The hmac module in Python offers us an implementation for this method. It uses the form of a hashing algorithm as an input, which is one of the algorithms mentioned in Python’s hashlib module. This article will show you how to build message authentication code with Python’s hmac module using simple examples.
Example 1:
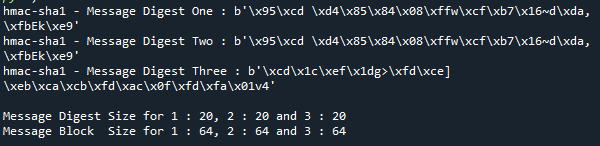
This is the article’s first example. The message and key (marked as “msgg” and key_val in our code) are first initialized in this example’s code. It then uses the key and the sha1 algorithm to create a message authentication code for the given message in three distinct ways.
We first construct an instance of HMAC using the new() method, passing it bytes for the key and message and “sha1” for the hashing algorithm.
The new() method generates an instance of HMAC with a bytes-based initial message. It can then be used to produce code for message authentication. Without the starting message, we can only build an instance of HMAC. But we’ll require a key and “digestmod” for this purpose.
A call to the update() method can be used to add messages. The key must follow a byte format. The digestmod parameter accepts names of secure hashing algorithms from the hashlib module.
The message authentication code is then printed. The HMAC instance is created without any starting message in the second half of the code. After that, the message will be added using the update() method. The update() method adds messages passed in as input to a message that already exists. We can call this method multiple times, and it will continue to accumulate messages.
Finally, it calculates and prints the digest. The code in the third section generates an instance of HMAC with no initial message. The update() method is then used to add messages in two sections. Finally, it calculates and prints the digest. Finally, the code publishes the digest and block sizes for each HMAC instance.
The digest() method returns the data’s message authentication code. The code is in bytes format. The output size is determined by the input secure hashing algorithm. If the hashing algorithm used in the input is SHA1, the output will be 20 bytes. For your understanding of the concept, we have attached an image of the entire code below.
msgg = "Python is easy."
key_val = "abcxyz"
hmac_one = hmac.new(key=key_val.encode(), msg=msgg.encode(), digestmod="sha1")
message_digest_one = hmac_one.digest()
print("{} - Message Digest One : {}".format(hmac_one.name, message_digest_one))
hmac_two = hmac.new(key=key_val.encode(), digestmod="sha1")
hmac_two.update(bytes(msgg, encoding="utf-8"))
message_digest_two = hmac_two.digest()
print("{} - Message Digest Two : {}".format(hmac_two.name, message_digest_two))
hmac_three = hmac.new(key=key_val.encode(), digestmod="sha1")
hmac_three.update(bytes("Programming is", encoding="utf-8"))
hmac_three.update(bytes("easy and fun", encoding="utf-8"))
message_digest_three = hmac_three.digest()
print("{} - Message Digest Three : {}".format(hmac_three.name, message_digest_three))
print("\nMessage Digest Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.digest_size, hmac_two.digest_size,hmac_three.digest_size,))
print("Message Block Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.block_size, hmac_two.block_size,hmac_three.block_size,))
Here, the authentication message and the byte size are displayed upon executing the attached code.
Example 2:
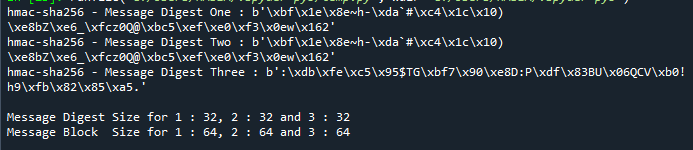
In our second example, we’ll show you how to construct message authentication codes using the HMAC technique once more, but this time with the SHA256 secure hashing algorithm. Our code for this section is nearly identical to that of our prior example, with a few small differences. It makes use of the hashlib library’s reference to the SHA256 algorithm.
import hashlib
msg_one = "Python is easy to learn."
key_one = "aabbccxxyyzz"
hmac_one = hmac.new(key=key_one.encode(), msg=msg_one.encode(), digestmod=hashlib.sha256)
message_digest_one = hmac_one.digest()
print("{} - Message Digest One : {}".format(hmac_one.name, message_digest_one))
hmac_two = hmac.new(key=key_one.encode(), digestmod=hashlib.sha256)
hmac_two.update(bytes(msg_one, encoding="utf-8"))
message_digest_two = hmac_two.digest()
print("{} - Message Digest Two : {}".format(hmac_two.name, message_digest_two))
hmac_three = hmac.new(key=key_one.encode(), digestmod=hashlib.sha256)
hmac_three.update(bytes("Learn", encoding="utf-8"))
hmac_three.update(bytes("Python", encoding="utf-8"))
message_digest_three = hmac_three.digest()
print("{} - Message Digest Three : {}".format(hmac_three.name, message_digest_three))
print("\nMessage Digest Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.digest_size, hmac_two.digest_size,hmac_three.digest_size,))
print("Message Block Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.block_size, hmac_two.block_size,hmac_three.block_size,))
Here is the result where you can see that we have calculated the message authentication code using the HMAC algorithm and SHA256.
Example 3:
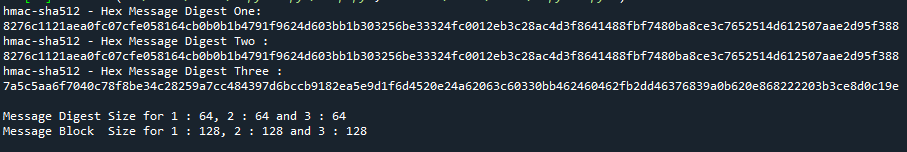
In our third example, we’ll show how to construct a hex message authentication code with the HMAC technique and SHA256 as the backend. This example’s code is identical to the previous one, with the exception that we’re using the hexdigest() technique to calculate the hexadecimal authentication code.
The hexdigest method returns data as hexadecimal digits as a message authentication code. Because one byte can make two hexadecimal digits, this is the case.
The output size is determined by the input secure hashing algorithm. If the SHA1 input hashing algorithm is used, for example, the resultant value will be 40 hexadecimal digits.
import hashlib
msg_one = "All about Python."
key_one = "aabbccxyz"
hmac_one = hmac.new(key=key_one.encode(), msg=msg_one.encode(), digestmod=hashlib.sha512)
message_digest_one = hmac_one.hexdigest()
print("{} - Hex Message Digest One: {}".format(hmac_one.name, message_digest_one))
hmac_two = hmac.new(key=key_one.encode(), digestmod=hashlib.sha512)
hmac_two.update(bytes(msg_one, encoding="utf-8"))
message_digest_two = hmac_two.hexdigest()
print("{} - Hex Message Digest Two : {}".format(hmac_two.name, message_digest_two))
hmac_three = hmac.new(key=key_one.encode(), digestmod=hashlib.sha512)
hmac_three.update(bytes("All about ", encoding="utf-8"))
hmac_three.update(bytes("Python language.", encoding="utf-8"))
message_digest_three = hmac_three.hexdigest()
print("{} - Hex Message Digest Three : {}".format(hmac_three.name, message_digest_three))
print("\nMessage Digest Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.digest_size, hmac_two.digest_size,hmac_three.digest_size,))
print("Message Block Size for 1 : {}, 2 : {} and 3 : {}".format(hmac_one.block_size, hmac_two.block_size,hmac_three.block_size,))
Below is the output screenshot where you can see that the authentication messages and the digest size and block size are displayed.
Example 4:
We demonstrate how to produce message authentication code without establishing an instance of the HMAC by utilizing the digest() method of the hmac module. digest(key, msg, digest) – It takes as input a key, a message to encode, and the digest algorithm generate an authentication code for the provided message.
This code demonstrates how to use the digest() method to construct a message authentication code for a specific message directly from the input key, rather than creating an instance of HMAC as in the previous example. Because it employs an optimized C implementation for constructing the digest, this method is faster than using HMAC to create authentication codes for tiny communications.
import hashlib
msgg = "Python Programming"
key_one = "abcabcabc"
message_digest_one = hmac.digest(key=key_one.encode(), msg=msgg.encode(), digest="sha3_256")
print("Message Digest One : {}".format(message_digest_one))
message_digest_two = hmac.digest(key=key_one.encode(), msg=bytes(msgg, encoding="utf-8"), digest=hashlib.sha3_256)
print("Message Digest Two : {}".format(message_digest_two))
Here is the result in which you can see that the message authentication code is created by using the digest() method.
Conclusion:
HMAC is a cryptographic hash function-based message authentication technique. The widely used HMAC technique is discussed in detail in this post. The main idea of this approach is to use a shared secret key to combine a cryptographic hash of the actual data. This is for the sole purpose of creating a shared secret key. We’ve gone through this idea in-depth and provided examples to help you understand it.