Burp Suite
Burp Suite is a rich-featured web application attack tool designed by Portswigger. It is equipped with everything needed to perform a successful pentest against a web application. Burp is the world’s most widely used web application tester & scanner, with over 40,000 active users, due to its easy to use interface and depth. It’s already an awesome web application pentesting with capabilities that can even further increased by adding extensions or add-ons called BApps.
Burp’s major features are as follows:
- The ability to intercept HTTP requests that normally go from browser to the server, and then the server returns the response. This is done by its core feature called “Intercepting Proxy”. Here the request is interrupted midway and goes from the user’s browser to Burp, and then the server.
- The ability to map the target, i.e., web application using the “Spider” tool. This is done to get the list of endpoints and crawl through them in order to find some vulnerabilities in them.
- An advanced scanning web application tool for automating tasks of detecting vulnerabilities in the target (available only in PRO version).
- An “Intruder” tool is used for automated attacks like brute-forcing a web application’s login page, dictionary attacks, fuzzing the web application to find vulnerabilities, etc.
- A “Repeater” tool used for manipulating the user-supplied values or requests, and observing their behavior in order to find potentially vulnerable vectors.
- A “Sequencer” tool for testing session tokens.
- A “Decoder” tool for decoding and encoding numerous encoding schemes like base64, HEX, etc.
- The ability to save the work and resume later (available only in PRO version).
Installation
Burp Suite can be downloaded from the official PortSwigger website:
https://portswigger.net/burp/communitydownload.
Burp is available to download for almost every operating system including Windows, Linux, and MacOS. By clicking on the Download Latest Version option, you will be redirected to a download page with different editions and operating systems, i.e., Community Edition or Professional Edition. Professional edition is paid with prices written on its official website. Download the Community edition, and you are ready to use its basic awesome features.
Usage
In order to use Burp, it needs to be configured to intercept HTTP requests. To configure browsers, i.e., Chrome, Firefox, etc., we have to follow the steps given below:
For configuring Chrome to work with Burp
In order to configure Chrome to work with a Burp, first, click on the Customize option on the top right corner of the window, then go to the Settings option. In the settings window, choose Advanced Settings, and then click on Change Proxy Settings from the given options.
For configuring Firefox to work with Burp
In order to configure Firefox to work with a Burp, go to the Firefox menu on the top right corner of the window, click on the Preferences option, then go to the Options button. Here, look for Network Proxy in the General tab. Click the Manual Proxy Config. Enter the listener address, i.e., 127.0.0.1, and Burp port, i.e., 8080. Delete everything in the “No Proxy for” field, and you are good to go.
Brute Force attack using Burp
Authentication is the process of making sure that the right person is accessing the service or the right person is logging in, using different techniques like access tokens, passwords, keys, etc. The use of passwords is highly common in everyday life. Here comes the importance of basic authentication, i.e., the choosing of a strong complex password, because the login area protected with weak authentication can be accessed easily using automated attacks like brute-forcing, dictionary attacks.
Dictionary Attack is a brute force attack on a login field with the help of a dictionary. In this attack, hundreds of thousands of possible combinations of guessed passwords stored in a dictionary are tried on the login field, with the intention that one of them may work. These passwords are tried successively on the login field in order to bypass the authentication.
Let’s consider a scenario where we have to brute force a login page using a dictionary or a word list containing hundreds of thousands or millions of commonly leaked passwords.
Open Burp Suite and start intercepting the traffic by turning Intercept On. Switch to the browser and enter any username or password in the given fields, then click Login. Now switch to Burp, you will see the traffic has been intercepted midway going to the server and goes to Burp instead. Right-click and choose, Send to Intruder from the given options.
Now, switch to Intruder tab, and we will see multiple tabs, i.e., Positions, Payloads, Options. We have to configure all the options in these tabs correctly to let the Burp do its work and get our desired outcome.
Positions
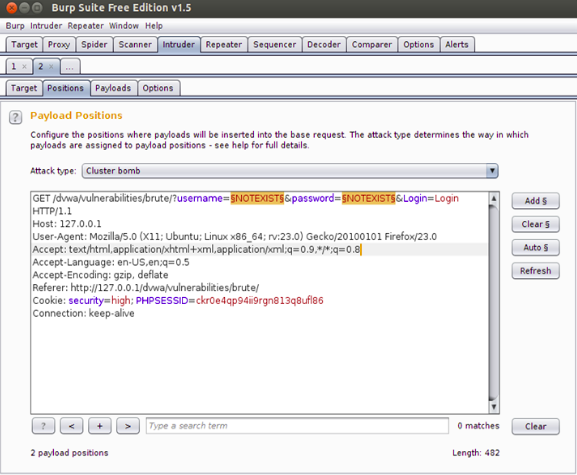
Let’s look at the Positions tab first. Here, we tell the burp the parameters we want to attack in the request, i.e., password field, username field, etc.
By default, Burp highlights some fields in order to recommend to the user what fields they can attack. But in our case, we just need to change the value of the username and password fields, so that they are changed with the next word in the dictionary, through which we are attacking in every request. For this, we need to first clear all the highlighted areas by clicking on the Clear button on the right side of the window. This will clear up Burp’s recommended highlighted areas. Now, highlight the username and password fields, which are “NOTEXIST” in our case, and then click Add. We also need to specify the Attack type, which is Sniper, by default and change it to Cluster Bomb.
Payloads
Now, we have to set our payload through which we are going to attack these selected fields. Their values will be changed with each request according to the payload. Let’s set up a payload for parameter 1, i.e., Username field. Let’s add a small word list of usernames we have in a file. Click on Payload 1, and choose Payload type as Simple List. In Payload Option, click Load and go to your desired word list file, then select it. The selected word list values will be shown as given below.
Now, in setting up a payload for parameter 2, i.e., the Password field, let’s add a commonly used word list of leaked passwords, i.e., “rockyou.txt” since in our case, we have this in a file. Click on Payload 2 and choose Payload type as Simple List. In Payload Option, click Load and go to your desired word list file, then select it. The selected word list values will be shown as given below.
Options
After setting up the attack parameters and payload list, it’s time to set up a very important option called “Options”. In the Options tab, some rules that are set to tell us which request is successful; in our case, it will tell which password did work. We have to configure a thing here, which is the string or message that will be displayed on getting the right password, i.e., Welcome, Welcome to our portal, Good to be back, etc. It depends on the web application developer. We can check it by entering any right credentials in the login area.
We have “Welcome to password protected area admin” here. Now, switch to Burp in the Options tab, find Grep Match, and write the following string here. Check the Simple String option, and we are good to go.
Everything is set up nicely. Now, all we have to do is to start the attack. Go to the Intruder tab, and then click Start Attack. An intruder will now try all combinations possible from the provided payloads.
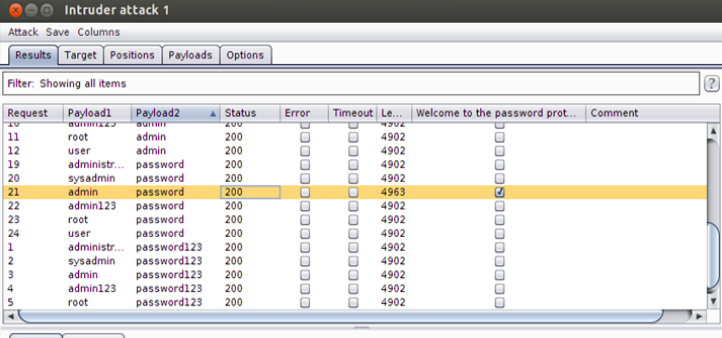
We can see Intruder trying all combinations like the image given above. We can see if the request is successful or not by looking at the length of the requests. The successful request would be of a different length than the non-successful one. Another way of knowing whether the request is successful or not is by looking at the “Welcome to password protected area” (i.e., the string we have provided to the Options tab earlier) tab. If the small box is ticked, it means the request is successful and vice versa. In our case, the successful request has length 4963, while it is 4902 in the case of an unsuccessful one.
Brute force attack using Burp, with the help of a powerful dictionary, is a very effective and underrated method of bypassing login pages, which are not made for malicious entities. In case of a weak password, a used, easy, or small password, this is a very effective technique.
Fuzzing
Fuzzing is an approach that is used for automating the process of discovering bugs, weaknesses, or vulnerabilities by sending a ton of requests to an application with various payloads, with the expectation that the web application might trigger an activity. It isn’t explicit to Web Applications, but can also be used in other numerous attacks like buffer, overflow, etc. A vast majority of common web vulnerabilities can be found through fuzzing like XSS cross-site scripting, SQL Injection, LFI, RFI, etc. Burp is -really powerful and it is also the best tool available – in getting the job done smoothly.
Fuzzing with Burp
Let’s take a web application vulnerable to SQL Injection and fuzz it with burp to find potentially vulnerable fields.
Fire up Burp and start intercepting the login request. We will see a bunch of data, right-click and click on the Send to Intruder options from the given menu. Go to the Positions tab and configure the right parameters. By default, Burp highlights some fields in order to recommend to the user what fields the user can attack. But in our case, we just need to change the value of username and password fields. First, clear all the highlighted areas by clicking on the Clear button on the right side of the window. This will clear Burp recommended highlighted areas. Now, just highlight the username and password fields, and then click Add. We also need to specify the Attack type and change it to Sniper.
Now, go to the Payloads tab and, here, we have to set our payload through which we are going to attack these selected fields. Their values will be changed with each request according to the payload. Let’s set up a payload for parameter 1 and parameter 2, i.e., Username and Password fields, respectively. Burp also has a wide range of its payloads for different types of vulnerabilities. We can use them or create or load one of our own in Burp’s easy to use interface. In this case, we are going to load Burp’s payload that will trigger an alert in case of finding a SQL vulnerability.
Select Simple List in Payload type option. Now, click on the Load option from the “Payload Options” window. Here, select Fuzzing-SQL injection payload from available options. Payload sets are used to figure out the list you are about to use for a specified parameter. In the event where you pick two attack vectors (parameters), there you can set an alternate word list for everyone. Likewise, you can set the payload type like case alteration, numbers, dates, and so on. For this situation, the basic list is vital since we are using Burp’s default payload.
Now, go to the Options tab, and you can see some very interesting options. For example, the “Grep” option that can be selected to match the response to the given keywords like “SQL”. Another cool option is the “Time out” option that comes in very handy in case of potential web application firewalls. In our case, we checked the “Follow redirection” option since we have a redirect parameter in the request. However, once in a while, the error can trigger additionally before the redirection, both then can be tested separately.
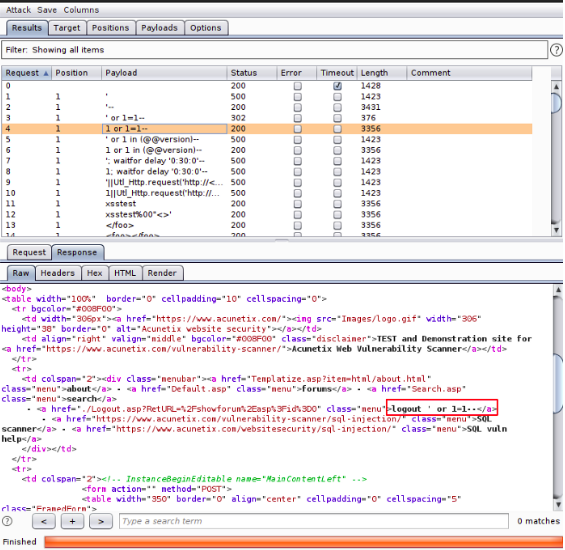
Now, everything is set up nicely, and the Burp intruder is ready to start the attack. Click on the Start attack option on the left corner and just wait for the attack, which would literally take hours manually to be completed, in just a minute or two. Once the attack is completed, all we have to do is to analyze the given results closely. We should look for a different or odd value in the length column. One should look for any anomalies in the status code too, as it also tells which request caused an error and vice versa.
On getting an odd status code or length value, one has to check the response window. In our case, we can see that the 4th request has a different status code and a higher length value than usual, and upon looking at the response area, we can see that Burp can bypass the login area using a value from the payload. The attack can be considered as successful.
This is a very effective technique in bug bounty and pen testing procedures as it investigates every parameter present in the site and attempts to comprehend what it does, if it is connected with Database or being reflected in the response page, among others. This technique, however, causes a lot of noise at the server’s side and can even lead to Denial of Service, which is frustrating to attackers as well as for web application users and developers.
Burp Extensions
With the help of Burp Extender, numerous useful Burp extensions can be added to enhance the capabilities of Burp. One can write its third-party code or load extensions. For loading and installing extensions to Burp, BApp Store is the place to go. There are various uses for Burp extensions, such as modifying HTTP requests and response, customizing the user interface, adding scanner and runtime checks, etc.
BApp Store
The BApp Store consists of Burp extensions that have been composed by clients of Burp Suite to enhance Burp’s abilities and features. You can see the rundown of accessible BApps introduced explicit BApps, and submitted client ratings for those you have introduced.
Burp extensions can also be downloaded from the BApp store’s website and can be added to Burp later on. Different BApps or BApp extensions are written in different languages like Python or Ruby and expect the user to download Jython or JRuby for them to work properly. Then configure Burp with the directory of the important language interpreters. In some cases, a BApp may require a later form of Burp or an alternate version of Burp. Let’s look at some of Burp’s enormous amount of useful extensions:
Autorize:
Autorize is a very effective extension when there is a need of detecting authorization vulnerabilities in a web application automatically. Detecting authorization vulnerabilities is a very time-consuming task for any bug bounty hunter or pentester. In the manual method, you need to remove cookies every time from each request to check whether authorization has been implemented or not. Autorize does this job automatically just by taking cookies of a low privileged user of a web application, then letting the more privileged user navigate it. Autorize does this by repeating each request with a low privileged user session and starts detecting authorization vulnerabilities or flaws.
It is likewise conceivable to repeat each request with no provided cookies, to recognize authentication flaws as well as authorization vulnerabilities. This extension works without any prior configuration, but at the same time is profoundly adaptable, permitting arrangement of the granularity of the approval authorization conditions and requesting the extension a must test and whatnot.
On completing the procedure, there will be Red, Green, and Yellow colors on the screen, showing “Bypassed”, “Enforced”, and “ Is Enforced ?? ” statuses respectively.
Turbo Intruder
Turbo Intruder is a modified version of Burp Intruder and is used when there is a need for extreme complexity and speed for handling HTTP requests. Turbo Intruder is Fast as it uses an HTTP stack handed code from the base, prioritizing and keeping speed in mind. This makes it extremely fast, and sometimes, even a better option than well written GO scripts. Its scalable nature is another highlight, which is due to its ability to achieve flat memory usage. Turbo Intruder can also run in a command-line environment. An advanced diffing algorithm is built in this awesome extension, which automatically filters out boring and useless output.
One of the main attacks in which Turbo Intruder can be used is Race Condition Attacks. When a system that has been designed to perform tasks in a specific sequence is forced to perform more than one task at a time, it is called a race condition. In that kind of scenario, Turbo Intruder is used, as it can perform multiple tasks with enormous speed. This type of attack can be used in the existence of race condition vulnerability and can cause attacks like redeeming multiple gift cards, abusing of like/unlike features, etc.
For sending the HTTP request to Turbo intruder, intercept the request and then right-click on the window, then select the Send to Turbo Intruder option from the given list of options. Turbo Intruder is a bit harder to use than Burp’s default Intruder.
Conclusion:
Burp is an extremely powerful & rich-featured tool whose one of its awesome functions and features is to automate the attacks and find vulnerabilities, which makes life way easier for a pentester or a bug bounty hunter. Tasks that can take days manually can be done in the least bit of time using Burp, and it also provides an easy graphical user interface to launch Brute force attacks with or without a dictionary, just by making one’s word list right at the moment. On the other hand, the BApp store provides extremely powerful extensions that even further enhances the capabilities of Burp Suite.