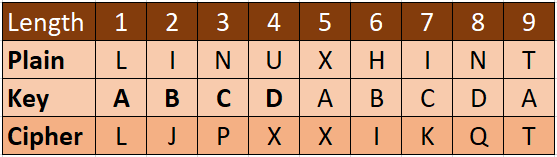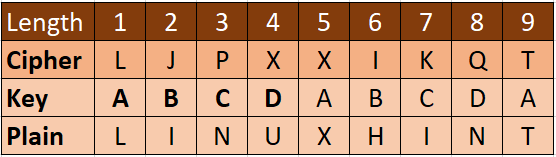Topic of Contents:
- Understanding Tabula Recta
- Vigenère Cipher Key Generation
- Vigenère Cipher Encryption
- Vigenère Cipher Decryption
- Conclusion
- Frequently Asked Questions (FAQs)
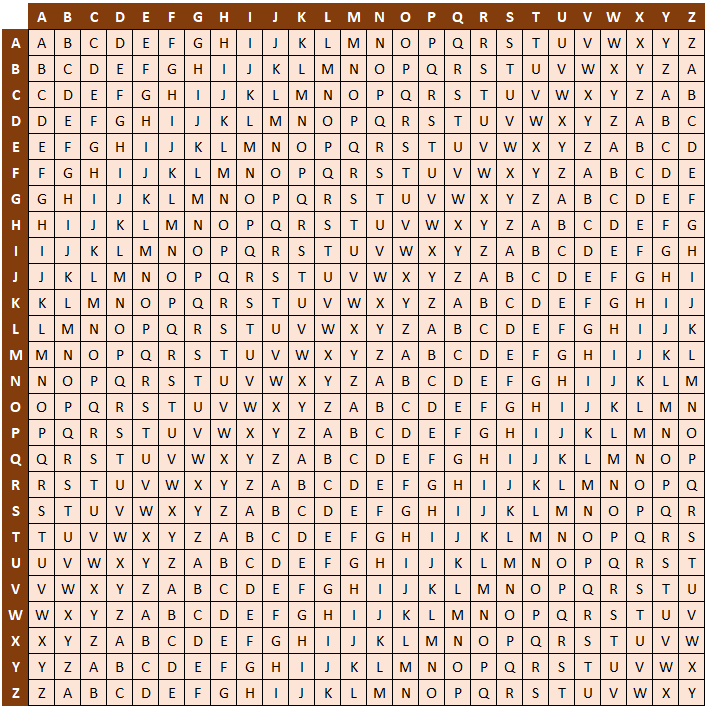
To learn the technical details of the Vigenère cipher, we need to understand first the concept of Tabula recta. The Tabula Recta is a table that is used to facilitate the encryption and decryption of the Vigenère cipher. Here is what it looks like:
Alt-image & caption: Tabula Recta
Take a look at the previous Tabula Recta. What do you think is it? The simplest way to understand Tabula Recta is a 26×26 table consisting of alphabetic text using a series of Caesar ciphers with one key backward, vertically and horizontally.
You might notice the difference in usage between the vertical (row) and horizontal (column) alphabet headers in Tabula Recta. Tabula Recta consists of three components which are:
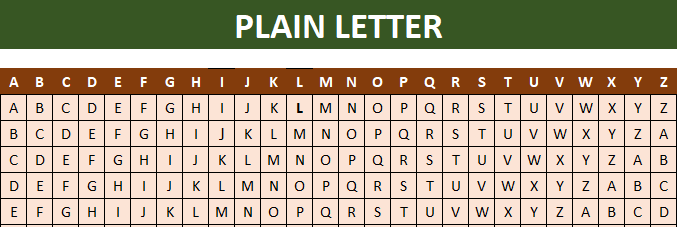
The Plain Letter Header
The Plain Letter header is represented in the form of sequentially alphabetic order horizontally (columns).
Alt-image & caption: Tabula Recta – Plain Letter Header
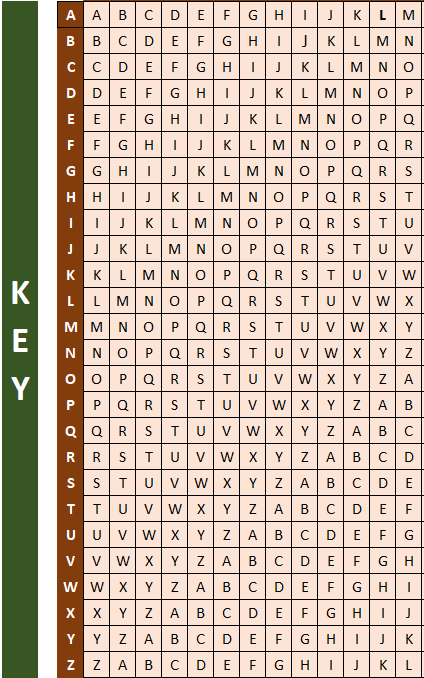
The Key Header
The Key header is represented in the form of sequentially alphabetic order vertically (rows).
Alt-image & caption: Tabula Recta – Key Header
The Cipher Letter
This is the alphabet which is the meeting point between the input and the key. For example, the plain letter of “K” and the key value of “C” result in the cipher letter of “M”.
Alt-image & caption: Tabula Recta – Cipher letter
Vigenère Cipher Key Generation
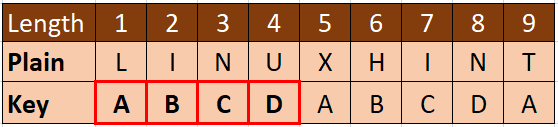
Different from Caesar cipher, where it is a monoalphabetic substitution, Vigenère cipher is a polyalphabetic substitution that shifts using multiple substitution alphabets. The secret relies on the meeting point of the input and the key. The key that is used in the Vigenère cipher must follow the following conditions: the key length should be the same length and cannot be larger than the input text. If the key is less than the input text, the key will be repeated until it matches the length of the input. For example, we want to encrypt the “LINUXHINT” plaintext with the “ABCD” key. The input has nine characters, while the key has only four characters. We need to generate by repeating the sequence of keys until it has the same length as the input (plaintext). So, the key would be “ABCDABCDA”.
Alt-image & caption: Vigenère Cipher Encryption
You have a strong foundation of Vigenère cipher. Now, we come to the technical details on how to do the Vigenère cipher encryption and decryption. The idea is to match the input and the key to generate the output.
Vigenère Cipher Encryption
With the given “LINUXHINT” plaintext, we want to encrypt it using the “ABCD” key. Using Tabula Recta, we match the meeting point from each input and key. For example, the first input of “L” and the key of “A” generate a meeting point alphabet of “L”.
Alt-image & caption: Vigenère Cipher Encryption
The second input of “I” and the key of “B” generate a meeting point alphabet of “J”.
Alt-image & caption: Vigenère Cipher Encryption
And soon until the last input of the “LINUXHINT” plaintext and “ABCDABCDA” key generate the “LJPXXIKQT” cipher.
Alt-image & caption: Vigenère Cipher Encryption
Vigenère Cipher Decryption
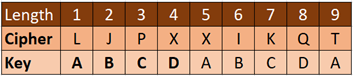
The Vigenère cipher decryption process is the reverse of the encryption process. While the Vigenère cipher encryption focuses on the meeting point (output), the decryption focuses on the corresponding input of the meeting point from the key.
For example, the given Vigenère “LJPXXIKQT” cipher and the “ABCD” key.
Alt-image & caption: Vigenère Cipher Decryption
The first cipher letter of “L” has a key of “A”. Look for the key row of “A” and find where the “L” letter is in that row. Now, look at the corresponding input header which results in “L”.
Alt-image & caption: Vigenère Cipher Decryption
The second cipher letter of “J” has a key of “B”. Look for the key row of “B” and find where the “J” letter is in that row. Now, look at the corresponding input header which results in “I”.
Alt-image & caption: Vigenère Cipher Decryption
Soon, the last decryption process results in plaintext as shown in the following:
Alt-image & caption: Vigenère Cipher Decryption
Conclusion
In conclusion, we learned a comprehensive exploration of the Vigenère cipher, its historical significance, and the intricate encryption mechanisms. We learned about the Tabula Recta and its role in facilitating the encryption and decryption processes. Furthermore, we gained insights into the complexities of the Vigenère cipher, particularly its polyalphabetic substitution nature and key generation process. While the Vigenère cipher is surpassed by modern encryption techniques, it remains a pivotal chapter in the history of cryptography which showcases the persistent human pursuit of secure communication and the continuous evolution of cryptographic methods.
Frequently Asked Questions (FAQs)
Q1: What makes the Vigenère cipher different from the Caesar cipher?
A1: Caesar cipher uses a fixed shift value, while the Vigenère cipher utilizes a sequence of shifts based on a keyword, making it more resistant to frequency analysis.
Q2: Can the Vigenère cipher handle numerical or special characters?
A2: The Vigenère cipher primarily operates on letters of the alphabet. Hence, the numerical and special characters are typically left unchanged during encryption and decryption.
Q3: Is the Vigenère cipher secure for modern encryption purposes?
A3: While the Vigenère cipher was once considered secure, it is vulnerable to modern cryptanalysis techniques and is no longer suitable for securing sensitive information.
Q4: Are there any modern applications or adaptations of the Vigenère cipher?
A4: While the Vigenère cipher is not commonly used for secure communications in modern technology, it has inspired various cryptographic algorithms and serves as an essential historical reference in the development of modern encryption methods.