This is a beginner’s tutorial on using the WMAP plugin incorporated in the Metasploit framework to scan for vulnerabilities in web applications. We will use the web application DVWA as a target to demonstrate the scanning process done using WAMP. DVWA is short for “damn vulnerable web application,” and the app is specially designed to used by cybersecurity novices to test and sharpen their penetration skills.
Setting up the Metasploit framework in Kali Linux
We will start by launching the Metasploit framework. First, start up the PostgreSQL server by typing:
Next, initialize the database with msfdb init:
Then start the PostgreSQL service with service postgresql start
Then type msfconsole to start the Metasploit database
The database is now loaded. You can make sure that the database has loaded properly, type in:
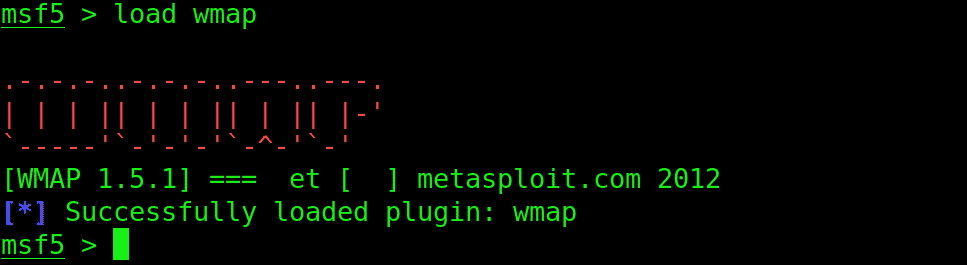
Load WMAP
Next up, launch WMAP using the following command:
The command shell will display the following window:
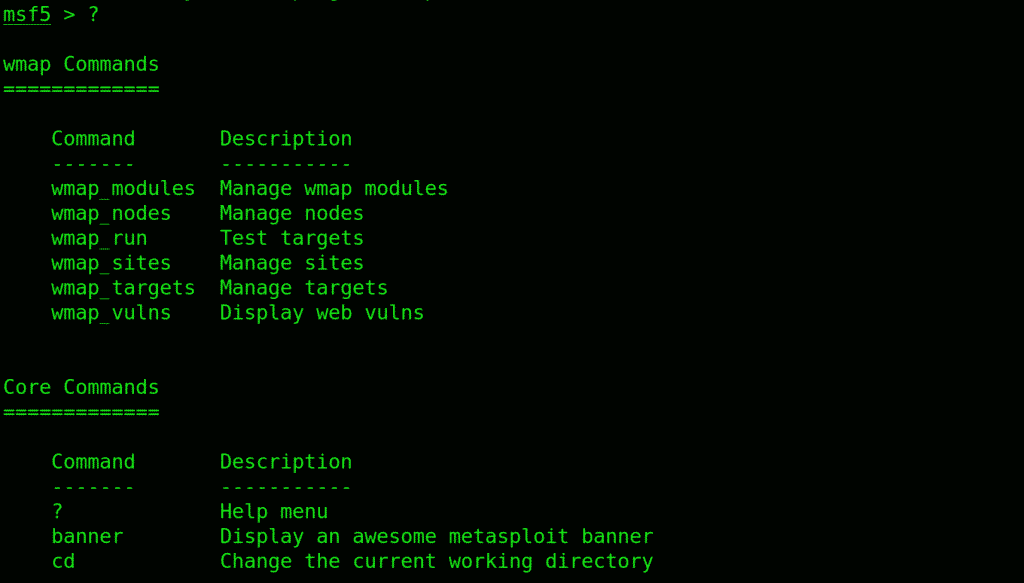
Type “?” and Metasploit will show the help menu, that’ll probably look something like:
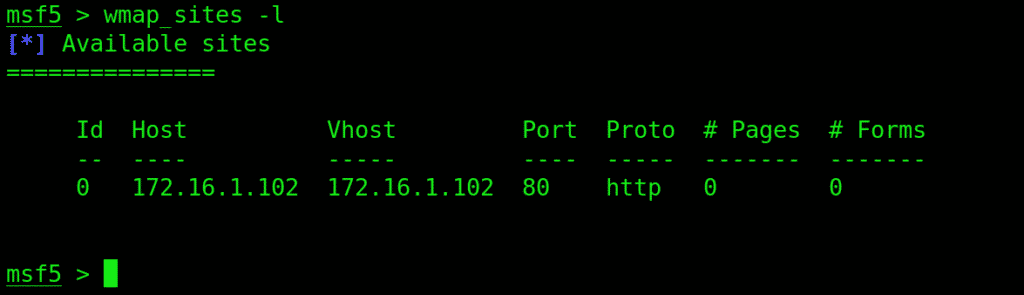
Input target site to initiate the scanning
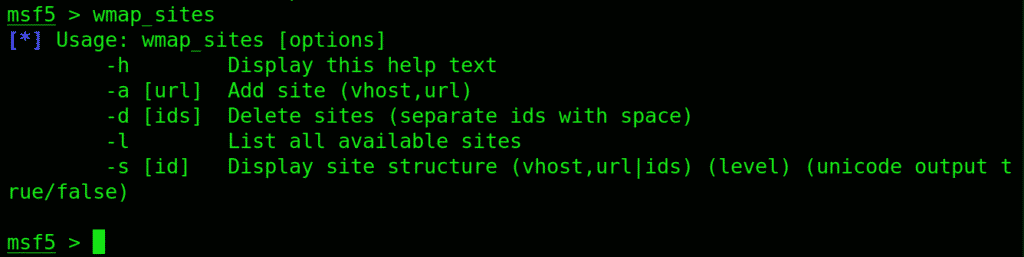
Use the wmap_sites to manage sites you wish to scan.
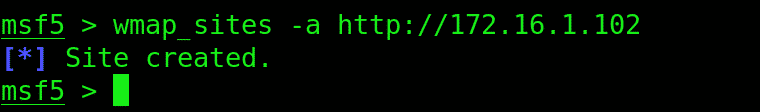
This is what you input to add a site:
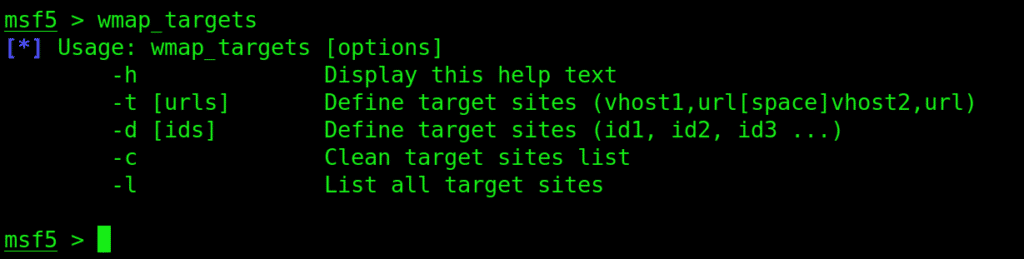
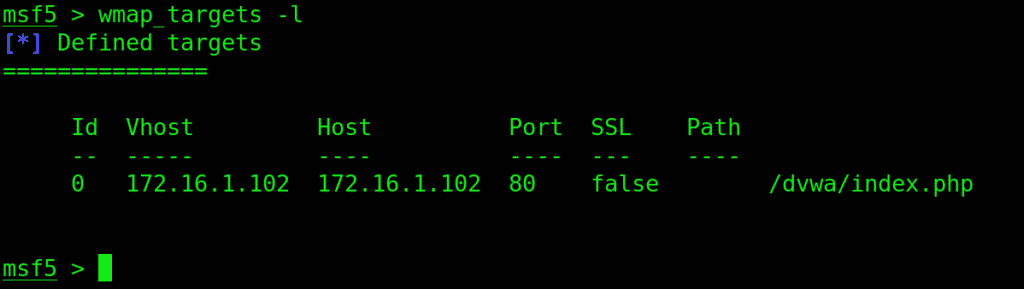
Now we need to point Metasploit to the victim site by providing the URL
Type in wmap_targets –t to point to the site:
Loading up the mods
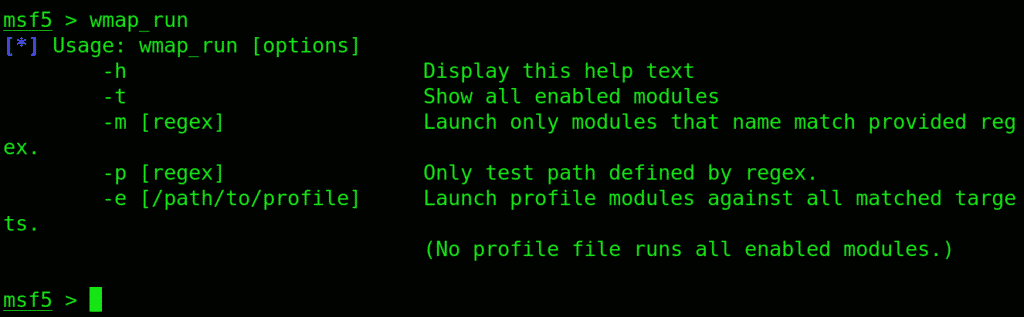
Before we run the scanner, type wmap_run. You will be displayed the options for this command.
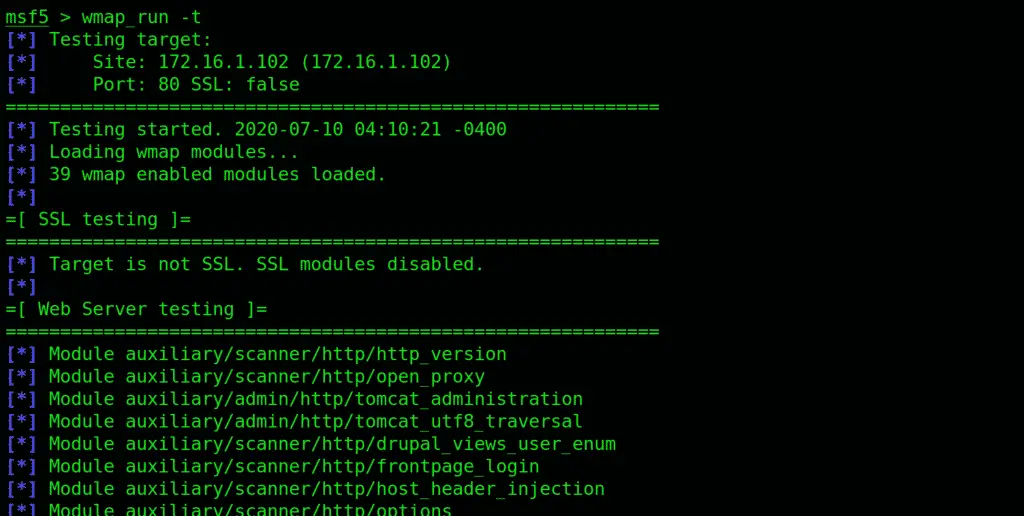
Put in wmap-run followed by a –t flag.
As you can see, this has listed all the enabled modules, of which there are all sorts of. There’s are a bunch that is disabled as well. You can see that the SSL module is among the disabled, which is because the victim site is not using it.
If you want detailed info, type info, followed by the information on the mod.
Running the Scanner
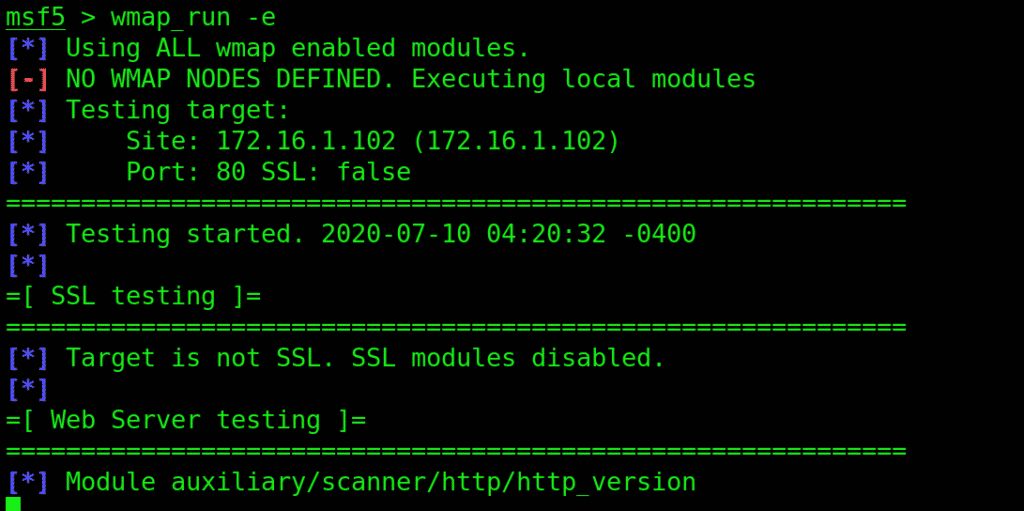
To begin the scanning, type in wmap_run succeeded by –e flag. The scanning normally takes quite some time to finish.
Use the wmap_vulns -l command to see the results of the scan.
Conclusion
This beginner’s walkthrough has been about using Metasploit’s WAMP module for scanning web applications and checking it for vulnerabilities. We’ve set up how to launch the Metasploit database, how to launch the WAMP addon, and to direct it to a web app to initiate scanning. With pen testing, you can check for possible breach hotspots in a web app to eliminate them, thus strengthening its security.