Therefore, the SSH keys emerged as a potent tool to bolster the security and simplify the access management. However, generating the SSH keys on Fedora Linux is not easy when you don’t have any prior knowledge about it. So, in this guide, we will include every possible information to generate the SSH keys on Fedora Linux.
How to Generate the SSH Keys on Fedora Linux
For Fedora Linux users, there are a few different approaches that you can try to generate the SSH keys with no hassle.
The Ssh-Keygen Command
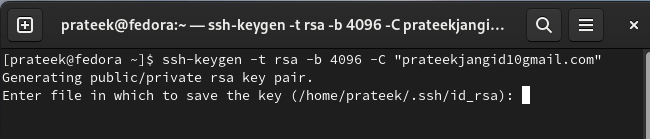
You can use the following given command to generate the RSA key (encryption algorithm) pair:
Let’s breakdown the given command:
- -t rsa: It specifies the key type, and we create an RSA key pair here.
- -b 4096: It provides the number of bits of your SSH key.
- -C “[email protected]”: It adds a comment to the key to identify the key later.
The command creates a 4096-bit RSA key pair and saves the SSH key in “~/.ssh/id_rsa” and the public key in “~/.ssh/id_rsa.pub”.
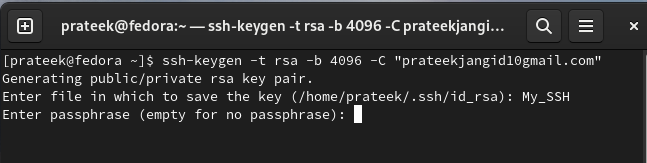
Now, add the name of the file to save the SSH key. For example, let’s save it to the My_SSH file.
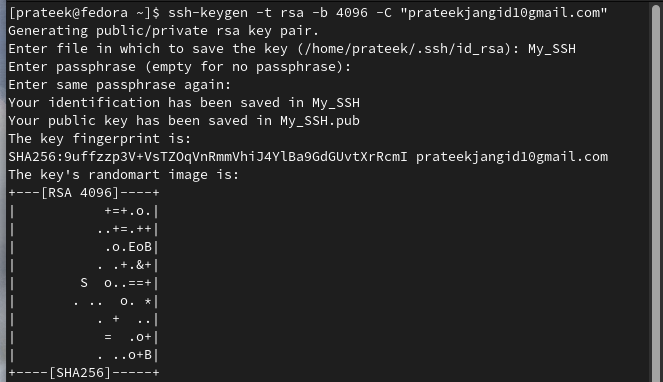
Finally, add the passphrase and then press the “Enter” button to finalize the SSH key generation:
Specify a Custom File Name
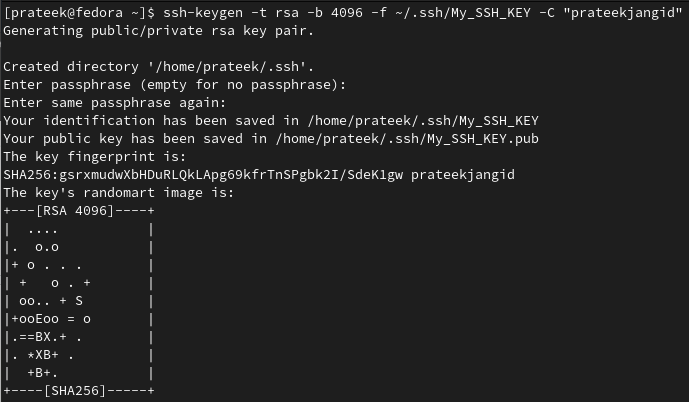
If you prefer a different file name or location, use the -f option to specify your choice:
This command creates a key pair named My_SSH_KEY within the “~/.ssh/” directory.
The Ssh-Copy-Id Command
You can run the following command to copy your public key on any server:
Replace the user with your remote server hostname with the server’s IP address or domain name. Following the public key transfer, you can validate the key-based authentication by attempting to SSH into the remote server:
If you configure everything correctly, you should gain an access without a password.
Conclusion
SSH keys represent a cornerstone of contemporary cybersecurity practices to ensure convenience and peace of mind in our interconnected world. That’s why we explained the simplest process to generate the SSH keys on Fedora Linux. It doesn’t matter whether you are an administrator or a developer; SSH keys come in handy to improve the security and privacy.