Many people have misconceptions about Ansible and the platforms it supports, believing that it is only accessible for Ubuntu. However, Ansible can also be used to control Windows PCs, connected devices, internet security devices, web services, applications, and other things. We are going to talk about using Windows with Ansible in this tutorial.
The Ansible configuration tool can administer and carry out essential tasks in Windows installations, such as remote managers with WinRM and protection alerts. Despite requiring Ubuntu to operate in Ansible, Microsoft controllers may administer and manage their devices using Ansible despite having any prior experience with Ubuntu terminals. Microsoft controllers will be able to administer Microsoft Windows using Ansible in some kind of way that is relevant to them because of native Windows functionality that employs Microsoft Windows PowerShell remote. Advanced solutions for controlling and managing Microsoft Windows platforms are included in the Ansible Software Platform for organizational management. You can automate deployment, software activation, and system integration for a multivendor environment with the aid of the Ansible Software Platform.
In Ansible, most of the terminology and guidelines used to manage remote hosts of Linux as well as these terminologies equally apply to Microsoft Windows hosts. But there are still certain peculiarities whenever it concerns variables of Ansible like path separators or OS-specific activities. WinRM must be set up to enable access to Windows systems from the Ansible controller. You can get initiated utilizing Ansible for Microsoft Windows in your developing or monitoring settings by running the PowerShell script. Every authorized Microsoft Windows host is configured by the script for WinRM.
Prerequisites:
Please make sure you always had these requirements:
Version: We are going to utilize Ansible Controller version 2.9. For it to make changes, we need a controlling server for Ansible, and in this case, we are using Ansible as a controller with the IP address 192.168.5.220.
Windows Host: We require them to interact with the local hosts. Furthermore, we are using the Windows host in this instance as a target remote server for the duration of the operation.
Python: Your Ansible controller host device will be configured to run Python. Python will utilize version 2, while version 3 is also an option.
Package: The Windows host server will be configured to install the “pip” package.
Windows Workstation: You will need to spend time at a Windows console as we pre-configure the host that Microsoft will use to handle Ansible.
Power Shell: The Windows server will have the ability to control PowerShell remote access.
Example: Establishing a Microsoft Windows Host to Allow Connections with Ansible Controller
In this example, first, we will work for the target remote host which is Windows_Host. Then, we will work with Ansible so there will be no confusion for the user.
Target Window_Host
There are no servers needed for Ansible. So, both SSH and Windows Remote manager are compatible with Windows WinRM. WinRM means Windows remote manager and it is frequently used over SSH because of the tight integration of WinRM.
Setup the WinRM
After that, we are going to update the WinRM in Microsoft Windows. The Ansible software has created commands that are available to evaluate WinRM and perform the required adjustments so that Ansible can access these commands. Although we only want to utilize basic credentials, so we would prefer to employ something more secure to access it. The following are the steps for the update of the WinRM:
Saving the Commands Path
We will use the commands, so for that, we first launch the Microsoft PowerShell terminal window so that we can save the commands path.
ConfigureRemotingForAnsible.ps1"
Address of the Command’s Storage
We will use the below URL so that we can easily store the commands there:
Download the Commands and Showcase them Locally
Now, we will download the commands and we will display these commands in a local document.
Run the Commands
To execute, the command is the path that will showcase the execution of the document.
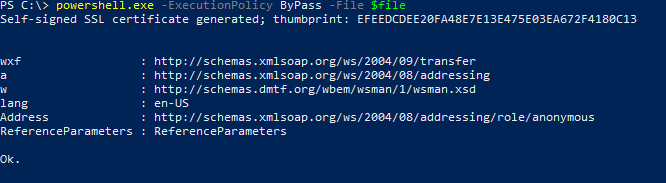
After writing the path above, we will get the output below in the PowerShell in Windows.
Verify the WinRM Connectivity
This is to check whether the connection of the WinRM is built with Ansible or not.
As shown, Ansible and WinRM are compatible with each other.
Ansible Controller
This is the working in the Ansible tool and the commands are used by the controller so that it can configure the information and build the connection between Windows and Ansible. First, we will create the playbook.
Creating the Playbook
Now, we will manage the deployment and updating of packages. For that, let us create a playbook in Ansible first:
Here is the declaration of the Ansible playbook. When the playbook win_ping.yml is created, then it will be launched into the new terminal of Ansible. Here, we will write the hosts and the task which we want to perform. In win_ping.yml, we first name the playbook which we want to do in the playbook.
Then, we will write the name of the hosts, as we are configuring the data of the Microsoft Windows host. So, the name of the target host is “Windows_Host”. Then, we have passed the “false” to the gather_fact option of the playbook so that it will not retrieve the information of the target Windows host in the playbook. Next, we have listed the tasks in the playbook. We want to check the connection between the Ansible playbook controller and the target Windows host so we will pass the playbook name in the task.
hosts: Windows_Host
become: false
gather_facts: false
tasks:
- name: test connection
win_ping:
Creating the Inventory File
After the creation and termination of the playbook, we will build the inventory file so that we will provide the information about the Windows host here. We will write the IP address, name of the user, password, connection name, port number, and WinRM validation. This is the statement we will write to build the inventory file in Ansible.
hosts:
Windows_Host:
ansible_host: 192.168.5.220
ansible_user: ansible
ansible_password: ********
ansible_connection: winrm
ansible_port: 5986
ansible_winrm_server_cert_validation: ignore
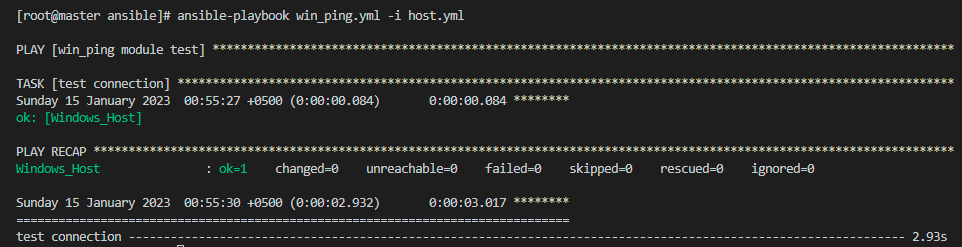
After providing the necessary information about the target Windows host, we will execute the playbook along with the inventory file. To do so, write the command below:
As shown, the connection between the ansible controller and the Windows host has been made successfully.
Conclusion
Using the WinRM package in Ansible, we have learned how to automate Microsoft Windows in this lecture. We described in detail how to set up a Microsoft Windows host for Ansible. Ansible is a tool that has historically been associated with Linux, although it can also be utilized on Microsoft Windows with ease.