This post will discuss what Linux sysctl is in Kubernetes and how it can be used within a cluster of Kubernetes. The sysctl is an interface in the Linux operating system which enables the administrator to modify the parameters of the kernel at runtime. Here, we will demonstrate how to use the Linux sysctls in the Kubernetes platform. We will demonstrate a simple example to help you understand what kind of output you can expect while implementing the kubectl commands for using the sysctls in Kubernetes.
What are sysctls?
The sysctls is an interface in Linux which is used to adjust kernel parameters at runtime for the namespace in a container. These parameters can be found in the /proc/sys/ virtual process file and they cover various subsystems like virtual memory, networking, kernel, etc. Only namespaced sysctls can be set independently on pods and Kubernetes exposes the sysctl settings. The node level sysctls which are not namespaced need to be set with other method of sysctls setting like node tuning operator. Moreover, only safe sysctls are whitelisted by default while the unsafe sysctls need to be manually enabled on the node so that they can be available to the user. Now, let us understand how to use Linux sysctls in Kubernetes.
Prerequisites
Before you begin to learn how to use the Linux sysctls in Kubernetes, make sure you have the following tools installed in your system:
-
- Kubernetes version 1.23 or any other latest version
- Ubuntu 20.04 or any other latest version
- Sysctls for pod support
- Kubectl command line tool
- Minikube cluster
Assuming that your system is meeting the prerequisite needs, we are moving to the implementation section.
How to Use the Linux sysctls in Kubernetes?
Linux operating system is a platform that allows you to tune the kernels via sysctls knobs in the network stack. Some of the sysctls are namespaced for a pod with its own configuration while others are valid for the entire system. Kubernetes have grouped the sysctls interface into two categories:
-
- Namespaced vs node-level sysctls
- Safe vs unsafe sysctls
Namespaced vs node-level sysctls:
In the Linux kernel, most of the sysctls are namespaced which enables you to set them independently between various pods on one node. The namespaced sysctls are easily accessible in a Kubernetes pod. Some of the namespaced sysctls are as follows:
-
- fs.mqueue.*
- kernel .msg*
- kernel.shm*
- kernel.sem
The node level sysctls are not namespaced and the cluster administrator needs to set them manually. The cluster administrator either uses a demon set with a privileged container or can modify the /etc/sysctls.conf node’s Linux distribution. The Node Tuning Operator can also be used to set the node level sysctls.
Safe vs unsafe sysctls:
There are two groups of sysctls: safe and unsafe. The safe sysctls are properly namespaced and they are entirely isolated within the pods on the same node. The safe sysctls are enabled by default and can be used in a pod by modifying the pod specification. However, the unsafe sysctls are disabled by default and they need to be manually enabled by the cluster administrator. The safe sysctls do not influence their neighbors since they are properly namespaced. While the unsafe sysctls can unexpectedly impact their neighbors like overloading a system. The safe set of sysctls is as follows:
-
- net.ipv4.ping_group_range
- net.ipv4.ip_local_port_range
- kernel.shm_rmid_forced
- net.ipv4.tcp_syncookies
The point here to be noted is that just being namespaced alone is not enough for the sysctl to be assumed safe.
Now that we have understood both the categories of sysctls, let us move on to learn how to use these sysctls in Kubernetes. Here, we will guide you on how to use both safe and unsafe sysctls and how to manually enable unsafe sysctls in Kubernetes.
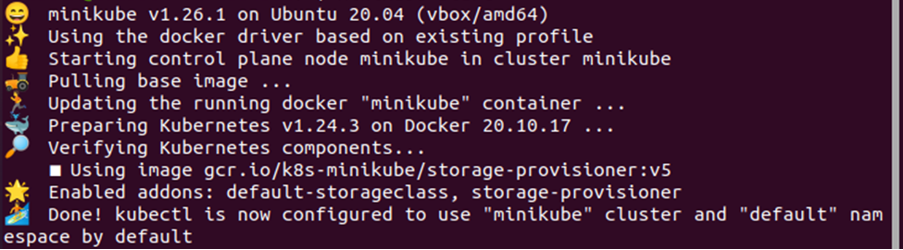
Step # 1: Start the Minikube Cluster
The Kubernetes platform can be used via some clusters and we are using the minikube cluster here. To start the minikube cluster, you can use the command given below:
This will start the minikube cluster where you can run the kubectl commands and use the Linux sysctls in the Kubernetes platform. When you execute this command, you will get a similar output to the one given below:
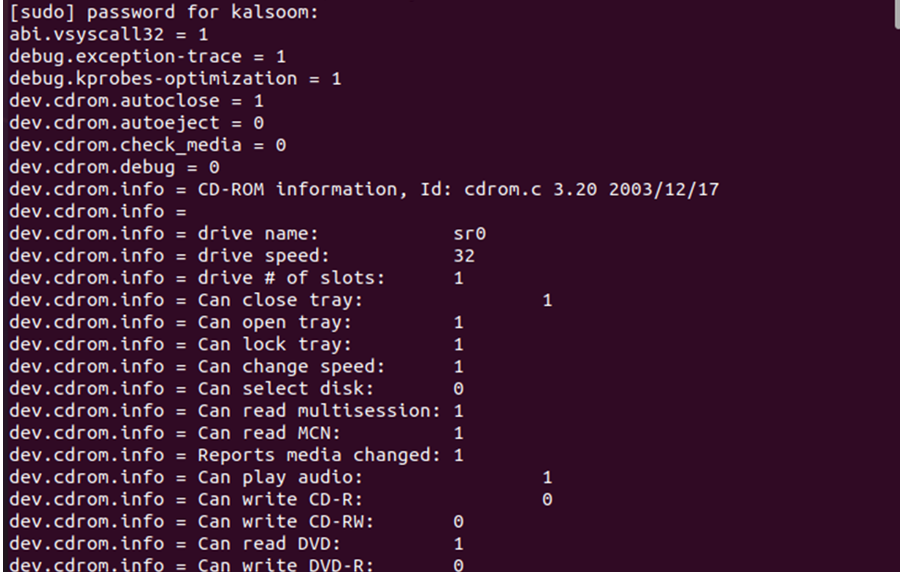
Step # 2: Check the Parameters of sysctls
The sysctls interface is used to modify the kernel parameters which are found in the /proc/sys/ virtual process file. To list all the parameters, the command given below can be used:
This command will list all the kernel parameters from the /proc/sys/ virtual process file. See the sample output given in the snapshot below:
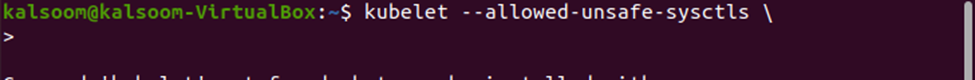
Step # 3: Enable Unsafe sysctls
The unsafe sysctls need to be enabled manually because they are disabled by default. The cluster admin manually enables the unsafe sysctls on a per-node basis. The pods which have disabled unsafe sysctls cannot be launched but only scheduled. There are some specific conditions (like run time application tuning, high performance, etc.) when the cluster admin can allow the unsafe sysctls. To enable the unsafe sysctls on a node-by-node basis, you can use the kubectl command given below:
This is a very basic and simple way to enable unsafe sysctls by using the kubectl command.
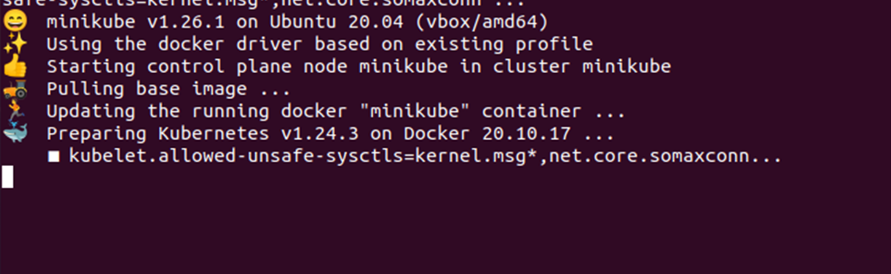
Moreover, unsafe sysctls can be enabled by using the minikube extra-config flag. This can be done using the command given below:
This command allows you to enable the unsafe sysctls via the minikube cluster. However, it can only enable the namespaced sysctls. See the sample output given in the snapshot below:
Conclusion
This article provided us with an overview of the Linux sysctls interface. We discussed what a Linux sysctl is and how it can be used in the Kubernetes environment. There are two groups of sysctls: is safe and unsafe. The safe group of sysctls is enabled by default, while the unsafe sysctls group is disabled by default. With the help of a simple and easy example, we learned how to enable the unsafe sysctls using the kubectl command and minikube –extra-config flag.