Auxiliary mods are generally used to perform one-off actions post-exploitation, but you can do far more with this fascinating tool, such as creating your own vulnerability scanners and port scanners. This article will take a detailed look at the auxiliary module in particular, and learn how to create a fuzzer with it.
Step 1: Navigate to the Metasploit Directory
[adthrive-in-post-video-player video-id=”ynp4AFfv” upload-date=”2020-09-14T14:56:29.000Z” name=”Creating a Fuzzer with Metasploit” description=”Creating a Fuzzer with Metasploit” player-type=”collapse” override-embed=”true”]
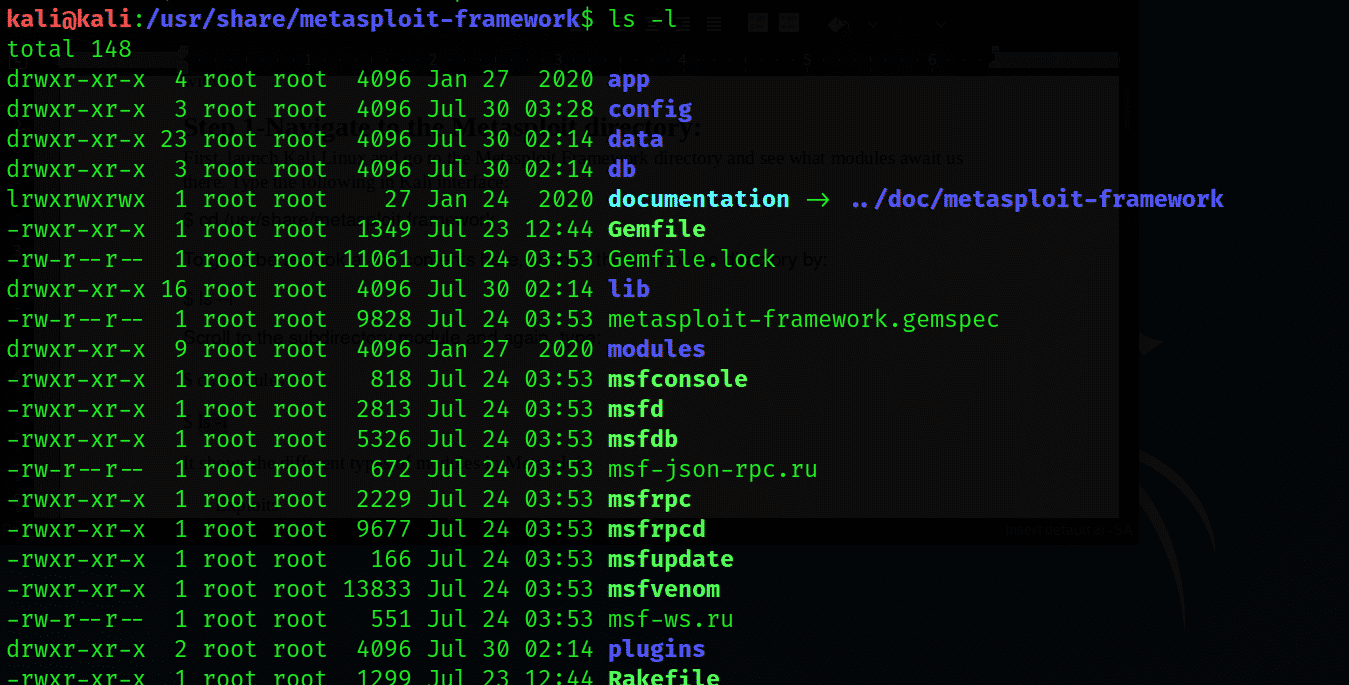
First, launch Kali Linux and go to the Metasploit Framework directory. Type the following in Kali interface:
To get a better look at the contents here, change the view of the directory by entering the following:
Scroll to the subdirectory module and again, type:
This output shows the different types of modules in Metasploit, including:
- Exploits
- Payloads
- Nod
- Post
- Encoders
- Auxiliary
Now, we will examine the auxiliary module in greater detail.
Step 2: Expand Auxiliary Directory
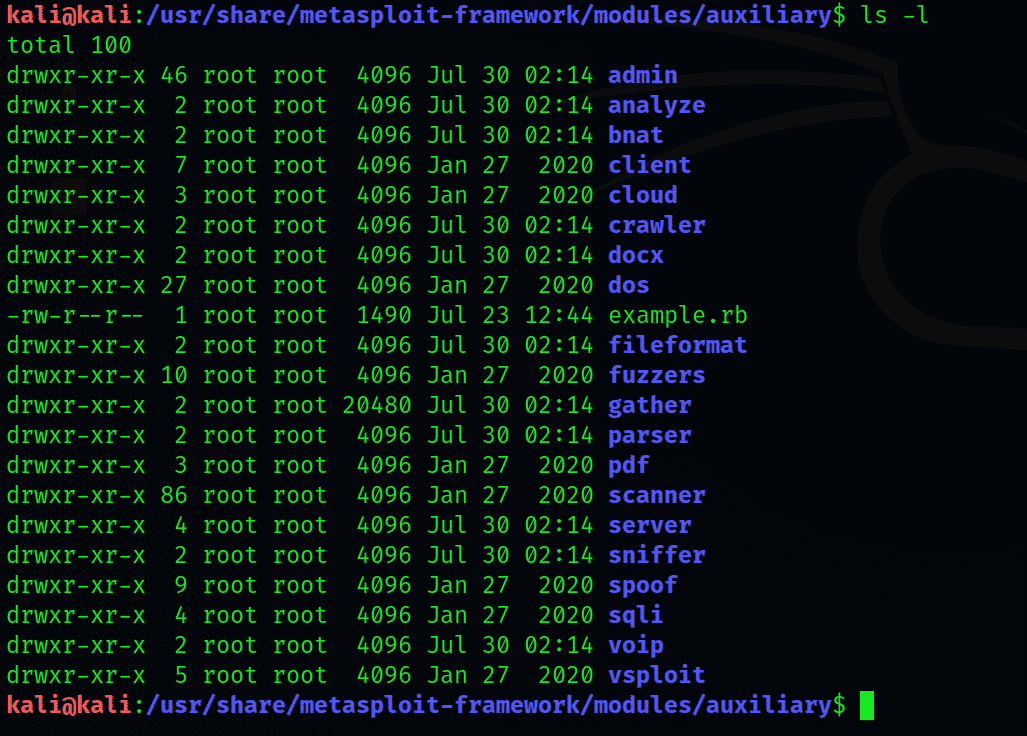
Enter the auxiliary directory
This will compartmentalize the auxiliary module directory into several subdirectories. The output will display a comprehensive list of subdirectories, starting with the admin directory.
Creating Fuzzers
Before we proceed, we will first define what fuzzing is.
Fuzzing: A Brief Introduction
Fuzzing is a practice in software testing discipline that involves continuously putting random, unexpected inputs into a computer program to determine all possible crashes that a system might face. Putting too much data or random inputs into a variable area causes a buffer overflow, a critical vulnerability, which is what Fuzzing looks out for as an inspection technique.
Not only is buffer overflow a serious vulnerability, but it is also often the go-to method for hackers when they are trying to break into a system.
The Fuzzing Process
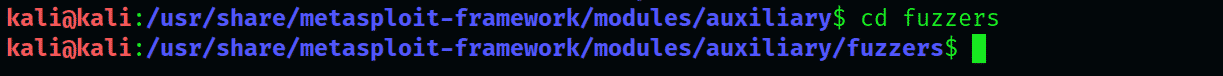
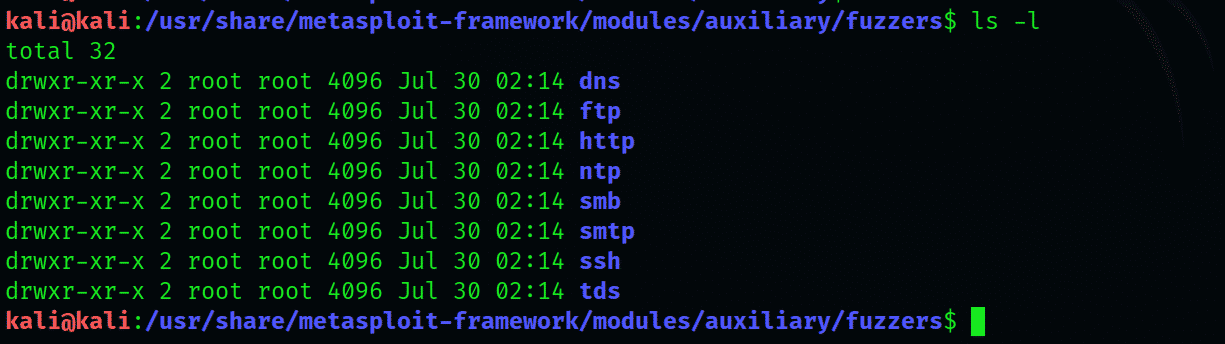
Go to the fuzzer directory and take a good look with the listing:
The types of fuzzers on display will include the following: dns, ftp, http, smb, smtp, ssh, and tds.
The fuzzer of particular interest to us here is ftp.
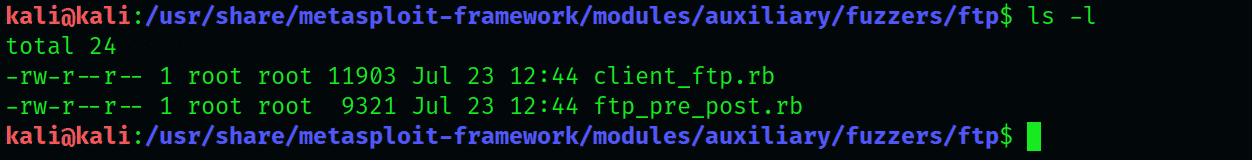
Next, open the fuzzers directory:
Out of the two types displayed here, we will use the “tp_pre_post fuzzer,” instead of “client_ft.rb.”
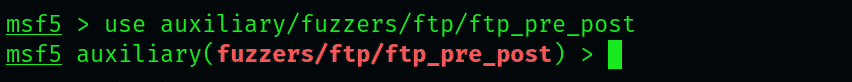
Open up the msfconsole, locate the “tp_pre_post fuzzer,” and run it. In the msf prompt, type the following:
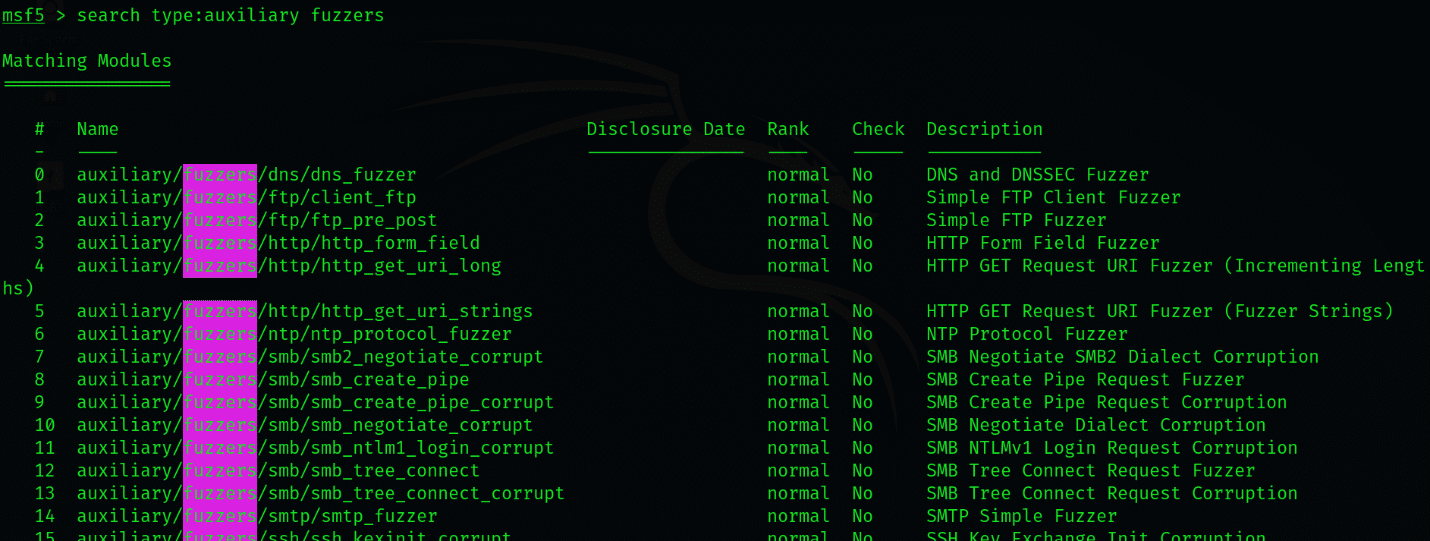
Msfconsole will list only those modules that are auxiliary and neglect other types. Notice that all the mods presented have the keyword ftp, requiring the process to sort out the modules as instructed by the command.
The search results show several different modules; we will only be using the “auxiliary/fuzzers/ftp/ftp_pre_post” module. You can look into the details regarding the functions this mod has by typing msf > info.
Now, load this module by typing:
As you can see, the module can take several different inputs. We will be using a specific IP address. In this example, we are using a system with Windows 2003 OS as the designated target to test out our fuzzer.
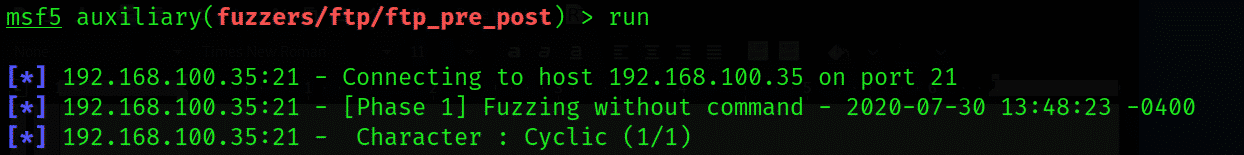
Set the IP address and run the module:
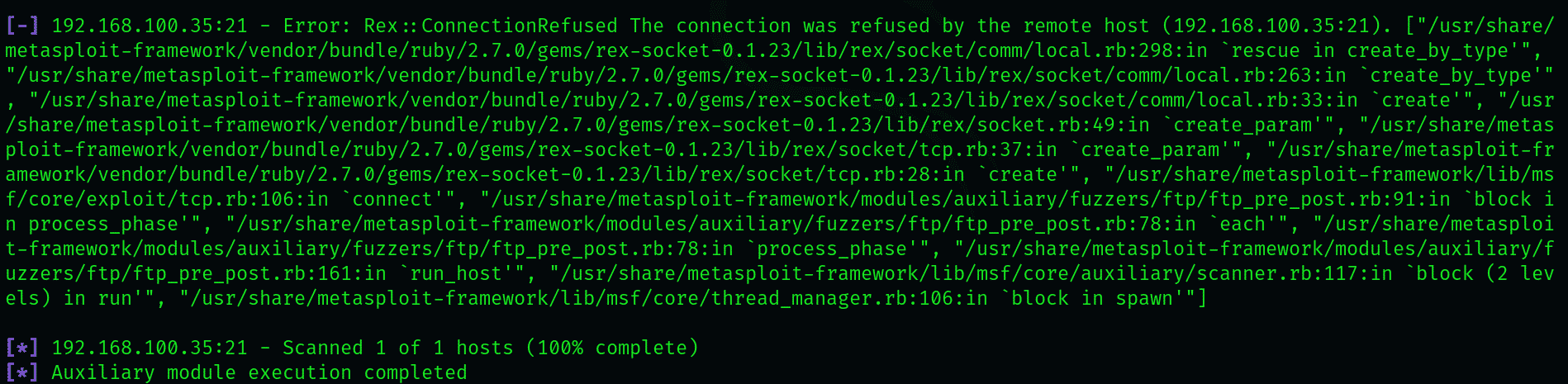
The fuzzer will begin with the light 10 bytes and slowly begin to overwhelm the system with more sizeable inputs, upsizing by 10 bytes with every iteration. The maximum size is 20000 bytes by default, which can be modified according to the system type.
This is a very convoluted and long process, so be patient. The fuzzer will stop at the specified size limit, or when it detects a few error messages.
Conclusion
This article described what fuzzers are: auxiliary modules that allow us to check a system for vulnerabilities, including the buffer overflow, which is the most significant as it is often overridden by its exploitation. The article also described how to perform fuzzing on a system with the tp_pre_post fuzzer. Despite being relatively simpler components of the Metasploit framework, fuzzers can be extremely valuable when it comes to pen-testing.
Obviously, this not the only thing that auxiliary modules are capable of; there are hundreds of different modules that serve a variety of different purposes for testing your system.