This tutorial shows how to use Netcat to scan ports on remote targets. Examples included in this tutorial explain individual port scan, scanning several ports, scanning port ranges, and banner grabbing using Netcat.
After Netcat examples, I added examples of the same scan types using Nmap and Nmap Scripting Engine for banner grabbing.
Installing Netcat:
To install Netcat on Debian or Debian based Linux distributions such as Ubuntu run:
On Red Hat-based Linux distributions (CentOS, Fedora) you can run:
How to scan a single port using Netcat:
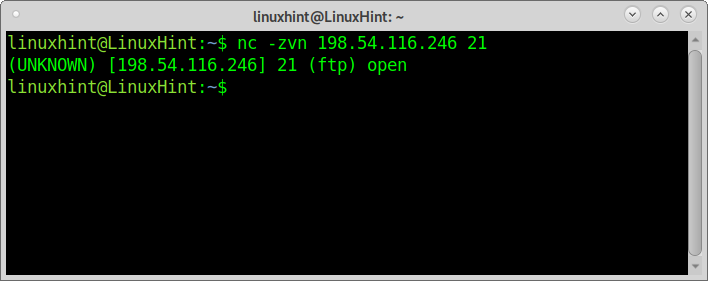
The first example shows how to scan a single port using Netcat. The scanned port is the FTP (21).
The arguments passed are:
z: instructs Netcat to scan without establishing a connection.
v: Verbosity to see the result.
n: Skip DNS lookup
NOTE: Replace <target> for your actual target.
As you can see, Netcat reports the FTP is open.
Scanning multiple ports using Netcat:
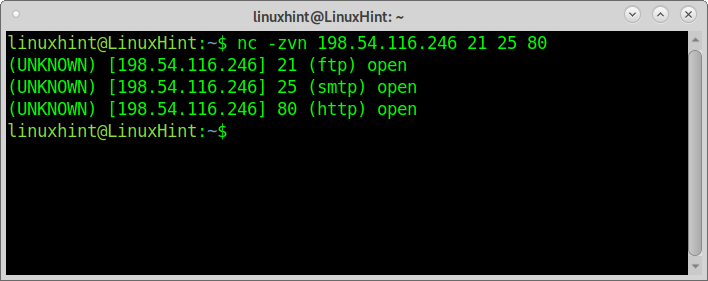
The second example shows how to scan multiple ports, in this case, ports 21, 25, and 80. After defining your target, just list the ports you can to be checked:
As you can see, all ports were reported as open.
How to scan a port range using Netcat:
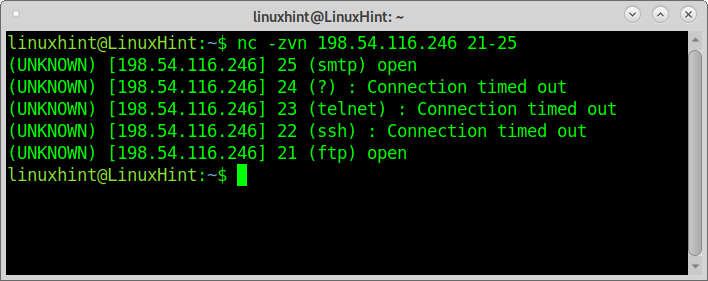
With Netcat, you can also scan port ranges by implementing a hyphen between the first and last port to scan, as shown in the example below:
As you can see, ports 25 and 21 are open while the rest are closed.
Banner grabbing using Netcat:
Banner grabbing is a method to collect information from targets from the banners some application displays when we connect to them. This technique can reveal information on the software running on the target. Banner grabbing can target ports 21, 25, and 80.
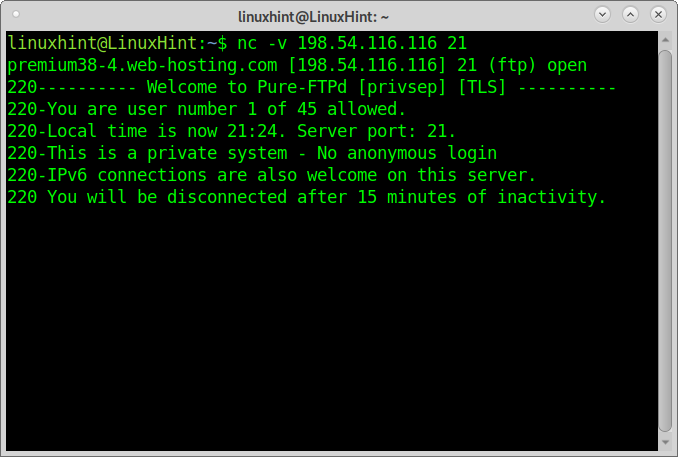
The following example shows how to use Netcat for banner grabbing to learn the FTP version running on the target:
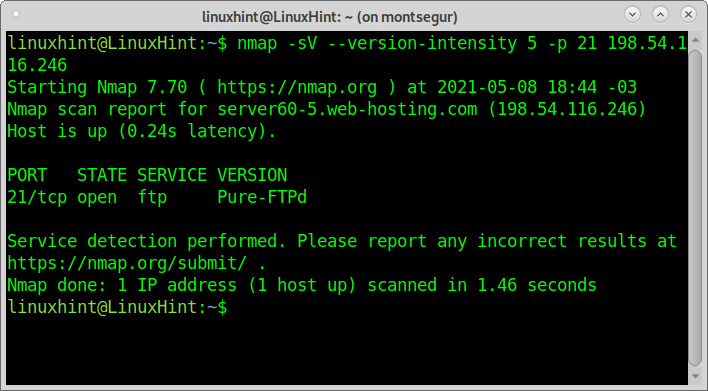
Netcat reports the server runs Pure-FTPd.
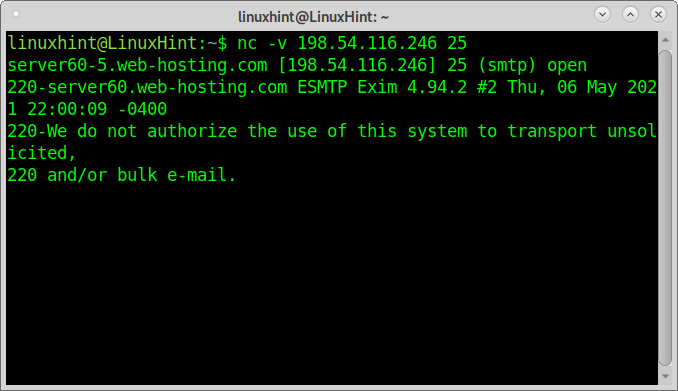
The following example shows banner grabbing using netcat to get information on the SMTP:
The output shows the server uses Exim 4.94.2.
How to scan a single port using Nmap:
This tutorial won’t list the obvious advantages of Nmap over Netcat to scan ports, but it explains how to do the scan processes described above with Nmap.
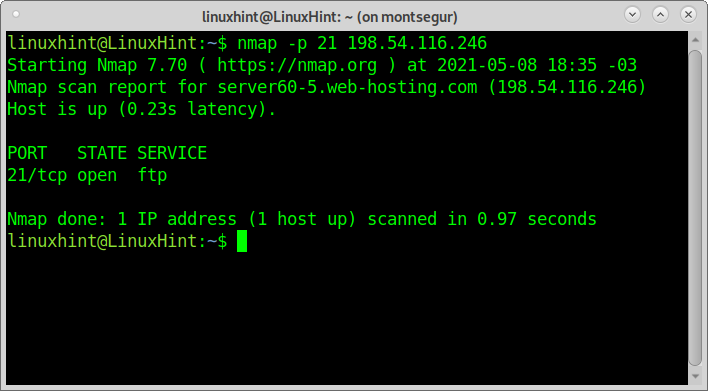
To scan a single port with nmap, specify it with the argument -p as shown in the example below using the same target and port I used with Netcat.
Scanning multiple ports using Nmap:
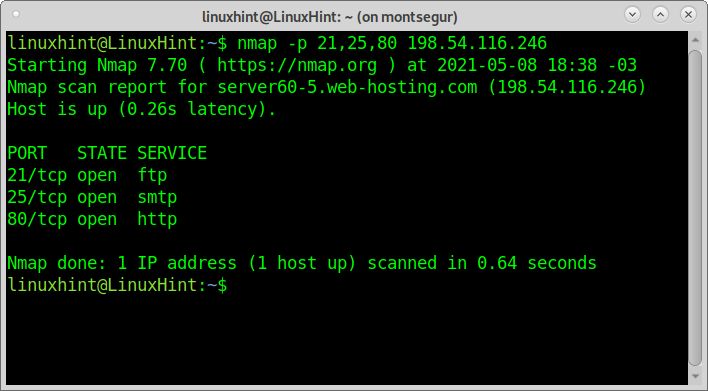
To scan multiple ports with Nmap, you can use the same syntax, just separate each port by a comma. The following example shows a scan for ports 21, 25, and 80 similarly to the second Netcat example:
How to scan a port range using Nmap:
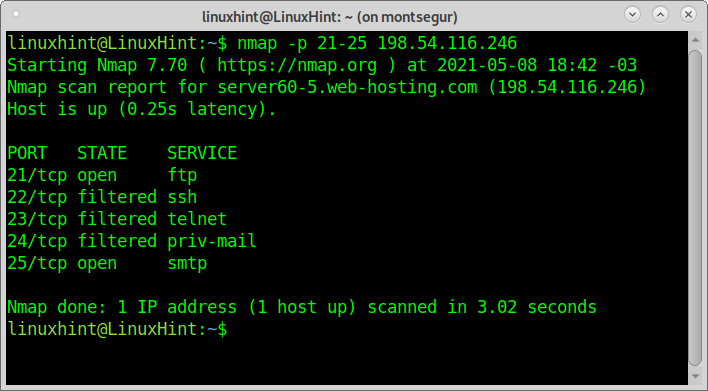
To scan port range, you can use a hyphen like with Netcat:
Banner grabbing using Nmap:
Finally, for banner grabbing with Nmap, I will apply the flags -sV instructing Nmap to check for service versions. I also instruct Nmap to run the –script=banner from NSE (Nmap Scripting Engine); like with the Netcat example, the process aims to discover the FTP version.
As you can see, the output is the same as with Netcat. If you are interested in this technique, you can read more on banner grabbing here.
Conclusion on Netcat for port scan:
Netcat is a real relic; it is a great network tool but very limited for port scanning. There is no reason to replace Nmap or any other port scanner for Netcat to scan ports.
Netcat doesn’t support multiple target scans; despite it can be integrated into a script to achieve this goal, the tool itself has very few options for port scanning.
Even if not Nmap, alternatives like Zmap, Angry IP Scanner, Masscan, all of them explained at Nmap Alternatives, have a wide list of advantages over Netcat, including more versatility, option to scan multiple targets or even the whole internet, option to use the wildcard, packet fragmentation or the possibility to edit packet headers, to add custom scripts and a lot more. Nmap also returns results faster than Netcat and keeps adding features like new scripts for Nmap Scripting Engine. Despite this conclusion, Netcat is still a great networking tool with additional features, which will be deeply explained in future articles at LinuxHint.