Notably, troubleshooting Linux SAML problems begins with identifying the source of the problems. Common issues include login failure, configuration issues, connection problems, authentication issues, and authorization problems.
This article looks into some of the main SAML problems. Besides highlighting the errors, the article will also specify the cause of the issues as well as how to troubleshoot them.”
Common SAML Errors
SAML Configuration Errors
Troubleshooting SAML configuration errors begins with understanding your configuration modules. And among the things you should know include;
- Your IdP and SP- If you are using Auth0, find out if it serves as your Service Provider (SP) or the Identity Provider (IdP). Of course, it can also be your IdP and SP simultaneously. An SP is a program or application that a user intends to access. It directs each user for authentication. On the other hand, an IdP confirms the credentials and sends a validation or denial report to the SP.
- Type of Authentication Mode– The two types of authentication flow modes used in SAML are IdP-initiated or SP-initiated modes. Your system could use either of the two or both of them. Notably, users will always attempt to navigate to the SP before being directed to the IdP, which approves login. This type of flow is an SP-initiated flow. In the IdP-initiated authentication flow, users will navigate to the IdP and log in before being redirected to the SP program or application.
- Type of User Profile Attribute at the IdP– The user profile attribute that the IdP uses when identifying the user and the attribute between applications is another vital consideration. Ensure that you configure the correct mappings. Notably, you can choose to use an email address or internal ID in enterprise organizations.
- Type of Authentication Assertions– It is vital to check if your authentication assertions have encryptions.
- Other Considerations– Other aspects you would want to look out for when troubleshooting SAML issues include the number of users affected, the number of applications inaccessible, is the issue is resulting from a new setup or an old one just stopped, and how far the problem occurs during the login process.
Among the common errors that you may encounter when AuthO is a service provider (SP) include;
Connection Disabled
When you do not have an association with any active connection, you will find the below message;
You should visit your AuthO dashboard and enable at least one application in case you experience this problem. Notably, you can achieve this by clicking Authentication🡺 Enterprise🡺Connection Name🡺Applications. You will find a list from which you can choose. If you do not find a list, create an application and proceed.
Attributes InResponseTo Do Not Match AuthNRequest ID
This error is pretty common in situations where the InResponseTo attribute does not match the AuthNRequest ID. Ideally, it happens when your AuthO tenant does not recognize the SAML response. The primary reasons could include blocked cookies, inconsistent domain use, and mismatched IDs.
In case your tenant has a custom domain, the chances are that you have a mismatch when the login indicates that your system begins on the custom domain but finishes on the comical domain. For example, if the below is your beginning custom domain;
But your identity provider has a configuration that returns the below SAML response to your ACS URL at comical domains;
A return of your ID to another domain in your InRespinseTo attribute of SAML responses implies that your tenant has no record of the ID. Using the same domain throughout your authentication solves this issue.
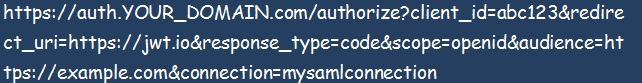
When IdP-Initiated Login is Not Enabled
When you configure your ACS URL in the identity provider or IdP used in the default tenant domain, and you start the authentication process by calling the custom domain using /authorize, this problem will most likely occur;
This error occurs when your transaction has no RelayState parameter or in case of a missing InResponseTo attribute in your SAML response. You can always check again and correct the anomaly.
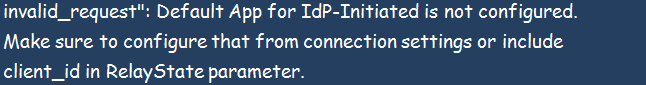
When IdP-Initiated Default Application Is Not Configured
In this case, your IdP-initiated flows are properly enabled but lack vital configuration information. You will see the below image;
Ideally, your ACS URL should have the same domain name used during the initial request. It can also use a custom domain callback in case you are using custom domains. The error could as well occur if your authentication flow lacks a RelayState parameter or an InResponseTo attribute.
SAML Configuration Errors
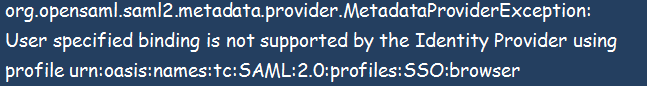
HTTP Status 500 Error
Occasionally, the below error could welcome you during configuration;
You can solve the above error by reviewing your settings. Among the areas of concern could include correcting the IdP URL for the single sign-on specified in your SAML tab, confirming the configured IdP for HTTP-POST, and correcting the IdP URL for the single sign-on profile specified during the creation of the SP.
Failed Login
A failed login will produce the message below;
The error happens when there is a mismatch in user names. Try to match the names to fix this problem.
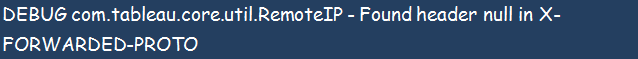
Failed Login Due to an Offloading SSL
Lookout for the below message;
It can also come alongside the below message from the portal logs;
The above combination implies that your system has a misconfiguration of the external proxy that offloads to the server.
Conclusion
The above are the notable problems you will encounter when dealing with SAML configuration and authentication. The article highlights the possible solutions for each problem. We hope this helps.