Kubernetes uses a service account to deliver the ID of the pod. Pods that interrelate through the API server are validated by a specific service account. By evasion, the application validates as the default service account in the namespace in which the application is running.
Kubernetes has two categories of accounts:
- The user account is used to provide humans with access to the specified Kubernetes cluster. For this, each user must be considered legitimate by the API server. The user account may be an administrator or designer demanding to get the resources at the cluster level.
- The service account is used to validate machine-level procedures to get the Kubernetes clusters. The API server is liable for these validations for the procedures executing in the pod.
Kubernetes service accounts let us assign pods an ID that we can utilize. Next, it validates the pod to the API server so that the pod can read and interact with the API objects. Then, utilize the workload. This agrees to provide the pod with a detailed ID and approval to attain the Google Cloud APIs.
In a Kubernetes cluster, any procedure in a container inside a pod can attain the cluster by validating from an API server using a service account. The service account offers the ID of the procedure running in the pod and distinguishes the service accounts by namespace conferring to the management boundaries of the cluster. This allows us to limit who might be able to work with specific service accounts. This turns out to be appreciated as the association grows. Remember to utilize the volume prediction for service account indications. This shortens the credential life of the service account and moderates the influence of credential leakage.
In this article, let’s discuss how kubectl gets service accounts.
Prerequisites:
First, we have to check our operating system. We have to utilize the Ubuntu 20.04 operating system in this situation. On the other hand, we also see Linux distributions, depending on our requests. Furthermore, ensure the Minikube cluster is an important constituent for running Kubernetes services. To implement the instances smoothly, we have a Minikube cluster installed on the laptop.
Now, we elaborate on the process of getting kubectl service accounts.
Start Minikube:
In starting the Minikube cluster, we need to open a terminal on Ubuntu 20.04. We may open the terminal by these two methods:
- Search for “Terminal” in the search bar of application of Ubuntu 20.04
- Use the key combination “Ctrl + Alt + T”.
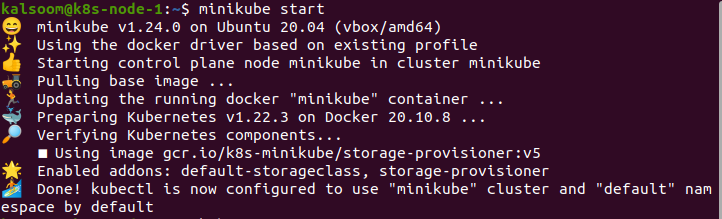
We can efficiently open the terminal by selecting one of these techniques. Now, we have to launch the Minikube. To do this, we run the following command:
There is no need to exit the terminal till Minikube starts. We may also upgrade the Minikube cluster.
Get the Service Accounts:
When pods are formed in a Kubernetes cluster using a specific namespace, by default, those pods will construct a service account termed as default. This account inevitably constructs a service token through the defined secret object. Therefore, applications can use this service account provided by the pod to attain API servers in an identical namespace.
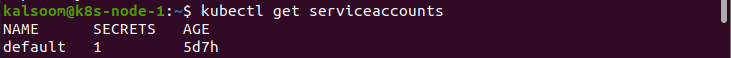
We can list all the service account resources in the namespace. Enter the following command:
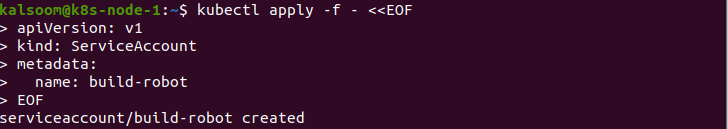
This is the output we get after running the “kubectl get serviceaccounts” command. We create additional ServiceAccount items by running the following command:
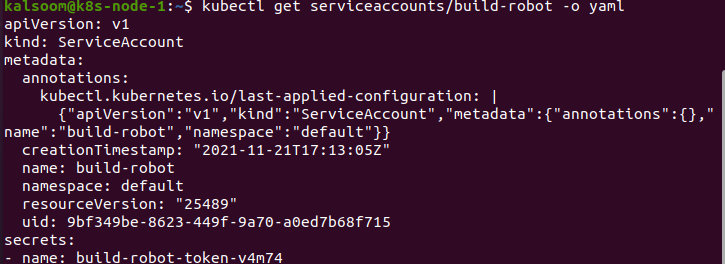
The title of a ServiceAccount item should be an effective DNS subdomain label. If we acquire a detailed dump of the service account item, we have to execute the following command:
We notice that the token is inevitably generated and specified by the service account. We can utilize the validation plugin to fix the authorizations on the service account. To utilize a non-standard service account, establish the pod’s field to the title of the service account we want to utilize. The service account must occur when the pod is generated. We do not upgrade the service account of the formed pod.
Delete the Service Account:
Now, we may delete the service account as follows:
If the pod couldn’t contain a Service Account series, the Service Account will be assigned to the default value.
Conclusion:
In this article, we have discussed how service accounts work in a cluster configured according to the references of the Kubernetes. The cluster administrator can adjust the compartment within the cluster. When we get the cluster, it is validated by the API server through a specific user account. At present, this is generally administrative if the cluster administrator modified the cluster. Procedures in the pods’ containers may be associated with the API server. Once we ensure this, they will be legitimate as a specific service account. We hope you found this article helpful. Check out Linux Hint for more tips and information on kubectl.