Since this article is focused on whitelisting and disabling the ModSecurity rules, we are not referring to the installation and configuration part. You will get the installation instructions by simply googling with the “install and configure ModSecurity” keyword.
Testing the ModSecurity Configuration
Testing is an important part of configuring any setup. In order to test the ModSecurity installation, you need to add the following rule to the ModSecurity and test it by accessing the mentioned URL. Add the following rule in “/etc/modsecurity/rules/000-default.conf” or in the respective location where the other rules are present.
SecRule ARGS:args "@contains test" "id:123456,deny,status:403,msg:'Test Ruleset'"
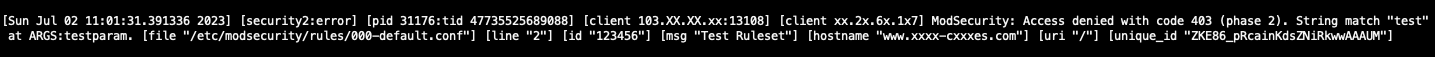
Restart the Apache service and test the same using the following link. Either use the server IP or any other domain in the server with the last parameters kept the same. If the ModSecurity installation is a success, the rule will trigger and you will get a 403 forbidden error like in the following screenshot. Also, you can check the logs with the “Test Ruleset” string to get the log related to the blocking.
http://www.xxxx-cxxxes.com/?args=test
Browser error
Log entry for the rule.
Disabling or Whitelisting ModSecurity
Disabling the ModSecurity rules for a specific domain is of paramount importance for web hosting users as it enables the fine-tuning of security measures to align with the unique requirements of that domain. White-listing specific entities such as domains, URLs, or IP addresses allows the web hosting users to exempt certain components from ModSecurity’s rule enforcement. This customization ensures the optimal functionality while maintaining an appropriate level of protection. It is particularly useful when dealing with trusted sources, internal systems, or specialized functionalities that could trigger the false positives.
For example, a payment gateway integration may require a communication with a third-party service which can be white-listed to ensure the uninterrupted transactions without triggering unnecessary security alerts.
Real-life examples abound where disabling the ModSecurity rules for a domain becomes necessary. Consider the e-commerce platforms that rely on complex interactions such as adding multiple items to a shopping cart simultaneously. Such legitimate behavior could inadvertently trigger the ModSecurity rules which results in false positives and hindering the user experience.
Additionally, the content management systems often require the file upload capabilities which can clash with certain ModSecurity rules. By selectively disabling the rules for these domains, the web hosting users can ensure the seamless operations without compromising the overall security.
On the other hand, disabling specific ModSecurity rules provides flexibility to address the compatibility issues or prevent the false positives. Sometimes, certain rules might incorrectly identify the harmless behaviors as potential threats which results in unnecessary blocking or interference with legitimate requests. For instance, a web application that utilizes AJAX might encounter the false positives due to ModSecurity’s strict rules which require the selective rule disabling to ensure a smooth and uninterrupted client-server communication.
However, it is crucial to strike a balance and regularly review the rule behavior to prevent potential vulnerabilities. With careful management, disabling the ModSecurity rules for specific domains empowers the web hosting users to optimize the website functionality and provide a secure browsing experience for their visitors.
For example, to whitelist ModSecurity for a specific domain, the users can configure the rules that exempt that domain from being scanned by ModSecurity. This ensures that legitimate requests from that domain are not unnecessarily blocked or flagged as suspicious.
Disable ModSecurity for a specific domain/virtual host. Add the following inside the <VirtualHost> section:
SecRuleEngine Off
</IfModule>
Whitelisting ModSecurity for a specific directory or URL is important for web hosting users. It allows them to exclude that particular location from being checked by the ModSecurity rules. By defining the custom rules, the users can ensure that legitimate requests that are made to that directory or URL are not blocked or flagged as suspicious. This helps maintain the functionality of specific parts of their websites or API endpoints while still benefiting from the overall security that is provided by ModSecurity.
Use the following entry to disable ModSecurity for specific URL/directory:
<IfModule security2_module>
SecRuleEngine Off
</IfModule>
</Directory>
Disabling a specific ModSecurity rule ID is a common practice for web hosting users when they encounter false positives or compatibility issues. By identifying the rule ID that causes the problem, the users can disable it in the ModSecurity configuration file. For instance, if the rule ID 123456 is triggering the false positives, the users can comment out or disable that specific rule in the configuration. This ensures that the rule is not enforced which prevents it from interfering with legitimate requests. However, it’s important to carefully assess the impact of disabling a rule, as it may leave the website vulnerable to actual security threats. Prudent consideration and testing are recommended before making any changes.
To disable a specific ModSecurity rule id for a URL, you can use the following code:
<IfModule security2_module>
SecRuleRemoveById 123456
</IfModule>
</LocationMatch>
The combination of the three mentioned entries can be utilized to disable the rules for a specific URL or virtual host. The users have the flexibility to disable the rules partially or completely, depending on their specific requirements. This allows for granular control over rule enforcement which ensures that certain rules are not applied to specific URLs or virtual hosts.
In cPanel, there is a free plugin available (“ConfigServer ModSecurity Control”) to whitelist the ModSecurity rules as well as to disable the ModSecurity for the domain/user/entire server, etc.
Conclusion
In conclusion, the web hosting users have the ability to fine-tune the ModSecurity by disabling the rules for specific domains, URLs, or virtual hosts. This flexibility ensures that legitimate traffic is not blocked unnecessarily. Additionally, the users can whitelist specific rule IDs for certain domains or URLs to prevent false positives and maintain an optimal functionality. However, it is crucial to exercise caution when disabling the rules, considering the potential security risks. Regularly review and assess the rule behavior to strike the right balance between website security and functionality. By leveraging these capabilities, the web hosting users can customize ModSecurity to suit their specific needs and enhance their website’s security posture effectively.