- Introduction
- How Caesar Cipher Works
- Encrypting a Message Using Caesar Cipher
- Decrypting a Message Using Caesar Cipher
- Cracking Caesar Cipher Using Brute Force Attack
- Conclusion
- Frequently Asked Questions (FAQs)
The Caesar cipher is one of the oldest encryption methods known. It derives its name from the Roman military general and statesman, Julius Caesar. He was thought to have employed it around 58 BC.

Alt-image & caption: Caesar Cipher Wheel – A Circular Metal Object with Letters on It
By employing this cipher, Caesar could encode messages in a manner that made them decipherable only to those privies to the particular shift value. This strategic approach aided him in safeguarding his military communications and obtaining an edge over potential adversaries who might intercept his messages.
How Caesar Cipher Works
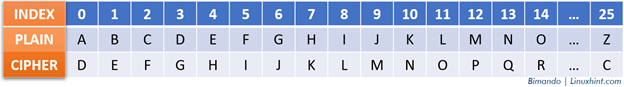
The Caesar cipher is a simple substitution cipher that involves shifting each letter of the plaintext’s fixed three number positions forward in the alphabet to generate the ciphertext. This specific shift value is referred to as the “key”. This cipher is categorized as a substitution cipher. To decrypt the message, the recipient must possess the identical key to reverse the procedure and unveil the original text.
Alt-image & caption: Caesar Cipher – Index Numbering Value Table
Encrypting a Message Using Caesar Cipher
To perform an encryption with the Caesar cipher, the following is a step-by-step guide for encrypting a message using the Caesar cipher:
- Generate Your Plaintext Message: Begin with the plaintext message that you want to encrypt. Ensure that it consists of letters from the English alphabet.
- Choose a Key: Determine the key which is typically set to 3 for a standard Caesar cipher. This key signifies how many positions each letter in the plaintext will be shifted.
- Encrypt the Message: For each letter in the plaintext message, perform the following steps:
- Identify the letter’s position (index number) in the alphabet.
- Add the key value to the letter’s position.
- Wrap around the alphabet if necessary. If the shifted position exceeds in “Z” loop back to the beginning of the alphabet.
- Replace the original letter (plaintext) with the one corresponding to the new position (ciphertext).
- Repeat for All Letters: Continue this process for every letter in the plaintext message, shifting each one according to the key value.
- Collect Ciphertext: As you complete the encryption for each letter, compile the resulting letters to form the ciphertext. Once you’ve processed all letters in the plaintext message, you will have the ciphertext which can be sent securely to the intended recipient.
Example:
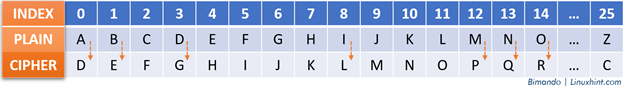
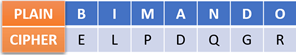
Let’s encrypt the word “BIMANDO” with a Caesar cipher key of 3 using the provided the table as a reference:
Alt-image & caption: Caesar Cipher Encrypt “Bimando”
Alt-image & caption: Caesar Cipher Encrypt “Bimando”
So, the “BIMANDO” plaintext becomes “ELPDQGR”.
Manually encrypting the messages that contains many paragraphs is certainly very tiring and raises the risk of calculation errors. Therefore, it would be better for us to create a program to automatically encrypt the Caesar cipher no matter how many messages there are. Read more about Caesar cipher encryption using Python in a step-by-step tutorial.
Decrypting a Message Using Caesar Cipher
Decrypting a Caesar cipher message involves reversing the encryption process. You need to know the key (shift value) that was used to encrypt the message. Here’s a step-by-step guide to decrypting a Caesar cipher.
Step 1: Obtain the Ciphertext and Key
First, you need the ciphertext which is the encrypted message and the key. Caesar cipher uses a fixed number of three forward positions. The person who encrypts the message or a secure channel should provide you with this information.
Step 2: Decrypt the Message
After obtaining both the ciphertext and the key, you can initiate the decryption process. The decryption method is straightforward. We simply reverse the order of the alphabet by shifting it three positions backward.
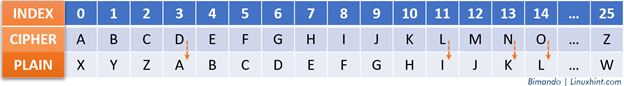
Example:
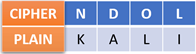
Let’s decrypt the “NDOL” ciphertext with a Caesar cipher key of 3. Use the following table as a guideline:
Alt-image & caption: Caesar Cipher Decrypt “Kali”
Alt-image & caption: Caesar Cipher Decrypt “Kali”
So, the “NDOL” ciphertext becomes “KALI”.
Manually decoding the messages that contain many paragraphs is certainly very tiring and raises the risk of calculation errors. Therefore, it would be better for us to create a program to automatically decrypt the Caesar cipher no matter how many messages there are. Read more about Decrypting the Caesar cipher using Python tutorial.
Cracking Caesar Cipher Using Bruteforce Attack
A brute force attack can be used to decrypt a Shift/Caesar cipher without knowing the key. It involves systematically trying all the possible key values (1 – 25) to decrypt the ciphertext until the correct key is found. Here’s how it works:
1. Generate Possible Keys
Start with a shift value of 1 and decrypt the ciphertext using this key. If the result doesn’t make sense (e.g., if it’s gibberish), move on to the next key and repeat the decryption process. Continue this cycle until you’ve tried all 25 possible keys (the Shift cipher has 25 possible keys because a shift of 0 or 26 would result in the same ciphertext as the original message).
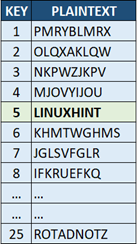
Example: Let’s say, we have a “QNSZCMNSY” ciphertext but we don’t know the key. How are we going to decrypt that? We decrypt it using each possible key from 1 to 25. =Here is what we got:
Alt-image & caption: Caesar Cipher – Bruteforce Attack
2. Evaluate the Results
After decrypting with each key, review the resulting plaintext. The correct key produces a coherent and meaningful message such as plain English text. Refer to the previous example, the key of 5 more likely makes sense, doesn’t it? So, the plaintext of the “QNSZCMNSY” Caesar ciphertext is “LINUXHINT” with the key of 5.
Instead of brute forcing Caesar Cipher manually, it would be more effective to use an automatic program as we explained in the article entitled Cracking Caesar Cipher Using Python.
Conclusion
Although Caesar cipher is no longer a practical choice for securing a sensitive information in today’s digital landscape due to susceptibility to brute force attacks and its limited key space, it remains an invaluable tool for educating individuals on the fundamental principles of encryption and decryption. The Caesar cipher serves as a testament to the evolution of encryption and its ongoing relevance in data security. As we explore more advanced encryption methods, we should acknowledge the essential role that this classic cipher has played in shaping cryptography and its continued impact on various aspects of our digital world.
Frequently Asked Questions (FAQs)
Q1: Is the Caesar cipher secure for modern use?
A1: No, the Caesar cipher is not considered secure for modern applications. It offers minimal security and is vulnerable to brute force attacks due to its limited key space. It’s mainly used for educational purposes and recreational activities.
Q2: How do we decrypt a message that is encrypted with the Caesar cipher?
A2: To decrypt a message, you need to know the key (shift value) that was used to encrypt it. You reverse the process by shifting each letter in the ciphertext backward by the same key value to reveal the original text.
Q3: What is a brute force attack against the Caesar cipher?
A3: A brute force attack is a method to decrypt a Caesar cipher without knowing the key. It involves systematically trying all possible key values (1 – 25) until the correct key is found. This attack is feasible due to the limited key space of the Caesar cipher.