For a detailed explanation on how the Let’s Encrypt DNS-01 challenge (or DNS validation) works, read the article entitled What Is Let’s Encrypt DNS-01 Challenge and How to Use It to Get the SSL Certificates.
In this article, we will show you how to use the Let’s Encrypt DNS validation to get an SSL certificate for your domain name using the Certbot and Certbot CloudFlare DNS plugin.
Topic of Contents:
- Managing Your Domain with CloudFlare DNS
- Installing Certbot and Certbot CloudFlare Plugin on Ubuntu/Debian
- Installing Certbot and Certbot CloudFlare Plugin on Fedora
- Installing Certbot and Certbot CloudFlare Plugin on RHEL/AlmaLinux/Rocky Linux/CentOS Stream
- Checking If Certbot and Certbot CloudFlare Plugin Are Installed Correctly
- Generating a CloudFlare API Token
- Securely Storing the CloudFlare API Token on the Computer/Server
- Generating an SSL Certificate Using the Certbot CloudFlare DNS Validation
- Listing the Let’s Encrypt SSL Certificates Using Certbot
- Renewing the Let’s Encrypt SSL Certificates Using Certbot
- Conclusion
- References
Managing Your Domain with CloudFlare DNS
To get a Let’s Encrypt SSL Certificate using the CloudFlare DNS validation, you must have a CloudFlare account and your domain must use the CloudFlare DNS. You can create a CloudFlare account for free and the CloudFlare DNS service is free to use as well.
To manage your domain with CloudFlare DNS, you can do one of the following:
- Register your domain from CloudFlare
- Transfer your domain to CloudFlare
- Change the DNS nameserver of your domain name to the CloudFlare DNS nameserver from the dashboard of your domain registrar
You don’t have to buy a domain from CloudFlare or transfer a domain to CloudFlare to manage it with the CloudFlare DNS service. You can just change the nameserver of your domain to the CloudFlare DNS nameserver from the dashboard of your domain registrar (where you bought the domain from) and manage your domain from CloudFlare. For more information on changing the nameserver of your domain to the CloudFlare DNS nameserver, read this article.
Installing Certbot and Certbot CloudFlare Plugin on Ubuntu/Debian
Certbot and Certbot CloudFlare plugin are available in the official package repository of Ubuntu/Debian. So, you can install them on Ubuntu/Debian very easily.
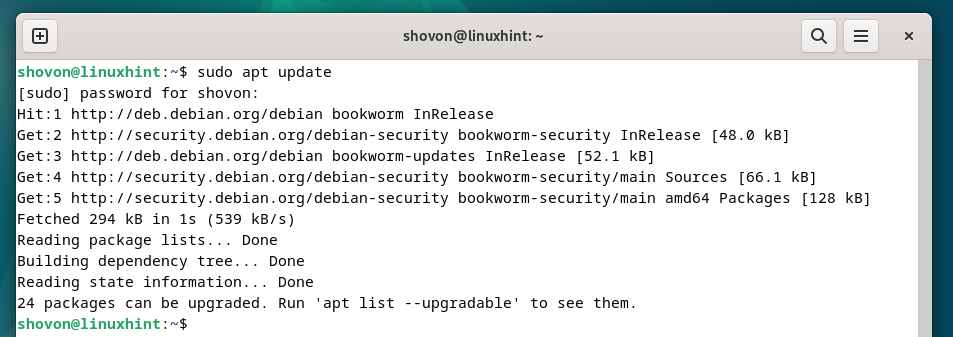
First, update the APT package repository cache with the following command:
To install Certbot and Certbot CloudFlare DNS plugin, run the following command:
To confirm the installation, press “Y” and then press <Enter>.
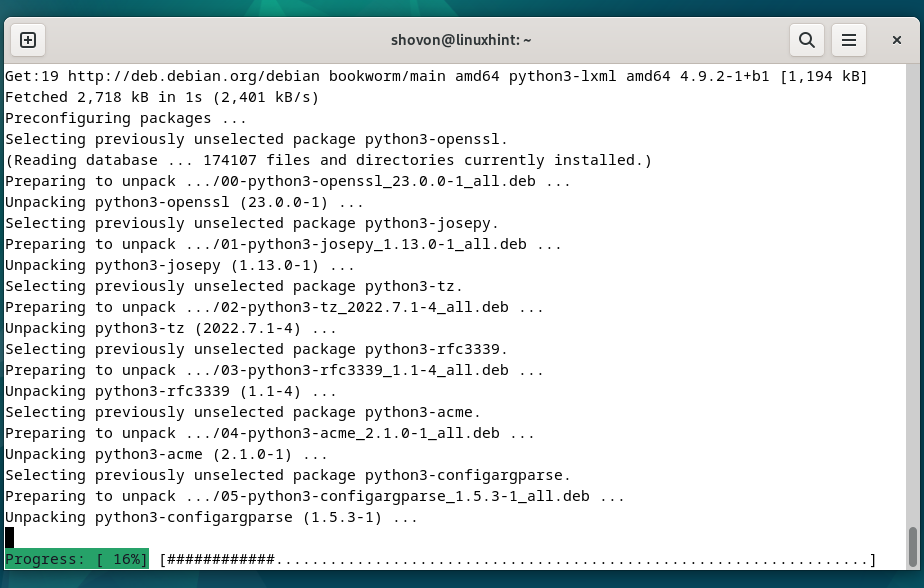
Certbot and Certbot CloudFlare DNS plugin are being installed. It takes a while to complete.
At this point, Certbot and Certbot CloudFlare DNS plugin should be installed.
Installing Certbot and Certbot CloudFlare Plugin on Fedora
Certbot and Certbot CloudFlare plugin are available in the official package repository of Fedora and can be installed on Fedora very easily.
First, update the DNF package database with the following command:
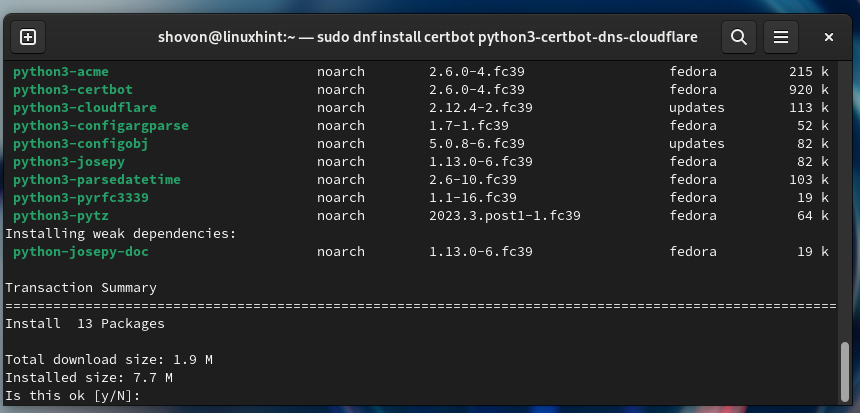
To install Certbot and Certbot CloudFlare DNS plugin on Fedora, run the following command:
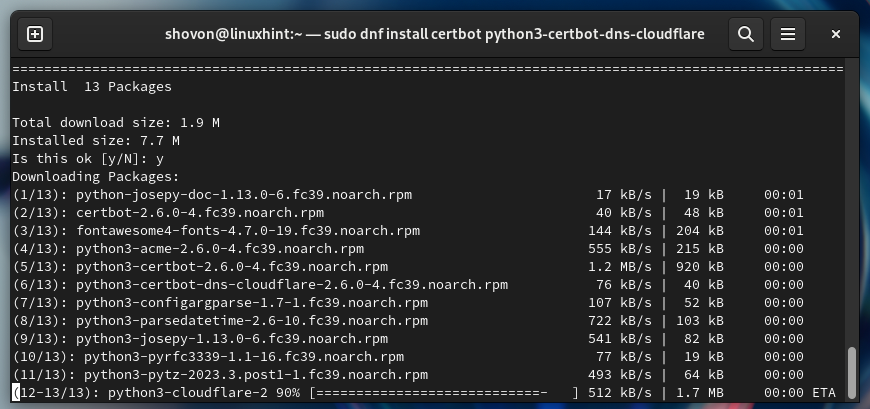
To confirm the installation, press “Y” and then press <Enter>.
Certbot and Certbot CloudFlare DNS plugin are being installed. It takes a while to complete.
At this point, Certbot and Certbot CloudFlare DNS plugin should be installed on Fedora.
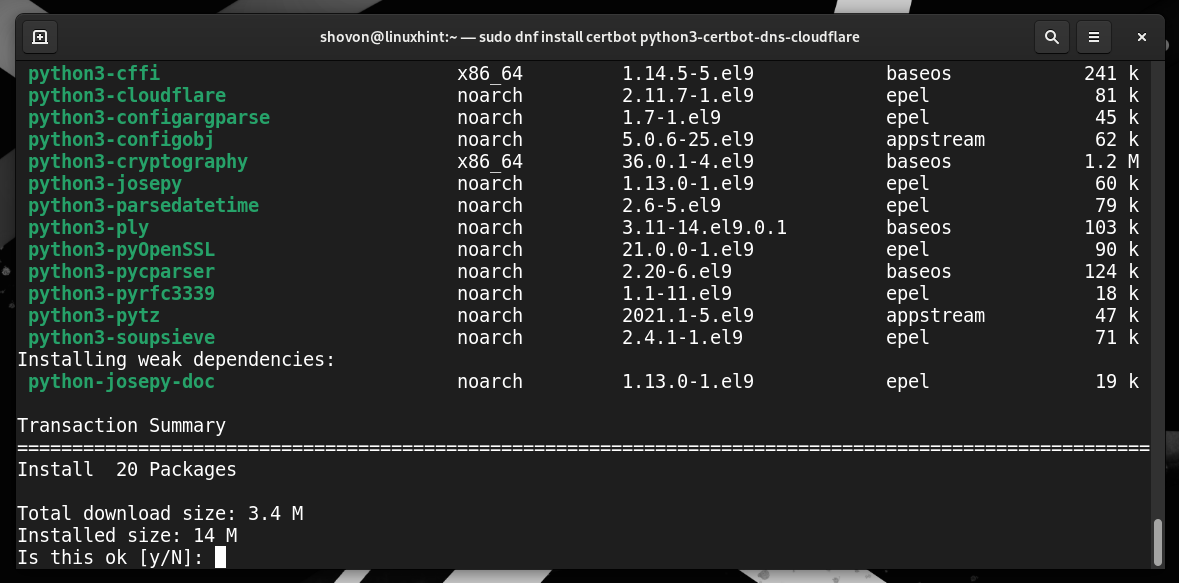
Installing Certbot and Certbot CloudFlare Plugin on RHEL/AlmaLinux/Rocky Linux/CentOS Stream
The Certbot CloudFlare DNS plugin is not available in the official package repositories of RHEL/AlmaLinux/Rocky Linux/CentOS Stream. The Certbot CloudFlare DNS plugin is available in the EPEL package repository. You can enable the EPEL package repository on RHEL/AlmaLinux/Rocky Linux/CentOS Stream and install the Certbot CloudFlare DNS plugin from there.
Once you enabled the EPEL package repository, update the DNF database cache with the following command:
Then, install Certbot and Certbot CloudFlare DNS plugin on your RHEL/AlmaLinux/Rocky Linux/CentOS Stream system with the following command:
To confirm the installation, press “Y” and then press <Enter>.
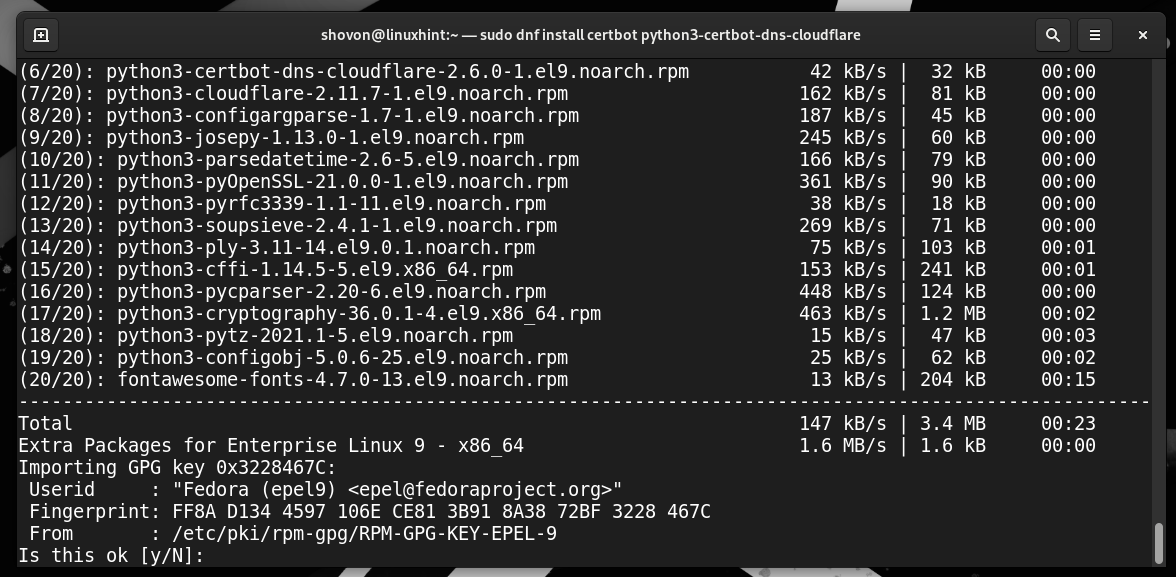
Certbot and Certbot CloudFlare DNS plugin are being installed. It takes a while to complete.
To accept the GPG key of the EPEL repository, press “Y” and then press <Enter>.
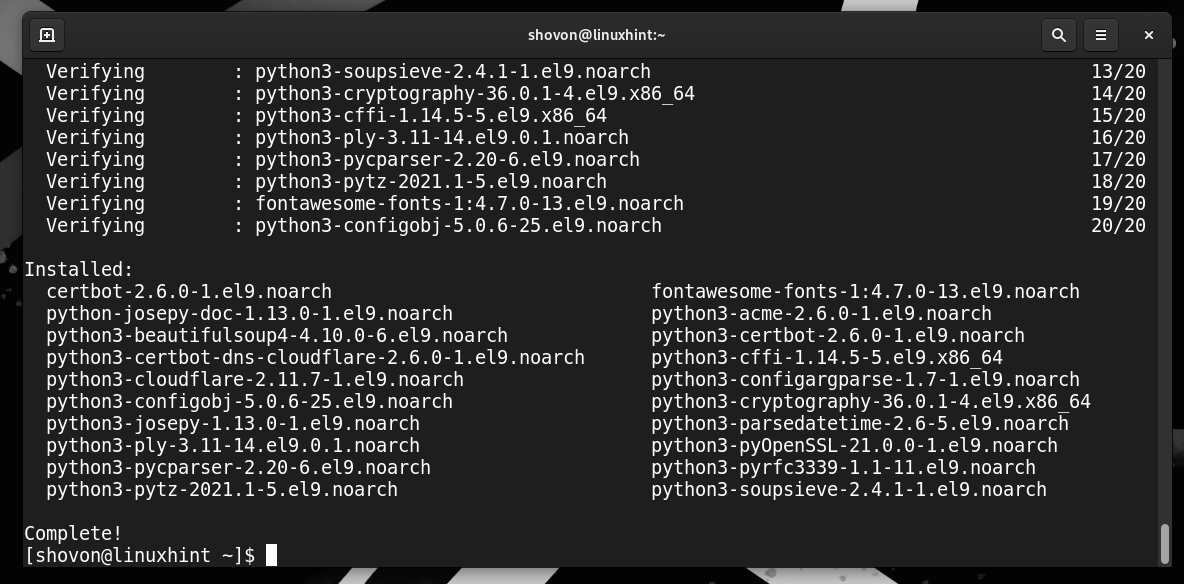
At this point, Certbot and Certbot CloudFlare DNS plugin should be installed.
Checking If Certbot and Certbot CloudFlare Plugin Are Installed Correctly
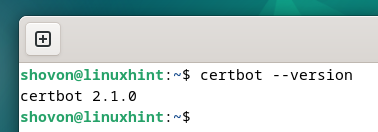
To check whether Certbot is installed on your computer, run the following command:
If Certbot is installed, the command should print the version number of the installed Certbot on your computer.
As you can see, we have Certbot 2.1.0 installed on our Debian machine.
To check whether the Certbot CloudFlare DNS plugin is installed on your computer, run the following command:
If the Certbot CloudFlare DNS plugin is installed, you should find the “dns-cloudflare” in the plugins list as marked in the following screenshot:
Generating a CloudFlare API Token
To verify the ownership of the domain, Certbot needs to add a TXT record on the domain that is managed by the CloudFlare DNS server. For that, Certbot needs access to the CloudFlare API token. You can create an API token for your domain from the CloudFlare dashboard.
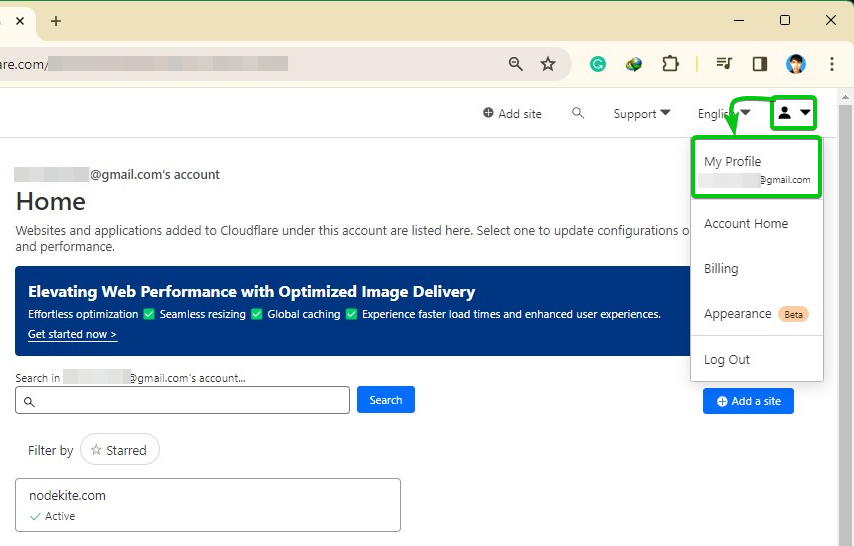
First, log in to your CloudFlare account. Then, click on your profile icon
> My Profile from the top-right corner of the page.
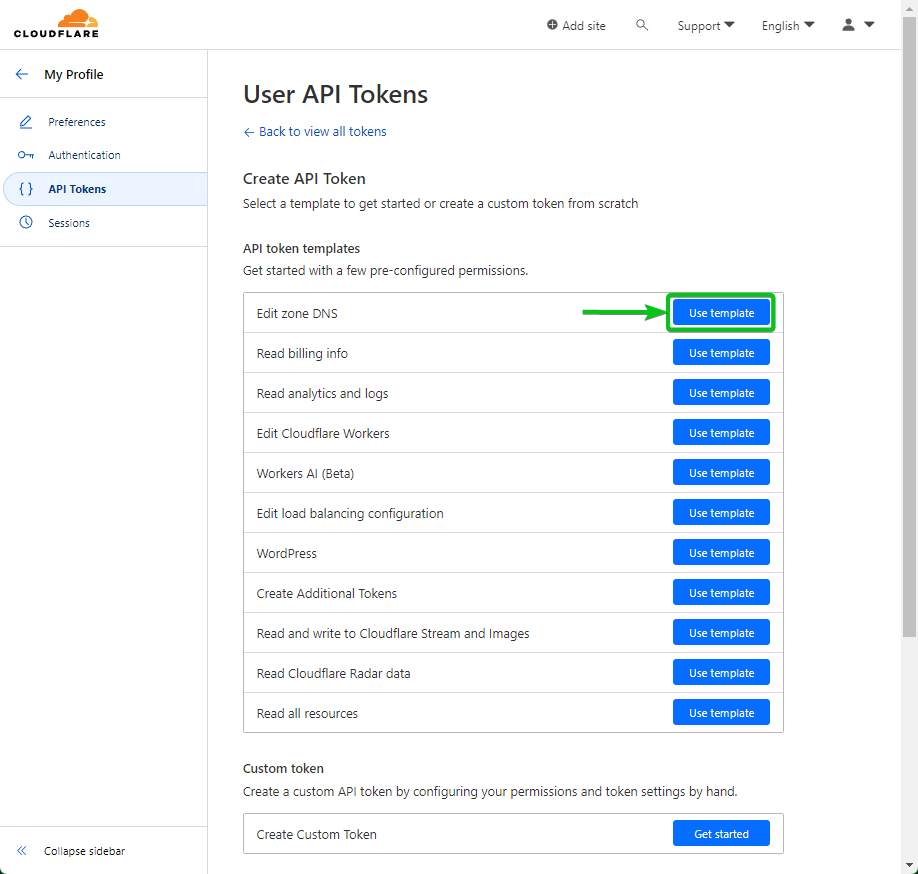
Click on “Use template” from the “Edit zone DNS” section.
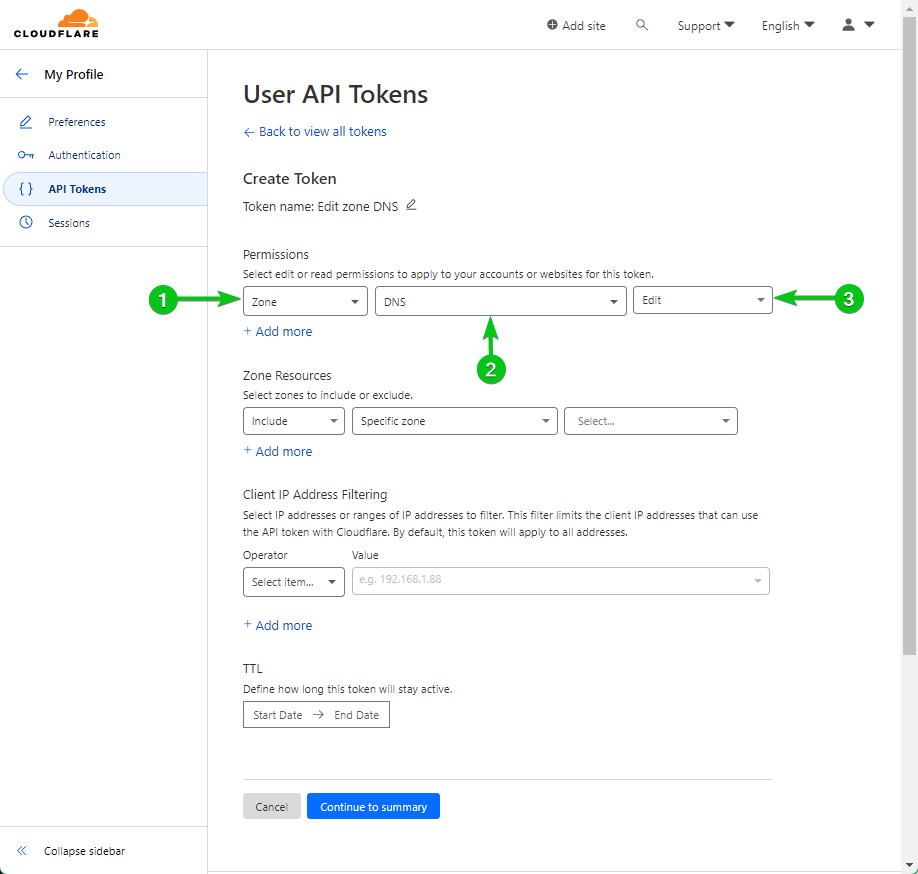
From the “Permission” section, allow the “Edit” permission to “DNS Zone” by selecting the marked options from the dropdown menus.
If you’re managing multiple domains with CloudFlare, you can allow the modification of a “Specific zone” from the “Zone Resource” section. Allowing an API token to modify only a single zone is more secure than allowing the API token to modify all zones. This is because if the API token is compromised, the attack surface will be smaller and less damage will be done.
If you want to use a single API key to modify all of your CloudFlare-managed domains, select “All zones” from the “Zone Resource” section.
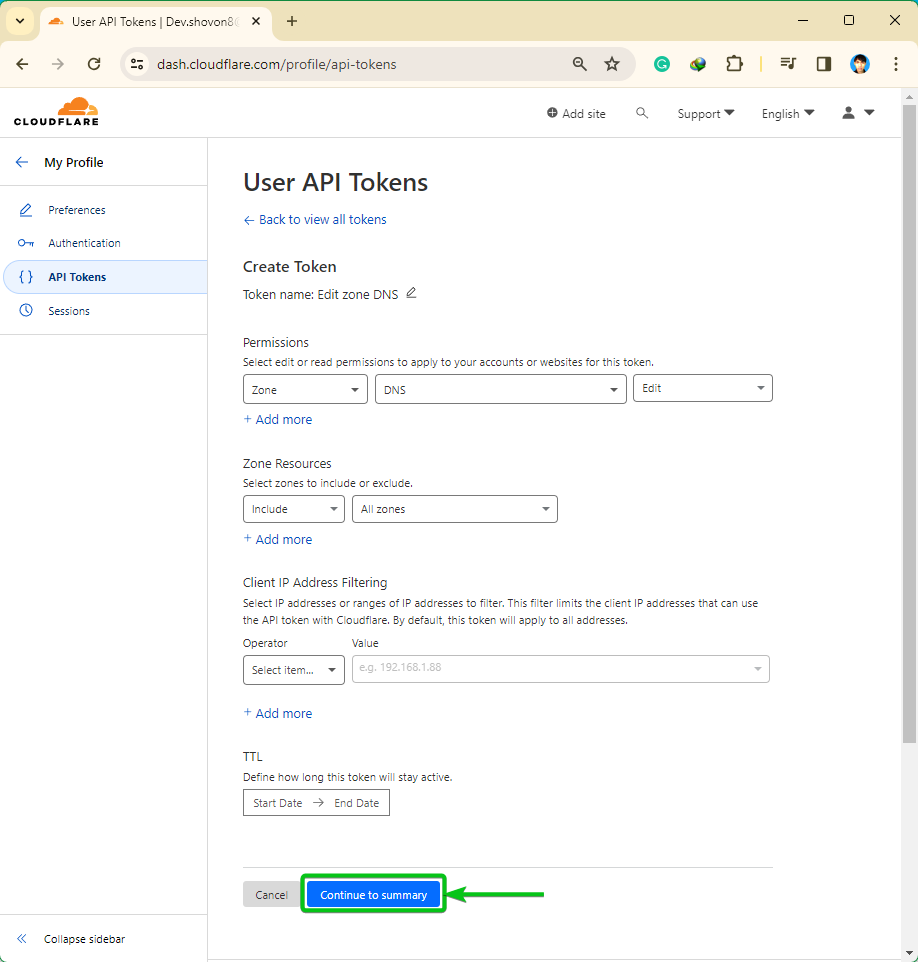
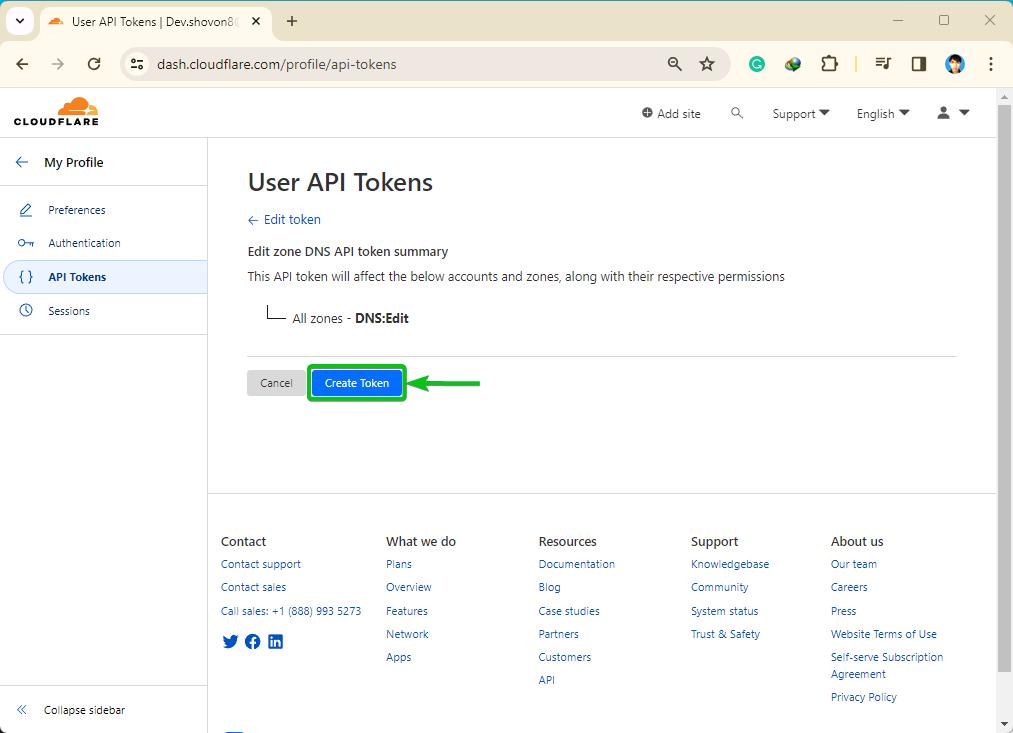
Once you’re done configuring your API token, click on “Continue to summary”.
A summary of the actions that you can perform on your CloudFlare-managed domains with the API token will be displayed. Click on “Create Token”.
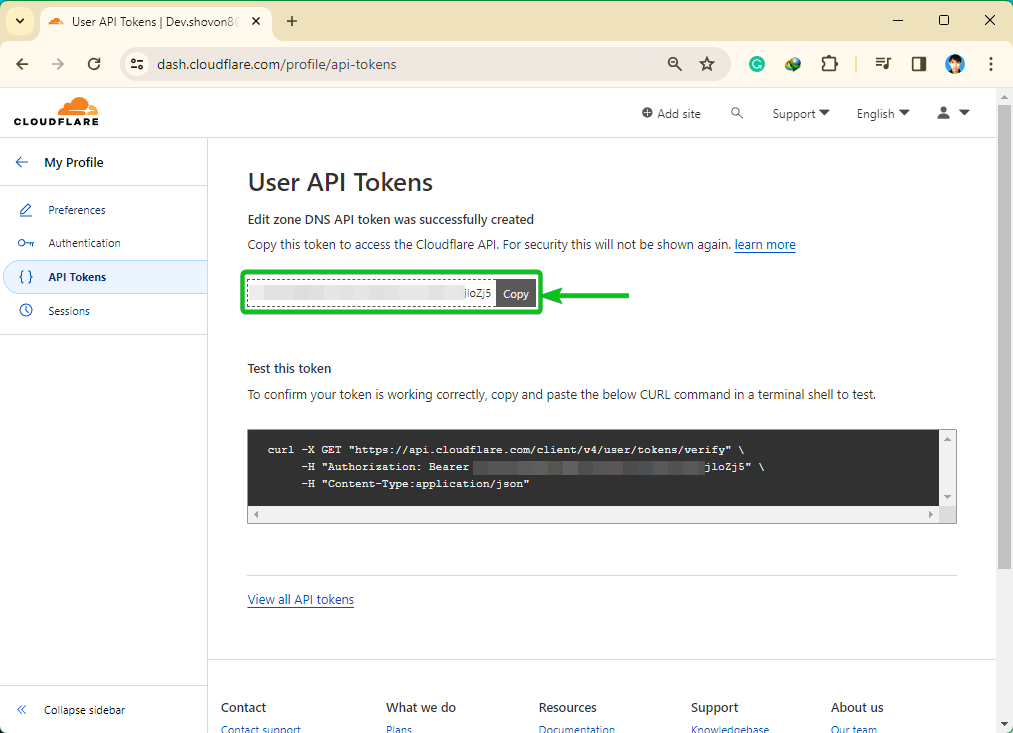
An API token should be created. Copy the API token somewhere safe so you don’t lose it. Once you leave this page, you won’t be able to find this API token again. You have to generate a new API token in case you lose it:
LyPCAcOBygX1UMHvcsvBFo41aItm2cCVxnjloZj5
Securely Storing the CloudFlare API Token on the Computer/Server
Certbot needs to use the CloudFlare API token to add a new TXT record for your domain in the CloudFlare DNS server. So, you must store the CloudFlare API token on your computer/server. Storing the API token without ensuring the proper file access permissions may allow the other programs/users with an access to the API token. This is not what you want for security reasons. In this section, we will show you how to securely store the CloudFlare API token on the filesystem.
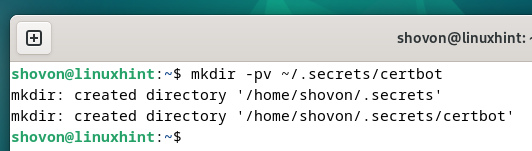
First, create a directory (i.e. ~/.secrets/certbot) where you want to store the CloudFlare API key as follows:
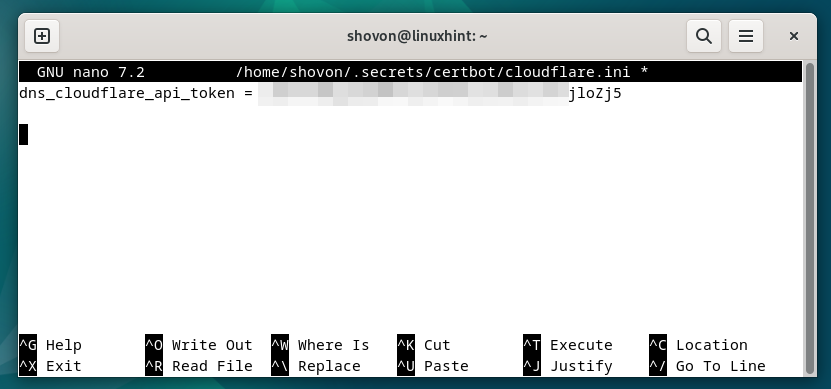
Create a “cloudflare.ini” file in the newly created directory (i.e. ~/.secrets/certbot) and open it with your favorite text editor (i.e. nano) as follows:
Type in the following line in the “cloudflare.ini” file and press <Ctrl> + X followed by “Y” and <Enter> to save it (if you’re using the nano text editor).
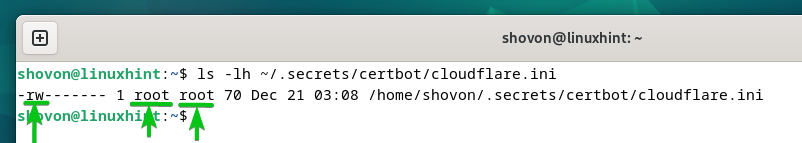
To ensure a proper access permission for the “cloudflare.ini” file, run the following commands to make sure that only the root user has the read and write access to the file:
$ sudo chmod 0600 ~/.secrets/certbot/cloudflare.ini
As you can see, only the root user has the read and write permissions to the “cloudflare.ini” file.
Other users who attempt to read the “cloudflare.ini” file will get a “Permission denied” error message.
Generating an SSL Certificate Using the Certbot CloudFlare DNS Validation
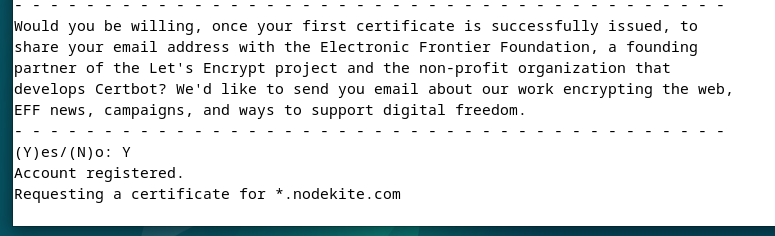
To generate a Let’s Encrypt SSL certificate for the wildcard domain name “*.nodekite.com” using the CloudFlare DNS validation, run the cerbot command as follows:
To generate a Let’s Encrypt SSL certificate for the domain names “nodekite.com” and “www.nodekite.com” using the CloudFlare DNS validation, use the “-d” option of the certbot command for each domain name as follows:
If the DNS changes take a long time to propagate to the popular DNS nameservers worldwide, you can use the “–dns-cloudflare-propagation-seconds” option of Certbot to set the number of seconds that you want Certbot to wait before the DNS validation is performed.
Once you run the Certbot command, you will be asked to type in your email address. Type in your email address and press <Enter> to continue.
Press “Y” and then press <Enter> to accept the “Terms of Service” of Let’s Encrypt.
Press “Y” and then press <Enter>.
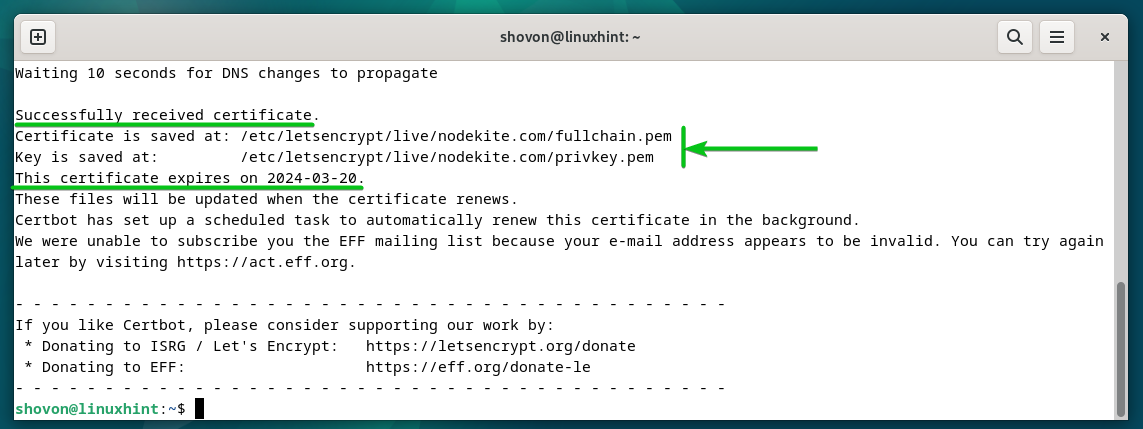
A Let’s Encrypt SSL certificate is being issued. It takes a while to complete.
At this point, the Let’s Encrypt SSL certificate is issued. The full path where the SSL certificate files are saved should be displayed. The expire date of the SSL certificate should also be displayed.
Listing the Let’s Encrypt SSL Certificates Using Certbot
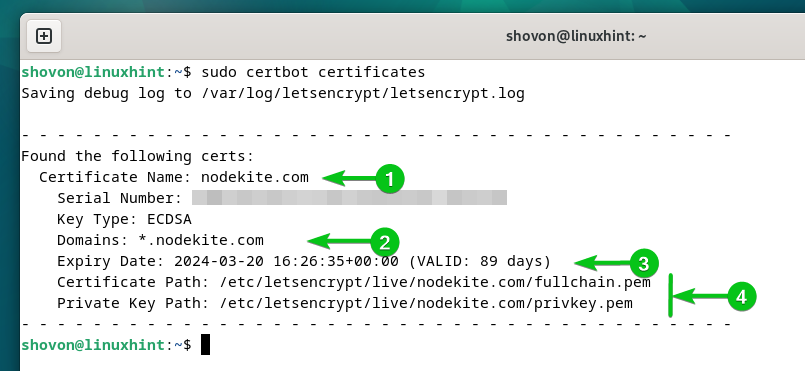
You can list all the Let’s Encrypt SSL certificates that you generated using Certbot with the following command:
As you can see, the generated Let’s Encrypt SSL certificate for the “nodekite.com” domain is listed[1]. A wildcard SSL certificate is issued for the “nodekite.com”[2] domain name. The expiry date of the certificate is 2024-03-20 (valid for 89 days)[3]. The certificate and private key path are also listed here[4].
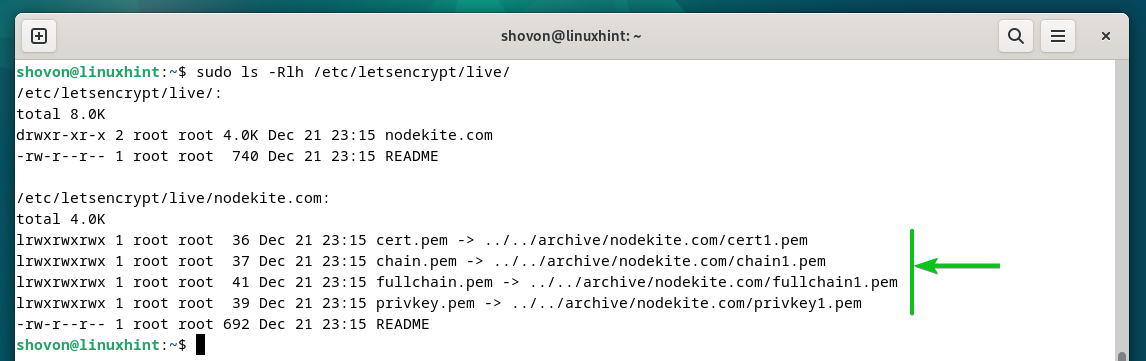
Certbot stores all the SSL certificates that you generated for your domains in the “/etc/letsencrypt/live” directory in their respective folder.
Renewing the Let’s Encrypt SSL Certificates Using Certbot
Certbot automatically renews all the Let’s Encrypt SSL certificates that you generated using the CloudFlare DNS validation.
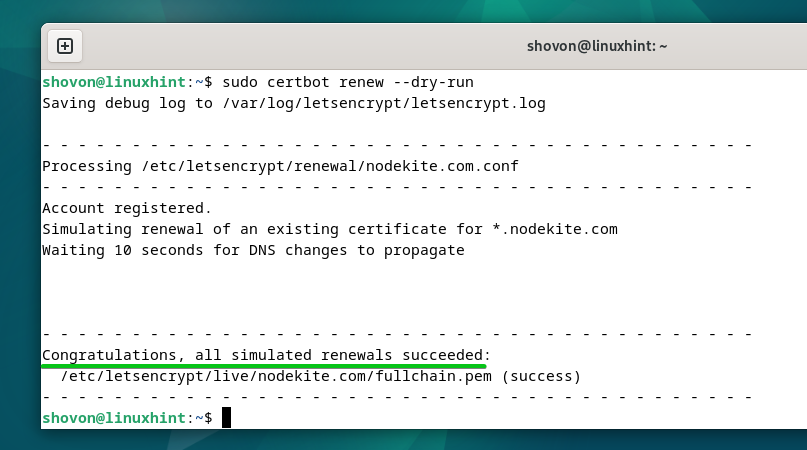
To test if the auto-renewal feature of the Let’s Encrypt SSL certificates works, run the following command:
The auto-renewal action is simulated for each of the Let’s Encrypt SSL certificates that you generated.
If the tests are successful, you will be congratulated. A successful test means that the SSL certificates will be automatically renewed before they expire. You won’t have to do anything else.
For the Certbot auto-renew feature to work, the “cerbot.timer” systemd timer must be enabled and active on your computer/server.
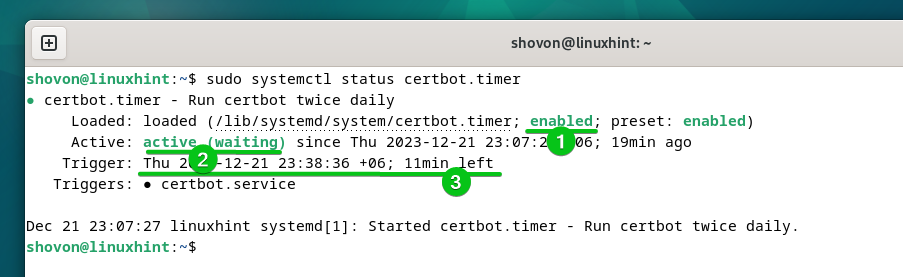
You can check whether the “cerbot.timer” systemd timer is enabled and active with the following command:
As you can see, the “certbot.timer” systemd timer is enabled (automatically starts at boot time)[1] and active[2]. Certbot checks if there’s a need to renew any SSL certificate after just 11 minutes (according to the following screenshot) and renews the SSL certificates that are about to expire[3].
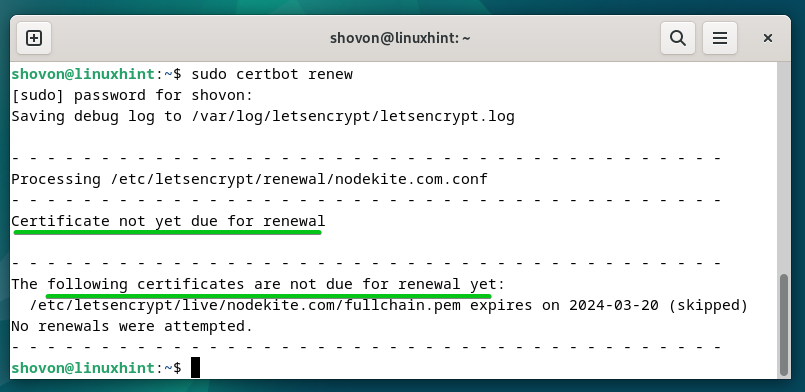
To manually check if any SSL certificate is about to expire and renew the expiring SSL certificates, run the following command:
In our case, no SSL certificate is about to expire. So, Certbot did not attempt to renew any SSL certificate.
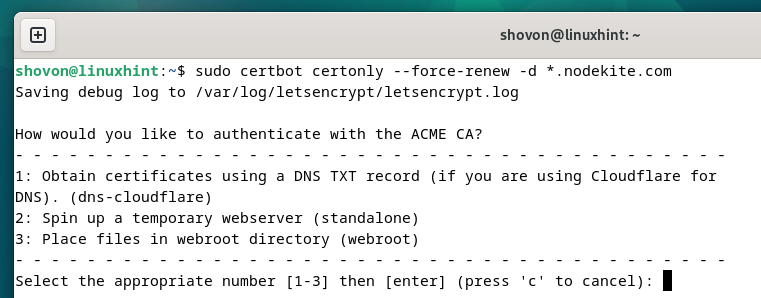
To force Certbot to renew the SSL certificate of a specific domain (let’s say *.nodekite.com), run the following command:
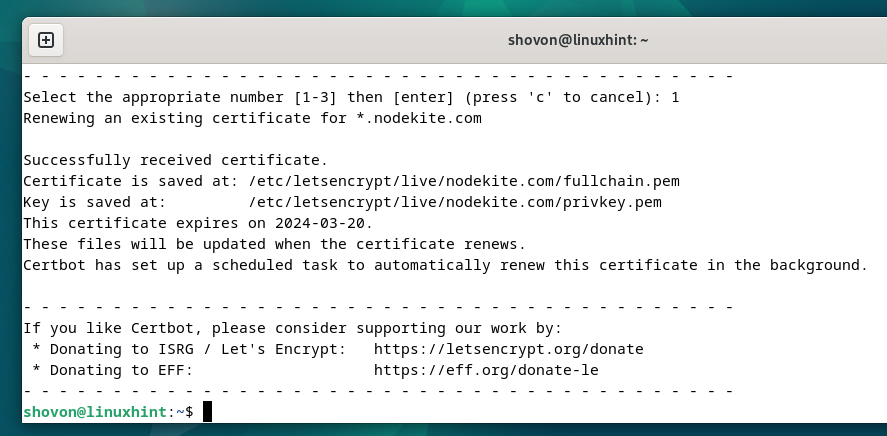
Press “1” and press <Enter> to select the first option (for DNS validation using CloudFlare DNS).
The SSL certificate should be renewed.
Conclusion
To get a Let’s Encrypt SSL certificate using the CloudFlare DNS validation using Certbot, you need an access to the CloudFlare API token. In this article, we showed you how to create a CloudFlare API token for your domain and securely store it on your computer/server so that you can access it with Certbot when needed. We also showed you how to install Certbot and the Certbot CloudFlare DNS plugin on the most popular Linux distributions. We showed you how to generate the Let’s Encrypt wildcard SSL certificates as well as SSL certificates for single domains using Certbot and CloudFlare DNS validation. Finally, we showed you how to renew the Let’s Encrypt SSL certificates using Certbot automatically and manually.