What Is Proxychains?
Proxychains is an open-source tool that is used for tunneling the connections through proxy servers. Through the utilization of a network of middle servers, it enables the users to access the internet invisibly. Users can do this to conceal their true IP address, making it challenging for others to monitor their online actions. This application is especially helpful for people who want to access the geo-restricted content, get around internet censorship, or maintain their online privacy.
Setting Up Proxychains
Proxychains is only compatible with Unix-based operating systems, including Linux and macOS, so it can’t be installed in Windows. However, you can use the Windows Subsystem for Linux (WSL) and follow the Linux installation process. Follow these instructions to set up Proxychains.
1. Update and Upgrade the System
Let’s start with updating your Linux system first to ensure that everything works better. Open a terminal and run the following full upgrade command:
sudo apt update -y && sudo apt upgrade -y && sudo apt dist-upgrade -y
2. Install Proxychains
Proxychains is pre-installed within some Linux distros, especially in the cyber security field such as Kali Linux. But, if you have not installed Proxychains yet, open a terminal and use the following command to install it:
For macOS users, you can use and easily install Proxychains by typing the following command:
3. Configure Proxychains
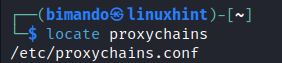
Once Proxychains is installed, you first need to edit a few configurations on the Proxychains configuration file that is located at /etc/proxychains.conf.
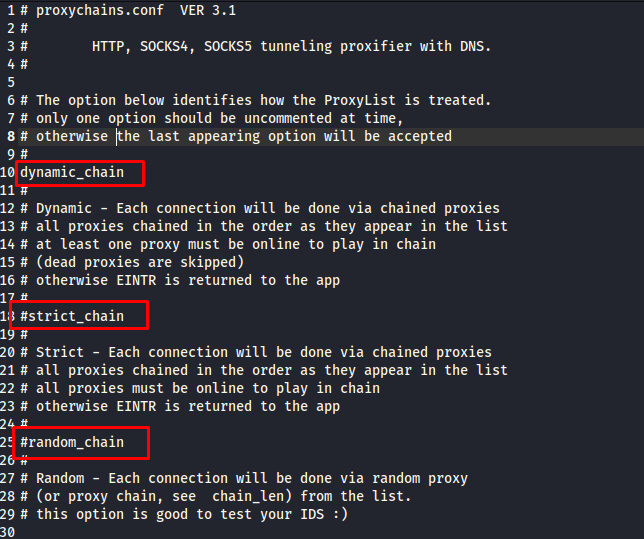
Open the configuration file using any text editor such as Nano, Gedit, Vim, or Mousepad. On the top line of the file, you will see the different options or methods of proxy chaining such as the Dynamic chain, Strict chain, and Random chain. Only one option should be uncommented at times. Otherwise, the last appearing option will be accepted.
Dynamic Chain
Each connection is done via the chained proxies; all proxies are chained in the order that they appear in the list. At least one proxy must be online to play in the chain (dead proxies are skipped). Activating the dynamic chaining allows for greater anonymity and trouble-free hacking experience. To enable the dynamic chaining, in the configuration file, uncomment the “dynamic_chain” line.
Random Chain
Random chaining allows the proxychains to randomly choose the IP addresses from our list. Each time we use proxychains, the chain of proxy looks different to the target which makes it harder to track our traffic from its source.
Strict Chain
Each connection is done via the chained proxies. All proxies are chained in the order as they appear in the list and they must be online to play in the chain.
How to Chain Multiple Proxies with Proxychains
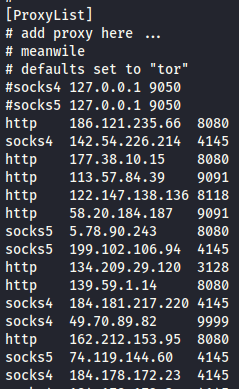
To chain multiple proxies, scroll down to the bottom of the file under the “Proxy List” section. Add the IP addresses and ports of the proxy servers that you want to use in succession. The traffic is forwarded through each proxy in the order that is specified in the configuration file. Proxychains could handle several protocols such as HTTP, SOCKS4, and SOCKS5. The format of inputting into the proxy list is as follows:
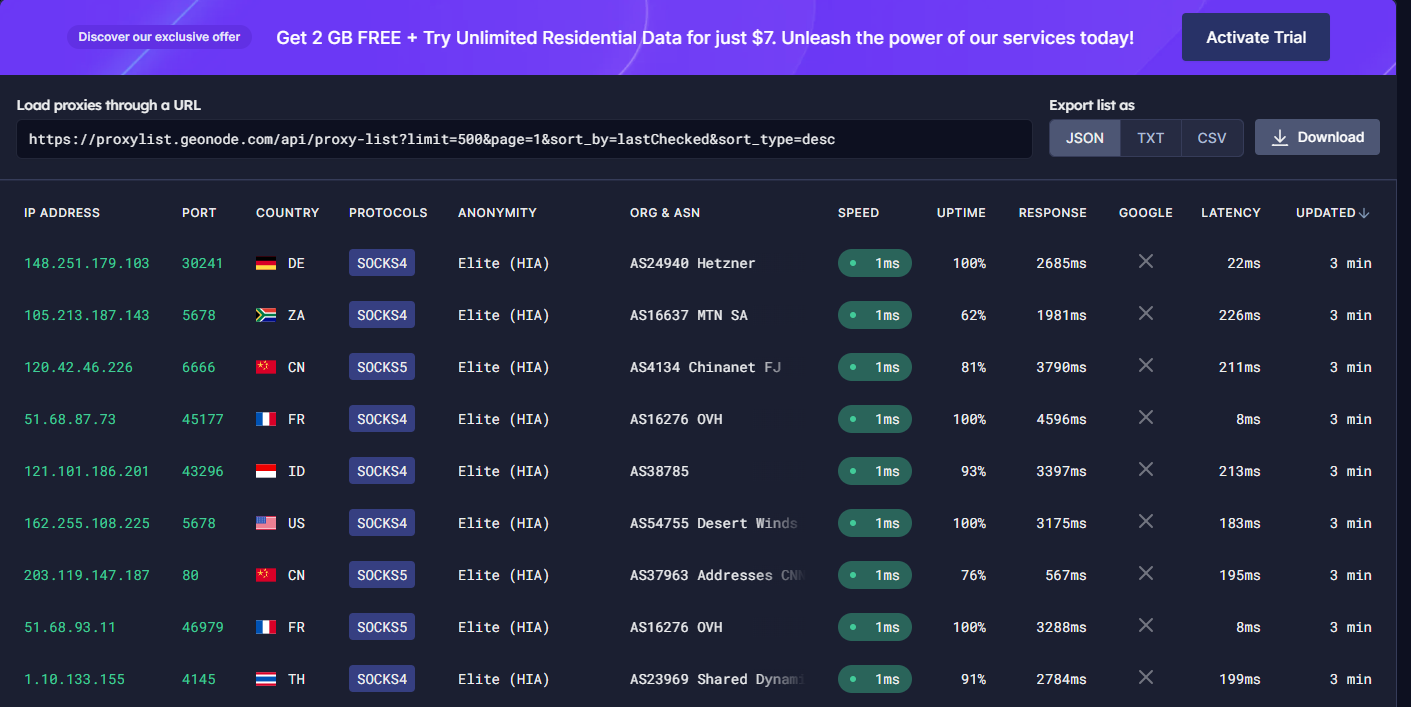
First, we need to search for some proxy servers. Actually, there are a lot of websites that provide free proxy servers such as Geonode.com. Go ahead to that website and select as many proxies as you want.
But please reduce your expectation if you are using a free service. Sometimes, those proxies are overworked or even dead. Use the premium instead if you take this privacy matter seriously.
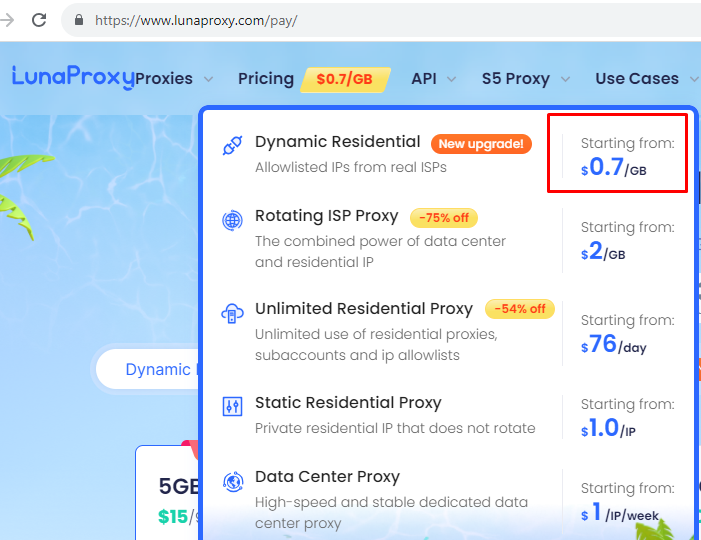
Don’t worry, we have done several trials on the proxy server provider which offers high-speed connectivity, super anonymous, and yet the most important thing is it needs less budget. If you have a high value of your internet data and privacy, you should try LunaProxy. It has a high-quality dynamic residential proxy IP network that helps you to bypass the country restrictions and website blocking which provides 200 million real residential IP proxies around the world, supports SOCKS5 and HTTP proxy protocols, and is super anonymous. LunaProxy also often shares a lot of discount coupons on its page. The price starts from $0.7 cent per GigaByte; it won’t affect your wallet though.
Go ahead and get your Luna Proxy here.
Once you get the proxy server, input the proxy list in the Proxychains configuration file with the format as shown in the following image:
The configuration file is case-sensitive, so make sure to input all in lowercase for the protocols. If you input “HTTP” or “SOCKS4” rather than “http” or “socks4”, it raises an error when you run Proxychains.
Save and Test
Save the changes to the configuration file and close it. Now, let’s test Proxychains. Open a terminal and type the following:
Replace <your_command_here> with any command that requires internet access such as a web browser, Nmap, Curl, etc. If it is configured correctly, the command’s traffic is routed through the chained proxies.
Increase Anonymity with Multiple Proxies
Chaining multiple proxies with Proxychains offers an additional layer of anonymity which makes it harder for adversaries to track your online activities. Here’s how multiple proxies contribute to increased anonymity:
1. IP Address Hiding
Each proxy server in the chain hides your real IP address and replaces it with its own. Using multiple proxies, your online presence is concealed under several layers of anonymity, making it extremely challenging for anyone to determine your actual identity or location.
2. Traffic Encryption
Many proxy servers support encryption protocols such as SSL or TLS. When you use multiple proxies with encryption, the data that passes through them becomes highly secure and encrypted. This prevents the hackers and eavesdroppers from intercepting a sensitive information.
3. Randomized Routing
Proxychains can be configured to use the random proxies from the chain for each connection. This feature further obfuscates your digital footprint as your traffic appears to be coming from different locations at different times.
Best Practices for Using Proxychains
While Proxychains can significantly enhance your online anonymity, it’s essential to follow some best practices to ensure the maximum security and effectiveness:
1. Use Trusted Proxies
Always choose the reputable and trusted proxy servers to include in your chain. Avoid using public proxies with unknown origins as they might compromise your privacy or even engage in malicious activities.
2. Regularly Update the Proxy List
Keep your list of proxy servers updated and remove any non-functional or unreliable ones. Fresh proxies can provide better performance and increased security.
3. Avoid Logging In
When using Proxychains for anonymity, refrain from logging into personal accounts or sharing sensitive information as some websites may still be able to track you through browser cookies and other means.
4. Combine with VPN
For an added layer of security, consider using Proxychains in conjunction with a Virtual Private Network (VPN). This combination further obscures your online identity.
Conclusion
Proxychains offers a potent option for obtaining better anonymity and security at a time when online privacy is crucial. Users can effectively mask their genuine IP addresses and conceal their digital identities from prying eyes by chaining many proxies together. To maintain a secure and productive browsing experience, you must use this tool carefully and in accordance with the best practices. So, give Proxychains a try if you respect your privacy and you wish to browse the web anonymously. Don’t risk your online privacy and security; arm yourself with Proxychains right away instead.