How to Check for and Patch Spectre and Meltdown Vulnerability on CentOS7
Spectre and Meltdown Vulnerabilities of Intel and some other processors got quite a lot of attention in 2018. These are really bad hardware security flaws. A lot of Desktops, Laptops, and Servers are affected by Spectre and Meltdown vulnerabilities. Let’s take a look at what these are.
Spectre Vulnerability:
By default, there’s an isolation between different applications in a computer. Spectre vulnerability breaks that isolation. The result is that it allows a hacker to trick an application into leaking their secret information from the kernel module of the operating system.
Meltdown Vulnerability:
By default, there’s an isolation between the user, the applications and the operating system of a computer. Meltdown breaks this isolation. The end result is that, a hacker can write a program and it can access the memory, even the memory used by other applications and get secret information out of the system.
Checking for Spectre and Meltdown Vulnerabilities:
You can use a Spectre and Meltdown Checker Script to check whether your processor is vulnerable to Spectre and Meltdown.
To use this script, first navigate to a directory where you would like to download the script. I will download it in the /tmp directory, so it will be removed the next time I boot automatically.
Now run the following command to download the Spectre and Meltdown Checker Script from GitHub using wget:
Spectre and Meltdown Checker Script should be downloaded.
Now run the Spectre and Meltdown Checker script with the following command:
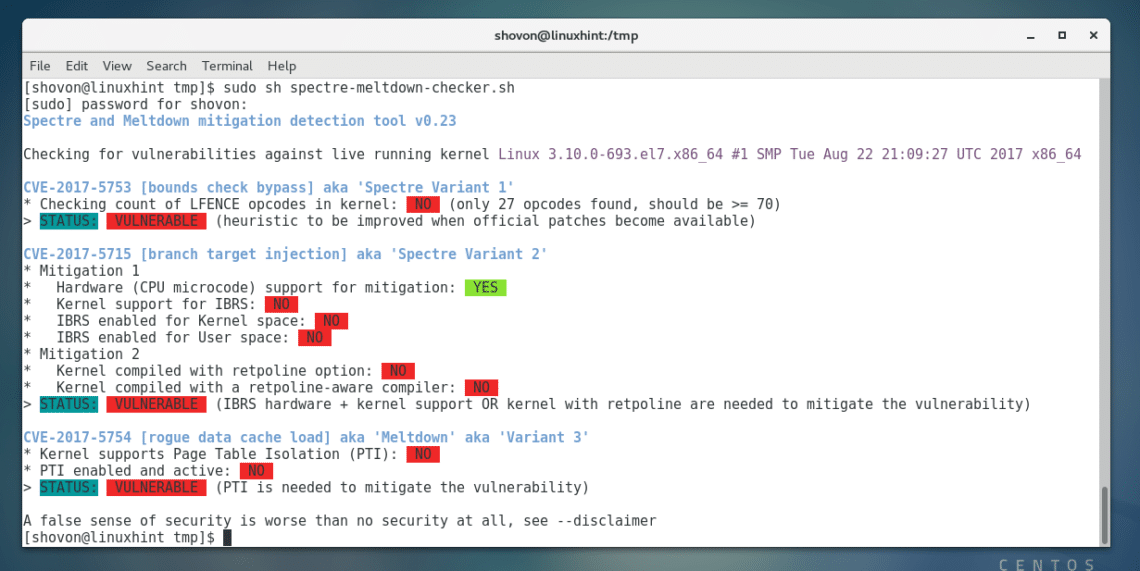
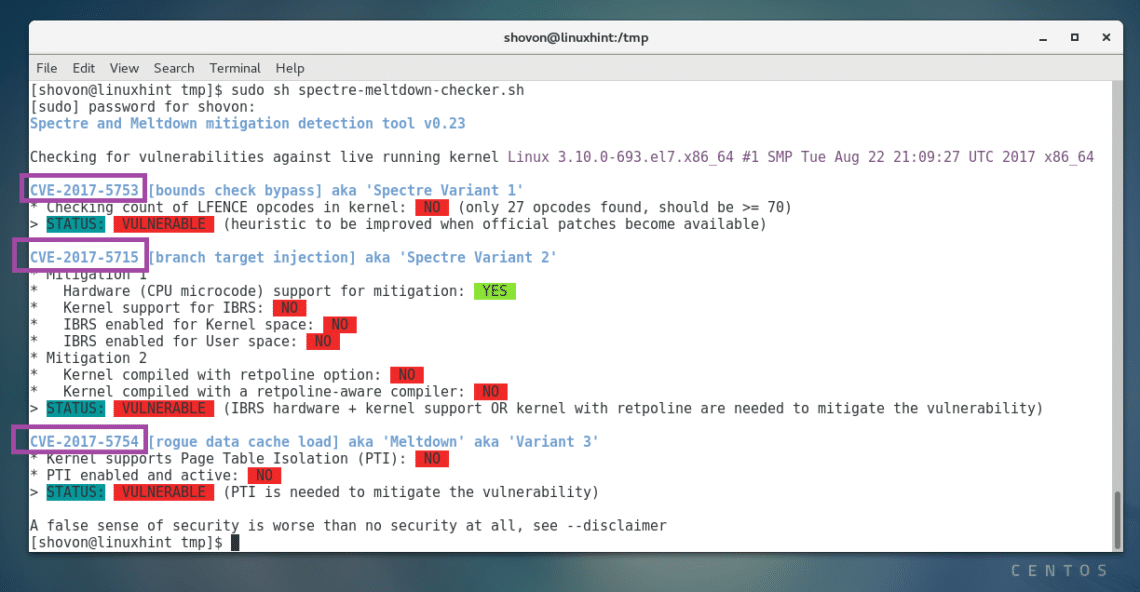
This is the output from my computer. You can see that my intel processor is affected by Spectre and Meltdown vulnerabilities. But luckily there’s a way to patch it.
The marked codes CVE-2017-5753, CVE-2017-5715, CVE-2017-5754 are used to identify these vulnerabilities internationally. If you happened to run into any problem, you may search on Google with these codes. Hopefully you will find something useful.
Fixing Spectre and Meltdown Vulnerabilities with Kernel Upgrade:
To fix Spectre and Meltdown Vulnerabilities RHEL7/CentOS 7 released recommended kernel upgrades. All you have to do is update the kernel and you will be able to fix these issues.
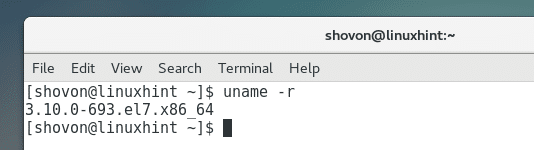
First check the version of Kernel you’re running using the following command:
You can see that I am running kernel 3.10.0-693 on my CentOS 7 machine.
Now I am going to update the CentOS 7 operating system. The kernel should be updated along with the operating system.
Run the following command to update the CentOS 7 operating system:
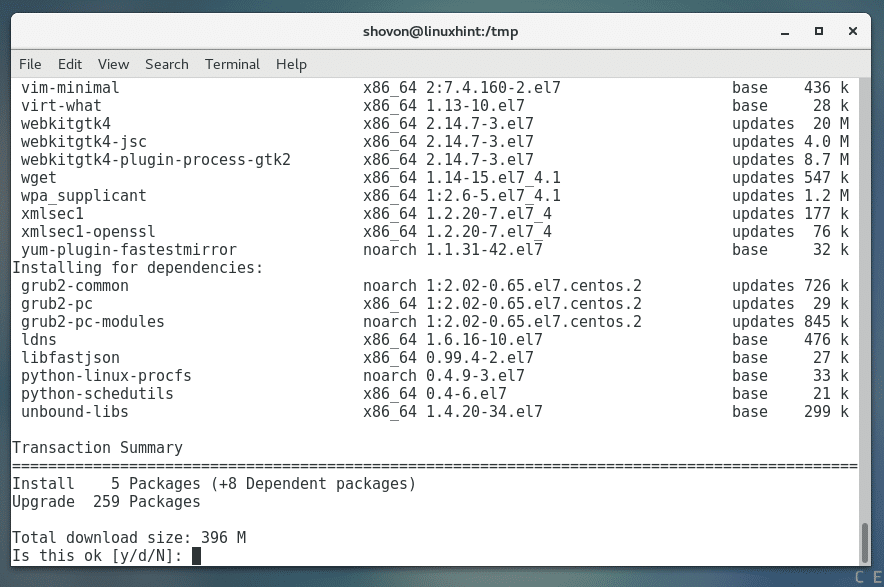
Press ‘y’ and press
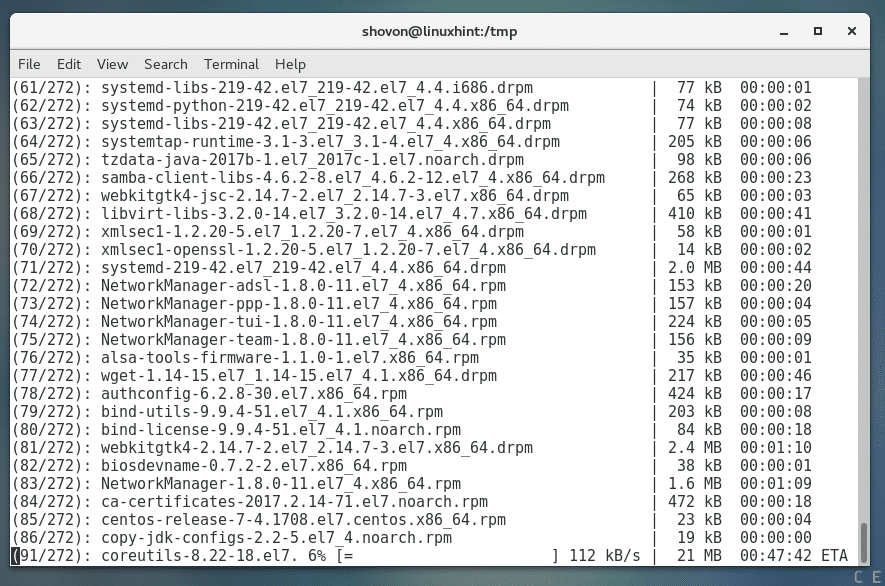
The updated packages should be downloaded and installed from the internet. It may take a while depending on your internet connection.
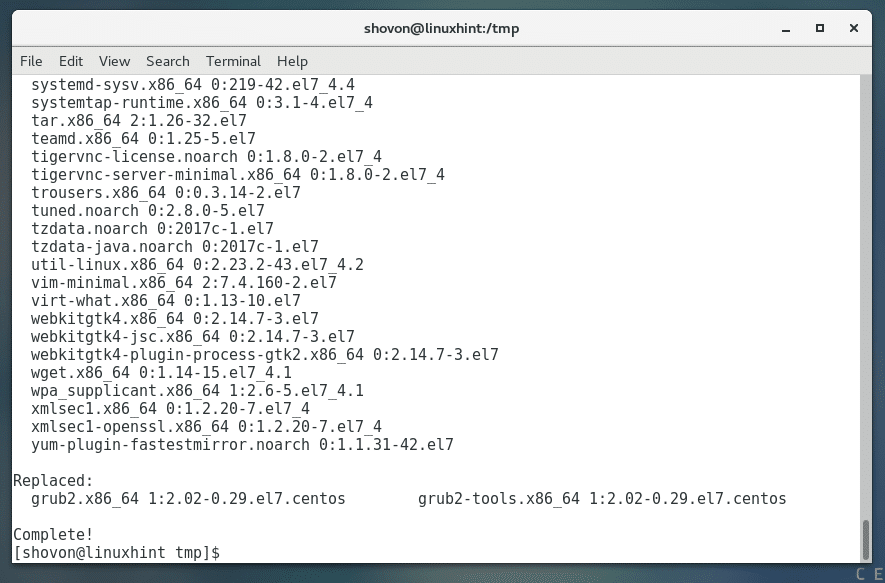
The update should go smoothly.
Once the update is complete, restart your computer. This is recommended as the kernel is also updated.
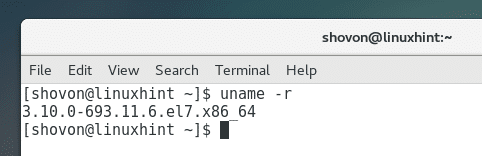
Once your computer boots, you can run the following command to check for the kernel version that you’re using again:
You should see a different kernel version than before. Earlier for me it was 3.10.0-693 and now it is 3.10.0-693.11.6
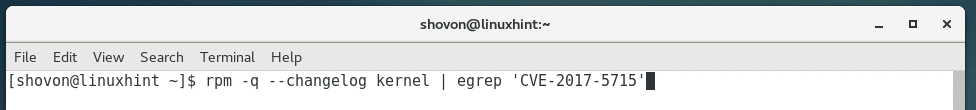
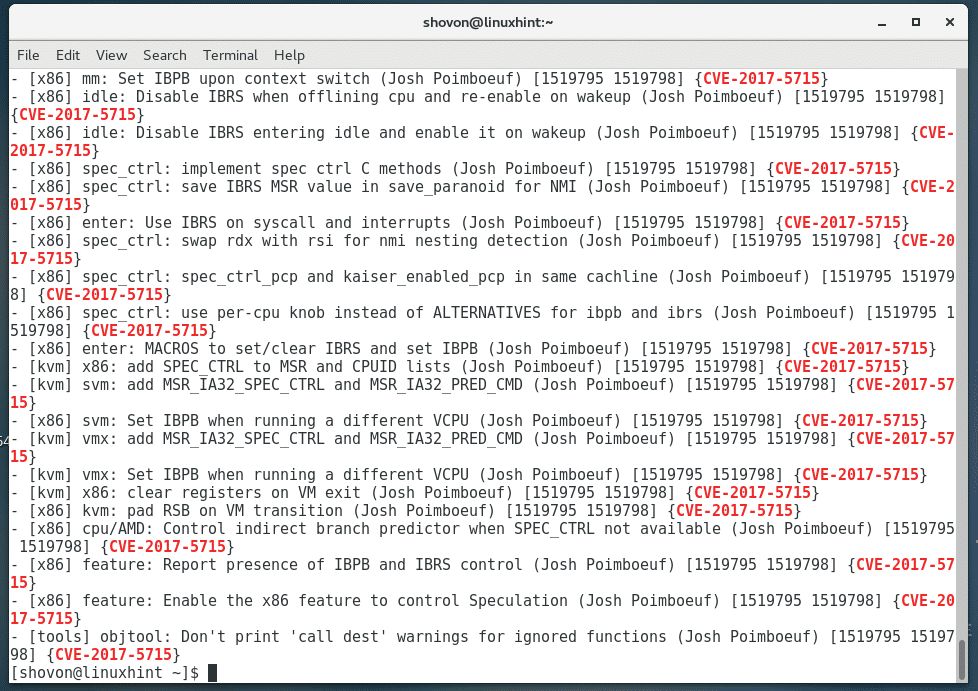
You can check whether any changes were made to the kernel for CVE-2017-5715 vulnerability with the following command:
You should find a lot of matches on CentOS 7. That’s a good sign.
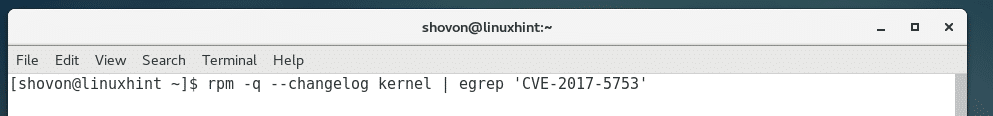
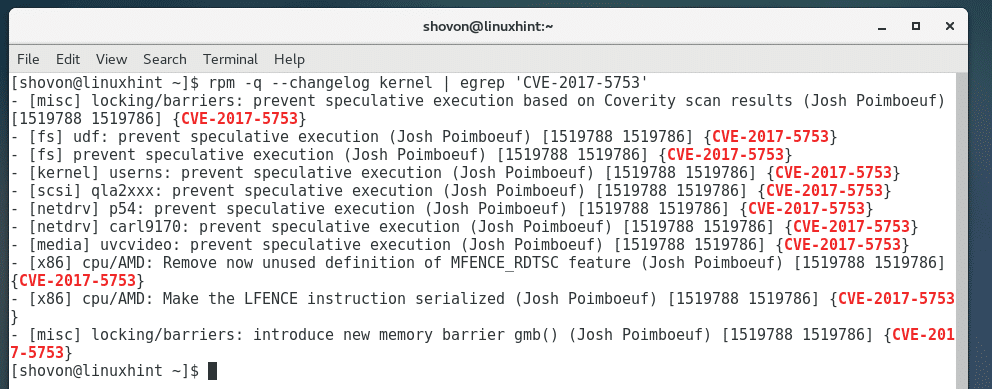
You can also check for kernel changes related to CVE-2017-5753 with the following command:
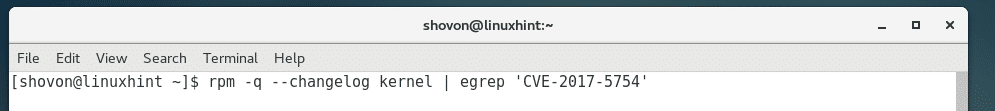
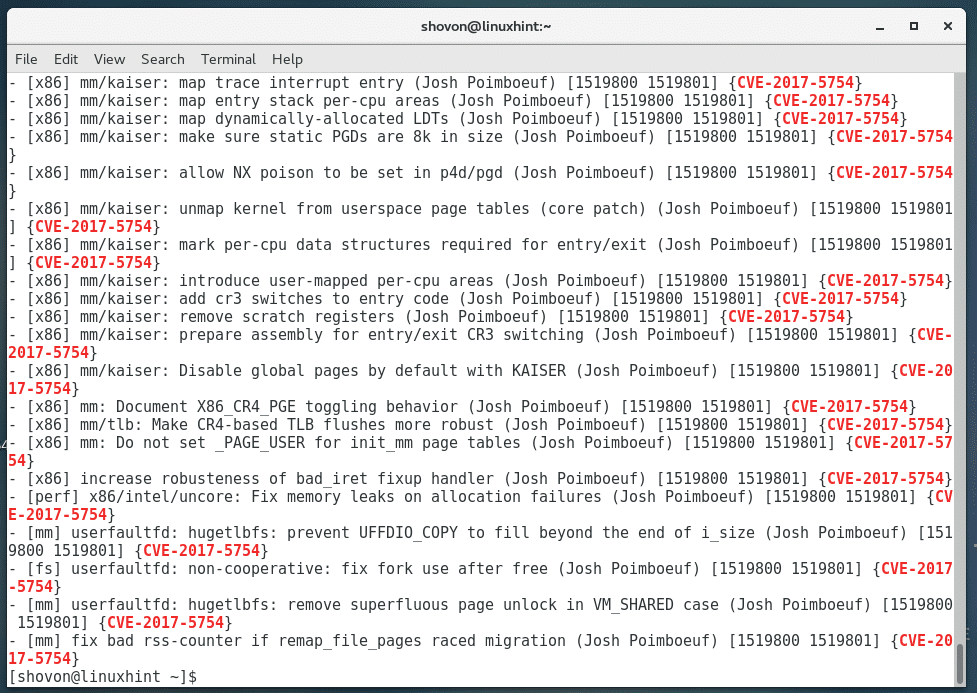
You can also check for kernel changes related to CVE-2017-5754 with the following command:
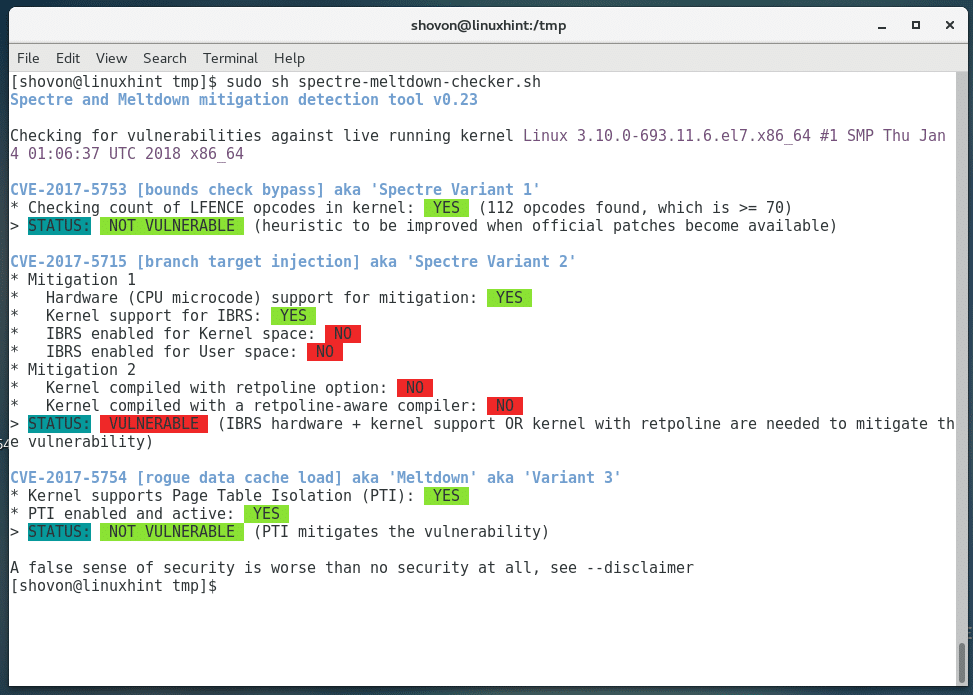
You can also run the Spectre and Meltdown Checker Script again to find out what were patched in the kernel upgrade.
You can see from the screenshot below that a lot of vulnerabilities were patched after the kernel updated. As of this writing, there are still some vulnerabilities that are not patched. Keep your eyes on the future kernel updates of CentOS 7. All of these will be fixed eventually.
That’s how you find out whether your processor is vulnerable to Spectre and Meltdown attacks on CentOS 7 and patch CentOS 7 for Spectre and Meltdown vulnerabilities. Thanks for reading this article.