When a penetration tester conducts web information gathering on a domain, they may not only target the main domain but also go deeper into the subdomain parts.
In this tutorial, we will learn the following topics in detail:
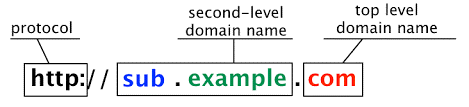
- The domain hierarchical structure
- Top-level domain and second-level domain
- Subdomain
- Enumerate the subdomain with Sublist3r in Kali Linux
- The most common error of using Sublist3r
What Is Subdomain
Subdomains are used to separate a section of a website from the main website. Subdomain names are placed before the second-level domain. For example, the most popular big company like Google separates its service into its subdomain – the Google mail service (mail.google), Google maps service (maps.google), Google cloud storage (drive.google), and many more. Not only do subdomains make a better organization of the various website functions, but they also make it easy for the users to recognize. The most common subdomain function that is used include a forum or community, the mobile version of the website, a specific location or language, a blog, and an eCommerce.
In making this tutorial, we prepared some of my favorite reliable tools to do the task of finding the subdomains namely Sublist3r and SubDomainizer. We briefly review why we end up using Subfinder.
The Best Kali Linux Tool to Enumerate the Subdomains
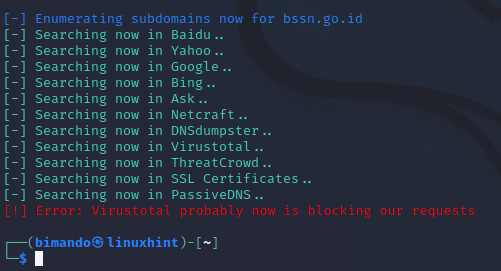
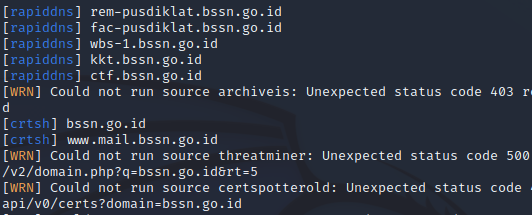
Sublist3r is a tool that we must use since a few years ago. But now, Sublist3r has more and more errors. Many users submit the bugs on the Sublist3r GitHub page. The developers from the Sublist3r have not made any updates or improvements to these bug findings in recent years. The first and most common error that is experienced by the users is that Sublist3r does not display any results even though there are no errors. After we analyzed the Sublist3r Python script, it turns out that there was an error in the base_url request on each search engine and service. The syntax to extract the subdomains is also found.
The second common error is regarding the use of the Virustotal service which cannot run, resulting in an output error that says “error: Virustotal probably now is blocking our requests sublist3r“. This is because the users are required to use the API token to use Virustotal. However, sublist3r did not find any arguments or configurations to add the API token.
It’s very unfortunate indeed. My flagship tool can no longer be used. Actually, we could dissect the script and fix the bugs one by one according to the analysis that we previously found. However, the material that we write here is about how to use a tool to achieve certain goals, not about troubleshooting.
Then, we look for other alternative tools which have the similar features as Sublist3r. We found two tools that interest me namely SubDomainizer and SubFinder. Both of these tools have the same goal which is to find the subdomains. We try both of these tools. There are no significant problems in the installation of each tool. The first one that we try is the SubDomainizer. When running the SubDomainizer, there is no option to display the verbose; the enumeration process takes too long.
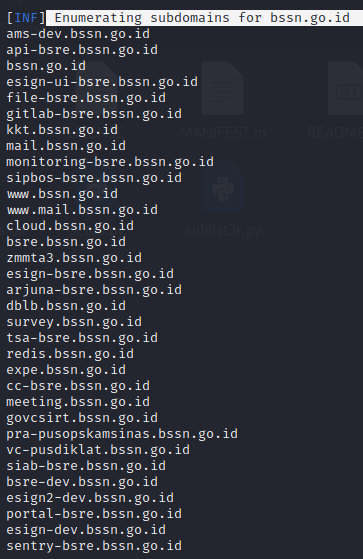
While waiting for the SubDomainizer to run its action, we then run the SubFinder which targets the same domain. The results are truly extraordinary. We are amazed at the speed with which the SubFinder enumerates the subdomains of a website.
After about 15 minutes, finally, the SubDomainizer finished running its enumeration process. We are a little disappointed that the SubDomainizer did not found as many as the SubFinder despite the long time process it takes.
Finally, we use the SubFinder as the best alternative to Sublist3r.
Install SubFinder in Kali Linux
SubFinder is originally built with the Go language. You can check the project on the SubFinder GitHub page at https://github.com/projectdiscovery/subfinder. But SubFinder also comes as a tool in the Kali Linux package at https://www.kali.org/tools/subfinder/. Installing Subfinder on Kali Linux is quite simple using the apt install command. Run the following command:
How to Use the SubFinder in Kali Linux
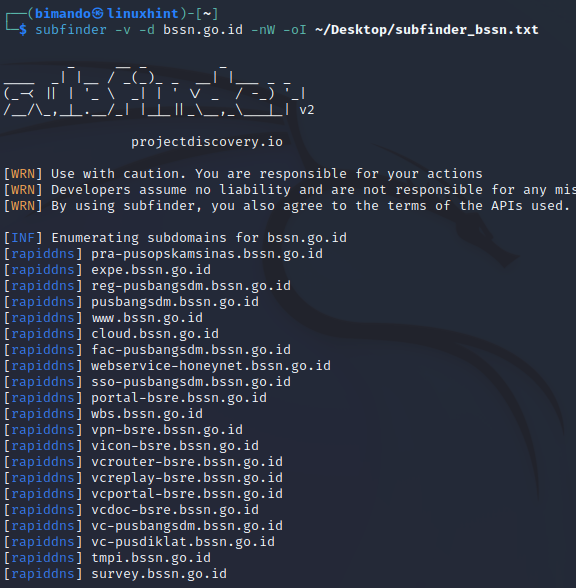
Let’s take a look at the usage of the SubFinder’s interesting command:
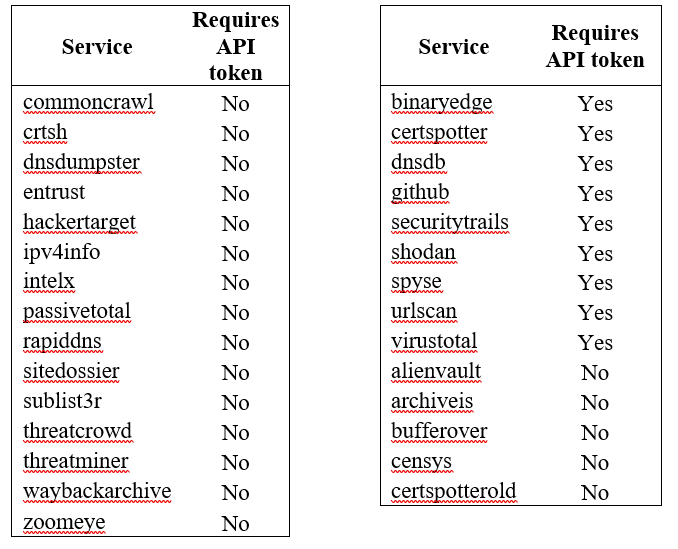
SubFinder Sources
SubFinder uses a passive reconnaissance to gather the subdomains using the following services. You can display the list using the -ls switch:
Among the bunch of service sources that the SubFinder use, there is some service that requires an API token such as Shodan, Virustotal, GitHub, SecurityTrails, and many more. You can add the API keys on the configuration file which is located under your home folder at /.config/subfinder/config.yaml.
SubFinder Verbosity
It got me more interest when a tool provides a verbosity feature. By activating verbosity, we can see what is going on in the running process. You can use verbosity in SubFinder using the -v switch.
SubFinder Logging
SubFinder provides output logging with three different styles which are:
| -o | Write the subdomains only. |
| -oI | Write in HOST & IP address format; this argument requires -nW switch, |
| -oJ | Write in JSON format. |
SubFinder Simple Command
You can run the SubFinder with the default setting by simply running the following command:
My favorite command is combining all of the interesting features that we previously learned:
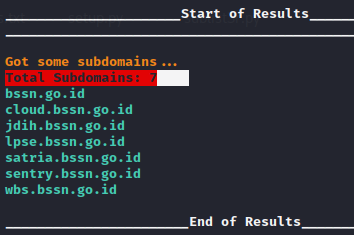
The final output result, since we used the HOST and IP address format, is shown in the following:
Conclusion
Hackers often set the scope of a target to be wider. They are not only targeting the main site but also doing assessments of the target subdomains. By doing that, they could enumerate more possibilities of the potential vulnerability of the target. In this tutorial, we intend to use the Sublist3r, but it is now an outdated tool. You might use another alternative tool when it is not worth to do a troubleshooting.