password
The default root password for Kali Linux is “toor” which can be easily accessible by any malicious user. It is not suggested to use the default Kali root password.
To modify the “root” password, open the root terminal using “sudo su”. After that, simply run the “passwd” command. This command will ask you to set a new password:
Here, we have updated the Kali root user password.
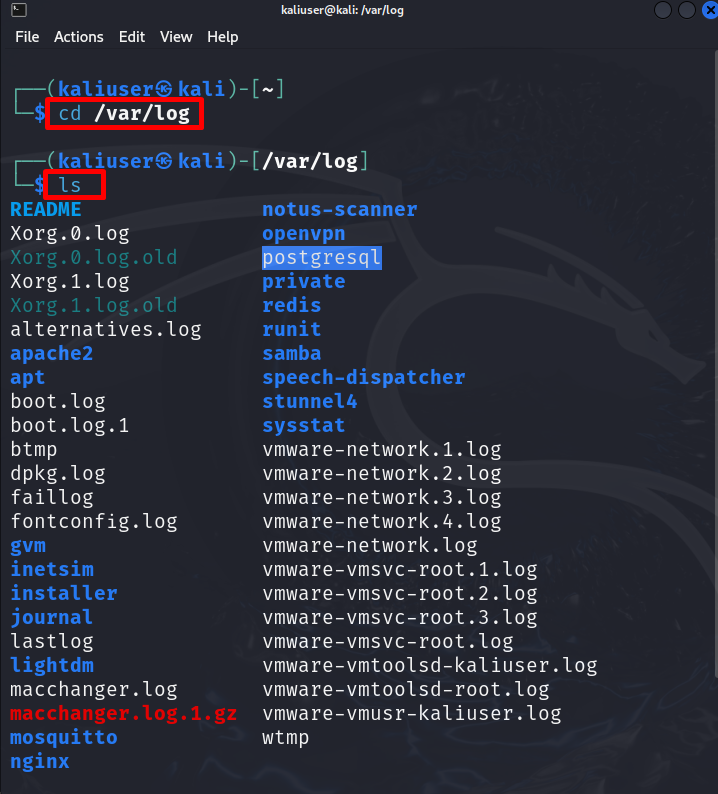
Step 5: Monitor Logs
To check for security risks, and to debug the problems and Kali’s errors, the user can monitor Kali’s log. This can also secure the Kali system. To monitor Kali’s logs file, navigate to the “/var/log” directory using “cd”. Then, run the “ls” to view the logs file:
ls
However, many logs monitoring tools are also available for Kali Linux such as “logcheck” or “Top”. Kali also provides the built-in “xfce4-taskmanager” tool to view and monitor the running task on the system.
To launch the Task Manager tool, open the Kali application menu and search for “xfce4-taskmanager”. After that, launch the below-pointed tool:
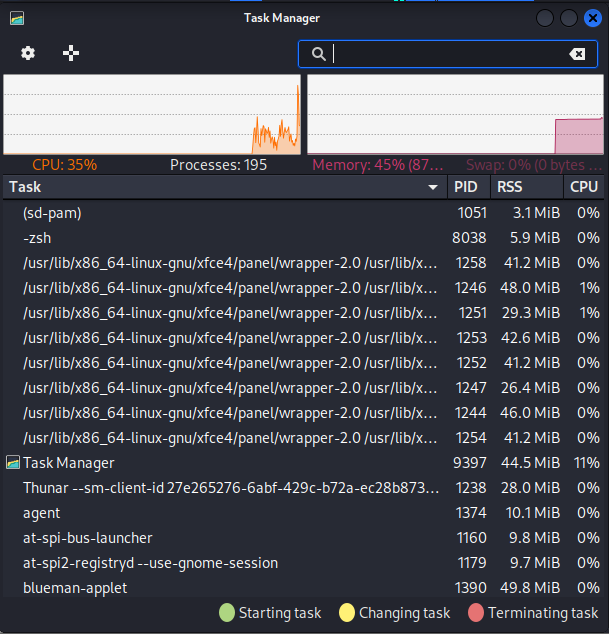
From the below Window, the user can view running tasks and processes. They can also manage and terminate malicious tasks:
Step 6: Change Default SSH Key
SSH key is a real risk to Kali’s security as it is a crown jewel for remote access to the system. The attackers can use stolen keys and easily access the user’s sensitive data. As Kali is also used for attacking purposes, its security can be compromised. So, we suggest you update the SSH keys for Kali.
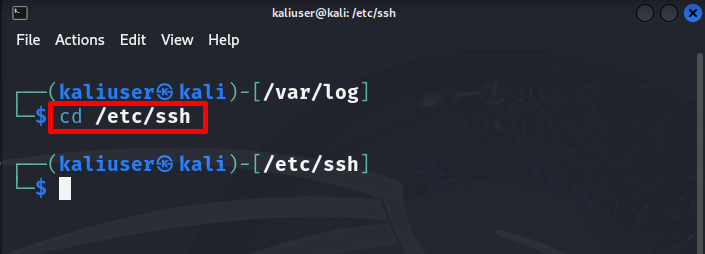
To generate the new SSH key, try to create a backup of the old SSH keys. For this purpose, first, navigate to the “/etc/ssh” directory:
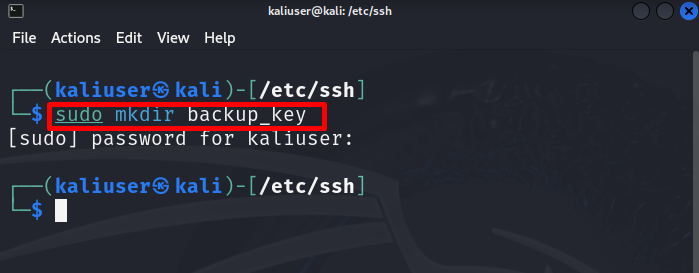
Next, create a new backup directory using the “mkdir <directory-name>” command. This may require root privileges. We have created the “backup_key” directory:
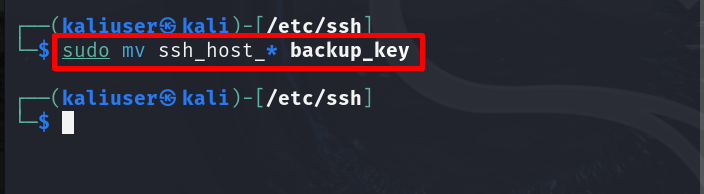
Move all the “ssh_host” files to the backup directory using the below command:
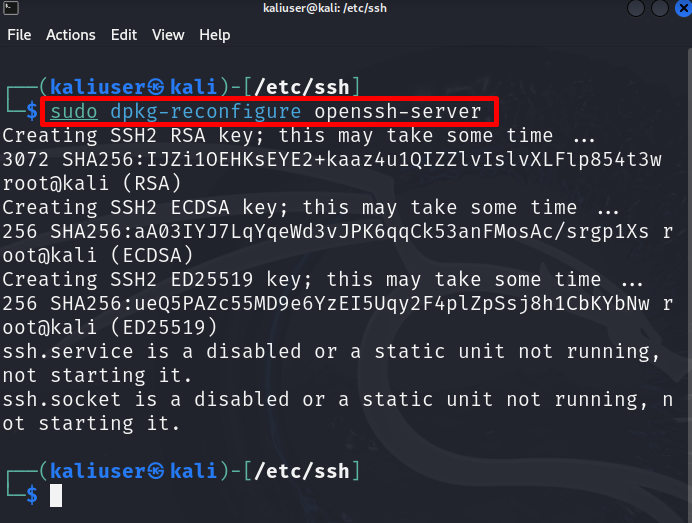
Now, generate the new SSH keys using the below command:
Step 7: Firewall Configuration
To control and manage the Kali incoming and outgoing traffic, install the Linux Firewall administrative tool. This will enable us to set rules for online traffic.
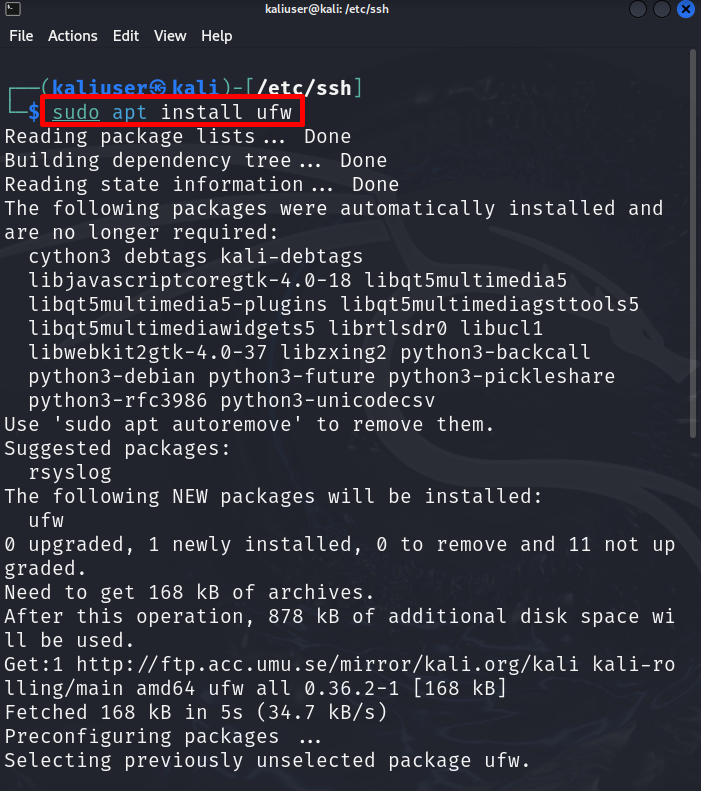
To install the Firewall tool on Kali, run the given command:
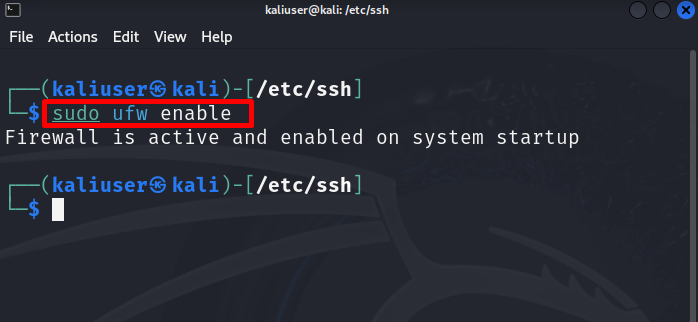
After installing the firewall, enable it on the system using the “ufw enable” command:
To manage incoming traffic or to explicitly allow the incoming traffic, set its default rule as “deny”. For this purpose, execute the below command:
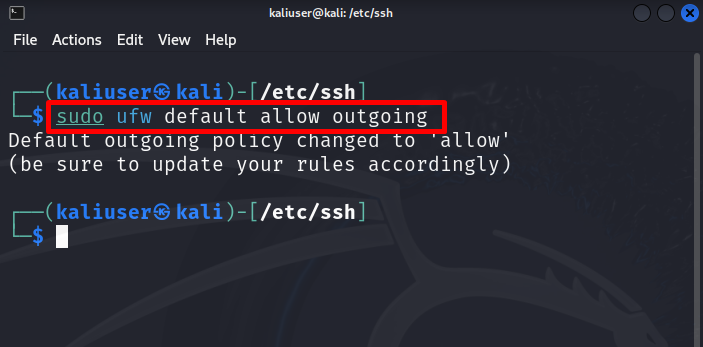
Then, set the default rule for outgoing traffic as “allow” to browser data on the internet or access any online source:
These are the steps that can completely secure Kali Linux.
Conclusion
To secure Kali Linux completely, users need to follow some essential security steps such as changing the default root password, browsing over the internet anonymously, generating private SSH keys, configuring a Firewall to manage traffic, and monitoring Kali’s logs. We have covered the steps to secure Kali Linux.