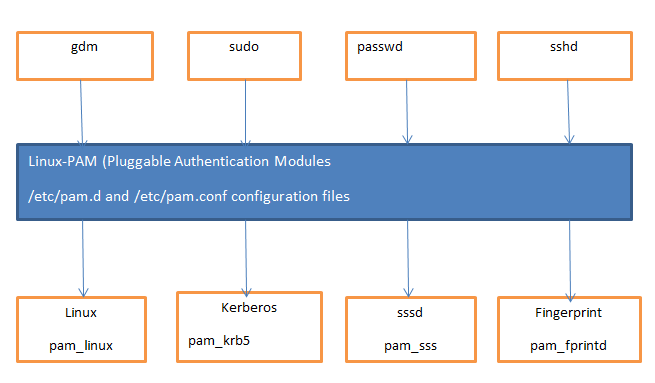
By using PAM, these programs can determine if a user is who they claim to be. With PAM, users can gain access by providing usernames and passwords stored in virtual protocols such as Kerberos or LDAP. Users can also provide certificates, tokens, or biometrics for authentication.
And unlike typical authentication protocols, PAM, or Pluggable Authentication Modules, is an Application Programming Interface (API). Thus, rather than rewriting codes for each program or application to ensure PAM compatibility, PAM modifies the source codes conveniently.
The diagram below details some of the programs you can integrate with PAM and the methods used.”
Linux PAM Tutorial
Ideally, PAM provides a unified login system for Linux programs and applications. But to use PAM correctly, this tutorial will come in handy.
1. Check the Linux Systems That are Compatible With PAM
Using PAM begins with checking if the program you intend to use is PAM-aware or not. And you can check that using this command;
Alternatively, you can use the below command to list the Linux programs or services that use PAM. The command allows you to check the content of the directory.
A listing using the above command will always produce a result similar to what is in the figure below;
Opening any service file will show you that each file has three columns. The first column signifies the management group, the middle column represents the control flags, and the third one is the module used for each category.
In the above figure, the “account” represents the management group, “required” is the control flag, while the “pam_nologin.so” is the module used. A fourth column may occasionally exist, and that will represent the module parameters.
2. Create or Edit PAM Configuration Files for PAM-ified Services or Programs
As a Linux server or system administrator, you can list all the PAM modules appropriate for implementing the access policy for any program. The list is known as a stack. You will need to invoke each module as listed in the stack of the configuration file for a particular program. Of course, this should happen before authenticating any user.
You can change the configuration file set up for a program in case a given module fails. This modification will allow you to implement more complex policies such as authenticating with LDAP first or trying local files in case that fails.
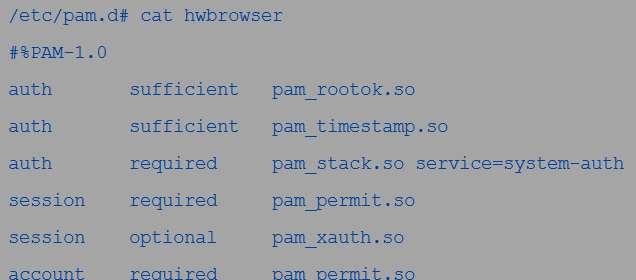
For example, hwbrowser is written to use Linux PAM for authenticating users. The /etc/pam.d controls the same set of modules in the configuration files. You can edit the program’s configuration file to allow you to enforce the desired access policies.
This is the default look of the program’s configuration file before editing;
As is evident above, the file contains a listing of the DLLs for use, with some containing additional details.
3. Using PAM to Restrict root Access or Admission to SSH
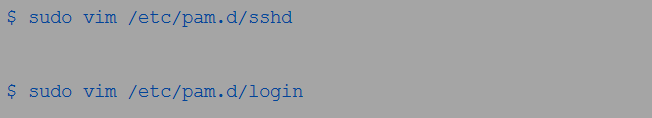
Notably, PAM also comes in handy in disabling root user access to programs or systems via SSH and other login programs. You can achieve this by restricting access to sshd and login services.
The /lib/security/pam_listfile.so is your preferred module as it offers immense flexibility in limiting the capabilities and privileges of certain accounts. Open and edit the target files in the /etc/pam.d/ using any of the below commands;
OR
Whichever the case, add the below outcome to both files;
4. Stacking Using Linux PAM
Finally, we would not want to end a PAM tutorial without discussing stacking, as PAM supports. This concept allows a particular service or program to use multiple mechanisms. You can create a stack in the configuration file by creating several entries for the target program with a similar module_type file.
You can invoke the modules in the order in which they appear in the stack. The control_flag field specifies the final result.
Notably, PAM control_flags have the following behavior;
- required- These modules must pass to produce a successful result. Other required modules in the stack will be tried out even when one or more in the category fails. However, the error from the first failed module will affect the result.
- requisite- This is similar to the required module. But in the case of failure of one requisite module, the system will attempt no other requisite modules in the stack for processing.
- sufficient- If all the previous required modules pass successfully and a sufficient module passes, the other modules will not be due for processing. The system will ignore the remaining modules and return a successful result.
- optional- An optional module must succeed in case there are no required modules in the stack and none of the sufficient modules have passed. But if there is another successful module in the stack, the system will ignore any failed optional module.
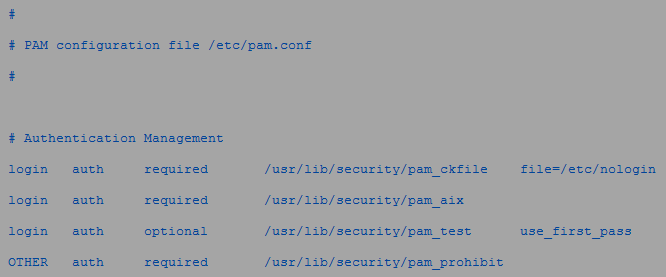
This /etc/pam.conf is an example of typical stacking in PAM for the login program in the auth_module type.
Conclusion
PAM is a robust API that allows services and programs on Linux systems to authenticate users. While it remains vital for authenticating users in a Linux environment, understanding and using Linux PAM can be a nightmare for novice techs. This tutorial aimed to make the entire process easier. Hopefully, it has achieved its objective.
Sources: