[adthrive-in-post-video-player video-id=”xH3Zro63″ upload-date=”2021-06-28T10:18:02.000Z” name=”How to do Firewall Configuration in CentOS 8″ description=”How to do Firewall Configuration in CentOS 8″ player-type=”collapse” override-embed=”true”]
To get started with the Firewall configuration in any Operating system, we first need to understand what a Firewall is and what it does. So let’s learn about Firewall first.
What is a firewall?
A firewall, in simple words, is a system used for network security by monitoring, controlling, and filtering the network traffic(incoming or outgoing). We can set some security rules if we want to allow or block some specific traffic. So, for the security of the system, a well-configured firewall is essential.
Firewalld: A firewall management system
If we talk about the firewall configuration in CentOS 8 Operating system, CentOS 8 comes with a firewall service known as firewalld. The firewalld daemon is an excellent firewall management software to manage and control the system’s network traffic. It is used by several major Linux distributions for performing the firewall configuration and as a network packet filtering system.
This post will learn all about firewalld and show you how to set up and do Firewall configuration in CentOS 8 Operating system. We will also try a couple of basic commands and perform some basic firewall configurations to manage network traffic. Let’s start with the understanding of Basic Firewalld concepts.
Basic Concepts of Firewalld
Firewalld daemon uses firewall-cmd behind it. The firewall-cmd is the command-line utility or client of the firewalld daemon. Let’s discuss and understand some concepts of this tool.
To control the traffic, firewalld uses zones and services. So to understand and start working with firewalld, you first have to understand what zones and services in firewalld are.
Zones
Zones are like a part of the network where we set some rules or set specific security requirements to manage and control the traffic flow under the defined rules of the zone. We first declare the rules of a zone, and then a Network interface is assigned to it, on which the security rules are applied.
We can set or change any rule based on the network environment. For public networks, we can set some strict rules for our firewall configuration. While, for a home network, you do not need to set some strict rules, some basic rules will work fine.
There are some predefined zones by the firewalld based on the trust level. So it is better to understand them and utilize them according to the security level that we want to set.
- drop: This is the zone with the lowest level of security. In this zone, outgoing traffic will pass, and incoming traffic will not be allowed to pass.
- block: This zone is almost the same as the above drop zone, but we will get a notification if a connection gets dropped in this zone.
- public: This zone is for untrusted public networks, where you want to limit the incoming connections based on the case scenario.
- external: This zone is used for external networks when you use the firewall as your gateway. It is used for the external portion of the gateway instead of the inner portion.
- internal: opposite to the external zone, this zone is for internal networks when you use the firewall as your gateway. It is opposite to the external zone and used on the internal portion of the gateway.
- dmz: This zone name is derived from the demilitarized zone, where the system will have minimal access to the rest of the network. This zone is used explicitly for the computers in a less populated network environment.
- work: This zone is used for working environment systems to have almost all the trusted systems.
- home: This zone is used for home networks where most of the systems are trustworthy.
- trusted: This zone is with the highest level of security. This zone is used where we can trust each and every system.
It is not mandatory to follow and use the zones as they are pre-defined. We can alter the zone’s rules and assign a network interface to it later.
Firewalld Rules Settings
There can be two types of rulesets in the firewalld:
- Runtime
- Permanent
When we add or change a ruleset, it is applied only to the running firewall. After reloading the firewalld service or system reboot, the firewalld service will only load the permanent configurations. Recently added or changed rulesets will not be applied because the changes we make to the firewalld are only used to the runtime configuration.
To load the recently added or changed rulesets on rebooting the system or reloading the firewalld service, we need to add them to the permanent firewalld configurations.
To add the rulesets and keep them in the configuration permanently, simply use the –permanent flag to the command:
After adding the rulesets to the permanent configurations, reload the firewall-cmd using the command:
On the other hand, if you want to add the runtime rulesets to the permanent settings, use the command typed below:
Using the above command, all the runtime rulesets will be added to the permanent firewall settings.
Installing and Enabling firewalld
Firewalld comes pre-installed on the latest version of CentOS 8. However, for some reason it is broken or not installed, you can install it using the command:
To start the firewalld service, execute the command typed below:
It is better if you automatically start on the boot, and you do not have to start it again and again.
To enable the firewalld daemon, execute the command given below:
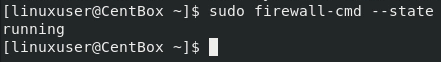
To verify the state of the firewall-cmd service, run the command given below:
You can see in the output; the firewall is running perfectly fine.
Default Firewall Rules
Let’s explore some of the default Firewall rules to understand them and change them if needed fully.
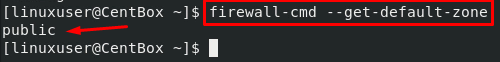
To know the selected zone, execute the firewall-cmd command with the –get-default-zone flag as shown below:
It will show the default active zone that controls the incoming and outgoing traffic for the interface.
The default zone will remain the only active zone as long as we don’t give firewalld any commands to change the default zone.
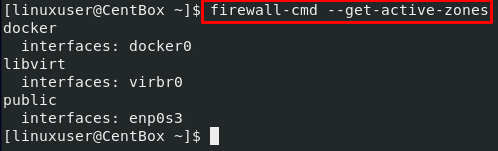
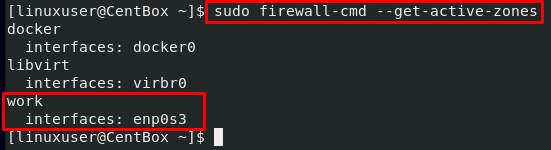
We can get the active zones by executing the firewall-cmd command with the –get-active-zones flag as shown below:
You can see in the output that the firewall controls our network interface, and the rulesets of the public zone will be applied on the Network Interface.
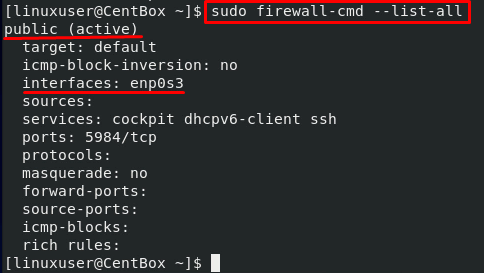
If you want to get rulesets defined for the public zone, execute the command typed below:
By looking at the output, you can witness that this public zone is the default zone and an active zone, and our Network interface is connected to this zone.
Changing zone of the Network Interface
Since we can change zones and change the network Interface zone, changing zones come in handy when we have more than one interface on our machine.
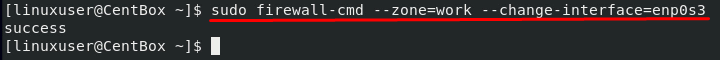
To change the zone of the Network Interface, you can use the firewall-cmd command, provide the zone name to the –zone option, and network interface name to the –change-interface option:
To verify either the zone is changed or not, run the firewall-cmd command with –get-active zones option:
You can see that the zone of the interface is successfully changed as we desired.
Change Default Zone
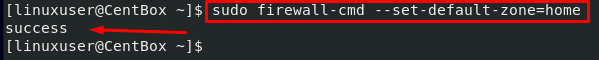
In case you want to change the default zone, you can use the –set-default-zone option and provide it the zone name that you want to set with the firewall-cmd command:
For example, for changing the default zone to home instead of the public zone:
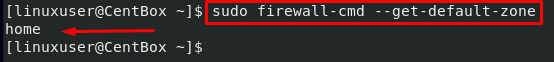
To verify, execute the command given below to get the default zone name:
Alright, after playing with zones and network interfaces, let’s learn how to set rules for applications in the firewall on CentOS 8 Operating system.
Setting Rules for Applications
We can configure the firewall and set rules for applications, so let’s learn how to add a service to any zone.
Add a Service to a Zone
We often need to add some services to the zone in which we are currently working.
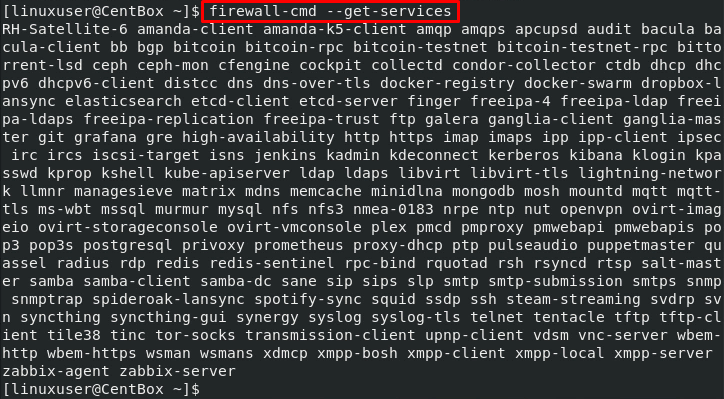
We can get all of the services using the –get-services option in the firewall-cmd command:
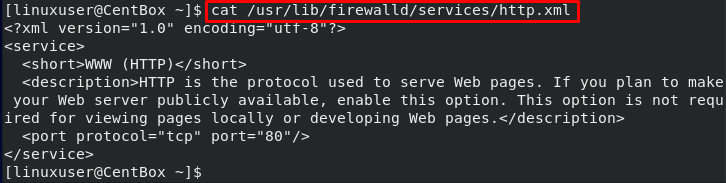
To get more details about any service, we can look at the .xml file of that specific service. The service file is placed in the /usr/lib/firewalld/services directory.
For example, if we take a look at the HTTP service, it will look like this:
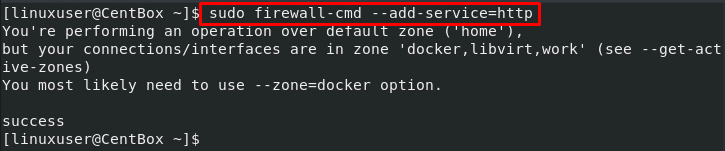
To enable or add the service to any zone, we can use the –add-service option and provide it with the service name.
If we do not provide the –zone option, the service will be included in the default zone.
For example, if we want to add an HTTP service to the default zone, the command will go like this:
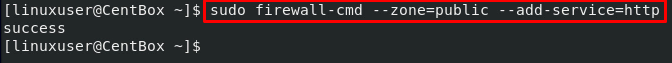
Contrary to this, if you want to add a service to a specific zone, mention the zone name to the –zone option:
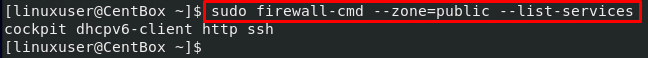
To verify the addition of service to the public zone, you can use the –list-services option in the firewall-cmd command:
In the above output, you can witness that the services added in the public zone are displayed.
However, the HTTP service that we have just added in the public zone is in the runtime configurations of the firewall. So, if you want to add the service into the permanent configuration, you can do so by providing an additional –permanent flag while adding the service:
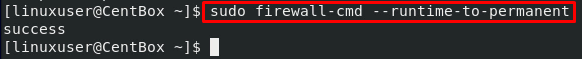
But, if you want to add all the runtime configurations into the permanent configurations of the firewall, execute the firewall-cmd command with the –runtime-to-permanent option:
All the wanted or unwanted runtime configurations will be added to the permanent configurations by running the above command. So, it is better to use the –permanent flag if you want to add a configuration to the permanent configurations.
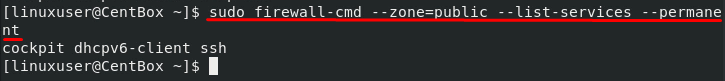
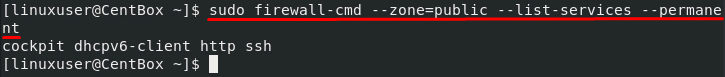
Now, to verify the changes, list the services added to the permanent configurations using the –permanent and –list-services option in the firewall-cmd command:
How to open IP addresses and Ports on the Firewall
Using the firewall, we can allow all or some specific IP addresses to pass and open some specific ports as per our requirement.
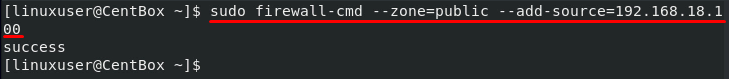
Allow a source IP
For allowing the traffic flow from a specific IP address, you can allow and add the IP address of the source by first mentioning the zone and using the –add-source option:
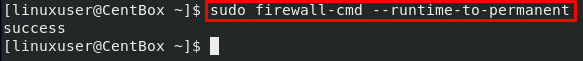
If you want to add the source IP address to the firewall configuration permanently, execute the firewall-cmd command with –runtime-to-permanent option:
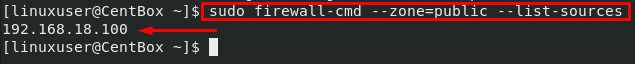
To verify, you can list the sources as well using the command given below:
In the above command, make sure to mention the zone whose sources you want to list.
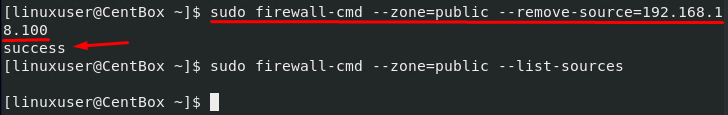
If for any reason, you want to remove a source IP address, the command for removing the source IP address would go like this:
Open a source port
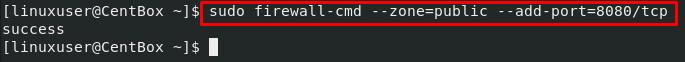
To open a port, we first have to mention the zone, and then we can use the –add-port option to open the port:
In the above command, /tcp is the protocol; you can provide the protocol according to your need, like UDP, SCTP, etc.
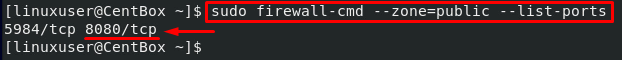
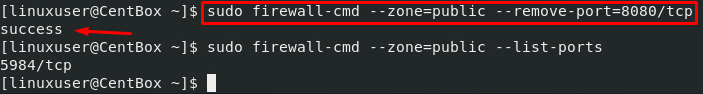
To verify, you can list the ports as well using the command given below:
In the above command, make sure to mention the zone whose ports you want to list.
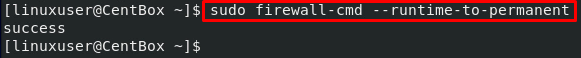
For keeping the port open and adding these configurations to the permanent configuration, either uses the –permanent flag at the end of the above command or execute the command given below to add all the runtime configuration to the permanent configuration of the firewall:
If for any reason, you want to remove a port, the command for removing the port would go like this:
Conclusion
In this detailed and profound post, you have learned what a Firewall is, the basic concepts of a Firewall, what zones are, and firewalld rules settings. You have learned to install and enable the firewalld service on CentOS 8 Operating system.
In the configuration of the firewall, you have learned about the default firewall rules, how to list default zones, active zones, and all zones of firewall-cmd. Moreover, this post contains a brief explanation on how to change the zone of the network interface, how to set rules for applications like adding a service to a zone, opening IP addresses and ports on the firewall.
After reading this post, you will manage the traffic flow to your server and alter the zone’s rulesets because this post has a detailed description of how to administer, configure, and manage the firewall on the CentOS 8 Operating system.
If you want to dig more and learn more about Firewall, do not hesitate to visit the Official Documentation of Firewalld.