By default, Let’s Encrypt uses the HTTP-01 challenge to verify the ownership. The HTTP-01 challenge puts a file on the Webroot of your web server and uses the DNS name of the webserver to fetch the file. If the file can be fetched from the internet, the authority of the domain name is verified and the SSL certificate is issued. That’s good for most servers and home users who can afford a public IP address from their internet service provider (ISP).
But, what if you want to use the Let’s Encrypt SSL certificates for the domain names of your home network or private/internal network? Well, in most home networks, getting a Let’s Encrypt SSL certificate is a challenge because most likely, your ISP won’t give you a public IP address. So, you won’t be able to pass the Let’s Encrypt HTTP-01 challenge (as your computers/servers are not accessible from the internet).
In this case, you can use the Let’s Encrypt DNS-01 challenge to get the SSL certificates for your home/internal network. In this method, Let’s Encrypt adds a DNS TXT record for the “subdomain _acme-challenge.yourdomain.xyz” on your DNS server and checks if the DNS TXT record is available from the internet. If the TXT record matches, you’re verified as the owner of the domain and Let’s Encrypt issues the SSL certificate.
For the Let’s Encrypt DNS-01 challenge to work and automatically renew the SSL certificate, you must use a DNS service provider (i.e. CloudFlare, DigitalOcean) that exposes an API that can be used to add/remove the TXT records on the DNS server.
If your DNS registrar (where you registered the domain name) does not have support for such services, you can use a third-party DNS service provider. All you need to do is change the DNS nameserver address of your domain from your DNS registrar’s DNS server to the DNS nameserver address of your desired third-party DNS service provider.
Topic of Contents:
- List of DNS Providers that Integrate Easily with Let’s Encrypt DNS Validation
- List of Let’s Encrypt ACME Clients
- Changing the DNS Nameserver from Your Domain Registrar
- Advantages of Let’s Encrypt DNS-01 Validation
- Disadvantages of Let’s Encrypt DNS-01 Validation
- Conclusion
- References
List of DNS Providers that Integrate Easily with Let’s Encrypt DNS Validation
The Let’s Encrypt community compiled a list of DNS providers that expose some sort of API to automatically add/remove the DNS records so that the Let’s Encrypt clients can validate the domain names and issue the SSL certificates.
The list of DNS providers that integrate easily with Let’s Encrypt DNS validation can be found at this link.
List of Let’s Encrypt ACME Clients
Let’s Encrypt clients are also called ACME clients. ACME stands for Automatic Certificate Management Environment. ACME is a protocol for automating the interaction between the computer/server and the certificate authority (i.e. Let’s Encrypt).
The most popular Let’s Encrypt ACME clients are:
Changing the DNS Nameserver from Your Domain Registrar
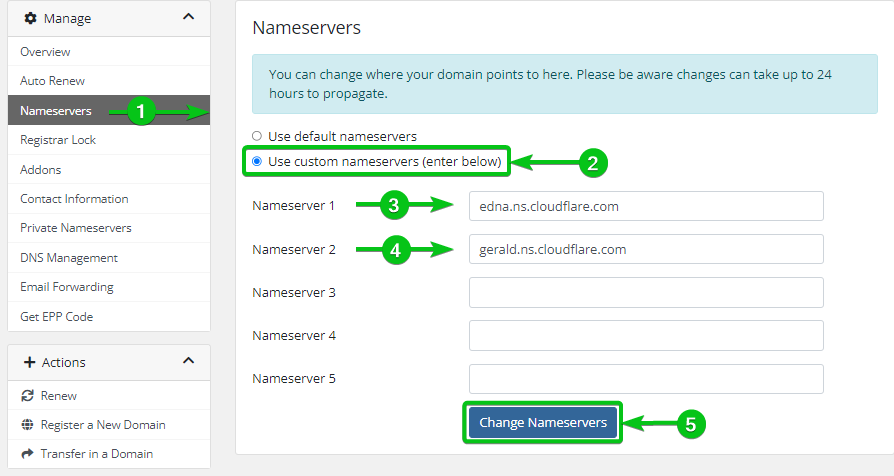
If your domain registrar is not on the list of DNS providers that integrates easily with Let’s Encrypt, you can use CloudFlare or other third-party DNS service providers. All you have to do is change the DNS nameserver of your domain from the dashboard of your domain registrar to the DNS nameserver of the third-party DNS service provider that you want to use.
We showed you the process of changing the DNS nameserver (to CloudFlare’s DNS server) for one of our domains from the dashboard/website of our domain registrar (where we registered our domain name) in the following screenshot. The process should be similar for your domain registrar. For more information, read the documentation of your domain registrar or contact them.
Advantages of Let’s Encrypt DNS-01 Validation
The advantages of Let’s Encrypt’s DNS-01 validation are:
- It does not require a public/internet-accessible IP address or a web server.
- You can use it to issue the SSL certificates for wildcard domain names (i.e. *.nodekite.com, *.linuxhint.com).
- It works well for multiple web servers.
Disadvantages of Let’s Encrypt DNS-01 Validation
Although there are many advantages of Let’s Encrypt DNS-01 validation, there are also some disadvantages:
- For DNS-01 validation to work, you need to keep the API key/token of your DNS service provider on the server which a Let’s Encrypt client will use to create a TXT record on the DNS server for DNS-01 validation. As the API key/token is kept on the server, if the server is hacked, there’s a chance that the API key/token will be compromised.
- After the Let’s Encrypt client adds a TXT record on the DNS server, it takes a while to propagate the changes to other DNS nameservers worldwide. The Let’s Encrypt client need to wait for the changes to propagate to the common DNS nameservers worldwide to verify the ownership of the domain. If your DNS service provider does not provide the DNS propagation time in the API, the Let’s Encrypt client will not know how long to wait for the DNS changes to propagate to other nameservers worldwide. In that case, the DNS validation may time out, and Let’s Encrypt might fail to issue an SSL certificate.
Conclusion
In this article, we discussed the Let’s Encrypt DNS-01 challenge and why use it over the default HTTP-01 challenge to verify the ownership of a domain name. We also discussed the requirements for passing the Let’s Encrypt DNS-01 challenge to get a Let’s Encrypt SSL certificate. We listed the DNS service providers that integrate well with Let’s Encrypt as well as the Let’s Encrypt ACME clients that you can use to perform the DNS validation from your computer/server. Finally, we discussed the advantages and disadvantages of the Let’s Encrypt DNS validation.
References:
- Challenge Types – Let’s Encrypt
- DNS providers who easily integrate with Let’s Encrypt DNS validation – Issuance Tech – Let’s Encrypt Community Support
- Automatic Certificate Management Environment – Wikipedia
- Certbot
- GitHub – acmesh-official/acme.sh: A pure Unix shell script implementing ACME client protocol
- Installation :: Let’s Encrypt client and ACME library written in Go.
- Home – Posh-ACME