Due to the comfort and control that SSH gives us, we try to implement methods such as Password-less logins using SSH keys and two-factor authentications. However, despite this, we can still encounter errors that might prevent us from using SSH to log in to remote machines.
This quick tutorial will show you how to solve bad ownership or permission on the .ssh/config file.
Pre-Requisites
Before we get started on the guide:
- Ensure you have a private and public key
- Ensure your public key is available in the authorized_keys file of your remote machine.
If you do not have either of the requirements above met, consider the following tutorial where I detail how to generate and copy SSH key-pairs.
https://linuxhint.com/use-ssh-copy-id-command/
What Causes Bad Owners or Permission Errors?
The bad owner or permission error on the .ssh/config file results from incorrect permissions either on the file itself or the .ssh directory.
The files in the .ssh directory should have the read and write permission of the user only; that does not include the group or others.
How to Fix Bad Owner and Permission Errors
To solve this error, all we need to do is set the correct permissions on the .ssh/config file.
If you are not that comfortable with Linux permissions, check out this intuitive tool for using chmod.
To set the correct permissions, use the command:
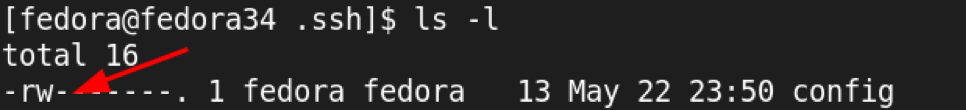
Once you execute the above command, the file permission should be as follows:
You can also use the chown command to upvote the owner of the file using the command:
Using these two methods, you should have the bad owner or permission error fixed, and you can proceed to log in to your SSH.
Conclusion
That was a short and quick guide on resolving .ssh/config bad owner or permission error. If you are looking for a more in-depth tutorial, check out the following SSH troubleshooting guide.