Prerequisites:
For running the commands in Kubernetes, we need to install Ubuntu 20.04. Here, we utilize the Linux operating system to execute the kubectl commands. Now, we install the Minikube cluster to run Kubernetes in Linux. Minikube offers an extremely smooth understanding as it provides an efficient mode to test the commands and applications. In this article, we are going to discuss the kubectl ignore certificate.
Methods to Ignore Certificate:
To Kubectl ignore certificate, we have to start the Minikube:
Start Minikube:
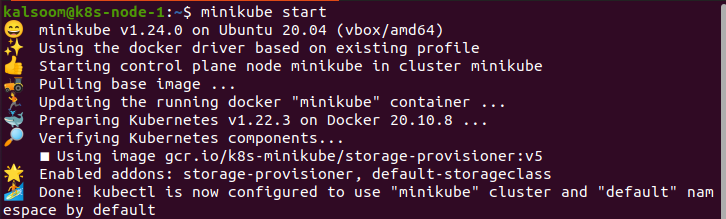
After installing the Minikube cluster, we need to start Ubuntu 20.04. First, we have to open a terminal for running the commands. For this purpose, we press “Ctrl+Alt+T” altogether on the keyboard.
In the terminal, we write the command “start minikube”, and after this, we wait unitl it effectively has started. The output of this command is provided below:
This process is time-consuming, and we will wait to execute the procedure efficiently.
TLS Certificates:
This article explains HTTP tier TLS certificates. The transport layer TLS certificate utilizes the interior statement amongst the nodes accomplished by ECK, and these are not to be modified. However, we can define our certification ability for the transport level.
Install OpenSSL:
The first step is to install OpenSSL. OpenSSL tool is usually preinstalled on the Linux operating system.
Create a Self-signed Certificate:
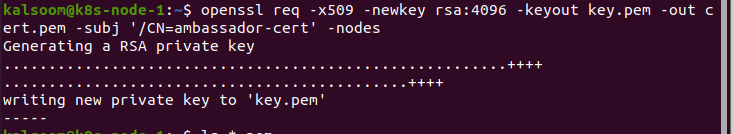
OpenSSL is a tool that is used for creating self-signed certificates and introducing TLS encrypted influences. The following OpenSSL command makes a certificate and secluded key pair that can be used to terminate TLS. Here, we make a secluded key and certificate. We utilize the succeeding command to check the legitimacy of the certificate:
The command mentioned above uses the Common Name “Ambassador” to make a certificate and secluded key. Then, the certificate is self-signed, and it is utilized for testing purposes only, so any other requested data may be blank:
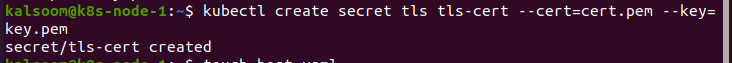
We dynamically load the TLS certification by interpreting the certificate as of the Kubernetes secret. Utilize the kubectl to make a TLS secret containing the pem file formed above:
Tell Ambassador Edge Stack to Use This Secret for TLS Termination:
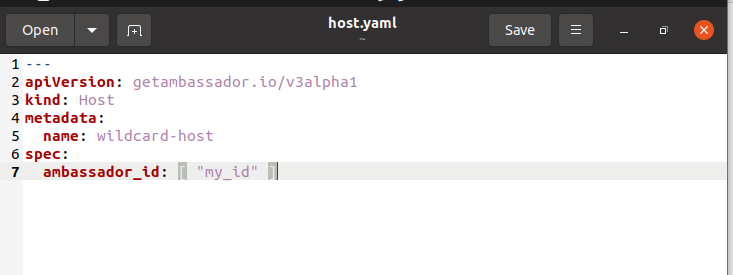
Now, the certificate and secluded key are stored in a Kubernetes secret called tls-cert. We have to utilize that certificate to terminate TLS for the domain. The host is utilized to update the certificate used to terminate TLS in the domain. Plus, it builds the subsequent host to use the secret made above to stop TLS on all areas:
If the cluster is executing numerous instances, be sure to involve the ambassador_id in the specification:
By running this command, we get the information apiVersion, kind, metadata, name, spec, and ambassador_id.
We apply the host constructed with kubectl. In this step, we are using “kubectl create –f host.yaml” command:
We organized to monitor TLS traffic on harbor 8443, and then, terminate TLS with the help of the self-signed certificate we formed.
Get Service Ambassador:
Now, we want to direct the encoded traffic terminated over HTTPS. First, we are assured the amenity on 443 and advancing on port 8443. We check this with the help of the “kubectl get service ambassador –o yaml” command:
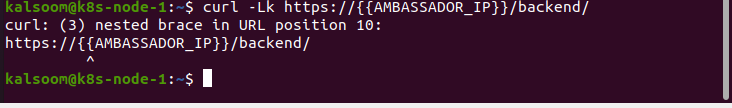
When the output from the kubectl command does not look like the example mentioned above, direct the Ambassador Edge Stack amenity to improve the HTTPS port. Subsequently validating that the Ambassador Edge Stack is attending port 443, use curl to direct demand the backend amenity.
Meanwhile, we utilize the self-signed certificate. We need to fix the k flag to turn off the hostname authentication.
Conclusion:
In this article, we obtain an effective certificate from a relevant certificate authority. Self-signed certificates are an easy and rapid method to acquire the Ambassador Edge Stack to dismiss TLS, but they cannot be utilized in the manufacturing systems. To assist HTTPS traffic deprived of security precautions, we want a certificate by an approved certificate authority. Through the Ambassador Edge Stack, we may do this merely by demanding a certificate through the built-in maintenance. For the API Gateway, we offer an easy method to acquire certificates. We discussed in this article how to get the information about ignored certificates. The Ambassador Edge Stack provides a configuration of numerous innovative selections related to TLS termination, origin, user certificate authentication, and SNI support. We hope you found this article helpful. Check out Linux Hint for more tips and information.