[adthrive-in-post-video-player video-id=”zGzEIocs” upload-date=”2020-09-18T11:30:26.000Z” name=”Metasploit Framework – Working with Metasploit Payloads” description=”Metasploit Framework – Working with Metasploit Payloads” player-type=”collapse” override-embed=”true”]
H.D.Moore, a network security expert, crafted Metasploit in Perl in 2003. He designed it to be an automated exploitation tool that eliminates the constant requirement of manual verification. The first version was released with a limited number of exploits. Later on, it was adapted to Ruby, which allowed many cybersecurity experts to further develop on the project. By 2006, the framework consisted of over 200 exploits.
In this article, we will first introduce the Metasploit framework, cover its various interfaces and components, and perform a surface-level task with the Metasploit Framework, which will entail searching for email addresses in search engines.
A Brief Introduction to Metasploit Components
Some of the interfaces of the Metasploit Framework that you can interact with include the following:
- msfconsole – an interactive shell that allows for navigation and manipulation
- msfcli – summons the terminal/cmd
- msfgui – stands for Metasploit Framework Graphical User Interface
- Armitage – a Java-based GUI tool that facilitates Metasploit tasks
- Metasploit Community Web Interface – this interface was developed by eapid7 to optimize the framework for pen-testing
Furthermore, there are several modules that expand the functionality of Metasploit.
Modules
Modules are snippets of codes that the Metasploit framework uses to accomplish exploitation and scanning tasks. The Metasploit framework contains the following modules:
Exploit: modules that initiate exploitation by giving the attacker access to the target system. Once inside the compromised system, exploits begin exploitation by uploading the payload module.
Payload: Once injected by the framework, a payload module allows the attacker to navigate the system and transfer data to and from the system. The degree of freedom when it comes to such actions depends upon the payload’s architecture and how well-suited it is to the OS of the breached system.
Auxiliary: Auxiliary modules let you perform arbitrary, one-off actions, such as port scanning, fuzzing, recon, dos attacks, etc
Nops: A payload can crash upon landing on an invalid memory location. A Nop module prevents this from happening by looping the machine instructions from the beginning if the payload happens to reach an invalid location.
Post: Post exploitation begins upon successfully entering a compromised system. Post modules include functionalities that help in post-exploitation, such as easing navigation through the system. Post modules also allow you to attack other systems in the networks.
Encoders: The core purpose of encoders is to avoid detection from the system. These modules deny the system to perform a certain task that might jeopardize the exploit and the attack, such as inspection by antivirus or restrictions from a firewall.
Listeners: These modules scout for connections from the payload module into the compromised system. This helps to enhance connectivity and to determine emergent coordination between the Metasploit components.
Exploitation with Metasploit
Now that we have introduced the Metasploit framework and its various components, we will begin with exploitation.
Extracting Publically Available Email Addresses from a Search Engine
We will start by collecting some email ids from a search engine
First, launch Metasploit through the msfconsole interface, having enabled the PostgreSQL service.
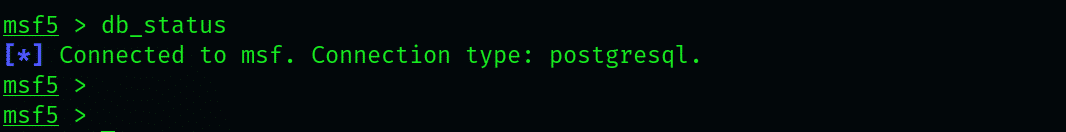
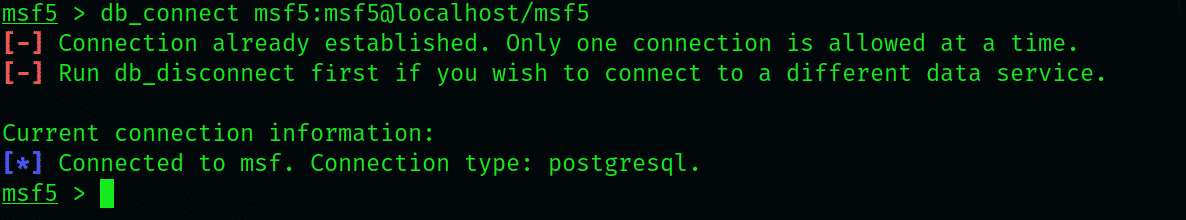
With that all set, you must connect the database to the msfconsole. Check whether the connection is already established by typing the below command:
Hopefully, the connection has been established, and Metasploit is working just fine. If that is not the case, retry and check the database status again by entering the following command:
If the connection has not established successfully, you may still continue. Although you will be missing some advanced features, the features at hand are enough to get the job done
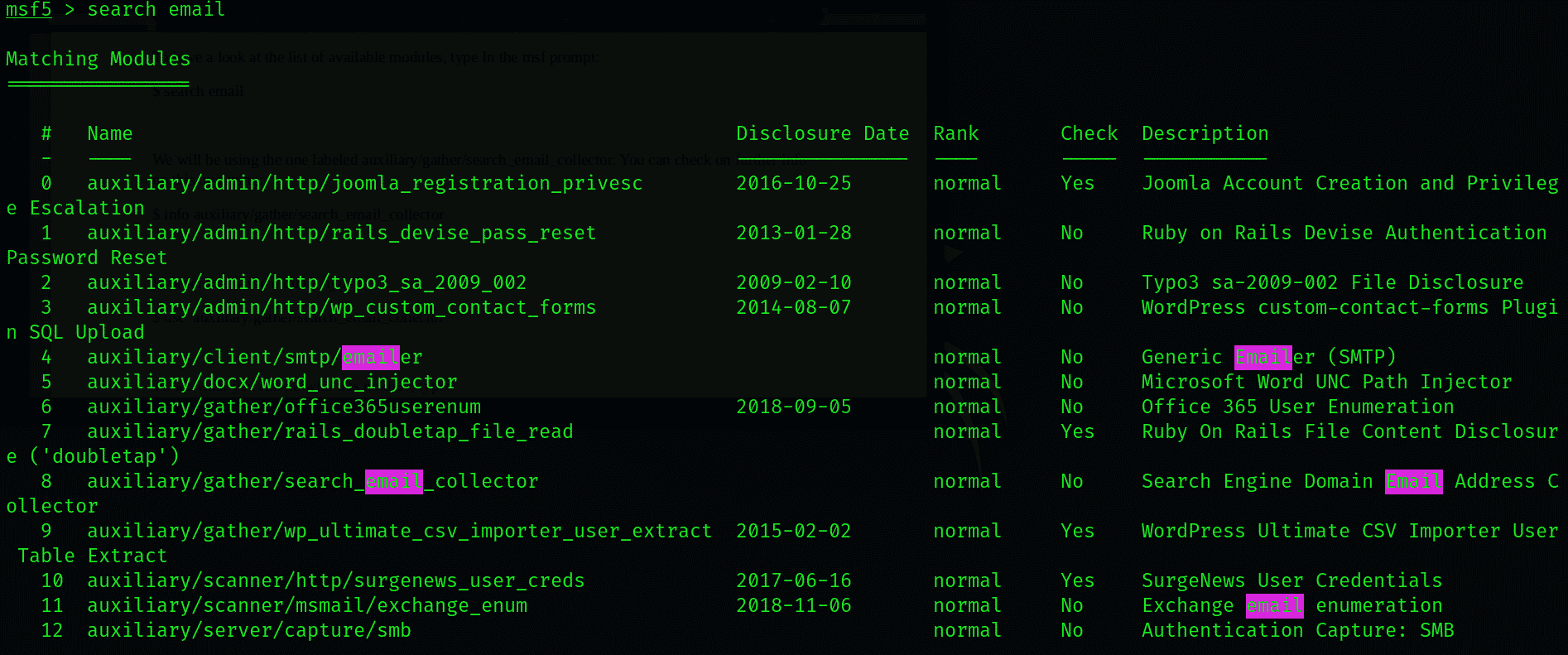
To have a look at the list of available modules, type in the msf prompt:
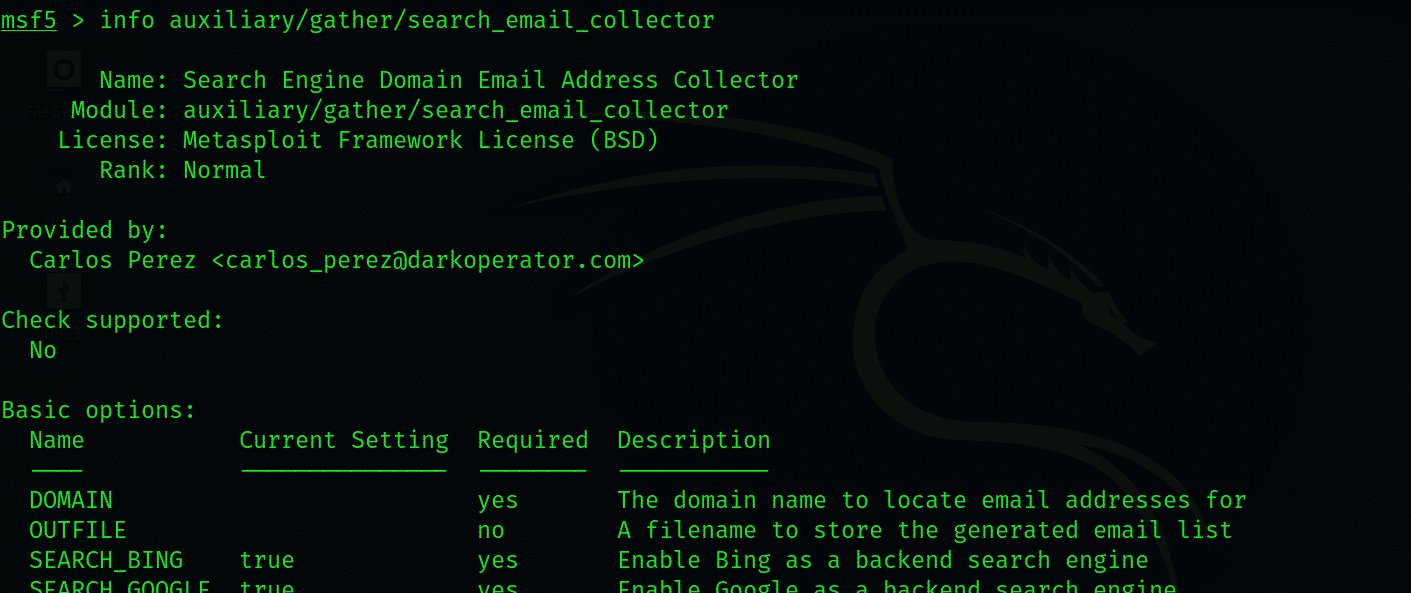
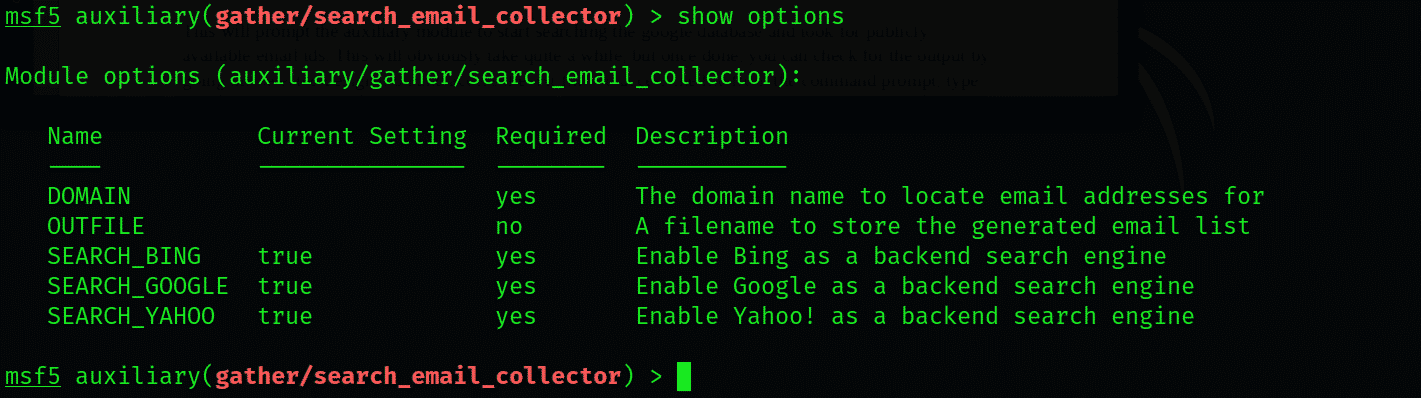
We will be using the module labeled auxiliary/gather/search_email_collector. You can check for further information on this module by typing the following command:
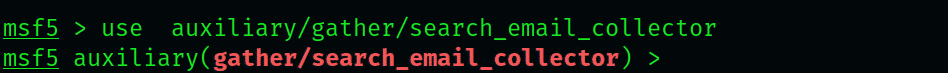
To use the module, type the following command:
To see what you can do with this module, enter the following:
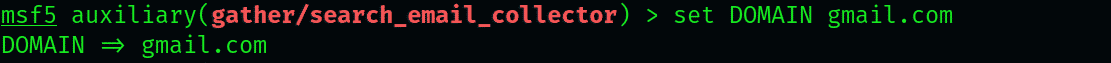
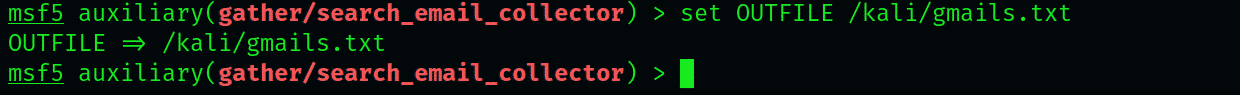
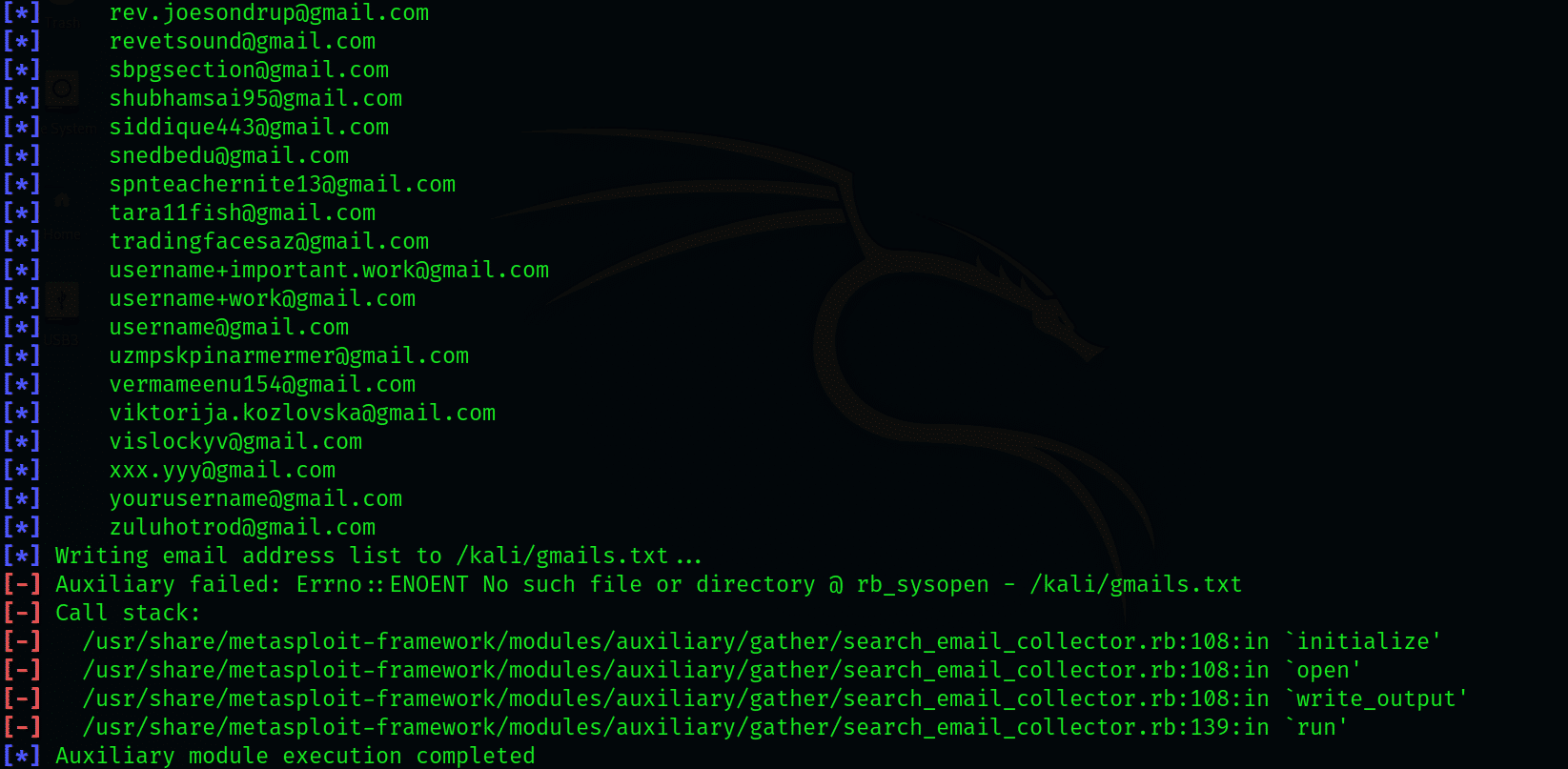
To start with the extraction, first set the domain to GMAIL id and instruct the module to save files in a .txt file.
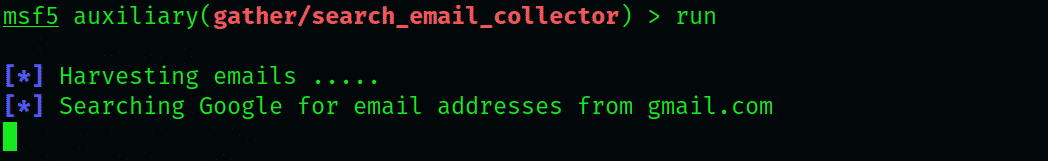
Then, type the following command:
This will prompt the auxiliary module to start searching the Google database and look for the publicly available email ids. This will take quite a while, but once it is done, you can check for the output by going to the selected designation and accessing the .txt file. To access the file from the command prompt, enter the following:
Conclusion
This short-walkthrough for beginners is about getting you familiarized with Metasploit payloads. The article showed you how to use the msfconsole interface to look for email ids in search engines. I chose this activity in particular, as it is intuitive and is fairly easy to grasp quickly. I have also explained in limited detail the additional functionalities Metasploit possesses, and its potential in pen-testing work.
I hope that you found this short guide useful and that this tutorial has sparked your interest in looking more into this intricate and versatile tool for pen-testing.