The three protocols are complementary, and together they offer confidence in email origin and email content integrity.
Applying DKIM, SPF, and DMARC ensures the sender of the legitimate email reaches the receiver’s inbox and assures the receiver the email was sent by a legitimate sender and the content wasn’t modified. This practice is essential for anyone sending emails from his own domain name.
This article explains what SPF, DKIM, and DMARC are and how they work.
SPF (Sender Policy Framework)
SPF is an authentication framework that links an SMTP server to a domain name. SPF communicates to the mail client that the sender mail address (The sender SMTP) is authorized to use the domain name.
SPF defines authorized servers allowed to use a domain name.
SPF can also be used to define that no emails are sent from a specific domain name.
If you create a new domain name without mail accounts associated with it, you can specify it in your DNS records to deauthorize all senders.
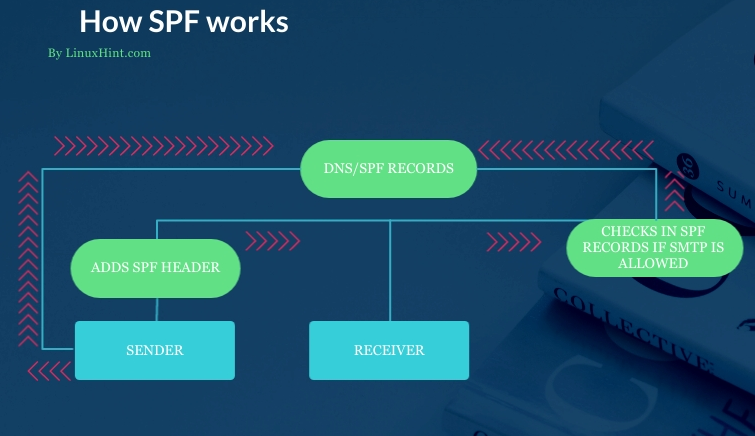
How SPF works
SPF is applied by adding a TXT record in the DNS configuration. It allows the SMTP protocol to confirm if sender SMTP servers are authorized to send mails using a specific domain. There must be only a unique SPF configured in the DNS records.
SPF works by doing a reverse MX or DNS lookup process. Usually, DNS is used to translate an IP address into a domain name. On the contrary, SPF checks DNS records to translate the domain name to allowed IP addresses within the MX records. Then, SPF compares allowed IP addresses in DNS records with the sender SMTP IP address. If the addresses match, the mail is approved; if the sender’s IP address isn’t in the records, the mail is refused, and the incident is reported to the actual mail address owner.
The following flowchart describes the sender (a legitimate sender) adds SPF in his DNS records. When he sends an email with SPF protocol included in the header, the receiver checks the last SMTP hop IP address and contrasts it with the list of allowed servers defined in the DNS records.
DKIM (DomainKeys Identified Mail)
DKIM is another mail authentication method that should be implemented together with SPF. At the same time, SPF checks if the last SMTP hop IP address is allowed to send mail on behalf of a specific domain name, DKIM checks if mail content is legitimate.
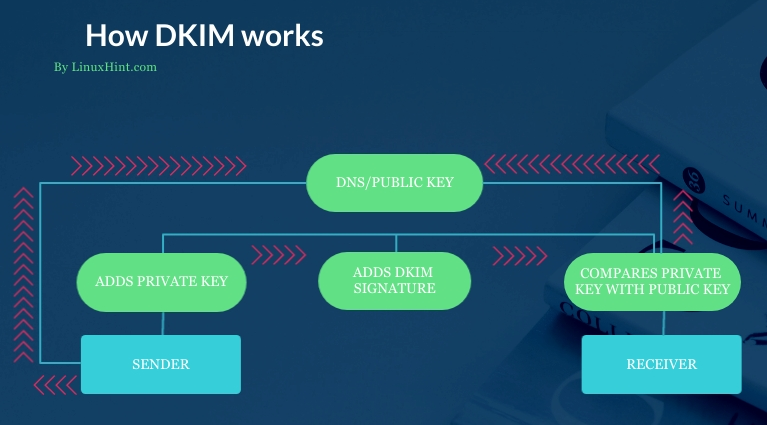
How DKIM works:
DKIM works differently but also requires DNS updates to be applied. Contrary to SPF, you can have multiple DKIM records in your DNS.
DKIM is based on key authentication to verify sender and message content legitimacy. When using DKIM, the sender attaches a signature containing a private key and information for the receiver to find the public key in the DNS records.
While SPF checks DNS records to resolve SMTP IP addresses, DKIM checks DNS looking for public keys to contrast with the signature attached to the mail body and mail header.
DKIM can detect if a sender was forged and if the message was modified on its way to the receiver.
The DKIM process is described in the following flowchart.
DMARC (Domain-based Message Authentication, Reporting, and Conformance):
DMARC is another method to deal with mail spoofing, spam, and phishing, and it also requires DNS records addition. But DMARC is more an informative protocol than an authentication protocol (it is an authentication protocol but fulfills informative tasks).
DMARC doesn’t check if the sender and content are legitimate; it collects that information from DKIM and SPF. DMARC supervises DKIM or SPF, or both of them.
DMARC also defines a public policy for mail addresses belonging to a specific domain name. That policy is published in DNS records, just like DKIM and SPF.
DMARC has 3 functions:
- Validate DKIM and SPF.
- Defines and publishes a policy for emails associated with a domain name.
- Reports incidents to the domain owner.
There are 3 types of DMARC policies:
- p=none: Allows all incoming mails to pass.
- p=quarantine: Sends unqualified emails to the spam folder.
- p=reject: Rejects unqualified emails. E-mails can’t reach the designatory inbox, spam folder, etc.
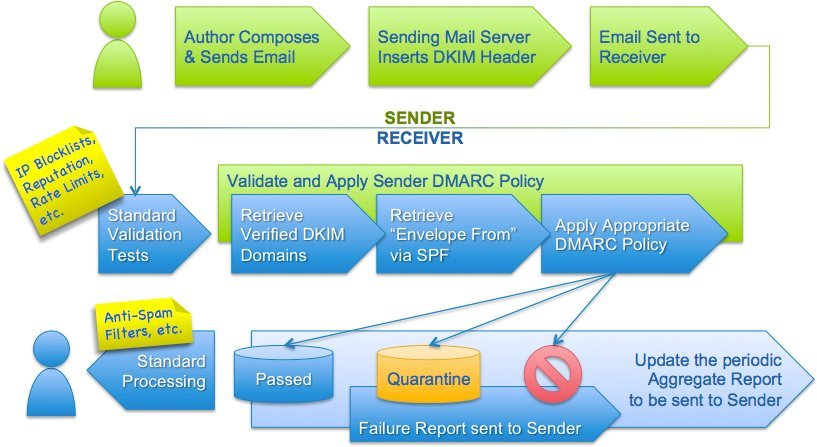
How DMARC works
DMARC is also applied by publishing a new DNS record. This DMARC record contains information on the policy to be used.
When a sender sends an email with a DKIM signature or SPF header (or both), DMARC validates or invalidates it first. Then it informs the receiver about the validation success or failure and the defined policy for that specific domain name. The receiver’s mail client checks the policy in the DNS and determines how to use the information provided by DMARC to handle the email. Then the receiver reports to the sender about the received email associated with that domain name.
The flowchart below taken from DMARC.org shows the whole process:
Conclusion:
DMARC, DKIM, and SPF must be combined to maximize anti-mail forging, phishing, and anti-spam results. For example, if an attacker receives a legitimate email and finds how to forward it exploiting the original DKIM signature, the SPF record may prevent the attack from succeeding.
Each of those protocols is an extension of the other, and applying them is an essential and critical measure against spam and social engineering attacks. The process to use DMARC, DKIM and SPF is pretty straightforward and consists of DNS records addition.
I hope this article was helpful. Keep following Linux Hint for more Linux tips and tutorials.