By implementing Iptables classify, you can assign specific Download/Upload bandwidth to a specific type of packets, sources/destinations, ports, etc.
For example, by implementing Iptables classify, you can prioritize your bandwidth for zoom conferences, gaming, etc., while limiting bandwidth for social networks, Torrent, etc.
This Iptables feature isn’t related to security but to QoS (Quality of Service), which is the bandwidth performance impacting the user’s experience.
Iptables classify can be applied only with the POSTROUTING chain. If you don’t know what POSTROUTING is, probably you may want to read this Iptables tutorial before continuing with this article.
Why to use Iptables classify
By default, the internet traffic is organized according to FIFO’s general policy (first in, first out). FIFO means the first packet which arrives will be the first to be replied to, the second arriving packet will be the second to be replied to, and the oldest packet arriving will be the last to be replied to.
For example, if you receive fragmented packets belonging to video conferences, gaming, emails and social networks simultaneously, your system will reply according to arrival order.
This behaviour is fair and allows the internet to work properly, but FIFO may be a regular problem at an internal level, and you can regulate it using Iptables. You can define, for example, that video conference or gaming traffic will enjoy priority over mails or P2P traffic.
FIFO is an example of a basic qdisc (queueing discipline). You can think about Qdisc as a policy implementer attached to a network device, defining the order in which packets will pass to the network device. Our commands in this tutorial will start by modifying the Queueing Discipline (Qsic).
QoS (Quality of Service) can be managed from the kernel using the tc (Traffic Control or Advanced Queuing) utility, but this feature is stateless while Iptables can provide complex stateful features. In any case, Iptables classify needs to be implemented with tc and qdisc, the functionality allowing you to distribute or limit bandwidth according to your own criteria.
How to use Iptables classify
Before starting with Iptables classify, we need to create the levels or traffic types to classify for Iptables.
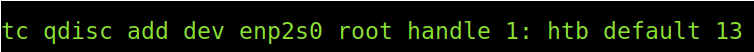
With the command below, we will modify the Queueing Discipline for the network device named enp2s0. This is applied for outbound traffic (root), but since your prioritized traffic replies first, they will get replied and downloaded first. By delaying certain outgoing traffic, it will download slower because it will arrive late to the destination.
The command above explained:
- tc qdisc: We run tc to modify the Queueing Discipline (Qdisc).
- add dev <NetworkDevice>: Here, we attach the Qdisc to a specific network device; in this case, my network card is enp2s0.
- Root: Outbound traffic.
- handle 1: The format of this section could be “handle 1:13” where the minor (1) is the class, and 13 is the handle. This creates class 1 and level 13 for us to divide the bandwidth in the following step.
- htb: htb (Hierarchical Token Bucket) is used to control outcoming bandwidth by simulating different slower links instead of your real and fast physical link. With this option, we tell the system we will divide our physical link between several simulated links. Then we will define the division parameters with Iptables.
- default 13: As said previously, the handle could be defined as “handle 1:13”, we didn’t because we established it at the end of the command the level 13 as default.
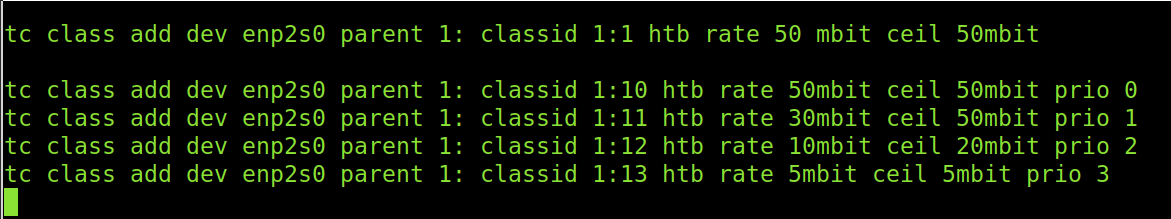
The lines below add the class, levels and define the bandwidth allocation for each.
As you can see, those packets we’ll flag as 1:10 with Iptables will enjoy 50 over 50 mbit bandwidth available.
Packets classified as 1:11 will have up to 30 mbits, but if there is no competing traffic and the bandwidth is free, they can escalate to up to 50 mbits speed.
1:12 packets can use up to 10mbit when the traffic is being used, but if there is no other traffic, its speed can increase up to 20mbits.
Finally, packets classified as 1:13 will always have up to 5mbit, independent of whether additional traffic needs the bandwidth.
tc class add dev enp2s0 parent 1: classid 1:10 htb rate 50mbit ceil 50mbit prio 0
tc class add dev enp2s0 parent 1: classid 1:11 htb rate 30mbit ceil 50mbit prio 1
tc class add dev enp2s0 parent 1: classid 1:12 htb rate 10mbit ceil 20mbit prio 2
tc class add dev enp2s0 parent 1: classid 1:13 htb rate 5mbit ceil 5mbit prio 3
So we defined some levels, and now we need to enforce them using Iptables. The lines above should be saved as script and executed before running your Iptables rules.
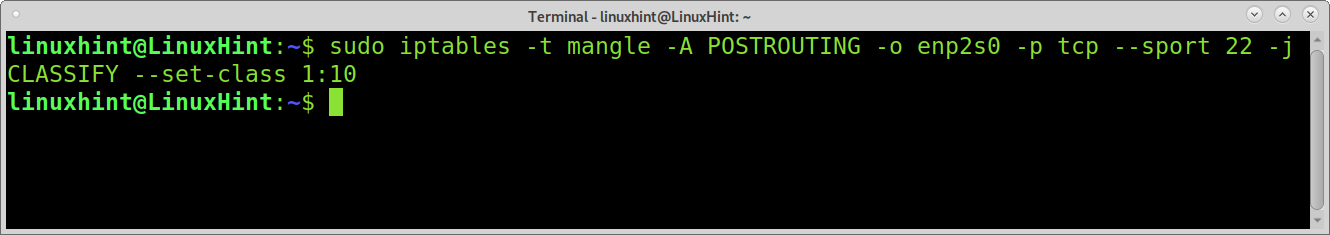
In the first example, I will use Iptables to prioritize ssh connections and scp file transferences by classifying port 22 as 1:10. This means ssh or scp connections will enjoy the maximum speed as defined previously (50/50).
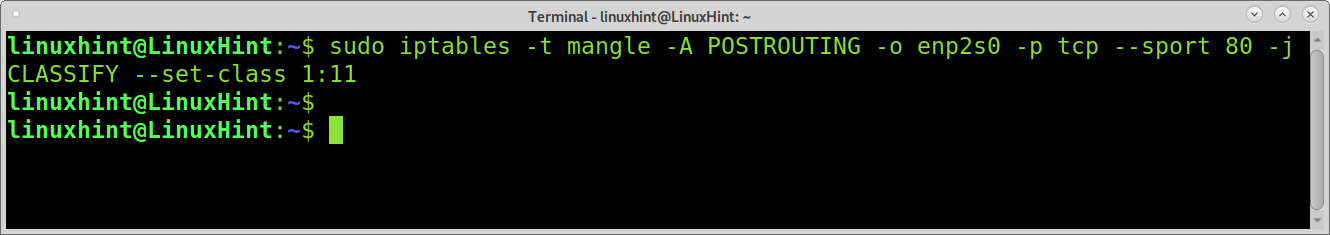
Now let’s say when you are transferring large scp files, you don’t want web traffic to compete for the 50mb bandwidth; you define, when there is scp traffic, the http traffic has less priority, with a maximum of 30mb. It can reach 50 mb only if there is no other competing traffic. The following line does that by classifying http packets as 1:11.
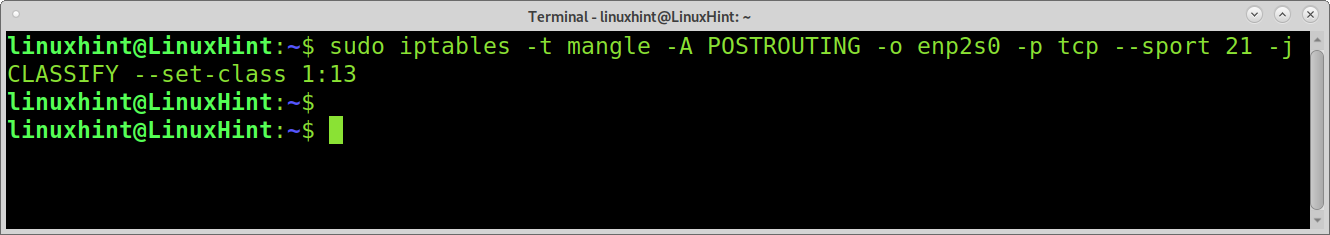
And now, for the following example, let’s assume for some reason you only want to allow up to 5mb for ftp traffic, independently if there is additional traffic, the Iptables rule must be:
There is a Netfilter extension for layer7, which you can download and add to your kernel. L7 allows classifying layer 7 traffic, meaning you can classify traffic by applications.
You can download L7 from https://sourceforge.net/projects/l7-filter/files/.
For example, the command to limit torrent traffic using L7 is the following.
As you can see, Iptables classification is a great feature that can improve your quality of life if you have limited resources or exclusive bandwidth demand.
Conclusion:
Iptables classify is an excellent method to increase your network performance. It is excellent for companies and home use. Domestic users can prioritize their Smart TVs or game consoles over computers or vice versa. It seems especially useful for networks allowing guests or in the office to prevent unwanted behaviour. At the technical level, classifying Iptables syntax is pretty simple.
I hope this tutorial explaining how to use Iptables classify was useful. Keep following us for additional Linux tutorials and tips.