This article focuses on EAP-TLS. We will highlight its benefits, why you may need it for your organization, how EAP-TLS works, and how secure it is.
But first, let us define and understand what EAP-TLS is.
What Is EAP-TLS?
Commonly referred to as Extensible Authentication Protocol-Transport Layer Security, EAP-TLS is an open standard developed by IETF and defined in RFC 5216. It provides certificate-based mutual authentication. This authentication protocol often comes in handy for WPA2-Enterprise networks as it helps these networks become compatible with X.509 digital certificates.
This protocol uses the TLS public key authentication certificate within the EAP framework to deliver mutual server-to-client or client-to-server authentications. While it is undoubtedly one of the most ultra-secure authentication mechanisms, it is still not as widespread as the other protocols. Besides, the gold standard authentication framework is viable for automated device onboarding processes for MDM and BYOD.
Some of the features of EAP-TLS as an authentication mechanism include:
- It offers mutual authentication which implies that it can provide a server-to-client authentication and client-to-server authentication.
- It features key exchange to establish TKIP keys or dynamic WEP keys.
- It can fragment and reassemble extremely long EAP messages should there be a need.
- The protocol allows for fast and efficient reconnection via TLS session resumption.
How EAP-TLS Works
Despite being the gold standard for network security, EAP-TLS is not as difficult to use as you may think. The authentication framework does not rely on complicated encryption schemes. Instead, it relies on the strength of the public key cryptography.
The cryptography used in this authentication mechanism is unique asymmetric cryptography that leverages the public-private key pairs to generate the symmetric cryptography over unsafe channels. This system eliminates the need for passing over the pre-shared keys.
Although EAP-TLS features a similar architecture to nearly all the other EAP types, it requires mutual authentication. Besides, the X.509 certificates are versatile and dramatically improves the security and user experience. These certificates also allow the SSO configuration to facilitate a broader range of services.
And as highlighted earlier, this protocol uses a certificate-based mutual authentication mechanism. This implies that both the client and server sides require certificates for authentication. The process begins with identifying the certificates before creating the session-based keys for both the server and client to complete the login process.
The following steps take place:
- Users request network access through an authenticator app or a wireless access point.
- The authenticator app or wireless access point (AP) will request the user’s identity credentials.
- The system will transfer the user’s identity information from the AP to the network’s authentication server.
- The server then requests identification verification from the AP.
- The AP fetches the validation and sends the details back to the authentication server.
- The system establishes a connection, and the user will connect directly to the network.
How to Configure FreeRadius to Work with EAP-TLS on Linux
It is vital to note the kinds of hardware and software that you need to make it functional to understand this authentication protocol. Among the things you need include:
- A public key infrastructure
- An access point or AP
- The RADIUS protocol
- A user directory
And the configuration involves the following steps:
Step 1: Install FreeRadius into Your System
Begin by installing a free radius using the following command:
Step 2: Create a Certificate Revocation List
Certificates do not come automatically. Thus, you will need to create them manually. The best way is to use the FreeRadius tutorials. However, you can still achieve this by creating the revocation list using the following command:
Step 3: Create a New File to Hold the Revoked Files and Certificate Authority Files
Proceed to create a fill that holds both the CA (Certificate Authority) and revoked files. The following command should be helpful:
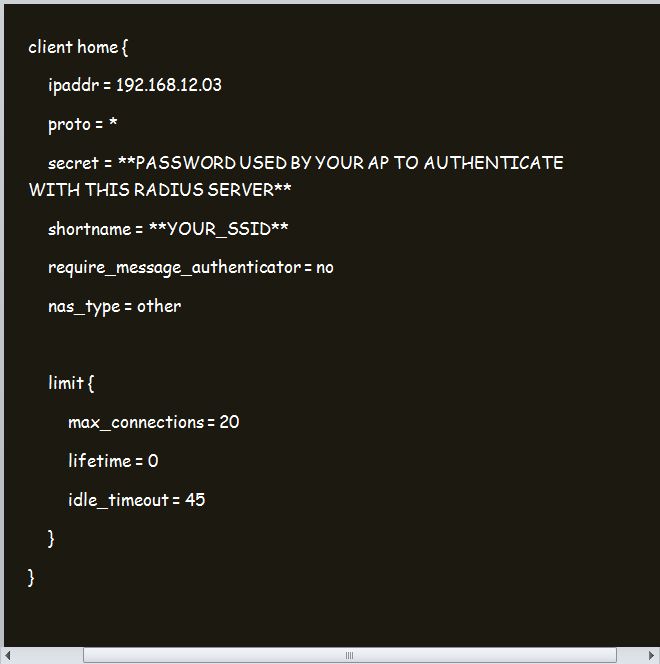
Step 4: Configure the Radius Using the /etc/raddb/clients.conf Command
Configure the radius. Among the top things you should do is to add a client. The client will be your WiFi AP.
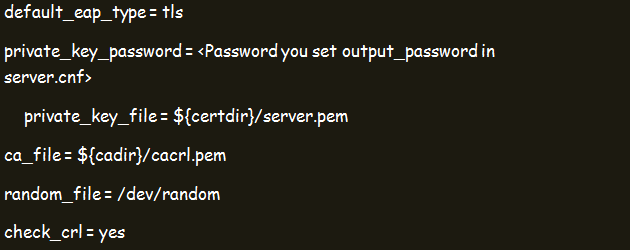
Step 5: Configure EAP Using the /etc/raddb/mods-enabled/eap Command
Once you get the file upon typing the command, ensure that your EAP File only has the following lines by deleting anything else that isn’t in this list:
Conclusion
EAP-TLS is by far a more secure authentication system. It is better than using WPA2 or pre-shared keys which are often prone to cyber-attacks. However, it is vital to use separate certificates for each of your devices in the network.