This article addresses some of the issues you may find. Some of the issues that we include here are:
- Issues arising from system setup
- Issues arising from client utilities and failure to use or manage the Kerberos environment
- KDC encryption issues
- Keytab problems
Troubleshooting Linux Kerberos System Setup and Monitoring Problems
Notably, the problems you may face with Linux Kerberos often begin from the setup stage. And the only way you can minimize setup and monitoring issues is by following these steps:
Step 1: Ensure you have a functional Kerberos protocol correctly installed in both machines.
Step 2: Synchronize the time on both machines to ensure that they run on a similar time frame. Notably, use the network time synchronization (NTS) to ensure that the machines are within 5 minutes of each other.
Step 3: Check if all hosts in the domain network service (DNS) have the correct entries. While at that, ensure that each entry in the host file has relevant IP addresses, host names, and fully-qualified domain names (FQDN). A good entry should look like this:
Troubleshooting Linux Kerberos Client Utility Issues
If you are finding it difficult to manage client utilities, you can always use the following three methods to solve the issues:
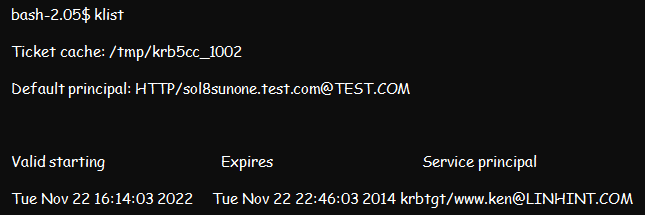
Method 1: Using the Klist Command
The Klist command will help you visualize all tickets in any credentials cache or the keys in the key tab file. Once you have the tickets, you can forward the details to complete the authentication process. A Klist output for troubleshooting client utilities will look like this:
Method 2: Using Kinit Command to Check for Issues on KDC Client
You can also use the Kinit command to confirm if you have any issues with your KDC host and KDC client. The Kinit utility will help you obtain and cache a ticket-granting ticket for the service principal and the user. Client utility problems could always result from a wrong principal name or a wrong user name.
Below is the Kinit syntax for the user principal:
The above command will prompt for a password as it creates a user principal. When running the command, ensure that you replace the username with a valid entry from your directory.
On the other hand, the Kinit syntax for service principal is similar to the details in the below screenshot. Note that this can vary from one host to another:
Interestingly, the Kinit command for the service principal will not prompt any passwords since it uses the bracketed key tab file to authenticate the service principal.
Method 3: Using kinit Command to Check SMP Problems
You can also run the below command irrespective of whether the above kit command worked or not. It helps to determine if there are any issues with the SMP host. Notably, this is more useable when testing your sever on mail.company.com.
Your kinit command will take the below structure:
Method 4: Using the ktpass Command
Sometimes the problem could be a problem with your passwords. To ascertain that this is not the cause of your Linux Kerberos issues, you can verify your ktpass utility version.
Troubleshooting KDC Support Issues
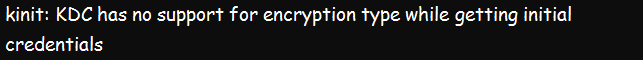
Kerberos can often fail due to an array of issues. But sometimes, the issues could result from KDC encryption support. Notably, such a problem will bring the message below:
Do the following in case you receive the above message:
- Verify if your KDC settings block or restrict any encryption types
- Confirm if your server account has all the encryption types checked.
Troubleshooting Keytab Issues
You can take the following steps if you encounter any key tab issues:
Step 1: Verify that both the location and name of the key tab file for the host are similar to the details in krb5.conf file.
Step 2: Verify if the host and client servers have principal names.
Step 3: Confirm the encryption type before creating a key tab file.
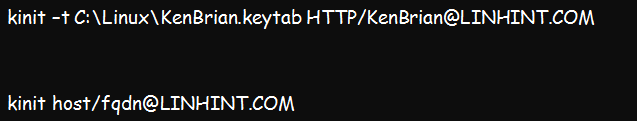
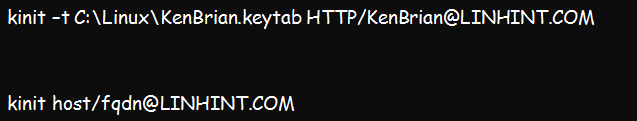
Step 4: Verify the validity of the key tab file by running the below kinit command;
The above command should return no error if you have a valid key tab file. But in case of an error, you can verify the validity of the SPN using this command:
The above utility will prompt you to key in your password. Failure to ask for a password implies that your SPN is invalid or unidentifiable. Once you key in a valid password, the command will not return any error.
The above are some common problems you might encounter when configuring or authenticating with Linux Kerberos. This write-up also contains the possible solutions for each of the issues you might face.