FTP
FTP is a protocol used by computers to share information over the network. Simply put, it’s a way to share files between connected computers. As HTTP is built for Websites, FTP is optimized for large file transfers between computers.
The FTP client first builds a control connection request to the server port 21. A control connection requires a login to establish a connection. But some servers make all of their content available without any credentials. Such servers are known as anonymous FTP servers. Later a separate data connection is established to transfer files and folders.
FTP Traffic Analysis
The FTP client and server communicate while being unaware that TCP manages every session. TCP is generally used in every session to control datagram delivery, arrival, and window size management. For every datagram exchange, TCP initiates a new session between the FTP client and the FTP server. Hence, we will begin our analysis with the available TCP packet information for the FTP session initiation and termination in the middle pane.
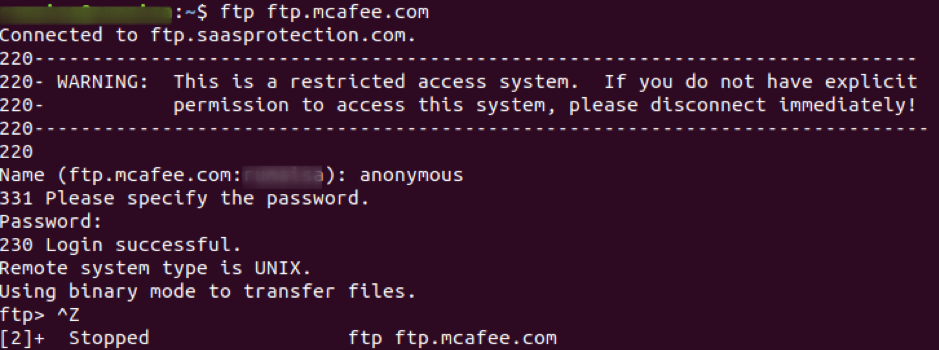
Start packet capture from your selected interface and use the ftp command in the terminal to access the site ftp.mcafee.com.
ubuntu$ubuntu:~$ ftp ftp.mcafee.com
Log-in with your credentials, as shown in the screenshot below.
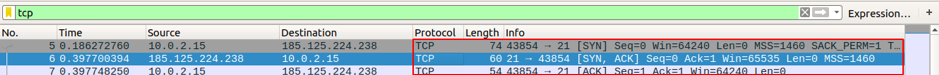
Use Ctrl+C to stop the capture and look for the FTP session initiation, followed by the tcp [SYN], [SYN-ACK], and [ACK] packets illustrating a three-way handshake for a reliable session. Apply tcp filter to see the first three packets in the Packet list panel.
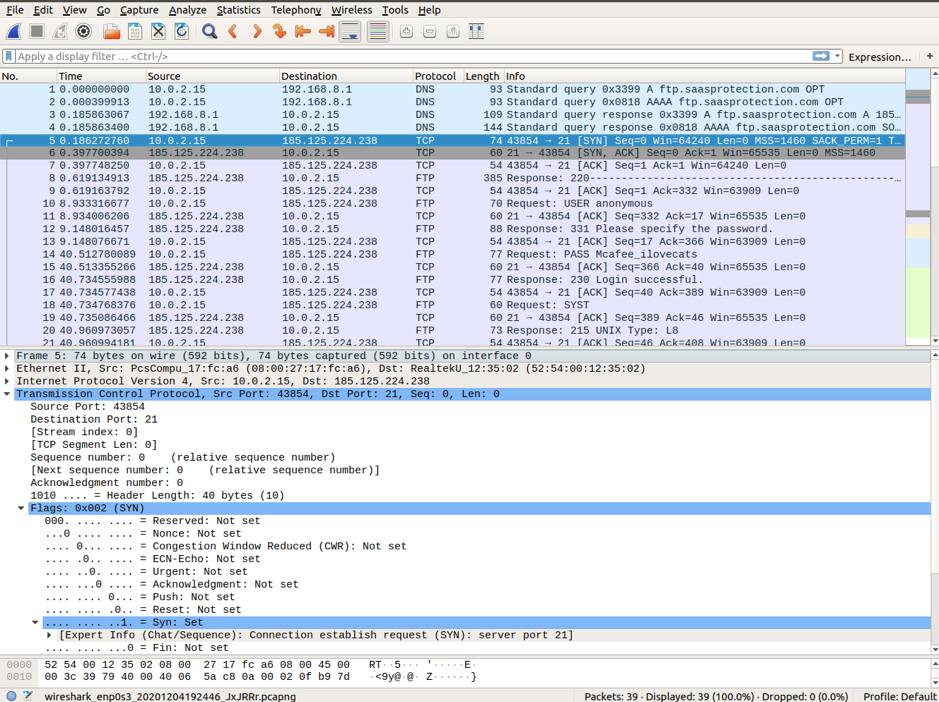
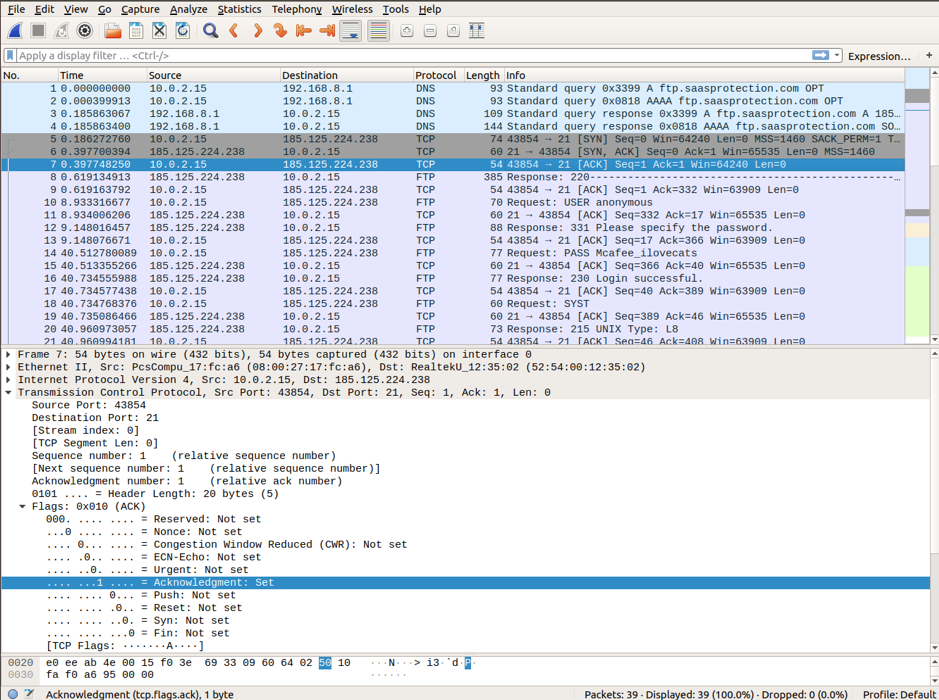
Wireshark displays detailed TCP information that matches the TCP packet segment. We highlight the TCP packet from the host computer to the ftp McAfee server to study the Transfer Control Protocol layer in the Packet detail panel. You can notice that the first TCP datagram for the ftp session initiation only sets SYN bit to 1.
The explanation for each field in the Transport Control Protocol layer in Wireshark is given below:
- Source Port: 43854, it’s the TCP host that initiated a connection. It’s a number that lies anywhere above 1023.
- Destination Port: 21, it’s a port number associated with ftp service. That means, FTP server listens on port 21 for client connection requests.
- Sequence Number: It’s a 32-bit field that holds a number for the first byte sent in a particular segment. This number helps in the identification of the messages received in order.
- Acknowledgment Number: A 32-bit field specifies an acknowledgment receiver expects to receive after successful transmission of previous bytes.
- Control Flags: each code bit form has a special meaning in TCP session management that contributes to each packet segment’s treatment.
ACK: validates acknowledgment number of a receipt segment.
SYN: synchronize sequence number, which is set at the initiation of a new TCP session
FIN: request for session termination
URG: requests by the sender to send urgent data
RST: request for resetting the session
PSH: request for push
- Window size: it’s the sliding window’s value that tells the size of sent TCP bytes.
- Checksum: field that holds checksum for error control. This field is mandatory in TCP in contrast to UDP.
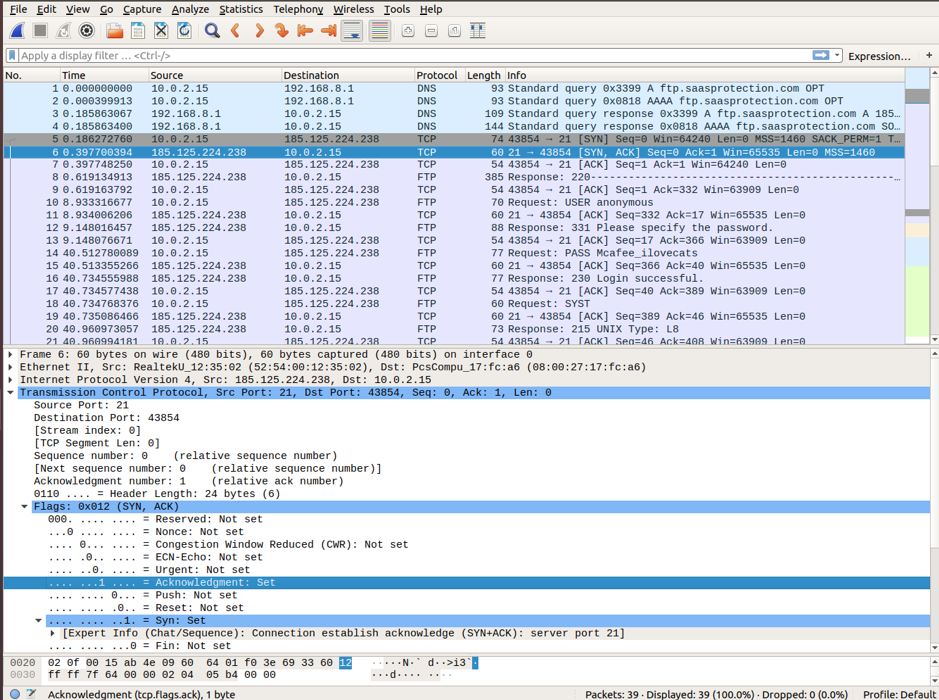
Moving toward the second TCP datagram captured in the Wireshark filter. The McAfee server acknowledges the SYN request. You can notice the values of SYN and ACK bits set to 1.
In the last packet, you can notice that the host sends an acknowledgment to the server for FTP session initiation. You can notice that the Sequence number and the ACK bits are set to 1.
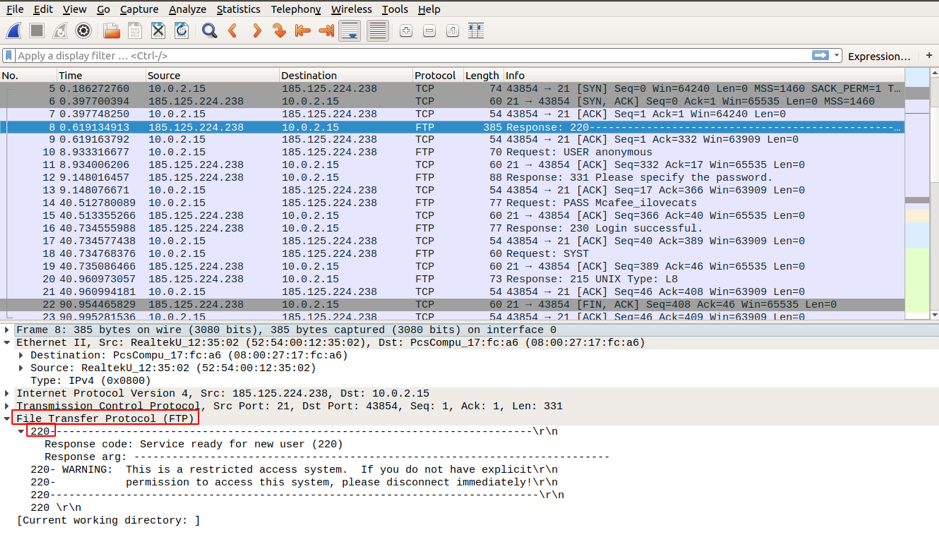
After establishing a TCP session, the FTP client and server exchange some traffic, the FTP client acknowledges the FTP server Response 220 packet sent via TCP session through a TCP session. Hence, all the information exchange is carried out via TCP session at FTP client and FTP server.
After the FTP session completion, the ftp client sends the termination message to the server. After request acknowledgment, the TCP session at the server sends a termination announcement to the client’s TCP session. In response, the TCP session at the client acknowledges the termination datagram and sends its own termination session. After receipt of the termination session, the FTP server sends an acknowledgment of the termination, and the session is closed.
Warning
FTP does not use encryption, and the login and password credentials are visible in broad daylight. Hence, as long as no one is eavesdropping and you are transferring sensitive files within your network, it’s safe. But do not use this protocol to access content from the internet. Use SFTP that uses secure shell SSH for file transfer.
FTP Password Capture
We will now show why it’s important not to use FTP over the internet. We will look for the specific phrases in the captured traffic containing user, username, password, etc., as instructed below.
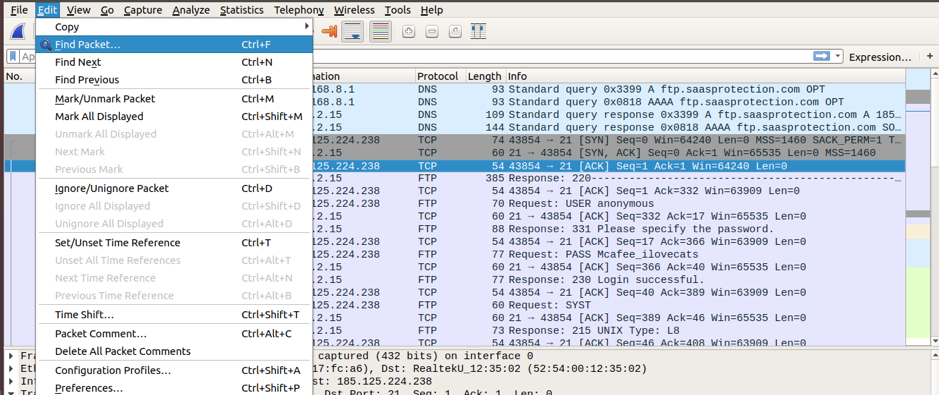
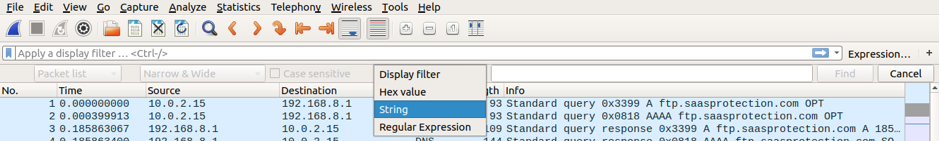
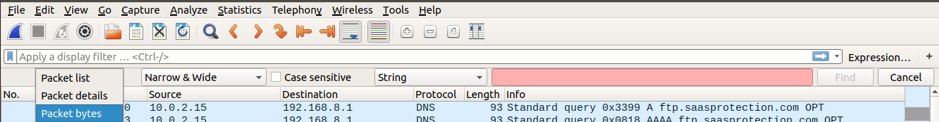
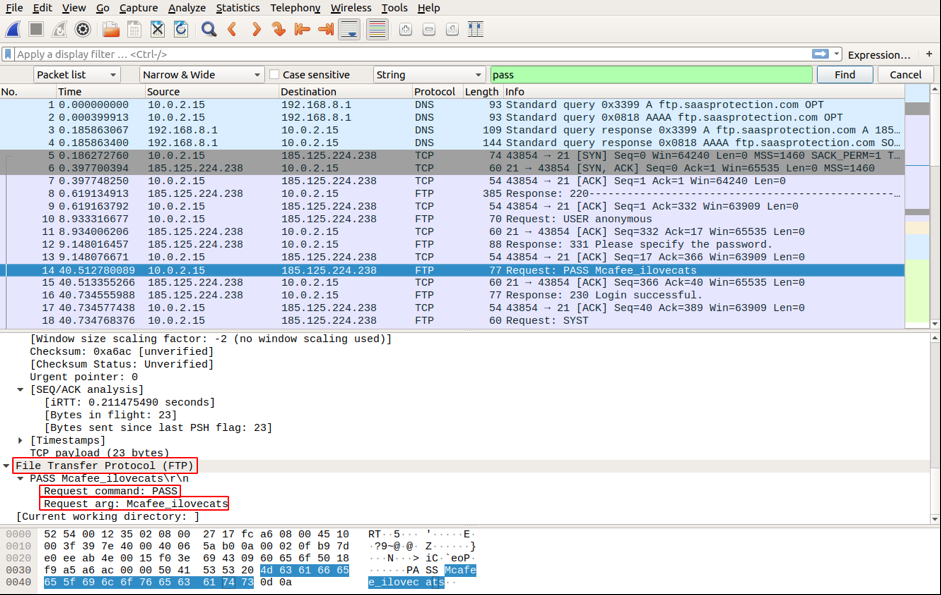
Go to Edit-> “Find Packet” and choose String for the Display Filter, and then select Packet bytes to show searched data in cleartext.
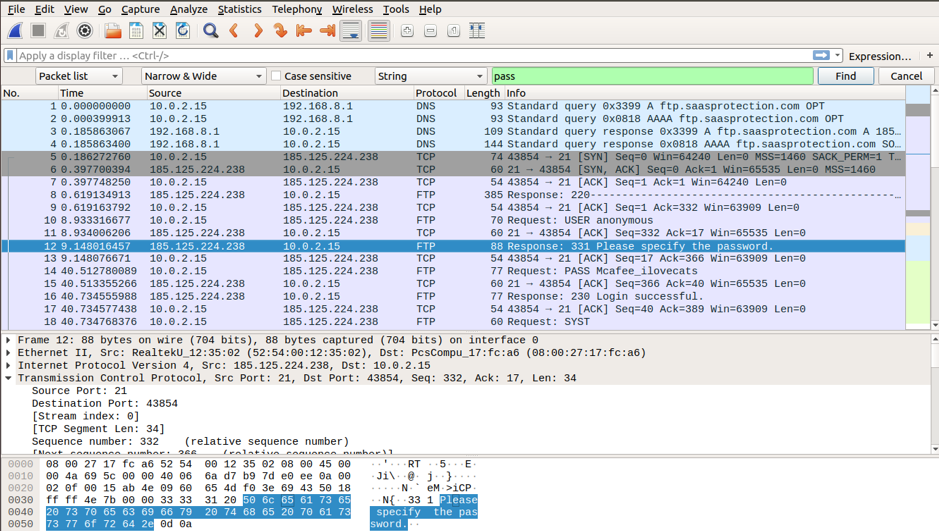
Type in the string pass in the filter, and click Find. You will find the packet with the string “Please specify the password” in the Packet bytes panel. You can also notice the highlighted packet in the Packet list panel.
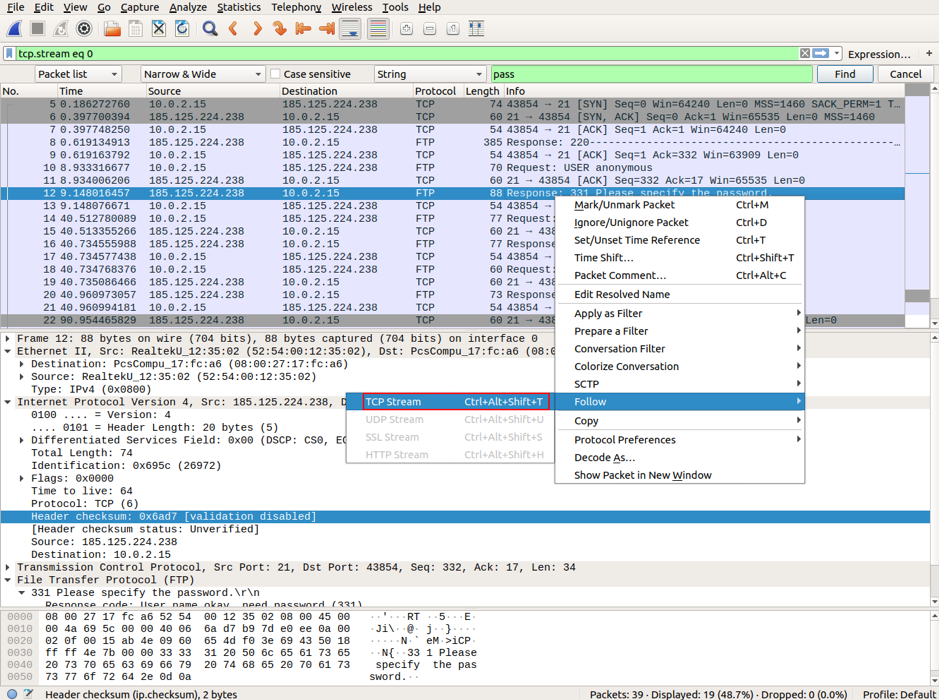
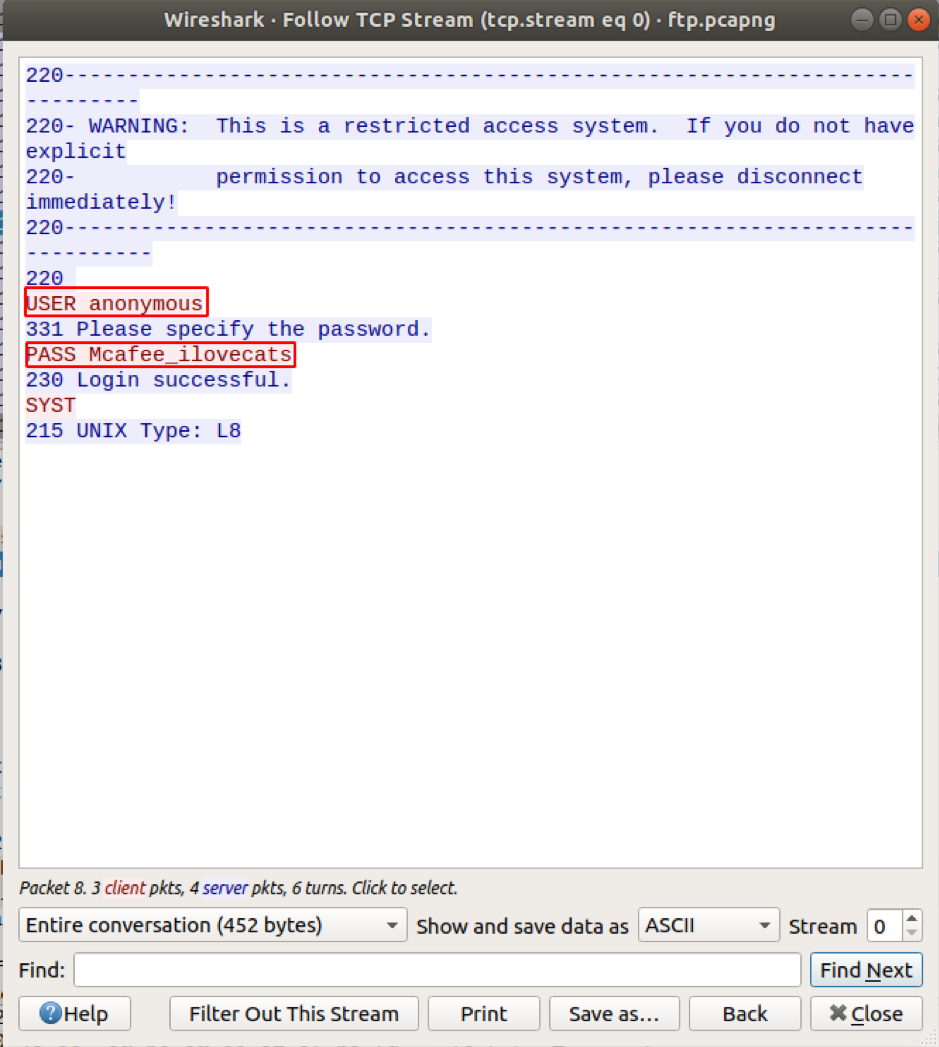
Open this packet in a separate Wireshark window by right-clicking on the packet and select Follow->TCP stream.
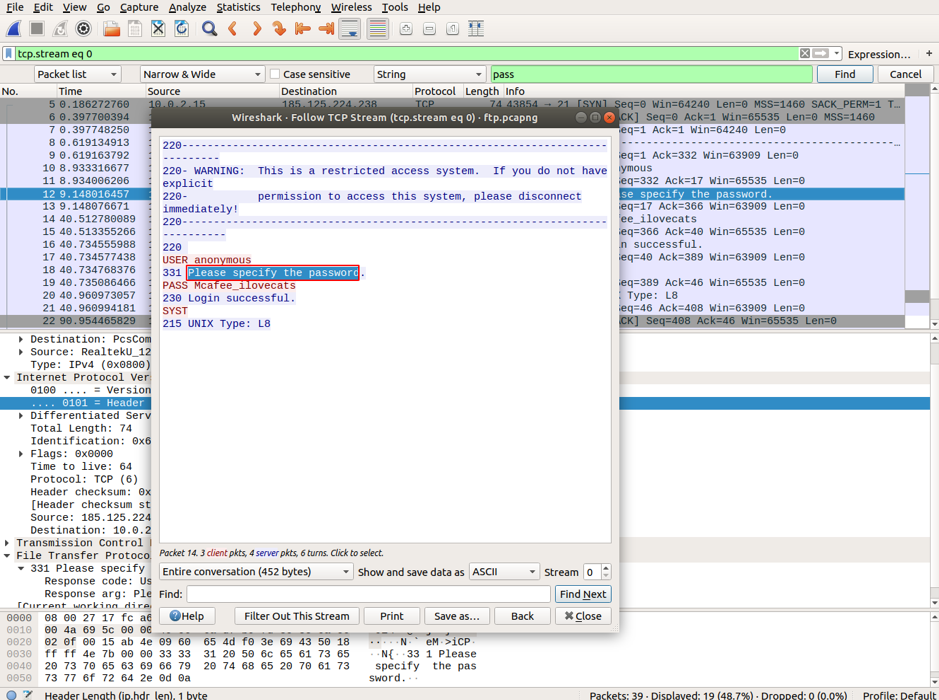
Now search again, and you will find the password in plain text in the Packet byte panel. Open the highlighted packet in a separate window as above. You will find the user credentials in plaintext.
Conclusion
This article has learned how FTP works, analyzed how TCP controls and manages operations in an FTP session, and understood why it’s important to use secure shell protocols for file transfer over the internet. Coming up in future articles, we will cover some of the command-line interfaces for Wireshark.