Such Kubernetes object is a Secret, which contains limited data and allows it to be used without even being revealed. Secrets can be created by Kubernetes users, and Secrets are created and used by the system itself.
Secrets are mentioned in a file that is attached to the pod via a volume. As a result, Secrets are included in Kubernetes. When the kubelet wants to extract a picture from an Image Registry that needs authorization, it uses Secrets.
Secrets are also used internally by Kubernetes to allow Pods to connect and interact with the API server component. API tokens are managed automatically by the system using Secrets connected to the Pods. A secret is a small piece of confidential data, such as a password, code, or key.
Alternatively, such information might be included in a Pod specification or a picture. Secrets can be created by users, and the system will also generate certain Secrets. Using Secrets allows you to define a Pod Life cycle with more flexibility and efficiency over how sensitive information is used. It lowers the chance of data being exposed to unauthorized users.
Secrets can be built using both the command line or configuration files. You could either refer to existing files (or have their content kept) or type the text straight into the command line while building Secrets. When inputting text directly, any special characters should be avoided. In this article, the creation of secrets in Kubernetes will be discussed.
Pre-requisites
To create a secret in Kubernetes, you have to install and configure Ubuntu 20.04. Also, install the latest version of minikube cluster on your system. Without the presence of a minikube cluster, you would not be able to run any of the services of Kubernetes on the Ubuntu system.
Method to Create a Secret in Kubernetes
To create a secret in Kubernetes, you have to log in to the Ubuntu system via root user. After that make sure to open the command line terminal by searching it in the application area or by running the shortcut key of “Ctrl+Alt+T”. Now you are ready to perform all steps mentioned below.
Step 1: Start minikube
To run any of the services of Kubernetes on the Ubuntu system, you have to start the minikube cluster. So, let’s begin with the execution of the below-listed command to get started with minikube.
The output will show up the installed version of minikube in your system. This might take some time so you are requested to never quit the terminal.
Step 2: Using the Command Line to Create Kubernetes Secrets
Now is the time to create a secret using the command line, so execute the following appended command in the shell.
From the output, you can view that the secret has been successfully created.
Step 3: Display Summary of Kubernetes Secrets
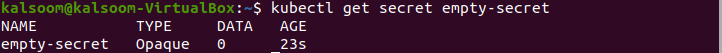
To display a summary of Kubernetes Secrets, run the following cited command in the terminal window of your Ubuntu 20.04 system.
You can find the name, type, data, and age of the secret. If a Secret configuration file is missing, the normal Secret type is Opaque. You will use the standard subcommand to designate an Opaque Secret type when creating a Secret with kubectl. The total of data items contained in the Secret is displayed in the DATA column. 0 indicates that we have constructed an empty Secret.
Step 4: Delete Kubernetes Secrets
To delete any specific Kubernetes Secret, run the following cited command in the terminal window of your Ubuntu 20.04 system.
You can check that the secret has been deleted successfully.
Conclusion
There is a fewer chance of the secret being revealed during the process of generating, reading, and modifying Pods because secrets can be produced irrespective of the Pods that use them. Secrets can also be handled differently by the system, such as preventing writing them to disk.
From this article, you can easily learn the way to create a secret. I hope you will have no problem while implementing it.